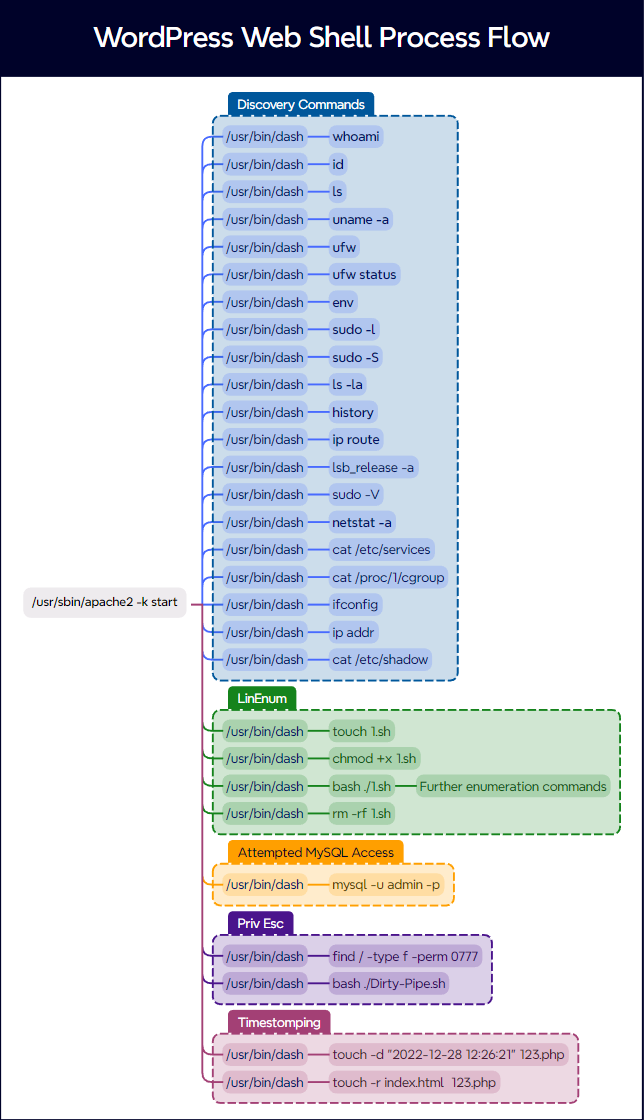
Threat Brief: WordPress Plugin Exploit Leads to Godzilla Web Shell, Discovery & New CVE
Below is a recent Threat Brief that we shared with our customers. Each year, we produce over 20 detailed Threat Briefs, which follow a format similar to the below. Typically, these reports include specific dates and times to provide comprehensive insights; however, please note that such information has been redacted in this public version. IOCs are available to customers within Event 27236 (uuid – fe12e833-6f0c-45c9-97d6-83337ea6c5d3).
Recent Private Threat Briefs:
- BlackSuit Ransomware
- BlackCat Ransomware
- AlphV Ransomware
- LockBit Black Ransomware
- LockBit 3.0 Ransomware
The DFIR Report Services
- Private Threat Briefs: Over 20 private reports annually, such as this one but more concise and quickly published post-intrusion.
- Threat Feed: Focuses on tracking Command and Control frameworks like Cobalt Strike, Metasploit, Sliver, etc.
- All Intel: Includes everything from Private Threat Briefs and Threat Feed, plus private events, long-term tracking, data clustering, and other curated intel.
- Private Sigma Ruleset: Features 100+ Sigma rules derived from 40+ cases, mapped to ATT&CK with test examples.
- DFIR Labs: Offers cloud-based, hands-on learning experiences, using real data, from real intrusions. Interactive labs are available with different difficulty levels and can be accessed on-demand, accommodating various learning speeds.
Contact us today for a demo!


