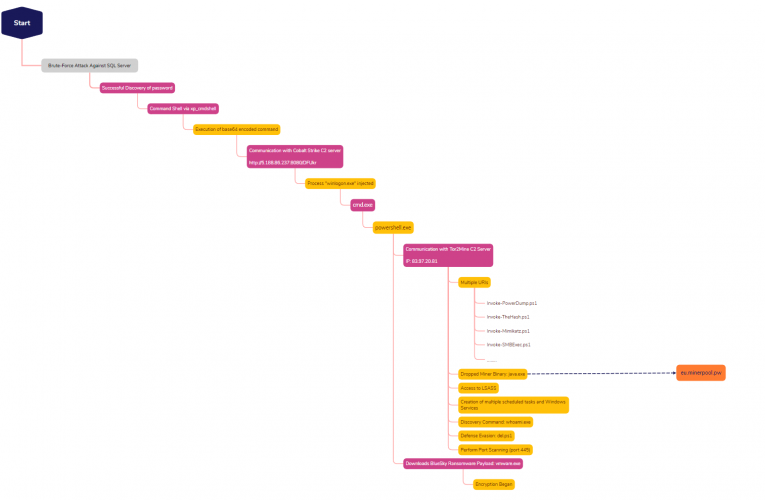
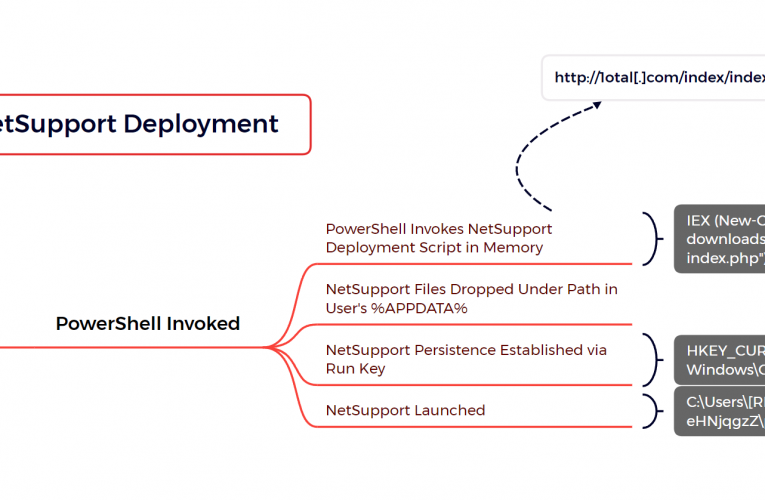
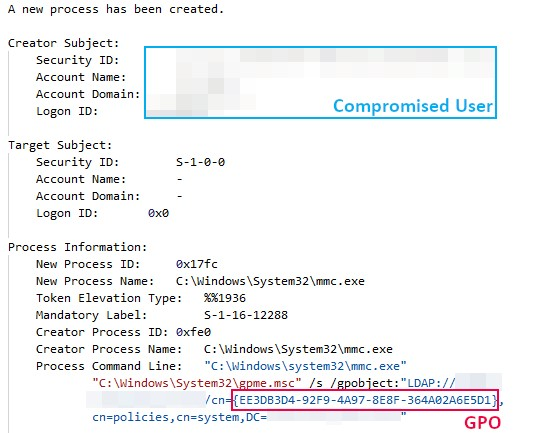
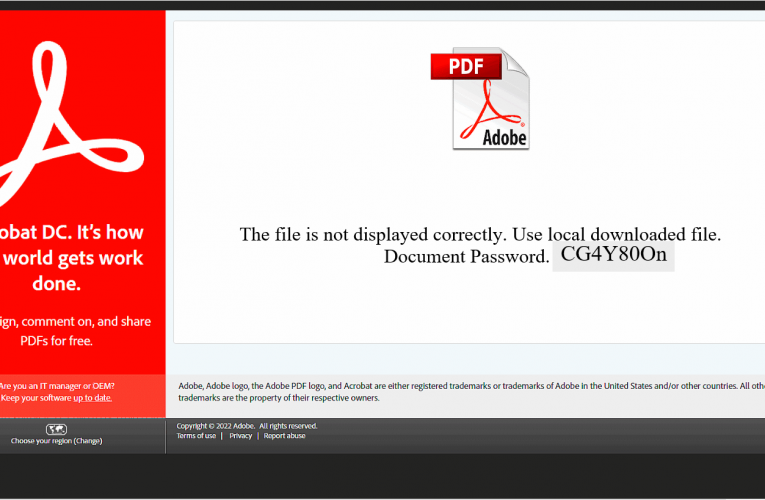
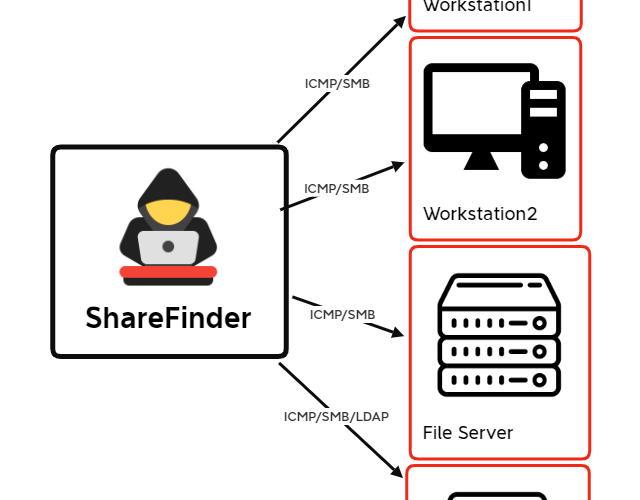
Lets Open(Dir) Some Presents: An Analysis of a Persistent Actor’s Activity
This report is a little different than our typical content. We were able to analyze data from a perspective we typically don’t get to see… a threat actor’s host! In … Read More