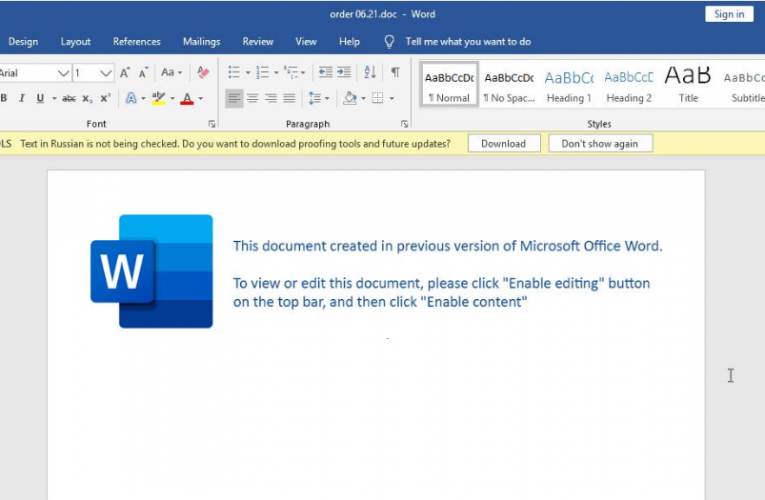
Will the Real Msiexec Please Stand Up? Exploit Leads to Data Exfiltration
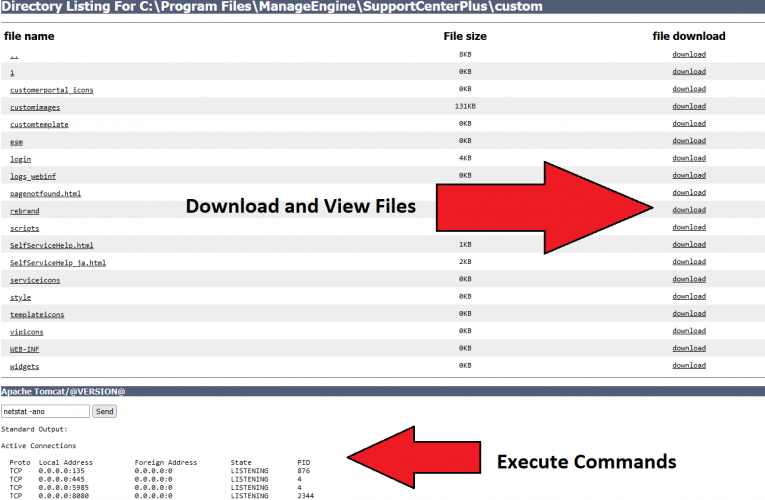
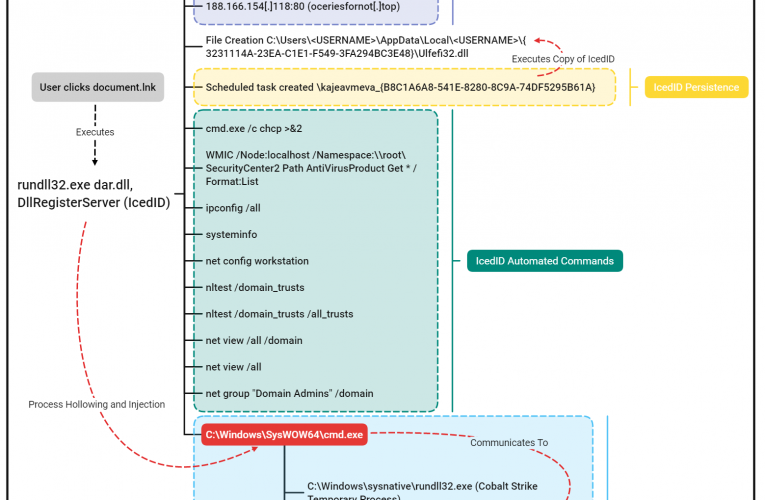
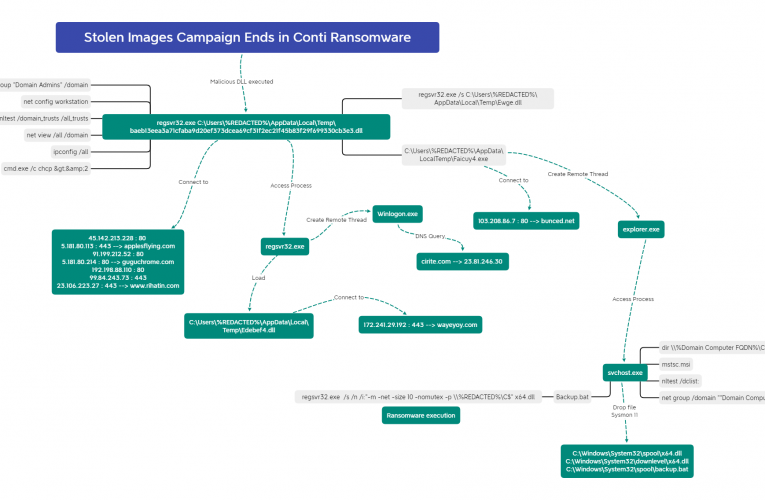
In this multi-day intrusion, we observed a threat actor gain initial access to an organization by exploiting a vulnerability in ManageEngine SupportCenter Plus. The threat actor, discovered files on the … Read More